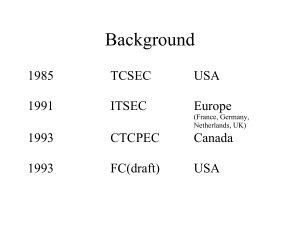
WelcometoCISandCybercorps
... Safety, reliability and security. Specification of mission critical system properties. Software and hardware validation, verification and certification. Enterprise Security Management: Security architecture design and implementation methodologies for enterprises. Risk management, policy development, ...
... Safety, reliability and security. Specification of mission critical system properties. Software and hardware validation, verification and certification. Enterprise Security Management: Security architecture design and implementation methodologies for enterprises. Risk management, policy development, ...
10.2 BASIC E-COMMERCE SECURITY ISSUES AND LANDSCAPE
... Availability: The assurance that access to any relevant data, information websites, or other EC services and their use is available in real time, whenever and wherever needed. ...
... Availability: The assurance that access to any relevant data, information websites, or other EC services and their use is available in real time, whenever and wherever needed. ...
Slide 1
... Project Agency (ARPA) of the U.S. government in 1969 and was known as ARPAnet. It was designed to enable U.S. military leaders to stay in contact in case of a nuclear war. The protocol used in ARPAnet was called Network Control Protocol (NCP). The protocol had too many limitations and was not robust ...
... Project Agency (ARPA) of the U.S. government in 1969 and was known as ARPAnet. It was designed to enable U.S. military leaders to stay in contact in case of a nuclear war. The protocol used in ARPAnet was called Network Control Protocol (NCP). The protocol had too many limitations and was not robust ...
XML Security Standards — Overview for the Non - Events
... Key problem: Immaterial changes to XML documents Solution: Canonicalization Defines rules to encrypt XML and record parameters Support all technologies in common use Key problem: Encrypted data not Schema-valid Solution: None ...
... Key problem: Immaterial changes to XML documents Solution: Canonicalization Defines rules to encrypt XML and record parameters Support all technologies in common use Key problem: Encrypted data not Schema-valid Solution: None ...
monitor
... Application Software Security Neutralize vulnerabilities in web-based and other application software • Carefully test all application software for security flaws • Coding errors, malware ...
... Application Software Security Neutralize vulnerabilities in web-based and other application software • Carefully test all application software for security flaws • Coding errors, malware ...
us-16-Price-Building-a-Product-Security-Incident
... • What Leadership needs to know about business risk • What Customers need to know about product security • DOCUMENT at time of investigation even if you don’t use the data until much later ...
... • What Leadership needs to know about business risk • What Customers need to know about product security • DOCUMENT at time of investigation even if you don’t use the data until much later ...
Protecting Valuable Physical Assets in a High Traffic Setting
... A public facility, such as an airport, must manage multiple entrances and security access points and identify the best solution for each one. For years, the Roanoke Regional Airport Commission in Roanoke, Va., used a combination of electronic card reader door locks and standard padlocks to guard sen ...
... A public facility, such as an airport, must manage multiple entrances and security access points and identify the best solution for each one. For years, the Roanoke Regional Airport Commission in Roanoke, Va., used a combination of electronic card reader door locks and standard padlocks to guard sen ...
Network Infrastructure Security
... retrieval of programs and data used by a group of people. LAN software and practices also need to provide for the security of these programs and data. ...
... retrieval of programs and data used by a group of people. LAN software and practices also need to provide for the security of these programs and data. ...
2014 IIEG Fall Conference – MEC Presentation
... • The Federal Regulatory Energy Commission (FERC) has authority for the development, review and enforcement of mandatory reliability and security standards of the bulk electric system. • FERC approved the North American Electric Corporation (NERC) as the electric reliability organization to develop ...
... • The Federal Regulatory Energy Commission (FERC) has authority for the development, review and enforcement of mandatory reliability and security standards of the bulk electric system. • FERC approved the North American Electric Corporation (NERC) as the electric reliability organization to develop ...
Chap013
... Backup Files – duplicate files of data or programs Security Monitors – monitor systems for unauthorized use, fraud, and destruction Biometric Security – measure/verify an individual’s physical traits ...
... Backup Files – duplicate files of data or programs Security Monitors – monitor systems for unauthorized use, fraud, and destruction Biometric Security – measure/verify an individual’s physical traits ...
Chapter 14 Network Security - Cambridge Regional College
... • E-mail users think they have the same expectation of privacy when sending e-mail as they do when sending a letter through the postal service. • A more accurate expectation would be to assume that the email is like a postcard that can be read by anyone who handles it during its journey from sender ...
... • E-mail users think they have the same expectation of privacy when sending e-mail as they do when sending a letter through the postal service. • A more accurate expectation would be to assume that the email is like a postcard that can be read by anyone who handles it during its journey from sender ...
Lecture 8 - Bhecker.com
... • Spoofing and Sniffers • Denial of Service (DoS) Attacks • Identity theft ...
... • Spoofing and Sniffers • Denial of Service (DoS) Attacks • Identity theft ...
Chapter 14 Network Security - Northern Arizona University
... – Keys no longer have to be distributed – Key control lists no longer have to be maintained – Combinations can also be reset when needed • The one drawback to this model is that it is very easy to share a combination with someone not authorized. • Card readers are the most common of the access contr ...
... – Keys no longer have to be distributed – Key control lists no longer have to be maintained – Combinations can also be reset when needed • The one drawback to this model is that it is very easy to share a combination with someone not authorized. • Card readers are the most common of the access contr ...
Chapter 14 Network Security
... – Keys no longer have to be distributed – Key control lists no longer have to be maintained – Combinations can also be reset when needed • The one drawback to this model is that it is very easy to share a combination with someone not authorized. • Card readers are the most common of the access contr ...
... – Keys no longer have to be distributed – Key control lists no longer have to be maintained – Combinations can also be reset when needed • The one drawback to this model is that it is very easy to share a combination with someone not authorized. • Card readers are the most common of the access contr ...
Overview of IT Security at Nottingham
... Decided these were not suitable for the wide range of research traffic on our network (which can break firewalls) Discovered the alternative approach of anomaly detection! It learns what is normal network behaviour for each computer on the network and alerts to significant changes in that beha ...
... Decided these were not suitable for the wide range of research traffic on our network (which can break firewalls) Discovered the alternative approach of anomaly detection! It learns what is normal network behaviour for each computer on the network and alerts to significant changes in that beha ...
Information Assurance Awareness, Training, Education at the U.S.
... Communicate security requirements • Policy, rules of behavior ...
... Communicate security requirements • Policy, rules of behavior ...
Designing Trusted Operating Systems Operating Systems
... “secure”? Or “trustworthy? How are trusted systems designed, and which of those design principles carry over naturally to other program development tasks? How do we develop “assurance” of the correctness of a trusted operating systems? ...
... “secure”? Or “trustworthy? How are trusted systems designed, and which of those design principles carry over naturally to other program development tasks? How do we develop “assurance” of the correctness of a trusted operating systems? ...
Network Security Overview
... service to intended users. It usually involves either crashing the system or slowing it down to the point where it is unusable. But DoS can also be as simple as wiping out or corrupting information necessary for business. In most cases, performing the attack simply involves running a hack, script, o ...
... service to intended users. It usually involves either crashing the system or slowing it down to the point where it is unusable. But DoS can also be as simple as wiping out or corrupting information necessary for business. In most cases, performing the attack simply involves running a hack, script, o ...
FireWall-1 - Evolution Security Systems Ltd
... and peer-to-peer applications even when they are running on commonly used ports. Truly the basis for a security infrastructure, you can extend Web application and CIFS security to include single sign-on with an optional UserAuthority Module. Protection Against Network and Application Threats In toda ...
... and peer-to-peer applications even when they are running on commonly used ports. Truly the basis for a security infrastructure, you can extend Web application and CIFS security to include single sign-on with an optional UserAuthority Module. Protection Against Network and Application Threats In toda ...
FEARLESS - Cyber Security Research and Education Institute
... – Patent pending technology on virtualization security – VMware has expressed interest in licensing; 70K gift from VMware for further development SNOD – Stream-based Novel Class Detection • Patent pending technology jointly by Dr. Latifur Khan and Dr. Jiawei Han (UIUC) • System being developed aroun ...
... – Patent pending technology on virtualization security – VMware has expressed interest in licensing; 70K gift from VMware for further development SNOD – Stream-based Novel Class Detection • Patent pending technology jointly by Dr. Latifur Khan and Dr. Jiawei Han (UIUC) • System being developed aroun ...
Enhancing the Security and Capacity of Collaborative Software for
... groupware for first responder”. The idea is to design a framework for enhancing the security, effectness, and capacity of the collaborative software tools for first responders and large task forces. An application of such framework will be enhancing some existing instant messenger and decision suppo ...
... groupware for first responder”. The idea is to design a framework for enhancing the security, effectness, and capacity of the collaborative software tools for first responders and large task forces. An application of such framework will be enhancing some existing instant messenger and decision suppo ...
Bandura® Releases REACT™ Software to Integrate Internal
... Bandura® Releases REACT™ Software to Integrate Internal Network Threat Intelligence into PoliWall® REACT Enhances PoliWall’s Easy‐to‐Use, Automated Threat‐Blocking System ...
... Bandura® Releases REACT™ Software to Integrate Internal Network Threat Intelligence into PoliWall® REACT Enhances PoliWall’s Easy‐to‐Use, Automated Threat‐Blocking System ...
Airport security
Airport security refers to the techniques and methods used in protecting passengers, staff and aircraft which use the airports from accidental/malicious harm, crime and other threats.