TeraMax™ P2MP
... of throughput, range, suitability for outdoor environments, network scalability and value. A powerful feature set – including orthogonal frequency division multiplexing (OFDM), adaptive dynamic polling, packet aggregation, bandwidth management at the client, and enhanced security comprising AES – pr ...
... of throughput, range, suitability for outdoor environments, network scalability and value. A powerful feature set – including orthogonal frequency division multiplexing (OFDM), adaptive dynamic polling, packet aggregation, bandwidth management at the client, and enhanced security comprising AES – pr ...
S6C6 – X.25
... and can be up to 15 decimal digits long. • DNIC --first four digits of an IDN are called the data network identification code • National terminal number (NTN) – identify the specific DTE on the PSN ...
... and can be up to 15 decimal digits long. • DNIC --first four digits of an IDN are called the data network identification code • National terminal number (NTN) – identify the specific DTE on the PSN ...
What is a VPN
... Same as Chap + functionality to which LAN-based users are accustomed MS-CHAP is consistent with standard CHAP (superset of functionalities) You must at least use MS-CHAP to use MPPE (encryption) ...
... Same as Chap + functionality to which LAN-based users are accustomed MS-CHAP is consistent with standard CHAP (superset of functionalities) You must at least use MS-CHAP to use MPPE (encryption) ...
What is a VPN
... Same as Chap + functionality to which LAN-based users are accustomed MS-CHAP is consistent with standard CHAP (superset of functionalities) You must at least use MS-CHAP to use MPPE (encryption) ...
... Same as Chap + functionality to which LAN-based users are accustomed MS-CHAP is consistent with standard CHAP (superset of functionalities) You must at least use MS-CHAP to use MPPE (encryption) ...
IP Addresses
... that enables the local network to determine whether any given IP address is internal or external to the local network. • A subnet mask is a series of 1’s followed by a series of 0’s. – The 1’s identify which bits go to the ...
... that enables the local network to determine whether any given IP address is internal or external to the local network. • A subnet mask is a series of 1’s followed by a series of 0’s. – The 1’s identify which bits go to the ...
What are the three basic LAN topologies? 2. What common WAN
... What common WAN topology often results in multiple connections to a single site (leading to a high degree of fault tolerance) and has one -to-many connections? ...
... What common WAN topology often results in multiple connections to a single site (leading to a high degree of fault tolerance) and has one -to-many connections? ...
Slide 1
... The receiving process only listens at the port intermittently (why?) What happens to data if this process is not yet listening? ...
... The receiving process only listens at the port intermittently (why?) What happens to data if this process is not yet listening? ...
Courseware Outline
... certification, and have around 9-12 months' experience of networking support or IT administration. It is not necessary that you pass the A+ exams before completing Network+ certification, but it is recommended. Regardless of whether you have passed A+, it is recommended that you have the following s ...
... certification, and have around 9-12 months' experience of networking support or IT administration. It is not necessary that you pass the A+ exams before completing Network+ certification, but it is recommended. Regardless of whether you have passed A+, it is recommended that you have the following s ...
Computer Science 335
... Principles Repeat • Many issues occur in a number of places • Understanding it once can be leveraged into the understanding of numerous features • Keep these issues at the forefront of learning • Many of your experiences will be similar but the wrong one. Be careful. Ask questions. • OSI model is n ...
... Principles Repeat • Many issues occur in a number of places • Understanding it once can be leveraged into the understanding of numerous features • Keep these issues at the forefront of learning • Many of your experiences will be similar but the wrong one. Be careful. Ask questions. • OSI model is n ...
Network Devices
... MAC level broadcast frames; that is the data frames that have a broadcast destination MAC address MAC-level broadcast frames are addressed to all MAC addresses on a given network (not a network segment, but an actual network as defined by its network address) A regular switch forwards all broadcast ...
... MAC level broadcast frames; that is the data frames that have a broadcast destination MAC address MAC-level broadcast frames are addressed to all MAC addresses on a given network (not a network segment, but an actual network as defined by its network address) A regular switch forwards all broadcast ...
Aprisa SR
... With the move to IP based RTUs, the traffic over the air is significantly increasing, reducing the number of Ethernet RTUs that can be supported in a single network, This is turn means more base station sites, which translates to increased costs for customers to add new points of presence, It is not ...
... With the move to IP based RTUs, the traffic over the air is significantly increasing, reducing the number of Ethernet RTUs that can be supported in a single network, This is turn means more base station sites, which translates to increased costs for customers to add new points of presence, It is not ...
1 - Portal UniMAP
... 10. Suppose a computer sends a frame to another computer on a bus topology LAN. The physical destination address of the frame is corrupted during the transmission. What happen to the frame? How can the sender be informed about the situation. ...
... 10. Suppose a computer sends a frame to another computer on a bus topology LAN. The physical destination address of the frame is corrupted during the transmission. What happen to the frame? How can the sender be informed about the situation. ...
Internet History - Physics, Computer Science and Engineering
... • link - physical connection • host - computer connected to network usually only one connection to the network • router - computer providing service of determining where to forward packets – multiple connections to net – called InterfaceMessageProcessor (IMP) or ...
... • link - physical connection • host - computer connected to network usually only one connection to the network • router - computer providing service of determining where to forward packets – multiple connections to net – called InterfaceMessageProcessor (IMP) or ...
document
... i.e., need an entry for each netid at the core of the Internet • Classful address for Class C creates a large number of addresses (2^21): CIDE allows aggregation • CIDR is used for routing purpose in the Internet (started with BGP version 4) • (More as we discuss routing later) ...
... i.e., need an entry for each netid at the core of the Internet • Classful address for Class C creates a large number of addresses (2^21): CIDE allows aggregation • CIDR is used for routing purpose in the Internet (started with BGP version 4) • (More as we discuss routing later) ...
Ingen lysbildetittel
... - Interoperability: Today only one public profile is defined (HCL) - Extensive development cost and effort with specific customer application layer - Not for data streaming (audio/video) but smaller data packets at periodic intervals - Star network (point-to-point) sufficient in most applications - ...
... - Interoperability: Today only one public profile is defined (HCL) - Extensive development cost and effort with specific customer application layer - Not for data streaming (audio/video) but smaller data packets at periodic intervals - Star network (point-to-point) sufficient in most applications - ...
Abstract: Performance Analysis of RPL over AMI (Advanced
... Advances in telecommunication services and technology have enabled machines to be operated by IP internet. With this, the researchers have come up with M2M communication paradigm to standardize the communication of IP operated machines with end hosts connected via traditional internet infrastructure ...
... Advances in telecommunication services and technology have enabled machines to be operated by IP internet. With this, the researchers have come up with M2M communication paradigm to standardize the communication of IP operated machines with end hosts connected via traditional internet infrastructure ...
Introduction to Communications and Networks
... Simple and inexpensive Client/Server: All clients must request service from the server The server is also called a host Different servers perform different tasks: File server, network server, etc. ...
... Simple and inexpensive Client/Server: All clients must request service from the server The server is also called a host Different servers perform different tasks: File server, network server, etc. ...
NETWORK FUNDAMENTALS
... • IP address (255.255.255.255) is a 32 bit number (2^32) • For example; 255.255.255.0 is /24 • Note that 0.0.0.0/0 means any IP address ...
... • IP address (255.255.255.255) is a 32 bit number (2^32) • For example; 255.255.255.0 is /24 • Note that 0.0.0.0/0 means any IP address ...
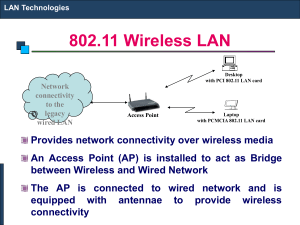
802.11 Wireless LAN
... A repeater receives a signal, regenerates it, and passes it on. It can regenerate and retime network signals at the bit level to allow them to travel a longer distance on the media. It operates at Physical Layer of OSI The Four Repeater Rule for 10-Mbps Ethernet should be used as a standard when ext ...
... A repeater receives a signal, regenerates it, and passes it on. It can regenerate and retime network signals at the bit level to allow them to travel a longer distance on the media. It operates at Physical Layer of OSI The Four Repeater Rule for 10-Mbps Ethernet should be used as a standard when ext ...
chapter1
... • Address: byte string that identifies a node – usually unique – sender and receiver addresses are always included in a packet ...
... • Address: byte string that identifies a node – usually unique – sender and receiver addresses are always included in a packet ...
Chapter 6 slides, Computer Networking, 3rd edition
... infrastructure mode contains: wireless hosts access point (AP): base station ...
... infrastructure mode contains: wireless hosts access point (AP): base station ...
Document
... TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) exist at the next layer up; these are the protocols by which data is transmitted TCP makes a virtual 'connection', which gives some level of guarantee of reliability. UDP is a best-effort, connectionless transport, in which dat ...
... TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) exist at the next layer up; these are the protocols by which data is transmitted TCP makes a virtual 'connection', which gives some level of guarantee of reliability. UDP is a best-effort, connectionless transport, in which dat ...