Network Security For Distributed Simulation Systems
... simulators on the network Initially developed for military systems - use ATM private networks Many civil applications - use Internet, lack security Use Internet Protocol Security (IPSEC) end-to-end mechanism for protecting data using tunneling Alternatively use a virtual private network (simulat ...
... simulators on the network Initially developed for military systems - use ATM private networks Many civil applications - use Internet, lack security Use Internet Protocol Security (IPSEC) end-to-end mechanism for protecting data using tunneling Alternatively use a virtual private network (simulat ...
Document
... encryption keys, operates by passively monitoring transmissions, computing the encryption key when enough packets have been ...
... encryption keys, operates by passively monitoring transmissions, computing the encryption key when enough packets have been ...
Slide 1
... switched network • Upgrade to support Gbit/s to desktop in next 2-3 years • Many switches now reaching end of life already off maintenance, need replacing • Need to clarify funding for non scientific needs: – Projects move in and out of buildings (SLD=>BaBar=>GLAST=>…) – Multiple projects share buil ...
... switched network • Upgrade to support Gbit/s to desktop in next 2-3 years • Many switches now reaching end of life already off maintenance, need replacing • Need to clarify funding for non scientific needs: – Projects move in and out of buildings (SLD=>BaBar=>GLAST=>…) – Multiple projects share buil ...
Intrusion Detection Systems
... one's source IP address. It is the act of using one machine to impersonate another. Many applications and tools in UNIX systems rely on source IP address authentication. ARP spoofing - ARP spoofing involves forging packet source hardware address (MAC address) to the address of the host you pretend t ...
... one's source IP address. It is the act of using one machine to impersonate another. Many applications and tools in UNIX systems rely on source IP address authentication. ARP spoofing - ARP spoofing involves forging packet source hardware address (MAC address) to the address of the host you pretend t ...
An Ultra-Low Power Asynchronous-Logic In-Situ Self
... Proposed Idea for Low Power Design Signal processor accounts for ~50% of total power consumption ...
... Proposed Idea for Low Power Design Signal processor accounts for ~50% of total power consumption ...
Wireless and Mobile Networks
... Single hop Base station connected to larger wired network (e.g., WiFi wireless LAN, and cellular telephony networks) Multi-hop Base station exists, but some nodes must relay through other nodes (e.g., wireless sensor networks, and wireless mesh networks) ...
... Single hop Base station connected to larger wired network (e.g., WiFi wireless LAN, and cellular telephony networks) Multi-hop Base station exists, but some nodes must relay through other nodes (e.g., wireless sensor networks, and wireless mesh networks) ...
Network Environments
... Software held centrally and shared. Server manages distribution of data and software to clients. Some processing may be handled locally but most done by file server. More speed and power but additional cost and complication. ...
... Software held centrally and shared. Server manages distribution of data and software to clients. Some processing may be handled locally but most done by file server. More speed and power but additional cost and complication. ...
William Stallings, Cryptography and Network Security 4/e
... Chapter 16 – IP Security If a secret piece of news is divulged by a spy before the time is ripe, he must be put to death, together with the man to whom the ...
... Chapter 16 – IP Security If a secret piece of news is divulged by a spy before the time is ripe, he must be put to death, together with the man to whom the ...
William Stallings, Cryptography and Network Security 4/e
... Chapter 16 – IP Security If a secret piece of news is divulged by a spy before the time is ripe, he must be put to death, together with the man to whom the ...
... Chapter 16 – IP Security If a secret piece of news is divulged by a spy before the time is ripe, he must be put to death, together with the man to whom the ...
2. Network Media
... A wireless network may consist of as few as two devices Access Point Central hub for WLAN It is hard wired to the cabled LAN to provide Internet access and connectivity to the wired network. Equipped with antennae and provide wireless connectivity over a specified area referred to as a cell. ...
... A wireless network may consist of as few as two devices Access Point Central hub for WLAN It is hard wired to the cabled LAN to provide Internet access and connectivity to the wired network. Equipped with antennae and provide wireless connectivity over a specified area referred to as a cell. ...
5th Chapter - information systems and it audit
... • Key Elements of Encryption Systems Encryption Algorithm Encryption Keys Key Length ...
... • Key Elements of Encryption Systems Encryption Algorithm Encryption Keys Key Length ...
INTRODUCTION TO INFORMATION SYSTEMS TECHNOLOGY
... Highly vulnerable to snooping Limited distance Blocked by thick objects ...
... Highly vulnerable to snooping Limited distance Blocked by thick objects ...
The protocol
... (under study by Tesla) could be used to transfer energy between locations without a physical connection. •Guglielmo Marconi began work in 1894 to reproduce the Hertz laboratory experiment over greater distances. His study and efforts brought about the first radio link in the form of wireless telegra ...
... (under study by Tesla) could be used to transfer energy between locations without a physical connection. •Guglielmo Marconi began work in 1894 to reproduce the Hertz laboratory experiment over greater distances. His study and efforts brought about the first radio link in the form of wireless telegra ...
sierra wireless watcher™ connection manager
... means update checks are made only during low usage times so it’s never impeding the user’s needs to send or receive information. Sierra Wireless Update includes an innovative download-resume capability that stops downloads when the system is in use and resumes downloading when the system is idle. In ...
... means update checks are made only during low usage times so it’s never impeding the user’s needs to send or receive information. Sierra Wireless Update includes an innovative download-resume capability that stops downloads when the system is in use and resumes downloading when the system is idle. In ...
security engineering
... – As the messages have a low entropy (parts are very easily guessed), an attacker can trivially decode both messages. ...
... – As the messages have a low entropy (parts are very easily guessed), an attacker can trivially decode both messages. ...
How to configure the HL2170W to print wireless
... address of the printer is in the same range (on the same network) as the IP address of the computer. ...
... address of the printer is in the same range (on the same network) as the IP address of the computer. ...
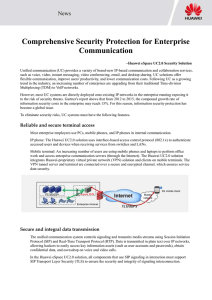
Comprehensive Security Protection for
... However, most UC systems are directly deployed onto existing IP networks in the enterprise running exposing it to the risk of security threats. Gartner's report shows that from 2012 to 2015, the compound growth rate of information security costs in the enterprise may reach 15%. For this reason, info ...
... However, most UC systems are directly deployed onto existing IP networks in the enterprise running exposing it to the risk of security threats. Gartner's report shows that from 2012 to 2015, the compound growth rate of information security costs in the enterprise may reach 15%. For this reason, info ...
Chapter 6 slides, Computer Networking, 3rd edition
... switch: which AP is associated with H1? ...
... switch: which AP is associated with H1? ...
ITEC 370 Midterm
... d. WAN In a(n) ____, every user must also act as a network administrator, controlling access to the resources on their machines. a. LAN c. peer-to-peer network b. internetwork d. client/server network The ____ is a short-range networking technology designed to connect personal devices to exchange in ...
... d. WAN In a(n) ____, every user must also act as a network administrator, controlling access to the resources on their machines. a. LAN c. peer-to-peer network b. internetwork d. client/server network The ____ is a short-range networking technology designed to connect personal devices to exchange in ...
CryptoPro - Applied Security GmbH
... CryptPro Secure Disk for BitLocker enhances the functionality of Microsoft BitLocker by adding an independent Pre-Boot-Authentication (PBA) and allows the usage of well established authentication methods like user-ID/password, smartcard/PIN and biometry for multi-user operation. The encryption of th ...
... CryptPro Secure Disk for BitLocker enhances the functionality of Microsoft BitLocker by adding an independent Pre-Boot-Authentication (PBA) and allows the usage of well established authentication methods like user-ID/password, smartcard/PIN and biometry for multi-user operation. The encryption of th ...
... Researches and recommends new ICT technologies and services to improve and optimize the Ministry’s network systems; Designs, develops and implements a comprehensive disaster recovery plan and strategies incorporating data and systems configuration backup, redundant devices and a test lab; Manages VO ...
Chapter 6 - University of Cyprus
... 802.11n: multiple antennae code 2.4-5 GHz range up to 200 Mbps, and more with MIMO all use CSMA/CA for multiple access all have base-station and ad-hoc network ...
... 802.11n: multiple antennae code 2.4-5 GHz range up to 200 Mbps, and more with MIMO all use CSMA/CA for multiple access all have base-station and ad-hoc network ...
WAN topology
... – Stateful access control and deep packet inspection – Controlling user’s internet bound traffic – Protecting public services in DMZ ...
... – Stateful access control and deep packet inspection – Controlling user’s internet bound traffic – Protecting public services in DMZ ...
Wireless security
.jpg?width=300)
Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). WEP is a notoriously weak security standard. The password it uses can often be cracked in a few minutes with a basic laptop computer and widely available software tools. WEP is an old IEEE 802.11 standard from 1999, which was outdated in 2003 by WPA, or Wi-Fi Protected Access. WPA was a quick alternative to improve security over WEP. The current standard is WPA2; some hardware cannot support WPA2 without firmware upgrade or replacement. WPA2 uses an encryption device that encrypts the network with a 256-bit key; the longer key length improves security over WEP.Many laptop computers have wireless cards pre-installed. The ability to enter a network while mobile has great benefits. However, wireless networking is prone to some security issues. Hackers have found wireless networks relatively easy to break into, and even use wireless technology to hack into wired networks. As a result, it is very important that enterprises define effective wireless security policies that guard against unauthorized access to important resources. Wireless Intrusion Prevention Systems (WIPS) or Wireless Intrusion Detection Systems (WIDS) are commonly used to enforce wireless security policies.The risks to users of wireless technology have increased as the service has become more popular. There were relatively few dangers when wireless technology was first introduced. Hackers had not yet had time to latch on to the new technology, and wireless networks were not commonly found in the work place. However, there are many security risks associated with the current wireless protocols and encryption methods, and in the carelessness and ignorance that exists at the user and corporate IT level. Hacking methods have become much more sophisticated and innovative with wireless access. Hacking has also become much easier and more accessible with easy-to-use Windows- or Linux-based tools being made available on the web at no charge.Some organizations that have no wireless access points installed do not feel that they need to address wireless security concerns. In-Stat MDR and META Group have estimated that 95% of all corporate laptop computers that were planned to be purchased in 2005 were equipped with wireless cards. Issues can arise in a supposedly non-wireless organization when a wireless laptop is plugged into the corporate network. A hacker could sit out in the parking lot and gather information from it through laptops and/or other devices, or even break in through this wireless card–equipped laptop and gain access to the wired network.