Slide 1 - itworkss
... route the traffic from one network to another network efficientlyIt provides intelligent redundancy and security required to select the optimum path.Usually routers are used for connecting remote networks. • 3]Hub-A typical hub is a multi-port repeater.The signals received at the backbone is regener ...
... route the traffic from one network to another network efficientlyIt provides intelligent redundancy and security required to select the optimum path.Usually routers are used for connecting remote networks. • 3]Hub-A typical hub is a multi-port repeater.The signals received at the backbone is regener ...
Backbone: the main connecting cable that runs from one end of the
... machine send a short “request ” message to the AP and wait until the AP acknowledges that request before transmitting an entire message. 9.All hub does is relay any signal it receives back out to all the machines connected to it. A repeater is little more than a device that simply passes signals ba ...
... machine send a short “request ” message to the AP and wait until the AP acknowledges that request before transmitting an entire message. 9.All hub does is relay any signal it receives back out to all the machines connected to it. A repeater is little more than a device that simply passes signals ba ...
Lecture Notes - Computer Science & Engineering
... TCP/IP Protocol Stack Application Layer Transport Layer Internetwork Layer Network Access Layer ...
... TCP/IP Protocol Stack Application Layer Transport Layer Internetwork Layer Network Access Layer ...
Computing Systems Division
... This module will look in detail at a range of techniques that can be used to capture biometric data from individuals together with a study of their practicalities, advantages and limitations. pattern recognition, signal processing, interfacing to biometric devices, biological metrics for face/hand/e ...
... This module will look in detail at a range of techniques that can be used to capture biometric data from individuals together with a study of their practicalities, advantages and limitations. pattern recognition, signal processing, interfacing to biometric devices, biological metrics for face/hand/e ...
Guide to Security - Cal Poly Pomona Foundation, Inc.
... networks • Software tools, such as sniffers and scanners, are used to map out and exploit potential weaknesses in home computers, web servers and applications – Example – password cracking software ...
... networks • Software tools, such as sniffers and scanners, are used to map out and exploit potential weaknesses in home computers, web servers and applications – Example – password cracking software ...
PPT
... Access networks and physical media Q: How to connect end systems to edge router? • residential access nets • institutional access networks (school, ...
... Access networks and physical media Q: How to connect end systems to edge router? • residential access nets • institutional access networks (school, ...
Small Business Networking
... Both of these networks serve the same purpose of allowing multiple users to share and exchange information and resources with each other. But the functions and benefits differ greatly. Peer-to-Peer networks are simple to configure, easy to install and are certainly a low-cost solution; but they are ...
... Both of these networks serve the same purpose of allowing multiple users to share and exchange information and resources with each other. But the functions and benefits differ greatly. Peer-to-Peer networks are simple to configure, easy to install and are certainly a low-cost solution; but they are ...
MASTER - HubSpot
... vendor with access to Customer Information, and you are responsible for ensuring that all third party vendors are compliant with the Security Standards, to the extent applicable. The Security Standards may require that you engage an approved third party vendor to conduct quarterly perimeter scans an ...
... vendor with access to Customer Information, and you are responsible for ensuring that all third party vendors are compliant with the Security Standards, to the extent applicable. The Security Standards may require that you engage an approved third party vendor to conduct quarterly perimeter scans an ...
find_panel.Nick
... The same properties which enable botnets and worms allows Skype, Bittorrent, and BOINC (Seti@home) ...
... The same properties which enable botnets and worms allows Skype, Bittorrent, and BOINC (Seti@home) ...
No Slide Title - Institute of Technology Sligo
... host/client computer speeds (for example, network interface cards and hard drive access speeds). ...
... host/client computer speeds (for example, network interface cards and hard drive access speeds). ...
Network Security Network Attacks and Mitigation
... • Uses for IP spoofing include: – Injecting malicious data or commands into an existing data stream – Diverting all network packets to the hacker who can then reply as a trusted user by changing the routing tables • IP spoofing may only be one step in a larger attack. ...
... • Uses for IP spoofing include: – Injecting malicious data or commands into an existing data stream – Diverting all network packets to the hacker who can then reply as a trusted user by changing the routing tables • IP spoofing may only be one step in a larger attack. ...
Courseware Outline
... certification, and have around 9-12 months' experience of networking support or IT administration. It is not necessary that you pass the A+ exams before completing Network+ certification, but it is recommended. Regardless of whether you have passed A+, it is recommended that you have the following s ...
... certification, and have around 9-12 months' experience of networking support or IT administration. It is not necessary that you pass the A+ exams before completing Network+ certification, but it is recommended. Regardless of whether you have passed A+, it is recommended that you have the following s ...
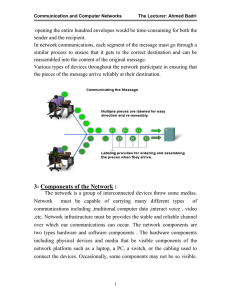
1-Introduction :
... must be capable of carrying many different types of communications including ,traditional computer data ,interact voice , video ,etc. Network infrastructure must be provides the stable and reliable channel over which our communications can occur. The network components are two types hardware and sof ...
... must be capable of carrying many different types of communications including ,traditional computer data ,interact voice , video ,etc. Network infrastructure must be provides the stable and reliable channel over which our communications can occur. The network components are two types hardware and sof ...
Configuring the WT-4 for Upload to a Computer (Ad-hoc Mode)
... * WT-4 firmware version 1.1 and the WT-4 Setup Utility version 1.1 are required when using the WT-4 under Mac OS X version 10.5.2. Updates to the WT-4 firmware and Setup Utility are available on the Nikon website for your ...
... * WT-4 firmware version 1.1 and the WT-4 Setup Utility version 1.1 are required when using the WT-4 under Mac OS X version 10.5.2. Updates to the WT-4 firmware and Setup Utility are available on the Nikon website for your ...
INTRODUCTION TO INFORMATION SYSTEMS TECHNOLOGY
... Packet sniffers – allow seeing data as it moves over network Keystroke monitors – allow seeing what users are ...
... Packet sniffers – allow seeing data as it moves over network Keystroke monitors – allow seeing what users are ...
Citrix GoToMyPC Corporate Technology
... While GoToMyPC® Personal is an easy-to-use, turnkey remote-access solution for individuals, GoToMyPC Corporate makes this same user-friendly remote-access solution available to corporate users. Through enterprise-class administration features, GoToMyPC Corporate gives IT administrators complete cont ...
... While GoToMyPC® Personal is an easy-to-use, turnkey remote-access solution for individuals, GoToMyPC Corporate makes this same user-friendly remote-access solution available to corporate users. Through enterprise-class administration features, GoToMyPC Corporate gives IT administrators complete cont ...
Samsung Smart WLAN
... airtime fairness where multiple users need to simultaneously connect to the network. It also allows seamless service even in an environment with multiple devices with different traffic types, without compromising service quality. In addition, it can maximize the AP’s total cell throughput by more th ...
... airtime fairness where multiple users need to simultaneously connect to the network. It also allows seamless service even in an environment with multiple devices with different traffic types, without compromising service quality. In addition, it can maximize the AP’s total cell throughput by more th ...
Telecom
... connected. The physical wiring can resemble a star pattern using a central device called Multistation Access Unit (MAU) wiring workstations into a logical ring. One disadvantage of a ring network is that if a network device fails (such as a PC or a server), the devices downstream from the failed d ...
... connected. The physical wiring can resemble a star pattern using a central device called Multistation Access Unit (MAU) wiring workstations into a logical ring. One disadvantage of a ring network is that if a network device fails (such as a PC or a server), the devices downstream from the failed d ...
Security Incidents Response in China
... Multiple services are running on the same system: DNS/Mail/Web/ FTP The password is too simple in public servers Auditing function is not enabled or sysadmin never checks the auditing logs No backup: very difficult to recover after intrusion. ...
... Multiple services are running on the same system: DNS/Mail/Web/ FTP The password is too simple in public servers Auditing function is not enabled or sysadmin never checks the auditing logs No backup: very difficult to recover after intrusion. ...
2040927-ITF-Mazurek
... – active and passive data gathering – provides reports on system usage and errors • system management ...
... – active and passive data gathering – provides reports on system usage and errors • system management ...
Wireless security
.jpg?width=300)
Wireless security is the prevention of unauthorized access or damage to computers using wireless networks. The most common types of wireless security are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA). WEP is a notoriously weak security standard. The password it uses can often be cracked in a few minutes with a basic laptop computer and widely available software tools. WEP is an old IEEE 802.11 standard from 1999, which was outdated in 2003 by WPA, or Wi-Fi Protected Access. WPA was a quick alternative to improve security over WEP. The current standard is WPA2; some hardware cannot support WPA2 without firmware upgrade or replacement. WPA2 uses an encryption device that encrypts the network with a 256-bit key; the longer key length improves security over WEP.Many laptop computers have wireless cards pre-installed. The ability to enter a network while mobile has great benefits. However, wireless networking is prone to some security issues. Hackers have found wireless networks relatively easy to break into, and even use wireless technology to hack into wired networks. As a result, it is very important that enterprises define effective wireless security policies that guard against unauthorized access to important resources. Wireless Intrusion Prevention Systems (WIPS) or Wireless Intrusion Detection Systems (WIDS) are commonly used to enforce wireless security policies.The risks to users of wireless technology have increased as the service has become more popular. There were relatively few dangers when wireless technology was first introduced. Hackers had not yet had time to latch on to the new technology, and wireless networks were not commonly found in the work place. However, there are many security risks associated with the current wireless protocols and encryption methods, and in the carelessness and ignorance that exists at the user and corporate IT level. Hacking methods have become much more sophisticated and innovative with wireless access. Hacking has also become much easier and more accessible with easy-to-use Windows- or Linux-based tools being made available on the web at no charge.Some organizations that have no wireless access points installed do not feel that they need to address wireless security concerns. In-Stat MDR and META Group have estimated that 95% of all corporate laptop computers that were planned to be purchased in 2005 were equipped with wireless cards. Issues can arise in a supposedly non-wireless organization when a wireless laptop is plugged into the corporate network. A hacker could sit out in the parking lot and gather information from it through laptops and/or other devices, or even break in through this wireless card–equipped laptop and gain access to the wired network.