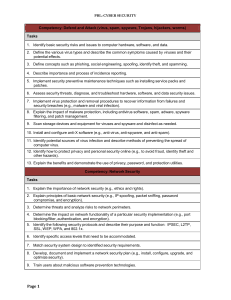
Competency: Defend and Attack (virus, spam, spyware - FBLA-PBL
... 4. Inspect the password files to detect inadvisable passwords. 5. Inspect other system areas to detect policy violations. 6. Assess system and file integrity. 7. Recognize patterns typical of attacks. 8. Analyze abnormal activity patterns. 9. Track user policy violations. 10. Demonstrate an understa ...
... 4. Inspect the password files to detect inadvisable passwords. 5. Inspect other system areas to detect policy violations. 6. Assess system and file integrity. 7. Recognize patterns typical of attacks. 8. Analyze abnormal activity patterns. 9. Track user policy violations. 10. Demonstrate an understa ...
Three challenges with secret key encryption
... 1. What is “brute-force attack”? How the “brute-force attack” is related to Keyspace (the range of possible value of the Key)? Why the issue of number of bit required in a key to ensure secure encryption is controversial? A brute -force attack is applying all possible value of a key to the algorithm ...
... 1. What is “brute-force attack”? How the “brute-force attack” is related to Keyspace (the range of possible value of the Key)? Why the issue of number of bit required in a key to ensure secure encryption is controversial? A brute -force attack is applying all possible value of a key to the algorithm ...
EHLANZENI DISTRICT MUNICIPALITY INTRUSION DETECTION
... intrusion detection implementation of the organizational networks and hosts along with associated roles and responsibilities. This policy is designed both to protect the confidentiality of any data that may be stored on the mobile computer and to protect the organizational network from being infecte ...
... intrusion detection implementation of the organizational networks and hosts along with associated roles and responsibilities. This policy is designed both to protect the confidentiality of any data that may be stored on the mobile computer and to protect the organizational network from being infecte ...
Building Secure System Using Mobile Agents - KTH
... System Components Roles in the Proposed System Components of the System Operations of the System ...
... System Components Roles in the Proposed System Components of the System Operations of the System ...
Key To Personal Information Security
... having to directly use your computers • Exploit Internet services that are intended to give out information • Induce these services to reveal extra information or to give it out to unauthorized people • Many services designed for use on local area networks do not have the security needed for safe us ...
... having to directly use your computers • Exploit Internet services that are intended to give out information • Induce these services to reveal extra information or to give it out to unauthorized people • Many services designed for use on local area networks do not have the security needed for safe us ...
Top-Ten Web Security Vulnerabilities
... Limits what users can do, which resources they have access to, and what functions they are allowed to perform on the data. Authorization The act of checking to see if a user has the proper permission to access a particular file or perform a particular action ...
... Limits what users can do, which resources they have access to, and what functions they are allowed to perform on the data. Authorization The act of checking to see if a user has the proper permission to access a particular file or perform a particular action ...
Network Security Network Attacks and Mitigation
... • IP spoofing can use either a trusted IP address in the network or a trusted external IP address. • Uses for IP spoofing include: – Injecting malicious data or commands into an existing data stream – Diverting all network packets to the hacker who can then reply as a trusted user by changing the ro ...
... • IP spoofing can use either a trusted IP address in the network or a trusted external IP address. • Uses for IP spoofing include: – Injecting malicious data or commands into an existing data stream – Diverting all network packets to the hacker who can then reply as a trusted user by changing the ro ...
Identify Security Risks and Threats
... that contains IPSec port filters that will be used to lock down unnecessary ports on an IIS server View IPSec port filter properties ...
... that contains IPSec port filters that will be used to lock down unnecessary ports on an IIS server View IPSec port filter properties ...
Lecture 12
... Informs analyst, other entities of results of analysis May reconfigure logging and/or analysis on basis of results May take some action ...
... Informs analyst, other entities of results of analysis May reconfigure logging and/or analysis on basis of results May take some action ...
Network Security - University of Hull
... The component steps that enable an activity Can be software components or human procedures ...
... The component steps that enable an activity Can be software components or human procedures ...
Network security policy: best practices
... system or data that if compromised would cause a moderate disruption in the business or minor legal or financial ramification, provide further access to other system The targeted system or data requires a moderate effort to restore The restoration process is disruptive to the system ...
... system or data that if compromised would cause a moderate disruption in the business or minor legal or financial ramification, provide further access to other system The targeted system or data requires a moderate effort to restore The restoration process is disruptive to the system ...
Network Infrastructure Security
... people. LAN software and practices also need to provide for the security of these programs and data. ...
... people. LAN software and practices also need to provide for the security of these programs and data. ...
Cyber Security in Evolving Enterprise
... & Defense-in-Depth Protection • Current Government approaches are limited – Can we continue to address the increasing threats • Growing numbers of vulnerabilities & patches? • Is signature based virus / malware detection enough – How are out sourced services protected? – How are insider threats deal ...
... & Defense-in-Depth Protection • Current Government approaches are limited – Can we continue to address the increasing threats • Growing numbers of vulnerabilities & patches? • Is signature based virus / malware detection enough – How are out sourced services protected? – How are insider threats deal ...
Chapter 05
... access control, enforce sharing, fair service, inter-process communications and synchronization, protected OS and data. ...
... access control, enforce sharing, fair service, inter-process communications and synchronization, protected OS and data. ...
E-Commerce Security
... venturing into new markets, new channels and new products. Their focus is on competitive advantage through new ways of managing relationships and doing business. • Experimentation: These businesses want to become learning organizations. They are exploring the Internet and Intranet and funding small ...
... venturing into new markets, new channels and new products. Their focus is on competitive advantage through new ways of managing relationships and doing business. • Experimentation: These businesses want to become learning organizations. They are exploring the Internet and Intranet and funding small ...
Global Information Assurance Certification (GIAC) develops and administers the premier
... • Comphrehensive Pen Test Planning, Scoping and Recon • In-Depth Scanning and Exploitation, Post-Exploitation and Pivoting • In-Depth Password Attacks and Web App Pen Testing • Web App Pen Testing and Ethical Hacking: Configuration, Identity and Authentication • Injection, JavaScript, XSS, and ...
... • Comphrehensive Pen Test Planning, Scoping and Recon • In-Depth Scanning and Exploitation, Post-Exploitation and Pivoting • In-Depth Password Attacks and Web App Pen Testing • Web App Pen Testing and Ethical Hacking: Configuration, Identity and Authentication • Injection, JavaScript, XSS, and ...
Cyberespionage campaign hits energy companies
... Most of the victims were infected with the Havex RAT; Karagany was identi ed on only 5% of the infected computers. Havex appears to be custom malware either written by the Dragon y group itself or commissioned by them. Security analysts of F-Secure [2] have identi ed and analyzed 88 variants of Have ...
... Most of the victims were infected with the Havex RAT; Karagany was identi ed on only 5% of the infected computers. Havex appears to be custom malware either written by the Dragon y group itself or commissioned by them. Security analysts of F-Secure [2] have identi ed and analyzed 88 variants of Have ...
Computer Security: Principles and Practice, 1/e
... • Can only identify known attacks for which it has patterns or rules (signature) ...
... • Can only identify known attacks for which it has patterns or rules (signature) ...
Computer security - University of London International Programmes
... This course deals with the more technical means of making a computing system secure. This process starts with defining the proper security requirements, which are usually stated as a security policy. Security models formalise those policies and may serve as a reference to check the correctness of an ...
... This course deals with the more technical means of making a computing system secure. This process starts with defining the proper security requirements, which are usually stated as a security policy. Security models formalise those policies and may serve as a reference to check the correctness of an ...
Chapter 4
... 32. The computers used in an organization are part of the ____________________ layer of the bull’s-eye model. 33. The responsibilities of both the users and the systems administrators should be specified in the ____________________ section of the ISSP. 34. The ____________________ section of the IS ...
... 32. The computers used in an organization are part of the ____________________ layer of the bull’s-eye model. 33. The responsibilities of both the users and the systems administrators should be specified in the ____________________ section of the ISSP. 34. The ____________________ section of the IS ...
download soal
... 1. What are the four types of architecture for multi user systems? 2. What are the four categories of controls discussed in this text ? Birefly describe each category 3. Why is IT planning important to an organization? 4. Briefly describe three important controls related to organizing the IT functio ...
... 1. What are the four types of architecture for multi user systems? 2. What are the four categories of controls discussed in this text ? Birefly describe each category 3. Why is IT planning important to an organization? 4. Briefly describe three important controls related to organizing the IT functio ...
Protection
... Definition of the object of protection (ISIR) and categories of protected information; Description of the process (simulation) of information security ISIR; Programming the required level of information security; Setting the required level of information security; Identification of measures to prote ...
... Definition of the object of protection (ISIR) and categories of protected information; Description of the process (simulation) of information security ISIR; Programming the required level of information security; Setting the required level of information security; Identification of measures to prote ...