AUDACIOUS User-Driven Access Control with Unmodified
... • Annotating code for SPARTA is fast for small applications, but a burden for ...
... • Annotating code for SPARTA is fast for small applications, but a burden for ...
Network and Systems Security
... The Universal Access and Information Security working groups have produced a set of draft Policies and Guidelines for consultation These are not meant to place unnecessary barriers in the way of users doing their legitimate work The general aim is to define the University’s security requirements wit ...
... The Universal Access and Information Security working groups have produced a set of draft Policies and Guidelines for consultation These are not meant to place unnecessary barriers in the way of users doing their legitimate work The general aim is to define the University’s security requirements wit ...
Network Improvement Project
... Configuration and Asset Management Infrastructure for Window, Mac, and Linux systems - $60,000 Provides us the ability to manage the security of over 5000 desktops, servers and other computers and to discover in detail what software is loaded and functioning on each machine. Software is provided ...
... Configuration and Asset Management Infrastructure for Window, Mac, and Linux systems - $60,000 Provides us the ability to manage the security of over 5000 desktops, servers and other computers and to discover in detail what software is loaded and functioning on each machine. Software is provided ...
View Presentation - InfoSec Nashville
... routing numbers, account type), driver’s license, full name, address, phone, etc. and counterfeit physical documents and hardware related to the identity data in the package (e.g. credit cards, driver’s license, insurance cards, etc.)—ranging between $1200 – $1300 per Kitz. Add $100 – $500 for rush ...
... routing numbers, account type), driver’s license, full name, address, phone, etc. and counterfeit physical documents and hardware related to the identity data in the package (e.g. credit cards, driver’s license, insurance cards, etc.)—ranging between $1200 – $1300 per Kitz. Add $100 – $500 for rush ...
The Top Six Risks of Employee Internet Use and How
... create what is called a “blended threat”. Many types of Spyware, often called Key Loggers, are used to compromise data and steal personal or proprietary information. Key Loggers monitor computer users’ every keystroke, hoping to encounter a series that will turn out to be a password or a credit card ...
... create what is called a “blended threat”. Many types of Spyware, often called Key Loggers, are used to compromise data and steal personal or proprietary information. Key Loggers monitor computer users’ every keystroke, hoping to encounter a series that will turn out to be a password or a credit card ...
Designing Trusted Operating Systems Operating Systems
... Trusted software- software portion of system that can be relied upon to enforce security policy Trusted computing base – set of all protection mechanisms within a computing system that enforce a nified security policy Trusted system – system that employs sufficient hardware and software integrity me ...
... Trusted software- software portion of system that can be relied upon to enforce security policy Trusted computing base – set of all protection mechanisms within a computing system that enforce a nified security policy Trusted system – system that employs sufficient hardware and software integrity me ...
SRA Customized Web Portal | Secure Remote Access | SonicWALL
... The personalized portal serves two purposes; first, it displays only those assets that each user is authorized to access based on corporate policy, and second, it provides an easy to use interface to make the end-user experience simple and straightforward. ...
... The personalized portal serves two purposes; first, it displays only those assets that each user is authorized to access based on corporate policy, and second, it provides an easy to use interface to make the end-user experience simple and straightforward. ...
426_Fall10_lect01 - Purdue Computer Science
... • Computer worms – E.g., Morris worm (1988), Melissa worm (1999), etc. ...
... • Computer worms – E.g., Morris worm (1988), Melissa worm (1999), etc. ...
Chapter 08
... Explain commonly used cryptographic systems Understand digital certificates and certificate authorities Use the PGP and GPG data-encryption utilities Describe different ways in which cryptography is applied to make computer systems more secure ...
... Explain commonly used cryptographic systems Understand digital certificates and certificate authorities Use the PGP and GPG data-encryption utilities Describe different ways in which cryptography is applied to make computer systems more secure ...
TEL2813/IS2820 Security Management
... All Internet Control Message Protocol (ICMP) data should be denied Telnet (terminal emulation) access to all internal servers from the public networks should be blocked When Web services are offered outside the firewall, HTTP traffic should be handled by some form of proxy access or DMZ architecture ...
... All Internet Control Message Protocol (ICMP) data should be denied Telnet (terminal emulation) access to all internal servers from the public networks should be blocked When Web services are offered outside the firewall, HTTP traffic should be handled by some form of proxy access or DMZ architecture ...
FLAX: Systematic Discovery of Client-Side Validation Vulnerabilities
... This is done by testing the client-side code independently of the server-side cody by generating candidate inputs that make simple assumptions about the transformations occurring in reflected flows. Subsequently, the tool verifies the assumption by running the candidate attack concretely, and report ...
... This is done by testing the client-side code independently of the server-side cody by generating candidate inputs that make simple assumptions about the transformations occurring in reflected flows. Subsequently, the tool verifies the assumption by running the candidate attack concretely, and report ...
FireWall-1 - Evolution Security Systems Ltd
... inspects Web applications such as Instant Messaging and peer-to-peer applications even when they are running on commonly used ports. Truly the basis for a security infrastructure, you can extend Web application and CIFS security to include single sign-on with an optional UserAuthority Module. Protec ...
... inspects Web applications such as Instant Messaging and peer-to-peer applications even when they are running on commonly used ports. Truly the basis for a security infrastructure, you can extend Web application and CIFS security to include single sign-on with an optional UserAuthority Module. Protec ...
VirtuWind–Security in a Virtual and Programmable Industrial
... transportation and logistics. Many of these applications have very stringent requirements on the underlying communication network(s). This is currently addressed by using complex and proprietary network protocols and mechanisms, but this approach has major drawbacks: substantial engineering, operati ...
... transportation and logistics. Many of these applications have very stringent requirements on the underlying communication network(s). This is currently addressed by using complex and proprietary network protocols and mechanisms, but this approach has major drawbacks: substantial engineering, operati ...
CNCERT/CC Annual Report 2008
... the handling of security incidents for national public networks, important national application systems and key organizations, involving detection, prediction, response and prevention. It collects, verifies, accumulates and publishes authoritative information on the Internet security issues. It is a ...
... the handling of security incidents for national public networks, important national application systems and key organizations, involving detection, prediction, response and prevention. It collects, verifies, accumulates and publishes authoritative information on the Internet security issues. It is a ...
Network Security Chapter 14
... ____ 21. One of the most common forms of social engineering is ____, or sending an e-mail or displaying a Web announcement that falsely claims to be from a legitimate enterprise in an attempt to trick the user into surrendering private information. a. dumpster diving c. computer hoax b. phishing d. ...
... ____ 21. One of the most common forms of social engineering is ____, or sending an e-mail or displaying a Web announcement that falsely claims to be from a legitimate enterprise in an attempt to trick the user into surrendering private information. a. dumpster diving c. computer hoax b. phishing d. ...
Some Tools for Computer Security Incident Response
... Snort is a free and open source network intrusion prevention system (NIPS) and network intrusion detection system (NIDS). Snort’s has the ability to perform real-time traffic analysis and packet logging on Internet Protocol (IP) networks. Snort performs protocol analysis, content searching, and cont ...
... Snort is a free and open source network intrusion prevention system (NIPS) and network intrusion detection system (NIDS). Snort’s has the ability to perform real-time traffic analysis and packet logging on Internet Protocol (IP) networks. Snort performs protocol analysis, content searching, and cont ...
What is Penetration Testing?
... in a system. It reveals potential security vulnerabilities or changes in the network which can be exploited by an attacker for malicious intent. ...
... in a system. It reveals potential security vulnerabilities or changes in the network which can be exploited by an attacker for malicious intent. ...
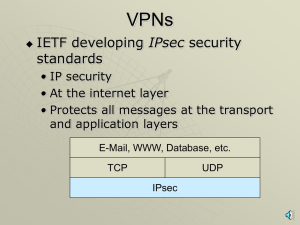
VPNs, PKIs, ISSs, SSLs with narration
... • Browser may authenticate itself but rarely does • Browser selects a symmetric session key, sends to webserver • Adds a digital signature and encrypts all messages with the symmetric key ...
... • Browser may authenticate itself but rarely does • Browser selects a symmetric session key, sends to webserver • Adds a digital signature and encrypts all messages with the symmetric key ...
Computer Networking and Security
... The course provides an introduction to the computer hardware and software skills as well as introductory networking skills needed to help meet the growing demand for entry-level information and communication technology (ICT) professionals. The curriculum covers the fundamentals of PC technology and ...
... The course provides an introduction to the computer hardware and software skills as well as introductory networking skills needed to help meet the growing demand for entry-level information and communication technology (ICT) professionals. The curriculum covers the fundamentals of PC technology and ...
Secure Deduplication with Efficient and Reliable
... supports both file-level and block level Deduplication. Security analysis demonstrates that Dekey is secure in terms of the definitions specified in the proposed security model. In particular, Dekey remains secure even the adversary controls a limited number of key servers. We implement Dekey using ...
... supports both file-level and block level Deduplication. Security analysis demonstrates that Dekey is secure in terms of the definitions specified in the proposed security model. In particular, Dekey remains secure even the adversary controls a limited number of key servers. We implement Dekey using ...
STUXNET - Clemson
... should be able to respond to cyber attacks "with overwhelming force," he added countries need not "respond to virtual attacks with real attacks but I do think it's important to define when and how it might be appropriate to respond. Everyone needs to understand to rules of the game." Acknowledging t ...
... should be able to respond to cyber attacks "with overwhelming force," he added countries need not "respond to virtual attacks with real attacks but I do think it's important to define when and how it might be appropriate to respond. Everyone needs to understand to rules of the game." Acknowledging t ...
Global Challenges
... • The adoption of common technical standards can also help developing countries and bring them up to speed (bridging the standardization gap) ...
... • The adoption of common technical standards can also help developing countries and bring them up to speed (bridging the standardization gap) ...
Assessing Network Security for Northwind Traders What
... Using Vulnerability Scanning to Assess Network Security Develop a process for vulnerability scanning that will do the following: Detect vulnerabilities Assign risk levels to discovered vulnerabilities Identify vulnerabilities that have not been remediated Determine improvement in network security o ...
... Using Vulnerability Scanning to Assess Network Security Develop a process for vulnerability scanning that will do the following: Detect vulnerabilities Assign risk levels to discovered vulnerabilities Identify vulnerabilities that have not been remediated Determine improvement in network security o ...
Final bits of OS - Department of Computer Science
... • Result: a transport allowing hosts to send IP event notification messages to syslog servers – provides a very general message format – allowing processes and applications to use suitable conventions for ...
... • Result: a transport allowing hosts to send IP event notification messages to syslog servers – provides a very general message format – allowing processes and applications to use suitable conventions for ...