School of Computing and Information Systems Unit Outline KXC254 Operating Systems
... Unless specifically stated in the specification of the assessment item provided on the unit website, it is required that: work submitted by a student is the work of that student alone OR where the assessment item is to be completed by a group of students, the work submitted by the group of students ...
... Unless specifically stated in the specification of the assessment item provided on the unit website, it is required that: work submitted by a student is the work of that student alone OR where the assessment item is to be completed by a group of students, the work submitted by the group of students ...
HDD for Operating System Concepts
... Education and Research Department, Infosys Technologies Limited. This document is not for general distribution and is meant for use only for the person they are specifically issued to. This document shall not be loaned to anyone, within or outside Infosys, including its customers. Copying or unautho ...
... Education and Research Department, Infosys Technologies Limited. This document is not for general distribution and is meant for use only for the person they are specifically issued to. This document shall not be loaned to anyone, within or outside Infosys, including its customers. Copying or unautho ...
3_firewall_m
... Mode or IP Masquerade) • Wherein a large group of internal clients share a single or small group of internal IP addresses for the purpose of hiding their identities or expanding the internal network address space. – Static Translation (also called Port Forwarding) • Wherein a specific internal netwo ...
... Mode or IP Masquerade) • Wherein a large group of internal clients share a single or small group of internal IP addresses for the purpose of hiding their identities or expanding the internal network address space. – Static Translation (also called Port Forwarding) • Wherein a specific internal netwo ...
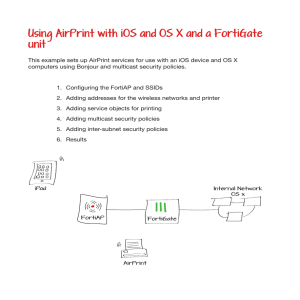
Using AirPrint with iOS and OS X and a FortiGate unit
... 2. Adding addresses for the wireless networks and printer 3. Adding service objects for printing 4. Adding multicast security policies 5. Adding inter-subnet security policies ...
... 2. Adding addresses for the wireless networks and printer 3. Adding service objects for printing 4. Adding multicast security policies 5. Adding inter-subnet security policies ...
3.basic hardware elements
... I/O SYSTEM MANAGEMENT The I/O subsystem consists of A general device driver interface Drivers for specific hardware devices ...
... I/O SYSTEM MANAGEMENT The I/O subsystem consists of A general device driver interface Drivers for specific hardware devices ...
DOS - InfoShare.tk
... The DOS kernel initializes its tables and sets up various work areas. It sets up the interrupt vector table. It then loads and executes the device drivers. These driver function determine device status, perform necessary hardware initialization and set up vectors for any external hardware interrupts ...
... The DOS kernel initializes its tables and sets up various work areas. It sets up the interrupt vector table. It then loads and executes the device drivers. These driver function determine device status, perform necessary hardware initialization and set up vectors for any external hardware interrupts ...
Curriculum Vitae - ASU People Search
... Solved catch the flag challenges including directory traversal, buffer overflow and Path based vulnerabilities. ...
... Solved catch the flag challenges including directory traversal, buffer overflow and Path based vulnerabilities. ...
Emerging Threats to Business Security
... (stolen bank accounts usually get "cleaned out" within hours or days). The most common type of phishing spam is based on threats to terminate the account being phished, while a second common variation is to ask a customer to enter their account info to "update the banking security app". The template ...
... (stolen bank accounts usually get "cleaned out" within hours or days). The most common type of phishing spam is based on threats to terminate the account being phished, while a second common variation is to ask a customer to enter their account info to "update the banking security app". The template ...
Introduction to Operating Systems
... Unix used to share research and data (foundation of the Internet and the WWW) Linus Torvalds orchestrated development of an operating system based on Unix, but able to operate on microprocessor platforms – Linux (1991) Lesson 8 – Linux ...
... Unix used to share research and data (foundation of the Internet and the WWW) Linus Torvalds orchestrated development of an operating system based on Unix, but able to operate on microprocessor platforms – Linux (1991) Lesson 8 – Linux ...
15 - Portland State University
... How to prevent CPU throughput from being limited by I/O device speed (for slow devices) Why would slow devices affect the CPU? How to prevent I/O throughput from being limited by CPU speed (for fast devices) Why would device throughput be limited by the CPU? ...
... How to prevent CPU throughput from being limited by I/O device speed (for slow devices) Why would slow devices affect the CPU? How to prevent I/O throughput from being limited by CPU speed (for fast devices) Why would device throughput be limited by the CPU? ...
csci19f2
... • Raid level 2 requires synchronized drives • Reading is very fast as all drives can transfer data (portions of the file). In one sector reading time n (number of drives) sectors are read in • Writing is slower because of parity information (to write parity all requests must access this drive) CS19D ...
... • Raid level 2 requires synchronized drives • Reading is very fast as all drives can transfer data (portions of the file). In one sector reading time n (number of drives) sectors are read in • Writing is slower because of parity information (to write parity all requests must access this drive) CS19D ...
網路犯罪案例 Cyber crime Case
... host hidden within a Taiwan Academic Network. The use of Trojan horse programs, together with web site vulnerabilities against well-known Web sites were used to harvest intrusive information and then, to circumvent tracing, stored this data on a foreign hosted website. Xx telecom companies user acco ...
... host hidden within a Taiwan Academic Network. The use of Trojan horse programs, together with web site vulnerabilities against well-known Web sites were used to harvest intrusive information and then, to circumvent tracing, stored this data on a foreign hosted website. Xx telecom companies user acco ...
module_70
... A firewall can be used to deny access to a specific host or a specific service in the organization. ...
... A firewall can be used to deny access to a specific host or a specific service in the organization. ...
PPT Chapter 13
... • Hash table directory efficient search – Hash with open addressing requires a single table – (Sometimes) at most two comparisons needed to locate a file – Cumbersome to change size, or to delete an entry ...
... • Hash table directory efficient search – Hash with open addressing requires a single table – (Sometimes) at most two comparisons needed to locate a file – Cumbersome to change size, or to delete an entry ...
Hardware and Software
... – word processing packages – spreadsheet packages – database packages – presentation packages ...
... – word processing packages – spreadsheet packages – database packages – presentation packages ...
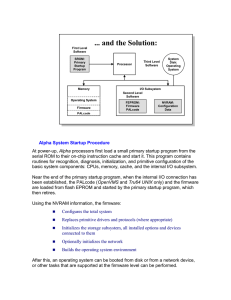
Alpha System Startup Procedure
... Near the end of the primary startup program, when the internal I/O connection has been established, the PALcode (OpenVMS and Tru64 UNIX only) and the firmware are loaded from flash EPROM and started by the primary startup program, which then retires. Using the NVRAM information, the firmware: ...
... Near the end of the primary startup program, when the internal I/O connection has been established, the PALcode (OpenVMS and Tru64 UNIX only) and the firmware are loaded from flash EPROM and started by the primary startup program, which then retires. Using the NVRAM information, the firmware: ...
18_DataCenter_Security_Overview
... •Eavesdropping - is the unauthorized interception of information that travels on the network, this information might contain confidential data such as username and password. Another example is packet capturing. •Viruses & Worms – both cases of malicious code, hidden in the system until the damage is ...
... •Eavesdropping - is the unauthorized interception of information that travels on the network, this information might contain confidential data such as username and password. Another example is packet capturing. •Viruses & Worms – both cases of malicious code, hidden in the system until the damage is ...
18_DataCenter_Security_Overview
... •Eavesdropping - is the unauthorized interception of information that travels on the network, this information might contain confidential data such as username and password. Another example is packet capturing. •Viruses & Worms – both cases of malicious code, hidden in the system until the damage is ...
... •Eavesdropping - is the unauthorized interception of information that travels on the network, this information might contain confidential data such as username and password. Another example is packet capturing. •Viruses & Worms – both cases of malicious code, hidden in the system until the damage is ...
ISEC0511
... Usage constraints on objects based on security level or privilege of the subject. This attribute is also called fine-grained access control or role-based security. ...
... Usage constraints on objects based on security level or privilege of the subject. This attribute is also called fine-grained access control or role-based security. ...
Ch. 4 Operating System Fundamentals
... are software programs that control thousands of operations, provide an interface between the user and the computer, and run applications. • An OS is designed to control the operations of programs such as web browsers, word processors, and e-mail programs. ...
... are software programs that control thousands of operations, provide an interface between the user and the computer, and run applications. • An OS is designed to control the operations of programs such as web browsers, word processors, and e-mail programs. ...
Taking Control of Advanced Threats
... “Next-generation network IPS will be incorporated within a next-generation firewall, but most nextgeneration firewall products currently include firstgeneration IPS capabilities.“ Source: “Defining Next-Generation Network Intrusion Prevention,” Gartner, October 7, 2011. “Defining the Next-Generation ...
... “Next-generation network IPS will be incorporated within a next-generation firewall, but most nextgeneration firewall products currently include firstgeneration IPS capabilities.“ Source: “Defining Next-Generation Network Intrusion Prevention,” Gartner, October 7, 2011. “Defining the Next-Generation ...
Operating Systems Sample Exam Questions and Answers Tommy Sailing
... - Theoretically greater performance, as the OS does not need to perform expensive context switches every time a thread changes. - More configurable, as you are not tied to the kernel to decide a scheduling algorithm, nor do you require kernel support for multiple threads. Disadvantages of user-level ...
... - Theoretically greater performance, as the OS does not need to perform expensive context switches every time a thread changes. - More configurable, as you are not tied to the kernel to decide a scheduling algorithm, nor do you require kernel support for multiple threads. Disadvantages of user-level ...
Windows Server 2008 - Dr. Edward E. Boas, Jr., Professor
... owned by the user lpadron: – find /usr –user lpadron ...
... owned by the user lpadron: – find /usr –user lpadron ...