Foundations of Information Security Webcast - ABA
... The technology must be put in place to manage and enforce security Management commitment is not difficult… if Metrics: If you can’t measure it, you can’t control it Information security bridges the business and the technology ...
... The technology must be put in place to manage and enforce security Management commitment is not difficult… if Metrics: If you can’t measure it, you can’t control it Information security bridges the business and the technology ...
CIS 203 Artificial Intelligence
... I feel that this topic suits my experiences just fine. I have a Network Administration Certificate, so I do have some familiarity with Networking in general. As for having specific knowledge of the involvement of AI in solving problems with Network Securities, I can't say the same is true. However, ...
... I feel that this topic suits my experiences just fine. I have a Network Administration Certificate, so I do have some familiarity with Networking in general. As for having specific knowledge of the involvement of AI in solving problems with Network Securities, I can't say the same is true. However, ...
TrendMicro Titanium - A New Concept in Security by Ira Wilsker
... clicking on the Tools button. Some of the other features accessible in this manner are a Secure Erase utility, Data Theft Prevention, Trend Micro Vault, and a Free Tool Center. The Parental Controls utility is intended to protect children from inappropriate websites, control access and online time, ...
... clicking on the Tools button. Some of the other features accessible in this manner are a Secure Erase utility, Data Theft Prevention, Trend Micro Vault, and a Free Tool Center. The Parental Controls utility is intended to protect children from inappropriate websites, control access and online time, ...
Computersikkerhed
... Program security Operating systems Data base security Security in network and distributed systems Administration of security Legal and ethical security ...
... Program security Operating systems Data base security Security in network and distributed systems Administration of security Legal and ethical security ...
Information System Security
... systems and the information transfers of an organization • intended to counter security attacks • make use of one or more security mechanisms to provide the service • replicate functions normally associated with physical documents • eg have signatures, dates; need protection from disclosure, tamperi ...
... systems and the information transfers of an organization • intended to counter security attacks • make use of one or more security mechanisms to provide the service • replicate functions normally associated with physical documents • eg have signatures, dates; need protection from disclosure, tamperi ...
20121101
... • The initial system/user didn’t have adequate access for their needs so they needed to take a step to another system to go further. ...
... • The initial system/user didn’t have adequate access for their needs so they needed to take a step to another system to go further. ...
HIPAA Security Standards
... implemented in both hardware and software, or a combination of both. Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets. All messages entering or leaving the intranet pass through the firewall, which ex ...
... implemented in both hardware and software, or a combination of both. Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets. All messages entering or leaving the intranet pass through the firewall, which ex ...
CS5038: The Electronic Society - Homepages | The University of
... • How to implement? – Technological enforcement? – Policy enforcement? • What are the barriers? • The major problem, identified by extensive empirical study (structured interviews, etc.) is a social one: – Bankers don’t like being embarrassed in front of clients, , losing face and maybe losing busin ...
... • How to implement? – Technological enforcement? – Policy enforcement? • What are the barriers? • The major problem, identified by extensive empirical study (structured interviews, etc.) is a social one: – Bankers don’t like being embarrassed in front of clients, , losing face and maybe losing busin ...
Overview of Database Security
... damage permanently and often irreparably the environment where it gets reproduced ...
... damage permanently and often irreparably the environment where it gets reproduced ...
Curriculum Vitae - ASU People Search
... Solved catch the flag challenges including directory traversal, buffer overflow and Path based vulnerabilities. ...
... Solved catch the flag challenges including directory traversal, buffer overflow and Path based vulnerabilities. ...
DOCSpec
... Compare and Contrast the 3 platforms J2EE, .NET, and CORBA. Evaluate the three in 4 areas: databases, security, web services, and parallel processing/multi-threading. GOAL: To determine in which areas J2EE or .NET is better suited to be used. Also to determine in which areas CORBA can be beneficial. ...
... Compare and Contrast the 3 platforms J2EE, .NET, and CORBA. Evaluate the three in 4 areas: databases, security, web services, and parallel processing/multi-threading. GOAL: To determine in which areas J2EE or .NET is better suited to be used. Also to determine in which areas CORBA can be beneficial. ...
Chapter 10: Electronic Commerce Security
... opportunities for criminals to steal? How? Why are some online merchants hesitant to ship to international addresses? What are some steps a company can take to thwart cybercriminals from within a business? Is a computer with anti-virus software protected from viruses? Why or why not? What ar ...
... opportunities for criminals to steal? How? Why are some online merchants hesitant to ship to international addresses? What are some steps a company can take to thwart cybercriminals from within a business? Is a computer with anti-virus software protected from viruses? Why or why not? What ar ...
Chapter 1
... The challenge is to develop operating systems which can share information without allowing this behavior. ...
... The challenge is to develop operating systems which can share information without allowing this behavior. ...
Importance of SETA programs
... confidentiality, and availability of information in today’s highly networked system environment without ensuring that each person involved understand their roles and responsibilities and is adequately trained to perform them” ...
... confidentiality, and availability of information in today’s highly networked system environment without ensuring that each person involved understand their roles and responsibilities and is adequately trained to perform them” ...
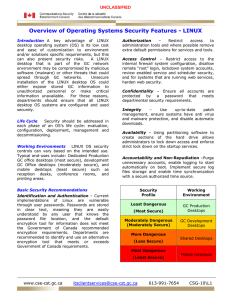
Overview of Operating Systems Security Features
... environment may be compromised by malicious software (malware) or other threats that could spread through GC networks. Unsecure installation of the LINUX desktop OS could either expose stored GC information to unauthorized personnel or make critical information unavailable. For these reasons, depart ...
... environment may be compromised by malicious software (malware) or other threats that could spread through GC networks. Unsecure installation of the LINUX desktop OS could either expose stored GC information to unauthorized personnel or make critical information unavailable. For these reasons, depart ...
diebold nixdorf software terminal security intrusion protection
... No financial services provider is safe from the viruses, malware and Trojans that infiltrate or are covertly installed on self-service environments. In fact, reports on new variants of ATM malware are published every few months. Recently, security experts discovered that the infamous Ploutus malware ...
... No financial services provider is safe from the viruses, malware and Trojans that infiltrate or are covertly installed on self-service environments. In fact, reports on new variants of ATM malware are published every few months. Recently, security experts discovered that the infamous Ploutus malware ...
Fundamentals of Computer Security
... Majority of information security incidents is perpetrated by insiders i.e. internal computer users constitute the largest threat to the computer systems security[2]. Traditional methods (such as identification and authentication, access restriction, etc.) do not solve this problem Drawbacks; among t ...
... Majority of information security incidents is perpetrated by insiders i.e. internal computer users constitute the largest threat to the computer systems security[2]. Traditional methods (such as identification and authentication, access restriction, etc.) do not solve this problem Drawbacks; among t ...
Course name Code/No Units Credit Units Prerequisite Lecture Lab
... To discuss the important of system and network security To explain the relationship between threats, vulnerabilities, countermeasures, attacks, compromises and remediation. To describe of how to manage information security. To explain the encryption technologies. To explain about the privacy and acc ...
... To discuss the important of system and network security To explain the relationship between threats, vulnerabilities, countermeasures, attacks, compromises and remediation. To describe of how to manage information security. To explain the encryption technologies. To explain about the privacy and acc ...
PowerPoint Presentation - IF-MAP
... • More Informed Sensors – Sensors can tune by role and other things – Should reduce false alarms ...
... • More Informed Sensors – Sensors can tune by role and other things – Should reduce false alarms ...
Computer Security Presentation
... administrator has to get everything right all the time; a hacker only has to find one small hole. A sysadmin has to be lucky all of the time; a hacker only has to get lucky once. It is easier to destroy than to create.” – Robert Graham, lead architect of Internet ...
... administrator has to get everything right all the time; a hacker only has to find one small hole. A sysadmin has to be lucky all of the time; a hacker only has to get lucky once. It is easier to destroy than to create.” – Robert Graham, lead architect of Internet ...
john p. carlin - AFCEA International
... Homeland Security Project, focused on the unique challenges and choices around protecting the American homeland. He also chairs the Aspen Institute’s Cybersecurity and Technology policy program, which provides a cross-disciplinary forum for industry, government, and media to address the rapidly deve ...
... Homeland Security Project, focused on the unique challenges and choices around protecting the American homeland. He also chairs the Aspen Institute’s Cybersecurity and Technology policy program, which provides a cross-disciplinary forum for industry, government, and media to address the rapidly deve ...
Airport security
Airport security refers to the techniques and methods used in protecting passengers, staff and aircraft which use the airports from accidental/malicious harm, crime and other threats.