Powerpoint Slides
... Public key encryption scheme can also handle the problem of privacy. Sender uses the receiver’s public key to encode the message. Receiver uses it’s private key to decode the message. Messages can be encoded twice to authenticate the sender and to enforce privacy. First with the sender’s private ...
... Public key encryption scheme can also handle the problem of privacy. Sender uses the receiver’s public key to encode the message. Receiver uses it’s private key to decode the message. Messages can be encoded twice to authenticate the sender and to enforce privacy. First with the sender’s private ...
BUILDING INTO A MULTILEVEL FILE TRUST
... (GEMSOS) [I], which is targeted for evaluation for a Class A1 rating according to the Trusted Computer System Evaluation Criteria (TCSEC) [2]. A requirement for an A1 TCB is the exclusion of non-security relevant functionality from the TCB. Thus it is the operating system executing on the TCB which ...
... (GEMSOS) [I], which is targeted for evaluation for a Class A1 rating according to the Trusted Computer System Evaluation Criteria (TCSEC) [2]. A requirement for an A1 TCB is the exclusion of non-security relevant functionality from the TCB. Thus it is the operating system executing on the TCB which ...
Presentation Prepared By: Raghda Zahran
... Information security is not just a paperwork drill…there are dangerous adversaries out there capable of launching serious attacks on our information systems that can result in severe or catastrophic damage to the nation’s critical information infrastructure and ultimately threaten our economic and ...
... Information security is not just a paperwork drill…there are dangerous adversaries out there capable of launching serious attacks on our information systems that can result in severe or catastrophic damage to the nation’s critical information infrastructure and ultimately threaten our economic and ...
Viruses - Bozonline
... Product activation allow users to input product identification numbers online or by phone and receive a unique installation identification number in return ...
... Product activation allow users to input product identification numbers online or by phone and receive a unique installation identification number in return ...
03-WAS Common Threats - Professional Data Management
... Buffer overflow attacks These kind of attacks involves sending overly long input streams to the attacked server, causing the server to overflow parts of the memory and either crash the system or execute the attackers arbitrary code as if it was part of the servers code. The attackers code can inject ...
... Buffer overflow attacks These kind of attacks involves sending overly long input streams to the attacked server, causing the server to overflow parts of the memory and either crash the system or execute the attackers arbitrary code as if it was part of the servers code. The attackers code can inject ...
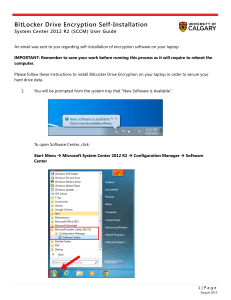
BitLocker Drive Encryption Self
... Click the checkbox next to Install U of C Encryption (Reboot Required) and then click Install Selected. ...
... Click the checkbox next to Install U of C Encryption (Reboot Required) and then click Install Selected. ...
Assignment #2 S.Popovic
... 2. Consider the statement: an individual threat, like a hacker, can be represented in more than one threat category. If a hacker hacks into a network, copies a few files, defaces the Web page, and steals credit card numbers, how many different threat categories does this attack cover? ...
... 2. Consider the statement: an individual threat, like a hacker, can be represented in more than one threat category. If a hacker hacks into a network, copies a few files, defaces the Web page, and steals credit card numbers, how many different threat categories does this attack cover? ...
Slide 1
... Project Agency (ARPA) of the U.S. government in 1969 and was known as ARPAnet. It was designed to enable U.S. military leaders to stay in contact in case of a nuclear war. The protocol used in ARPAnet was called Network Control Protocol (NCP). The protocol had too many limitations and was not robust ...
... Project Agency (ARPA) of the U.S. government in 1969 and was known as ARPAnet. It was designed to enable U.S. military leaders to stay in contact in case of a nuclear war. The protocol used in ARPAnet was called Network Control Protocol (NCP). The protocol had too many limitations and was not robust ...
Cisco 642-552
... Denial of Service (DoS) is an attack designed to render a computer or network incapable of providing normal services. The most common DoS attacks will target the computer's network bandwidth or connectivity. Bandwidth attacks flood the network with such a high volume of traffic, that all available n ...
... Denial of Service (DoS) is an attack designed to render a computer or network incapable of providing normal services. The most common DoS attacks will target the computer's network bandwidth or connectivity. Bandwidth attacks flood the network with such a high volume of traffic, that all available n ...
Remote Access - York Technical College
... algorithm that makes it difficult for unauthorized users to read the data if they intercept it. Encryption requires a key (math. Algorithm) to read the data. Two types of encryption ...
... algorithm that makes it difficult for unauthorized users to read the data if they intercept it. Encryption requires a key (math. Algorithm) to read the data. Two types of encryption ...
Word Template
... Seamlessly investigate bot infections with advanced logs and management system providing key inputs such as infected machine/user, bot name, bot actions (such as communication with command & control and spam sending), amount of data sent/received, infection severity and more. In addition, the soluti ...
... Seamlessly investigate bot infections with advanced logs and management system providing key inputs such as infected machine/user, bot name, bot actions (such as communication with command & control and spam sending), amount of data sent/received, infection severity and more. In addition, the soluti ...
Types of Surveillance Technology Currently Used by Governments
... Internet user receives e-mail appearing to be legitimate and from reputable company, asking user to reply with updated credit card information Clicking on link sends user to fake Website, where user provides ...
... Internet user receives e-mail appearing to be legitimate and from reputable company, asking user to reply with updated credit card information Clicking on link sends user to fake Website, where user provides ...
Chapter 03
... Assess: verify product security before release. Respond: know how to deal with customers who report security concerns with your product. ...
... Assess: verify product security before release. Respond: know how to deal with customers who report security concerns with your product. ...
here - Penndel Mental Health Center
... writing or by email. IS will unblock that site or category for that associate only and will track approved exceptions and report on them upon request. 4.0 Enforcement The IS Security Officer will periodically review Internet use monitoring and filtering systems and processes to ensure they are in co ...
... writing or by email. IS will unblock that site or category for that associate only and will track approved exceptions and report on them upon request. 4.0 Enforcement The IS Security Officer will periodically review Internet use monitoring and filtering systems and processes to ensure they are in co ...
spear-phishing attacks
... responded to several targeted attacks that resulted in the theft of PII by threat actors linked to China. The volume of PII stolen indicated that the objective was the mass collection of PII data, not that of specific individuals. However, Mandiant had not previously observed a trend of indiscrimina ...
... responded to several targeted attacks that resulted in the theft of PII by threat actors linked to China. The volume of PII stolen indicated that the objective was the mass collection of PII data, not that of specific individuals. However, Mandiant had not previously observed a trend of indiscrimina ...
Web Server Administration
... A default list of files is included but it will take time to refine the list A report can be produced to find out which files have been added, changed, and deleted ...
... A default list of files is included but it will take time to refine the list A report can be produced to find out which files have been added, changed, and deleted ...
TECHNOLOGY-DRIVEN METRICS
... Ensure all software is approved and recently patched Whitelist defines the permitted list of software. Blacklist defines illegal software (e.g., IT tools). Endpoint Security Suites (ESS) contain antivirus, antispyware, firewall, IDS/IPS, s/w white/blacklisting. Metric: Temporarily install un ...
... Ensure all software is approved and recently patched Whitelist defines the permitted list of software. Blacklist defines illegal software (e.g., IT tools). Endpoint Security Suites (ESS) contain antivirus, antispyware, firewall, IDS/IPS, s/w white/blacklisting. Metric: Temporarily install un ...
PASS4TEST
... A. Publish the desired policies to all employees directing them to implement according to policy. B. Configure each computer to adhere to the standard policies. C. When installing new workstations or servers, image a machine that has proper security settings install the new machine with that image. ...
... A. Publish the desired policies to all employees directing them to implement according to policy. B. Configure each computer to adhere to the standard policies. C. When installing new workstations or servers, image a machine that has proper security settings install the new machine with that image. ...
Chap013
... with You What is an “orphaned account”? Why are they dangerous? Why do people take data with them when they leave an organization? How many firms monitor or track these accounts? What threats does this pose to the firm? ...
... with You What is an “orphaned account”? Why are they dangerous? Why do people take data with them when they leave an organization? How many firms monitor or track these accounts? What threats does this pose to the firm? ...
Access Security Requirements
... In accessing the credit reporting agency’s services, you agree to follow these security requirements: 1. Implement Strong Access Control Measures 1.1 Do not provide your credit reporting agency Subscriber Codes or passwords to anyone. No one from the credit reporting agency will ever contact you and ...
... In accessing the credit reporting agency’s services, you agree to follow these security requirements: 1. Implement Strong Access Control Measures 1.1 Do not provide your credit reporting agency Subscriber Codes or passwords to anyone. No one from the credit reporting agency will ever contact you and ...
WHAT IS EC SECURITY? - Joseph H. Schuessler, PhD
... occurs; each function in the business should have a valid recovery capability plan cybercrime Intentional crimes carried out on the Internet cybercriminal A person who intentionally carries out crimes over the Internet ...
... occurs; each function in the business should have a valid recovery capability plan cybercrime Intentional crimes carried out on the Internet cybercriminal A person who intentionally carries out crimes over the Internet ...
Lecture 10 - The University of Texas at Dallas
... - Before installing a secure system or a network one needs to conduct a risk analysis study - What are the threats? What are the risks? Various types of risk analysis methods Quantitative approach: Events are ranked in the order of risks and decisions are made based on then risks Qualitative appro ...
... - Before installing a secure system or a network one needs to conduct a risk analysis study - What are the threats? What are the risks? Various types of risk analysis methods Quantitative approach: Events are ranked in the order of risks and decisions are made based on then risks Qualitative appro ...