Slides
... • Referring to the fact that physical systems can be modeled using well-understood physical laws, Department of Homeland Security (DHS) Best Practices state that “The deterministic nature of the engineering systems can greatly improve the granularity of the signatures, because rogue or malicious beh ...
... • Referring to the fact that physical systems can be modeled using well-understood physical laws, Department of Homeland Security (DHS) Best Practices state that “The deterministic nature of the engineering systems can greatly improve the granularity of the signatures, because rogue or malicious beh ...
Networks - ZSIS-ITGS
... you. You may not know which ones or how, but the fact that you are, means that you should be concerned about the Security of your personal details as well as how it is being protected. A good example would be banking. There are probably no banks in existence that keep their customer’s data on paper ...
... you. You may not know which ones or how, but the fact that you are, means that you should be concerned about the Security of your personal details as well as how it is being protected. A good example would be banking. There are probably no banks in existence that keep their customer’s data on paper ...
Computing Systems Division
... User no longer had ANY direct contact with the computer (everything done via submission of jobs to operator who actually used the computer) Reduce setup time by loading jobs together that have similar requirements e.g. all jobs that need compiler loaded together – known as batching (set of similar j ...
... User no longer had ANY direct contact with the computer (everything done via submission of jobs to operator who actually used the computer) Reduce setup time by loading jobs together that have similar requirements e.g. all jobs that need compiler loaded together – known as batching (set of similar j ...
ICS 143 - Introduction to Operating Systems
... Control card interpreter replaced by command language interpreter. ...
... Control card interpreter replaced by command language interpreter. ...
2007-06.pdf
... Creating a software drive is nothing but creating the means such that other tools can access data as if it where placed on a real drive. The equivalent in UNIX is actually creating a mount point. 7b What does mounting the CD ISO image actually establish in Windows? By mounting the ISO image, we have ...
... Creating a software drive is nothing but creating the means such that other tools can access data as if it where placed on a real drive. The equivalent in UNIX is actually creating a mount point. 7b What does mounting the CD ISO image actually establish in Windows? By mounting the ISO image, we have ...
LSD1518 - Control Cloud Data Access Privilege
... schemes based on the attribute-based encryption have been proposed to secure the cloud storage. However, most work focuses on the data contents privacy and the access control, while less attention is paid to the privilege control and the identity privacy. In this paper, we present a semi-anonymous p ...
... schemes based on the attribute-based encryption have been proposed to secure the cloud storage. However, most work focuses on the data contents privacy and the access control, while less attention is paid to the privilege control and the identity privacy. In this paper, we present a semi-anonymous p ...
Orange Earth - Central Ohio ISSA
... • Audit trails are whatever the application developer built in, so they are both application-specific and limited in scope • What data needs to be logged for security analytics purposes? • What should be the log format for business v. security logs? • Do we need to store the security logs in a diffe ...
... • Audit trails are whatever the application developer built in, so they are both application-specific and limited in scope • What data needs to be logged for security analytics purposes? • What should be the log format for business v. security logs? • Do we need to store the security logs in a diffe ...
COS 318: Operating Systems OS Structures and System Calls Andy Bavier
... Change processor modes from kernel to user Change the voltage and frequency of processor Halt a processor Reset a processor Perform I/O operations ...
... Change processor modes from kernel to user Change the voltage and frequency of processor Halt a processor Reset a processor Perform I/O operations ...
ppt
... What are the main sources of overhead in microkernel based OSs compared to monolithic OSs? How does L3 address these overheads? o ...
... What are the main sources of overhead in microkernel based OSs compared to monolithic OSs? How does L3 address these overheads? o ...
Figure 15.1 A distributed multimedia system
... into thinking that the collection of machines is simply an old-fashioned time-sharing system, instead of a collection of independent components. The transparency is generally preferable for any DS. It also should be considered together with other issues such as performance. ...
... into thinking that the collection of machines is simply an old-fashioned time-sharing system, instead of a collection of independent components. The transparency is generally preferable for any DS. It also should be considered together with other issues such as performance. ...
Slide - Courses
... Some incidents may occur on a SAN or large servers with special complications Cannot go offline OR They have so much storage that it cannot be successfully imaged (or have RAID, so an image will be technically infeasible) ...
... Some incidents may occur on a SAN or large servers with special complications Cannot go offline OR They have so much storage that it cannot be successfully imaged (or have RAID, so an image will be technically infeasible) ...
Operating Systems and Using Linux
... where # is the number of the Linux server that you have connected to. You may use any of the Linux servers. • The number in the brackets will change as you work. It is the “number” of the command that you are about to type. • If this prompt is not on the screen at any time, you are not communicating ...
... where # is the number of the Linux server that you have connected to. You may use any of the Linux servers. • The number in the brackets will change as you work. It is the “number” of the command that you are about to type. • If this prompt is not on the screen at any time, you are not communicating ...
Introduction to Programming Methodology Notes
... place, a bank account, a table of data or any item that the program has to handle. They may also represent user-defined data such as vectors, time and lists. Programming problem is analyzed in terms of objects and the nature of communication between them. Program objects should be chosen such that t ...
... place, a bank account, a table of data or any item that the program has to handle. They may also represent user-defined data such as vectors, time and lists. Programming problem is analyzed in terms of objects and the nature of communication between them. Program objects should be chosen such that t ...
CS3204 Operating Systems - Spring 2001 Instructor: Dr. Craig A
... where is the file containing the error (input or job file), is the line number
in the file containing the error, and is a message describing the error
that occurred.
You may assume that each line of the input and job files corresponds to a command,
however, the commands ...
... where
PowerPoint 프레젠테이션 - POSTECH CSE DPNM
... • Virtual (distributed) shared memory requires OS to maintain global memory map in software • Inherent distributed resource management: no central point where allocation decisions can be made Practice: Only very few truly multicomputer operating systems exist (example: Amoeba) ...
... • Virtual (distributed) shared memory requires OS to maintain global memory map in software • Inherent distributed resource management: no central point where allocation decisions can be made Practice: Only very few truly multicomputer operating systems exist (example: Amoeba) ...
slides
... Definition: A root kit is a collection of trojans to replace widely used system utility programs in order to conceal the activities of an intruder. Example: You break into a system, you upload some files and install services to create a backdoor. The system administrator can find evidence of your in ...
... Definition: A root kit is a collection of trojans to replace widely used system utility programs in order to conceal the activities of an intruder. Example: You break into a system, you upload some files and install services to create a backdoor. The system administrator can find evidence of your in ...
ch18
... The system libraries define a standard set of functions through which applications interact with the kernel, and which implement much of the operating-system functionality that does not need the full privileges of kernel code ...
... The system libraries define a standard set of functions through which applications interact with the kernel, and which implement much of the operating-system functionality that does not need the full privileges of kernel code ...
slides - Embedded System and Wireless Networking Lab National
... the number of general-purpose processors used. Single-processor systems: There is one main CPU capable of executing a ...
... the number of general-purpose processors used. Single-processor systems: There is one main CPU capable of executing a ...
Quick History of Open Source
... Microsoft), people thru-out the world work on Linux (and other open software) as a team • Linux is sort of notorious with Computer Security experts. Since the source is all available, hackers are able to break in sometimes. But this is often due to people running Linux who do not really understand n ...
... Microsoft), people thru-out the world work on Linux (and other open software) as a team • Linux is sort of notorious with Computer Security experts. Since the source is all available, hackers are able to break in sometimes. But this is often due to people running Linux who do not really understand n ...
Document
... operating system to perform some additional tasks, such as searching and printing the files and scanning the viruses, etc. A utility program is not an essential part of an operating system, because it does not help the operating system in the execution of a command or a program. A utility program on ...
... operating system to perform some additional tasks, such as searching and printing the files and scanning the viruses, etc. A utility program is not an essential part of an operating system, because it does not help the operating system in the execution of a command or a program. A utility program on ...
Test1: Spring 2017 (Hint)
... Or, Q3B. A DMA scheme provides one approach to do I/O by device controllers. What is DMA? How is it distinguished from the other possible ways of doing I/O? Ans. A DMA is used when a device controller directly dumps input from an external source into a specific location in RAM, or directly output fr ...
... Or, Q3B. A DMA scheme provides one approach to do I/O by device controllers. What is DMA? How is it distinguished from the other possible ways of doing I/O? Ans. A DMA is used when a device controller directly dumps input from an external source into a specific location in RAM, or directly output fr ...
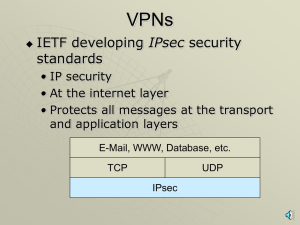
VPNs, PKIs, ISSs, SSLs with narration
... • Webserver authenticates itself • Browser may authenticate itself but rarely does • Browser selects a symmetric session key, sends to webserver • Adds a digital signature and encrypts all messages with the symmetric key ...
... • Webserver authenticates itself • Browser may authenticate itself but rarely does • Browser selects a symmetric session key, sends to webserver • Adds a digital signature and encrypts all messages with the symmetric key ...