5-1 note
... – think of electronic storage devices as filing cabinets – use folders to make paths that make sense to you – create folders and then subfolders to group your files together ...
... – think of electronic storage devices as filing cabinets – use folders to make paths that make sense to you – create folders and then subfolders to group your files together ...
business computer and network check list
... RELIABILITY My computer works at optimal performance. It’s maintained, de-fragged, clean from temporary files. It does not have unnecessary programs slowing it down . The internet connection is reliable and does not go down I have a second internet connection for 100% up time I have clean power. Pow ...
... RELIABILITY My computer works at optimal performance. It’s maintained, de-fragged, clean from temporary files. It does not have unnecessary programs slowing it down . The internet connection is reliable and does not go down I have a second internet connection for 100% up time I have clean power. Pow ...
Heading Goes Here
... verification. The major difficulty with layered approach is careful definition of layers, because a layer can only use the layers below it Less efficient than other approaches ...
... verification. The major difficulty with layered approach is careful definition of layers, because a layer can only use the layers below it Less efficient than other approaches ...
OPERATING SYSTEMS UNIT I Syllabus: Operating Systems
... 1. Explain the various types of computer systems. 2. Explain how protection is provided for the hardware resources by the operating system. 3. What are the system components of an operating system and explain them? 4. What are the various process scheduling concepts? 5. List five services provided b ...
... 1. Explain the various types of computer systems. 2. Explain how protection is provided for the hardware resources by the operating system. 3. What are the system components of an operating system and explain them? 4. What are the various process scheduling concepts? 5. List five services provided b ...
Design of MS-DOS
... - Basis of many other Disk(based) Operating Systems. • The first personal computer DOS, called Personal Computer Disk Operating System, was developed for IBM by Microsoft Corporation. • MS retained the rights to market a Microsoft version, called MS-DOS. PC-DOS and MS-DOS are almost identical and mo ...
... - Basis of many other Disk(based) Operating Systems. • The first personal computer DOS, called Personal Computer Disk Operating System, was developed for IBM by Microsoft Corporation. • MS retained the rights to market a Microsoft version, called MS-DOS. PC-DOS and MS-DOS are almost identical and mo ...
OUTLINE - Bilkent University
... is an open source based on a microkernel architecture. Andrew S. Tanenbaum wrote the o\s to be used for educational purposes; MINIX also inspired the creation of Linux. name derives from the words minimal and UNIX. Today MINIX is not used by people. filename length limitation to 14 characters allowe ...
... is an open source based on a microkernel architecture. Andrew S. Tanenbaum wrote the o\s to be used for educational purposes; MINIX also inspired the creation of Linux. name derives from the words minimal and UNIX. Today MINIX is not used by people. filename length limitation to 14 characters allowe ...
ch2
... – Protection and security - The owners of information stored in a multiuser or networked computer system may want to control use of that information, concurrent processes should not interfere with each other • Protection involves ensuring that all access to system resources is controlled • Security ...
... – Protection and security - The owners of information stored in a multiuser or networked computer system may want to control use of that information, concurrent processes should not interfere with each other • Protection involves ensuring that all access to system resources is controlled • Security ...
Ceng 334 - Operating Systems
... second that the process has had during the past few seconds Nice is a value between –20 to 20 (default 0). Nice system call can be used to set this value 0-20 Base is a system parameter in UNIX source code The scheduler forces CPU bound (on positive queues) get any service that is left over when all ...
... second that the process has had during the past few seconds Nice is a value between –20 to 20 (default 0). Nice system call can be used to set this value 0-20 Base is a system parameter in UNIX source code The scheduler forces CPU bound (on positive queues) get any service that is left over when all ...
2. OS Components
... and the Java API for programs that run on the Java virtual machine. A programmer accesses an API via a library of code provided by the operating system. In the case of UNIX and Linux for programs written in the C language, the library is called libc. Note that—unless specified—the system-call name ...
... and the Java API for programs that run on the Java virtual machine. A programmer accesses an API via a library of code provided by the operating system. In the case of UNIX and Linux for programs written in the C language, the library is called libc. Note that—unless specified—the system-call name ...
Introduction - Stanford Secure Computer Systems Group
... - Can also watch if you miss a lecture, or to review - But resist temptation to miss a bunch of lectures and watch them all at once • SCPD students welcome to attend lecture in person - 4:15pm lecture time conveniently at end of work day - Many parking spaces don’t require permit after 4pm • Other n ...
... - Can also watch if you miss a lecture, or to review - But resist temptation to miss a bunch of lectures and watch them all at once • SCPD students welcome to attend lecture in person - 4:15pm lecture time conveniently at end of work day - Many parking spaces don’t require permit after 4pm • Other n ...
Page 1 •Program Execution •I/O Operation •File System
... Memory management. Communication via process to process messaging. ...
... Memory management. Communication via process to process messaging. ...
Operating Systems Questions
... Cambridge Tech LO1 – Operating Systems task You are to write a report that must contain the following information about operating systems. I will expect there to be examples of different operating systems used so you may want to talk about how Windows XP performs a task compared to a single task ope ...
... Cambridge Tech LO1 – Operating Systems task You are to write a report that must contain the following information about operating systems. I will expect there to be examples of different operating systems used so you may want to talk about how Windows XP performs a task compared to a single task ope ...
What is Linux? - Longwood Blogs
... As the title implies, this guide is for people who want to learn about coding in a Linux environment. Topics covered include VIM shortcuts, comparisons of Linux to other operating systems, and more. One of the topics not covered is the installation process, and so this guide is not intended for thos ...
... As the title implies, this guide is for people who want to learn about coding in a Linux environment. Topics covered include VIM shortcuts, comparisons of Linux to other operating systems, and more. One of the topics not covered is the installation process, and so this guide is not intended for thos ...
CMPT 880: Internet Architectures and Protocols
... (block 0) on the disk into memory, which loads the rest of the loader from disk, which ...
... (block 0) on the disk into memory, which loads the rest of the loader from disk, which ...
operating systems - Ronny`s Web Site
... is also called real time executive. The kernel contains all the devices that interact with the hardware. ...
... is also called real time executive. The kernel contains all the devices that interact with the hardware. ...
Slide 1
... multimedia presentation, software for handling network communication. It is common to find companies or individuals who have modified, or added to, the utility software. ...
... multimedia presentation, software for handling network communication. It is common to find companies or individuals who have modified, or added to, the utility software. ...
Operating systems. History. Function. Organization. Software
... • Alters the timer of OS – extend its own time slice and dominate the machine • Access to peripheral devices directly – access to files that otherwise access would have been denied • Access memory cells outside its allowed area, it can read and alter data from other processes ...
... • Alters the timer of OS – extend its own time slice and dominate the machine • Access to peripheral devices directly – access to files that otherwise access would have been denied • Access memory cells outside its allowed area, it can read and alter data from other processes ...
Document
... • Alters the timer of OS – extend its own time slice and dominate the machine • Access to peripheral devices directly – access to files that otherwise access would have been denied • Access memory cells outside its allowed area, it can read and alter data from other processes ...
... • Alters the timer of OS – extend its own time slice and dominate the machine • Access to peripheral devices directly – access to files that otherwise access would have been denied • Access memory cells outside its allowed area, it can read and alter data from other processes ...
Operating System Structures
... − Huge range, including denial-of-service, worms, viruses, identity theft, theft of service Systems generally first distinguish among users, to determine who can do what − User identities (user IDs, security IDs) include name and associated number, one per user − User ID then associated with all fil ...
... − Huge range, including denial-of-service, worms, viruses, identity theft, theft of service Systems generally first distinguish among users, to determine who can do what − User identities (user IDs, security IDs) include name and associated number, one per user − User ID then associated with all fil ...
Chap8.doc
... __ 1. A program that tells the computer how to calculate the correct amount to print on a paycheck is an example of system software. __ 2. DOS was a popular operating system in the past, but is no longer widely used. __ 3. A computer cannot work without an operating system. __ 4. The functions of an ...
... __ 1. A program that tells the computer how to calculate the correct amount to print on a paycheck is an example of system software. __ 2. DOS was a popular operating system in the past, but is no longer widely used. __ 3. A computer cannot work without an operating system. __ 4. The functions of an ...
Web Server Administration
... and what goes out It is best to start with a default policy that denies all traffic, in and out We can reject or drop a failed packet ...
... and what goes out It is best to start with a default policy that denies all traffic, in and out We can reject or drop a failed packet ...
JAWAHARLAL NEHRU TECHNOLOGICAL UNIVERSITY
... COLLEGE OF ENGINEERING (AUTONOMOUS) :: PULIVENDULA Operating Systems B.TECH. III Year I sem (C.S.E) ...
... COLLEGE OF ENGINEERING (AUTONOMOUS) :: PULIVENDULA Operating Systems B.TECH. III Year I sem (C.S.E) ...
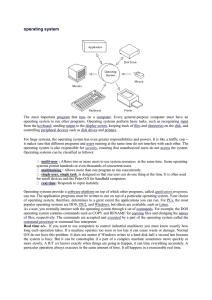
operating system
... The most important program that runs on a computer. Every general-purpose computer must have an operating system to run other programs. Operating systems perform basic tasks, such as recognizing input from the keyboard, sending output to the display screen, keeping track of files and directories on ...
... The most important program that runs on a computer. Every general-purpose computer must have an operating system to run other programs. Operating systems perform basic tasks, such as recognizing input from the keyboard, sending output to the display screen, keeping track of files and directories on ...
Sec (3.2)
... Application software: Consists of programs for performing tasks particular to machine's utilization ...
... Application software: Consists of programs for performing tasks particular to machine's utilization ...