IP Address - Department of Computing & Immersive Technologies
... Private IP Addresses cannot exist on the public Internet. Name Address Translation (NAT) used to give data packets a “legitimate” IP source address. Class A: 10.0.0.0 (Favored by large enterprises because of its flexibility) ...
... Private IP Addresses cannot exist on the public Internet. Name Address Translation (NAT) used to give data packets a “legitimate” IP source address. Class A: 10.0.0.0 (Favored by large enterprises because of its flexibility) ...
LURP
... It starts by behaving like a hub, and forwards all packets out every port When it sees a new source ethernet address on a port, it adds that address to a cache of known addresses When this ethernet address appears in the destination address of a packet, the switch sends it only to the port where thi ...
... It starts by behaving like a hub, and forwards all packets out every port When it sees a new source ethernet address on a port, it adds that address to a cache of known addresses When this ethernet address appears in the destination address of a packet, the switch sends it only to the port where thi ...
CISSP – Chapter 7
... Don’t get too stressed, try to follow along I will try to point out the most important things to understand. If you have questions ASK ME, luckily this is my area of expertise so I should be able to help you out. Some questions may have to be directed to after class or in between breaks if they go t ...
... Don’t get too stressed, try to follow along I will try to point out the most important things to understand. If you have questions ASK ME, luckily this is my area of expertise so I should be able to help you out. Some questions may have to be directed to after class or in between breaks if they go t ...
physcial_sci_networks_part1
... – Current max speed 54Mbps shared by all on same access point – Prone to interference and poor reception – Speed drops under poor conditions to reduce errors – Range 100m+ in open much less in office situation ...
... – Current max speed 54Mbps shared by all on same access point – Prone to interference and poor reception – Speed drops under poor conditions to reduce errors – Range 100m+ in open much less in office situation ...
Three challenges with secret key encryption
... The primary reason is the security policy variations. A good security policy details corporate infrastructure, information authentication mechanism and access privileges. This will vary depending on how the corporate resources are accessed. 10. What is NAT, why it is used, and what is its security ...
... The primary reason is the security policy variations. A good security policy details corporate infrastructure, information authentication mechanism and access privileges. This will vary depending on how the corporate resources are accessed. 10. What is NAT, why it is used, and what is its security ...
IP address. - Seneca - School of Information & Communications
... enforcement mechanism to control access to a 2008 network. ...
... enforcement mechanism to control access to a 2008 network. ...
EECat_ATCA_Viewpoint_Emerson(2)
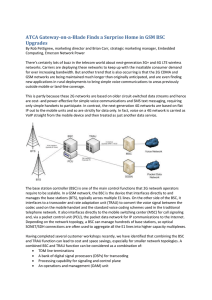
... i7) for running OAM or user applications all on the same board. Enter the “gateway-on-a-blade” approach. Originally conceived for media gateway applications, this blade is an ideal basis around which to build a new BSC. It gives the lowest possible cost and size for entry-level redundant systems, an ...
... i7) for running OAM or user applications all on the same board. Enter the “gateway-on-a-blade” approach. Originally conceived for media gateway applications, this blade is an ideal basis around which to build a new BSC. It gives the lowest possible cost and size for entry-level redundant systems, an ...
Changes in Power System Communications
... Other Computer Networking Devices • Gateway: device sitting at a network node for interfacing with another network that uses different protocols. Works on OSI layers 4 to 7. • Bridge: a device that connects multiple network segments along the data link layer. Works on OSI layer 2. • Repeater: devic ...
... Other Computer Networking Devices • Gateway: device sitting at a network node for interfacing with another network that uses different protocols. Works on OSI layers 4 to 7. • Bridge: a device that connects multiple network segments along the data link layer. Works on OSI layer 2. • Repeater: devic ...
Firewalls
... establish the needs and requirements of the organization. This is a time consuming approach and probably more expensive. – The other approach is what many organizations do and take a short cut and install a vendor firewall already loaded with ...
... establish the needs and requirements of the organization. This is a time consuming approach and probably more expensive. – The other approach is what many organizations do and take a short cut and install a vendor firewall already loaded with ...
PowerPoint
... - The step-by-step process of building a network. - Typically you can find many sites that already provide this information: • E.g., http://www.microsoft.com/windowsxp/using/networking/setup/default.mspx ...
... - The step-by-step process of building a network. - Typically you can find many sites that already provide this information: • E.g., http://www.microsoft.com/windowsxp/using/networking/setup/default.mspx ...
Visual Basic 2005 Chapter 1 Vocabulary
... DSL (Digital Subscriber Line) modem A modem that uses standard telephone phone lines. ADSL is the most common form used. E-mail (electronic mail) The sending and receiving of messages and electronic files over a communications network such as a LAN or the Internet. Environment A computer’s hardware ...
... DSL (Digital Subscriber Line) modem A modem that uses standard telephone phone lines. ADSL is the most common form used. E-mail (electronic mail) The sending and receiving of messages and electronic files over a communications network such as a LAN or the Internet. Environment A computer’s hardware ...
The Internet: Co-Evolution of Technology and Society
... packets, can be potentially lost, can be potentially delivered out-of-order • What you may want: application-to-application (end-to-end) channel, communication stream, ...
... packets, can be potentially lost, can be potentially delivered out-of-order • What you may want: application-to-application (end-to-end) channel, communication stream, ...
IEEE 802.11 Wireless LAN Draft Standard
... • Ad Hoc Network: A temporary one made up of stations in mutual range. • Infrastructure Network: One with one or more Access Points. • Channel: A radio frequency band, or Infrared, used for shared communication. • Basic Service Set (BSS): A set of stations communicating wirelessly on the same channe ...
... • Ad Hoc Network: A temporary one made up of stations in mutual range. • Infrastructure Network: One with one or more Access Points. • Channel: A radio frequency band, or Infrared, used for shared communication. • Basic Service Set (BSS): A set of stations communicating wirelessly on the same channe ...
ROB: Route Optimization Assisted by BGP
... ROB: Route Optimization Assisted by BGP • BGP is a highly robust and scalable routing protocol, as evidenced by its wide use in the Internet. – An entry in the BGP routing table (Network, Next Hop, Path) • Network field: the network destination address. • Next Hop field: the BR’s IP address that sh ...
... ROB: Route Optimization Assisted by BGP • BGP is a highly robust and scalable routing protocol, as evidenced by its wide use in the Internet. – An entry in the BGP routing table (Network, Next Hop, Path) • Network field: the network destination address. • Next Hop field: the BR’s IP address that sh ...
Chapter6
... point (AP) Basic Service Set (BSS) (aka “cell”) in infrastructure mode contains: wireless hosts access point (AP): base station ad hoc mode: hosts only ...
... point (AP) Basic Service Set (BSS) (aka “cell”) in infrastructure mode contains: wireless hosts access point (AP): base station ad hoc mode: hosts only ...
... domain for which it is authoritative itself, or it provides a partial result without querying other servers. A recursive query is one for which the DNS server will fully answer the query (or give an error) by querying other name servers as needed. DNS servers are not required to support recursive qu ...
Document
... • Like motor technology, embedding computers everywhere and having them “disappear in the background” is easy ...
... • Like motor technology, embedding computers everywhere and having them “disappear in the background” is easy ...
U1L6_The_Internet
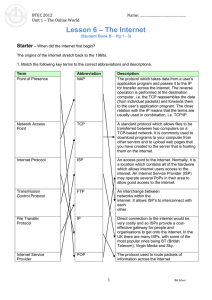
... (from individual packets) and forwards them to the user’s application program. The close relation with the IP means that the terms are usually used in combination, i.e. TCP/IP. ...
... (from individual packets) and forwards them to the user’s application program. The close relation with the IP means that the terms are usually used in combination, i.e. TCP/IP. ...
The Network Layer
... – first set up a connection between two nodes – label it (called a virtual circuit identifier (VCI)) – all packets carry label ...
... – first set up a connection between two nodes – label it (called a virtual circuit identifier (VCI)) – all packets carry label ...