Module 3: Operating-System Structures
... into memory and to run it. I/O operations – since user programs cannot execute I/O operations directly, the operating system must provide some means to perform I/O. File-system manipulation – program capability to read, write, create, and delete files. Communications – exchange of information betwee ...
... into memory and to run it. I/O operations – since user programs cannot execute I/O operations directly, the operating system must provide some means to perform I/O. File-system manipulation – program capability to read, write, create, and delete files. Communications – exchange of information betwee ...
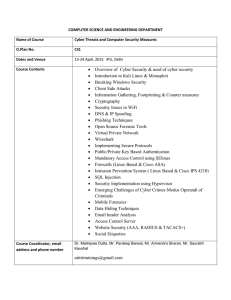
• Overview of Cyber Security & need of cyber security • Introduction
... COMPUTER SCIENCE AND ENGINEERING DEPARTMENT Name of Course ...
... COMPUTER SCIENCE AND ENGINEERING DEPARTMENT Name of Course ...
IO Systems - monismith.info
... • This will prevent user processes from disrupting the OS • Protect memory-mapped and I/O memory port locations from user access, too • Kernel must provide a locking mechanism to allow only protected access to these features ...
... • This will prevent user processes from disrupting the OS • Protect memory-mapped and I/O memory port locations from user access, too • Kernel must provide a locking mechanism to allow only protected access to these features ...
batch systems
... • “All the code you didn’t write” – this view includes all system libraries, compilers, assemblers – all the software shipped with the machine (and maybe more) ...
... • “All the code you didn’t write” – this view includes all system libraries, compilers, assemblers – all the software shipped with the machine (and maybe more) ...
Operating Systems Operating System (OS) CS 217
... OS gains control through trap, switches to supervisor model, performs service, switches back to user mode, and gives control back to user ...
... OS gains control through trap, switches to supervisor model, performs service, switches back to user mode, and gives control back to user ...
Lect03
... the OS rotates its various jobs in and out of execution via time-sharing o Each job gets a predetermined “time slice” o At end of time slice current job is set aside and a new one starts o By rapidly shuffling jobs, illusion of several jobs executing simultaneously is created ...
... the OS rotates its various jobs in and out of execution via time-sharing o Each job gets a predetermined “time slice” o At end of time slice current job is set aside and a new one starts o By rapidly shuffling jobs, illusion of several jobs executing simultaneously is created ...
Security strategy
... documents and computer files. Organisations have a duty to protect the privacy of data which they hold about members of the public and their staff, and to process this data only in the manner for which it was intended. ...
... documents and computer files. Organisations have a duty to protect the privacy of data which they hold about members of the public and their staff, and to process this data only in the manner for which it was intended. ...
Directories
... • Directory can contain a maximum of 64,000 subdirectories (as opposed to 32,000 in ext3) • You can also mount an existing ext3 filesystem as ext4 filesystem (without having to upgrade it). • Several other new features are introduced in ext4: ...
... • Directory can contain a maximum of 64,000 subdirectories (as opposed to 32,000 in ext3) • You can also mount an existing ext3 filesystem as ext4 filesystem (without having to upgrade it). • Several other new features are introduced in ext4: ...
powerpoint
... Issues in Operating Systems • structure - how is the OS organized? • sharing - how are resources shared among users? • naming - how are resources named by users or programs? • protection - how is one user/program ...
... Issues in Operating Systems • structure - how is the OS organized? • sharing - how are resources shared among users? • naming - how are resources named by users or programs? • protection - how is one user/program ...
System Software
... identify and remove the virus found in memory, storage media or incoming files identify a virus by finding its virus signature Signs of viruses Unusual messages on screen Decrease system performance Missing data Inability to access the hard drive ...
... identify and remove the virus found in memory, storage media or incoming files identify a virus by finding its virus signature Signs of viruses Unusual messages on screen Decrease system performance Missing data Inability to access the hard drive ...
Linux - the most important … Linux: SHELL ~$ command –options
... system (assuming you have local mail), the messages are first stored in /var/spool/mail /lib ...
... system (assuming you have local mail), the messages are first stored in /var/spool/mail /lib ...
FAT:
... The FAT file system is relatively straightforward technically and is supported by virtually all existing operating systems for personal computers. This makes it an ideal format for solid-state memory cards and a convenient way to share data between operating systems. The FAT file system was created ...
... The FAT file system is relatively straightforward technically and is supported by virtually all existing operating systems for personal computers. This makes it an ideal format for solid-state memory cards and a convenient way to share data between operating systems. The FAT file system was created ...
Nechiele Whittington - Optimal Resume at KAPLAN UNIVERSITY
... created the first version of UNIX which was based off of the C programming language. From that point on, the world of computers would never be the same (FreeDictionary.com UNIX). UNIX was the launch pad for operating systems then, and as you can imagine, is still the basis of the standard operating ...
... created the first version of UNIX which was based off of the C programming language. From that point on, the world of computers would never be the same (FreeDictionary.com UNIX). UNIX was the launch pad for operating systems then, and as you can imagine, is still the basis of the standard operating ...
Presentación de PowerPoint
... File system: mecanism to access the file using its symbolic name Directory: data structure that groups a set of files File operations: open, close, read, write, append, ... UNIX file management is implemented using ...
... File system: mecanism to access the file using its symbolic name Directory: data structure that groups a set of files File operations: open, close, read, write, append, ... UNIX file management is implemented using ...
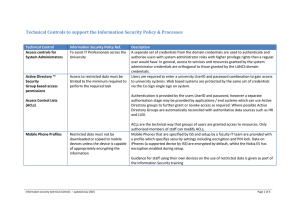
Technical Controls to support the Information
... MSCHAPv2 security for user authentication. Users are required to authenticate using their University ID and Password. RDP access is only allowed once the user has connected via a VPN connection, and only when a user has explicitly been added by the Service Desk to use the RDP service. ...
... MSCHAPv2 security for user authentication. Users are required to authenticate using their University ID and Password. RDP access is only allowed once the user has connected via a VPN connection, and only when a user has explicitly been added by the Service Desk to use the RDP service. ...
N4Less11
... in other programs without re-creating it. • Windows provides the Clipboard, a special area that stores data cut or copied from one document, so you can re-use it elsewhere. ...
... in other programs without re-creating it. • Windows provides the Clipboard, a special area that stores data cut or copied from one document, so you can re-use it elsewhere. ...
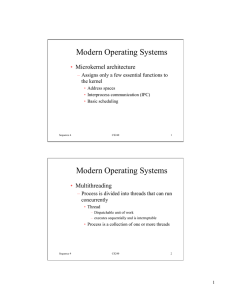
Modern Operating Systems Modern Operating Systems
... • Symmetric multiprocessing (SMP) – There are multiple processors – These processors share same main memory and I/O facilities – All processors can perform the same functions ...
... • Symmetric multiprocessing (SMP) – There are multiple processors – These processors share same main memory and I/O facilities – All processors can perform the same functions ...
UNIX-like Operating Systems
... were very diverse — each OS specific to particular hardware, used radically different models of commands and procedures, Typically, each time the manufacturer brought out a new machine, there would be a new OS. ...
... were very diverse — each OS specific to particular hardware, used radically different models of commands and procedures, Typically, each time the manufacturer brought out a new machine, there would be a new OS. ...
Security Considerations for Health Care Organizations
... AUDIT, DETECT, and SECURE Three stages of secure process that are to be followed Provide security agents Automated Continually monitor all systems ...
... AUDIT, DETECT, and SECURE Three stages of secure process that are to be followed Provide security agents Automated Continually monitor all systems ...
Web server software
... Web server computer As of March 2014 Apache served 58% of all web servers Apache available for Microsoft Windows, Novell NetWare and Unix-like OS ...
... Web server computer As of March 2014 Apache served 58% of all web servers Apache available for Microsoft Windows, Novell NetWare and Unix-like OS ...
3460:426/526 Operating Systems
... multiprogramming systems and interacting processes: storage management; process and resource control; deadlock problem. Course is independent of any particular operating system. Detailed Description: Operating systems define a user’s view of a computer and define the environment in which programs ru ...
... multiprogramming systems and interacting processes: storage management; process and resource control; deadlock problem. Course is independent of any particular operating system. Detailed Description: Operating systems define a user’s view of a computer and define the environment in which programs ru ...
Operating Systems - Home - KSU Faculty Member websites
... internal and external attacks – Huge range, including denial-of-service, worms, viruses, identity theft, theft of service ...
... internal and external attacks – Huge range, including denial-of-service, worms, viruses, identity theft, theft of service ...
Answers to Even-numbered Exercises
... that is frequently related to the operating system. A utility is simpler than an application program, although no clear line separates the two. Linux distributions, such as Ubuntu Linux, include many utilities. You can also download many utilities from the Internet. Examples of utilities are cp (cop ...
... that is frequently related to the operating system. A utility is simpler than an application program, although no clear line separates the two. Linux distributions, such as Ubuntu Linux, include many utilities. You can also download many utilities from the Internet. Examples of utilities are cp (cop ...
eFS: encrypted File system
... information. The system is cracked while attached to a network or with some malicious software. ...
... information. The system is cracked while attached to a network or with some malicious software. ...