Computer and Information Security
... • Is the web site I am downloading information from a legitimate one, or a fake? • How do I ensure that the person I just did a financial transaction denies having done it tomorrow or at a later time? • I want to buy some thing online, but I don’t want to let them charge my credit card before they d ...
... • Is the web site I am downloading information from a legitimate one, or a fake? • How do I ensure that the person I just did a financial transaction denies having done it tomorrow or at a later time? • I want to buy some thing online, but I don’t want to let them charge my credit card before they d ...
WiHawk
... Allows a free access to many hosts on the Internet. Allows various remote commands like: Remote access to root shell of routers File copy ...
... Allows a free access to many hosts on the Internet. Allows various remote commands like: Remote access to root shell of routers File copy ...
Intrusion Detection and Prevention
... IDSs monitoring various network zones. (Network-based IDSs) Place outside a firewall for learning about malicious activities on the Internet. Place in the DMZ to see attacks originating from the Internet that are able to get through the outer firewall to public servers. Place in the private network ...
... IDSs monitoring various network zones. (Network-based IDSs) Place outside a firewall for learning about malicious activities on the Internet. Place in the DMZ to see attacks originating from the Internet that are able to get through the outer firewall to public servers. Place in the private network ...
Document
... effects on your organization. 2. Security topology covers four primary areas of concern (design goals, security zones, technologies, and business requirements). Describe each area including key topics in each area. 3. Discuss software threats classified as malicious code on page 81 of your text. ...
... effects on your organization. 2. Security topology covers four primary areas of concern (design goals, security zones, technologies, and business requirements). Describe each area including key topics in each area. 3. Discuss software threats classified as malicious code on page 81 of your text. ...
Security+ Guide to Network Security Fundamentals
... Network management device that sits between network segments and routes traffic from one network to another Allows networks to communicate with one ...
... Network management device that sits between network segments and routes traffic from one network to another Allows networks to communicate with one ...
Introduction - Computer Science
... Algorithms and protocols – Conventional and public key-based encryption, hash function, digital signature, and key exchange Applications and tools – Kerberos, X.509v3 certificates, PGP, S/MIME, IP security (VPN), SSL/TLS, SET, and SNMPv3 ...
... Algorithms and protocols – Conventional and public key-based encryption, hash function, digital signature, and key exchange Applications and tools – Kerberos, X.509v3 certificates, PGP, S/MIME, IP security (VPN), SSL/TLS, SET, and SNMPv3 ...
procedure name - Siskiyou Central Credit Union
... the third week of each month on Thursday after EOD is processed. The Information Security Officer receives an e-mail and / or a phone call to confirm and notify the credit union of each deployment. ...
... the third week of each month on Thursday after EOD is processed. The Information Security Officer receives an e-mail and / or a phone call to confirm and notify the credit union of each deployment. ...
Overview of Knowledge Discovery in Databases Process and Data
... Development of more effective early warning systems (EWSs) for various applications have been possible during the past decade due to advancements in information, detection, data mining (DM) and surveillance technologies. These application areas include economy, banking, finance, health care, bioinfo ...
... Development of more effective early warning systems (EWSs) for various applications have been possible during the past decade due to advancements in information, detection, data mining (DM) and surveillance technologies. These application areas include economy, banking, finance, health care, bioinfo ...
IT Security Policy
... DISTRICTS shall maintain a network configuration management program which includes as a minimum: a network diagram identifying all connections, addresses, and purpose of each connection including management approval of all high risk internetfacing ports such as mail (SMTP/25), file transport protoco ...
... DISTRICTS shall maintain a network configuration management program which includes as a minimum: a network diagram identifying all connections, addresses, and purpose of each connection including management approval of all high risk internetfacing ports such as mail (SMTP/25), file transport protoco ...
Secure your remote access with VASCO and
... while remaining easy-to-use When employees use their PC, they want to read e-mail, use software and documents, access files on the corporate network, work with applications and access websites. With the workforce becoming more mobile, the employees want to do all this anywhere and any time. SSL VPN ...
... while remaining easy-to-use When employees use their PC, they want to read e-mail, use software and documents, access files on the corporate network, work with applications and access websites. With the workforce becoming more mobile, the employees want to do all this anywhere and any time. SSL VPN ...
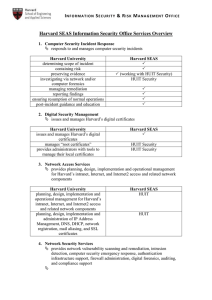
Harvard SEAS Information Security Office Services Overview
... may indicate computer attack, compromised machine, data breach, etc Harvard University monitors network traffic in real-time aggregates and correlates security data from network and system infrastructure ...
... may indicate computer attack, compromised machine, data breach, etc Harvard University monitors network traffic in real-time aggregates and correlates security data from network and system infrastructure ...
Speech Title Here
... Essential part of development process Just like specing and designing Just like coding and testing ...
... Essential part of development process Just like specing and designing Just like coding and testing ...
Web Security
... • Once a secure session is established the source requests the destinations certificate ( sent in the http header (uncncrypted)) • once the source accepts the authenticity of the certificate it uses the public-key from the certificate to encrypt the generated session key for protecting the conversat ...
... • Once a secure session is established the source requests the destinations certificate ( sent in the http header (uncncrypted)) • once the source accepts the authenticity of the certificate it uses the public-key from the certificate to encrypt the generated session key for protecting the conversat ...
Web Security
... • Once a secure session is established the source requests the destinations certificate ( sent in the http header (uncncrypted)) • once the source accepts the authenticity of the certificate it uses the public-key from the certificate to encrypt the generated session key for protecting the conversat ...
... • Once a secure session is established the source requests the destinations certificate ( sent in the http header (uncncrypted)) • once the source accepts the authenticity of the certificate it uses the public-key from the certificate to encrypt the generated session key for protecting the conversat ...
2001-10-11-AIC-SecurityForEducation
... if all student directories were wiped out and no backups existed? • Discuss privacy issues – all of the superintendent’s or spec. ed director’s email being sent to the local paper for example • Loss of USF funding, loss of accreditation • Loss of stakeholder confidence and support • Loss of valuable ...
... if all student directories were wiped out and no backups existed? • Discuss privacy issues – all of the superintendent’s or spec. ed director’s email being sent to the local paper for example • Loss of USF funding, loss of accreditation • Loss of stakeholder confidence and support • Loss of valuable ...
Chapter 2: Introduction to Microprocessor
... It is composed of collection of files that are linked in such a way that information from one of the files may be combined with information from other files so that a user may receive the exact required information. ...
... It is composed of collection of files that are linked in such a way that information from one of the files may be combined with information from other files so that a user may receive the exact required information. ...
Rocket® Blue Zone Security Server
... access to host systems, increasing data stream privacy, and strengthening authentication. Rocket® BlueZone Security Server secures confidential information, authenticates users and reinforces network and perimeter security. ...
... access to host systems, increasing data stream privacy, and strengthening authentication. Rocket® BlueZone Security Server secures confidential information, authenticates users and reinforces network and perimeter security. ...
BUNDLE PROTOCOL
... Netcat as a Backdoor • A popular backdoor tool • Netcat must be compiled with “GAPING_SECURITY_HOLE” option • On victim machine, run Netcat in listener mode with –e flag to execute a specific program such as a command shell • On attacker’s machine run Netcat in client mode to connect to backdoor on ...
... Netcat as a Backdoor • A popular backdoor tool • Netcat must be compiled with “GAPING_SECURITY_HOLE” option • On victim machine, run Netcat in listener mode with –e flag to execute a specific program such as a command shell • On attacker’s machine run Netcat in client mode to connect to backdoor on ...
Ecommerce: Security and Control
... connections through a network Firewalls are gateways that provide this They can limit or allow connections based on: ...
... connections through a network Firewalls are gateways that provide this They can limit or allow connections based on: ...
DO NOT - Middlebury College
... •Use secure passwords which you change often. This also applies to mobile devices. ...
... •Use secure passwords which you change often. This also applies to mobile devices. ...
Information System Security
... systems and the information transfers of an organization • intended to counter security attacks • make use of one or more security mechanisms to provide the service • replicate functions normally associated with physical documents • eg have signatures, dates; need protection from disclosure, tamperi ...
... systems and the information transfers of an organization • intended to counter security attacks • make use of one or more security mechanisms to provide the service • replicate functions normally associated with physical documents • eg have signatures, dates; need protection from disclosure, tamperi ...
Document
... Ensure all software is approved and recently patched Whitelist defines the permitted list of software. Blacklist defines illegal software (e.g., IT tools). Endpoint Security Suites (ESS) contain antivirus, antispyware, firewall, IDS/IPS, s/w white/blacklisting. Metric: Temporarily install un ...
... Ensure all software is approved and recently patched Whitelist defines the permitted list of software. Blacklist defines illegal software (e.g., IT tools). Endpoint Security Suites (ESS) contain antivirus, antispyware, firewall, IDS/IPS, s/w white/blacklisting. Metric: Temporarily install un ...