NJR2 - 100 Delawanna Ave., Clifton, NJ
... NJR2 (100 Delawanna Ave.) is one of the most network-rich, interconnected colocation centers in the New York City metro area. Located just 11-miles outside of Manhattan, this 211,000 sq. ft. data center is an ideal location for financial services firms looking to run low-latency back office operatio ...
... NJR2 (100 Delawanna Ave.) is one of the most network-rich, interconnected colocation centers in the New York City metro area. Located just 11-miles outside of Manhattan, this 211,000 sq. ft. data center is an ideal location for financial services firms looking to run low-latency back office operatio ...
Digital Security - UC San Diego
... Eliminates Class A, B, and C networks. Subnet masks must be specified for everything • This is a 3rd piece of configuration now required by an IP host: IP address Subnet mask Default Router ...
... Eliminates Class A, B, and C networks. Subnet masks must be specified for everything • This is a 3rd piece of configuration now required by an IP host: IP address Subnet mask Default Router ...
Terminal Bridge Extension Over Distributed Architecture
... • Distributed Service Architecture describes a network environment which offers shared services to network users • Services can be distributed by using different approaches over CORBA or the Wireless CORBA • Both CORBA architectures can support several wireless networking technologies such as Blueto ...
... • Distributed Service Architecture describes a network environment which offers shared services to network users • Services can be distributed by using different approaches over CORBA or the Wireless CORBA • Both CORBA architectures can support several wireless networking technologies such as Blueto ...
2003 - Msjc
... A switch checks the source address of each frame it receives and adds that source address to the local address table (LAT) for the port. The switch is learning, without having to be manually reconfigured, about new workstations that might have been added to the network. ...
... A switch checks the source address of each frame it receives and adds that source address to the local address table (LAT) for the port. The switch is learning, without having to be manually reconfigured, about new workstations that might have been added to the network. ...
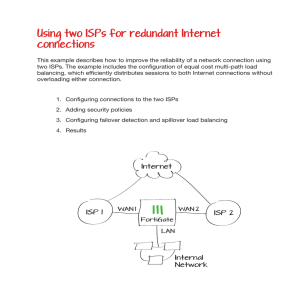
Using two ISPs for redundant Internet connections
... This example describes how to improve the reliability of a network connection using two ISPs. The example includes the configuration of equal cost multi-path load balancing, which efficiently distributes sessions to both Internet connections without overloading either connection. ...
... This example describes how to improve the reliability of a network connection using two ISPs. The example includes the configuration of equal cost multi-path load balancing, which efficiently distributes sessions to both Internet connections without overloading either connection. ...
Slide 1
... ◦ Physical layer: ISDN, T-carriers, DSL, SONET ◦ Data Link layer: X.25, frame relay, ATM ◦ Physical and Data link: broadband ...
... ◦ Physical layer: ISDN, T-carriers, DSL, SONET ◦ Data Link layer: X.25, frame relay, ATM ◦ Physical and Data link: broadband ...
Wireless Communications Research Overview
... Network virtualization combines hardware and software network resources and functionality into a single, software-based virtual network ...
... Network virtualization combines hardware and software network resources and functionality into a single, software-based virtual network ...
IEEE 802.11 based WLANs
... Data Integrity • Data integrity is ensured by a simple encrypted version of CRC (Cyclic Redundant Check) • Also vulnerable to some attacks ...
... Data Integrity • Data integrity is ensured by a simple encrypted version of CRC (Cyclic Redundant Check) • Also vulnerable to some attacks ...
PPT Version
... Solution: Header compression/decompression close to access link with the help of an intermediary could be used [RFC 1144, RFC 2507, RFC 3095, SRTP] An end-to-end IPsec tunnel between the two endpoints would prevent header compression at an intermediate node ...
... Solution: Header compression/decompression close to access link with the help of an intermediary could be used [RFC 1144, RFC 2507, RFC 3095, SRTP] An end-to-end IPsec tunnel between the two endpoints would prevent header compression at an intermediate node ...
Domain name - 3.LF UK 2015
... • A client runs on a host but needs to connect with a sever on another host to accomplish its task. Usually, different clients are used for different tasks, e.g. Web browsing and e-mail. Thus a Web browser is a client. • Some programs are not structured as clients and servers. For example a game, pl ...
... • A client runs on a host but needs to connect with a sever on another host to accomplish its task. Usually, different clients are used for different tasks, e.g. Web browsing and e-mail. Thus a Web browser is a client. • Some programs are not structured as clients and servers. For example a game, pl ...
Curriculum Vitae - ASU People Search
... Implemented Automated and Precise Cross Site Script (XSS) generator for Web Application testing in python. Simulated malicious web server client to identify vulnerabilities in code of python based Web Server. Solved catch the flag challenges including directory traversal, buffer overflow and P ...
... Implemented Automated and Precise Cross Site Script (XSS) generator for Web Application testing in python. Simulated malicious web server client to identify vulnerabilities in code of python based Web Server. Solved catch the flag challenges including directory traversal, buffer overflow and P ...
Binary and Decimal Number Systems What is 101011002 in decimal
... IP addresses 224.0.0.0 to 239.255.255.255 are reserved for multicast ...
... IP addresses 224.0.0.0 to 239.255.255.255 are reserved for multicast ...
Chapter 6. Contemporary Information Systems Issues
... Packet-Switching Technology • Data sent in small standard sized chunks called “packets” • Packets have headers with addresses of sending and receiving computers • Users take turns sending packets • Packets reassembled by the receiver ...
... Packet-Switching Technology • Data sent in small standard sized chunks called “packets” • Packets have headers with addresses of sending and receiving computers • Users take turns sending packets • Packets reassembled by the receiver ...
Network types Point-to-Point (Direct) Connection
... • If cable fails, the entire network will shut down • Earlier Ethernet commonly implement a bus topology ...
... • If cable fails, the entire network will shut down • Earlier Ethernet commonly implement a bus topology ...
Wireless, Voice, Desktop Video, and BYOD Implications for
... globally integrated enterprise, and must meet the diverse needs for connecting employees, customers, and suppliers/partners to IBM services and applications. 2.The network provides integrated security services as a component in the enterprise security architecture through access control, authenticat ...
... globally integrated enterprise, and must meet the diverse needs for connecting employees, customers, and suppliers/partners to IBM services and applications. 2.The network provides integrated security services as a component in the enterprise security architecture through access control, authenticat ...
Slide 1
... Recognizing the Different Types of Network Traffic Network File System Protocol Network File System (NFS) is the default file-sharing protocol for Unix systems. NFS allows a remote user to mount drives on a machine in the network. To be secure, NFS requires special configuration. NFS is equivalent t ...
... Recognizing the Different Types of Network Traffic Network File System Protocol Network File System (NFS) is the default file-sharing protocol for Unix systems. NFS allows a remote user to mount drives on a machine in the network. To be secure, NFS requires special configuration. NFS is equivalent t ...
CS219: Advanced Topics in Internet Research
... – Ability to switch interfaces on the fly to migrate between failure-prone networks – Ability to provide quality of service: what is QoS in this environment? ...
... – Ability to switch interfaces on the fly to migrate between failure-prone networks – Ability to provide quality of service: what is QoS in this environment? ...
Multiple Processor Systems
... src to destination; IP (Internet Protocol) – Transport – provides a msg service to apps; apps don’t need to care that communication is in packets; TCP, UDP – Application – implementing app need; Web, DNS, P2P, email … and protocols like HTTP, DNS, SMTP … Application Transport Network Link ...
... src to destination; IP (Internet Protocol) – Transport – provides a msg service to apps; apps don’t need to care that communication is in packets; TCP, UDP – Application – implementing app need; Web, DNS, P2P, email … and protocols like HTTP, DNS, SMTP … Application Transport Network Link ...
Internet Addressing A Brief Introduction and History
... How to split an Internet address into the network part and the host part has changed over time… ...
... How to split an Internet address into the network part and the host part has changed over time… ...
網路犯罪案例 Cyber crime Case
... Network Packet Forensics Analysis Training The knowledge of network packet analysis is important for Forensic Investigators and Lawful Enforcement Agency (LEA) to carry out their daily duty. Network Packet Forensics Analysis Training (NPFAT) provides useful and sufficient knowledge required to anal ...
... Network Packet Forensics Analysis Training The knowledge of network packet analysis is important for Forensic Investigators and Lawful Enforcement Agency (LEA) to carry out their daily duty. Network Packet Forensics Analysis Training (NPFAT) provides useful and sufficient knowledge required to anal ...
Chapter 1: Protocols and Layers
... between adjacent intermediate systems (routers or gateways) or end systems (hosts). The transport layer can technically be absent from intermediate systems and delivers packet content end-to-end between hosts. The network layer is usually “unreliable” and connectionless but the transport layer often ...
... between adjacent intermediate systems (routers or gateways) or end systems (hosts). The transport layer can technically be absent from intermediate systems and delivers packet content end-to-end between hosts. The network layer is usually “unreliable” and connectionless but the transport layer often ...
DBA 102:NOW WHAT
... Biggest factor is hardware Must be properly configured Creates abstraction layer between Windows Server and hardware Virtualization layer controls access to physical hardware Host level memory pressure may require minimum memory setting Viable part of High Availability solution, but not the whole so ...
... Biggest factor is hardware Must be properly configured Creates abstraction layer between Windows Server and hardware Virtualization layer controls access to physical hardware Host level memory pressure may require minimum memory setting Viable part of High Availability solution, but not the whole so ...