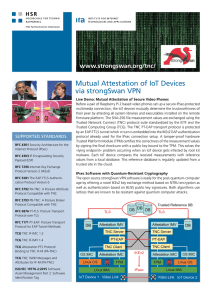
Mutual Attestation of IoT Devices via strongSwan VPN
... Trusted Network Connect (TNC) protocol suite standardized by the IETF and the Trusted Computing Group (TCG). The TNC PT-EAP transport protocol is protected by an EAP-TTLS tunnel which in turn is embedded into the IKEv2 EAP authentication protocol already used for the IPsec connection setup. A tamper ...
... Trusted Network Connect (TNC) protocol suite standardized by the IETF and the Trusted Computing Group (TCG). The TNC PT-EAP transport protocol is protected by an EAP-TTLS tunnel which in turn is embedded into the IKEv2 EAP authentication protocol already used for the IPsec connection setup. A tamper ...
Guidance for when No PP Exists
... NIAP will only accept products for evaluation against Protection Profiles (i.e. Security Target-based evaluations are not accepted within NIAP), this guidance explains options for vendors and end users when a suitable Protection Profile is not available for certain products. NIAP takes several facto ...
... NIAP will only accept products for evaluation against Protection Profiles (i.e. Security Target-based evaluations are not accepted within NIAP), this guidance explains options for vendors and end users when a suitable Protection Profile is not available for certain products. NIAP takes several facto ...
Hardware Building Blocks and Encoding
... Internet for the telephone system as the underlying structure for communications. The trusted VPN components of the new VPN still do not offer security but they give customers a way to easily create network segments for wide area networks (WANs). On the other hand, the secure VPN components can be c ...
... Internet for the telephone system as the underlying structure for communications. The trusted VPN components of the new VPN still do not offer security but they give customers a way to easily create network segments for wide area networks (WANs). On the other hand, the secure VPN components can be c ...
Windows Server 2012 Dynamic Access Control Deep Dive for Active
... • Automatic RMS encryption based on classification ...
... • Automatic RMS encryption based on classification ...
Document
... campaigns. Without these, advertisers and brands face low performance and reduced ROI of their marketing campaigns. When starting to build mobile number lists, enterprises must use strictly opt-in. Consumer numbers collected through opt-in are highly relevant and targeted, thus permission-based SMS ...
... campaigns. Without these, advertisers and brands face low performance and reduced ROI of their marketing campaigns. When starting to build mobile number lists, enterprises must use strictly opt-in. Consumer numbers collected through opt-in are highly relevant and targeted, thus permission-based SMS ...
Internet Security
... Typically less restrictive than in-bound But – good citizenship make it more difficult for hackers A packet filter can reject outbound packets with illegal ...
... Typically less restrictive than in-bound But – good citizenship make it more difficult for hackers A packet filter can reject outbound packets with illegal ...
Extreme Networks Supports Wireless Mobility at Patient Bedside for
... In order to allow the use of mobile ward rounds in a hospital environment, a resilient network architecture is necessary to support the required high network availability. The hospital has chosen Extreme Networks for its infrastructure, with the redundancy provided by Extreme Standby Router Protocol ...
... In order to allow the use of mobile ward rounds in a hospital environment, a resilient network architecture is necessary to support the required high network availability. The hospital has chosen Extreme Networks for its infrastructure, with the redundancy provided by Extreme Standby Router Protocol ...
Department of Information Resources, State
... • Risk analysis is part of due diligence for investors, too! • It demonstrates that your company is aware of the environment. • It’s often wise to have a third party do an initial risk analysis. ...
... • Risk analysis is part of due diligence for investors, too! • It demonstrates that your company is aware of the environment. • It’s often wise to have a third party do an initial risk analysis. ...
Computer Ethics
... A social network service focuses on building and reflecting of social networks or social relations among people, e.g., who share interests and/or activities. A social network service essentially consists of a representation of each user (often a profile), his/her social links, and a variety of add ...
... A social network service focuses on building and reflecting of social networks or social relations among people, e.g., who share interests and/or activities. A social network service essentially consists of a representation of each user (often a profile), his/her social links, and a variety of add ...
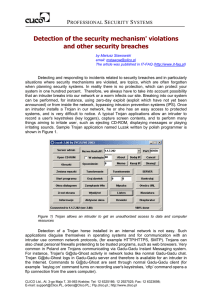
Detection of the security mechanism` violations and other
... have little features allowing detection of security breaches and in particular situations where protections were broken. Usually their functionality in this respect is limited to recognizing known network attacks (exploit, DoS) and discrepancies in network communication when compared to RFC standard ...
... have little features allowing detection of security breaches and in particular situations where protections were broken. Usually their functionality in this respect is limited to recognizing known network attacks (exploit, DoS) and discrepancies in network communication when compared to RFC standard ...
Rapid Response to the Advanced Persistent Threat (APT)
... will at some point attempt to access the target data, whether this is immediately or a period of time after the initial breach has occurred. By performing lightweight recording of all interaction with the data and measuring this against expected policy or behaviour, ZoneFox immediately provides a de ...
... will at some point attempt to access the target data, whether this is immediately or a period of time after the initial breach has occurred. By performing lightweight recording of all interaction with the data and measuring this against expected policy or behaviour, ZoneFox immediately provides a de ...
abstract - Chennaisunday.com
... successful PKI, such as insurance and legal aspects, have been greatly improved. The Public-key system makes it possible for two parties to communicate securely without either having to know or trust the other party. However, this is only possible because a third party that both the other parties tr ...
... successful PKI, such as insurance and legal aspects, have been greatly improved. The Public-key system makes it possible for two parties to communicate securely without either having to know or trust the other party. However, this is only possible because a third party that both the other parties tr ...
Essentials of Security
... Strive for systems that are secure by design Apply the principle of least privilege ...
... Strive for systems that are secure by design Apply the principle of least privilege ...
updated system threat and requirements analysis for high assurance
... 802.11 Wireless Fidelity (WIFI), are susceptible to wireless hacking [1] [2] [3]. “Blended” attacks against commercial wireless interfaces have been studied by standardization groups such as the 3rd Generation Partnership Program [4]. Five attack methods (unauthorized access to data, threats to inte ...
... 802.11 Wireless Fidelity (WIFI), are susceptible to wireless hacking [1] [2] [3]. “Blended” attacks against commercial wireless interfaces have been studied by standardization groups such as the 3rd Generation Partnership Program [4]. Five attack methods (unauthorized access to data, threats to inte ...
Symbolic Honeynets for Gathering Cyber
... ● uses SHODAN to detect how many ICS systems are connected to internet EACH DAY: ● 2000-8000 NEW ICS on internet PER DAY ...
... ● uses SHODAN to detect how many ICS systems are connected to internet EACH DAY: ● 2000-8000 NEW ICS on internet PER DAY ...
CS5038: The Electronic Society - Homepages | The University of
... Targets for all of C, I, and A are 0. When the shock hits, C (blue) is way below target. This causes spend (red) to go way above target, and system availability to go way below target; that is, the system’s operations have to be curtailed and money spent to fix the problem; with these actions taken, ...
... Targets for all of C, I, and A are 0. When the shock hits, C (blue) is way below target. This causes spend (red) to go way above target, and system availability to go way below target; that is, the system’s operations have to be curtailed and money spent to fix the problem; with these actions taken, ...
AIS-Talk-Bhavani-200.. - The University of Texas at Dallas
... • More recently joint work with UMBC, UTSA, MIT (SACMAT 2008) ...
... • More recently joint work with UMBC, UTSA, MIT (SACMAT 2008) ...
LSD1518 - Control Cloud Data Access Privilege
... schemes based on the attribute-based encryption have been proposed to secure the cloud storage. However, most work focuses on the data contents privacy and the access control, while less attention is paid to the privilege control and the identity privacy. In this paper, we present a semi-anonymous p ...
... schemes based on the attribute-based encryption have been proposed to secure the cloud storage. However, most work focuses on the data contents privacy and the access control, while less attention is paid to the privilege control and the identity privacy. In this paper, we present a semi-anonymous p ...
Europe`s World - Growing Cyber Threats Demand
... Raytheon Company It seems like every day that we hear about the growing cyber threat environment, whether from nation states trying to steal intellectual property, cyber criminals attempting to steal credit information or money, or just political activists who want to emphasize one cause or another. ...
... Raytheon Company It seems like every day that we hear about the growing cyber threat environment, whether from nation states trying to steal intellectual property, cyber criminals attempting to steal credit information or money, or just political activists who want to emphasize one cause or another. ...
Out Of The Blue - Joshua`s Learning Log
... cover 100-300 feet indoors and up to 600-1000 feet in open space. However, when accessed points are placed at maximum range, they tend to suffer from poor connections and intermittent service. Finally, the number of users that can access a network is typically left to the manufacturer of the access ...
... cover 100-300 feet indoors and up to 600-1000 feet in open space. However, when accessed points are placed at maximum range, they tend to suffer from poor connections and intermittent service. Finally, the number of users that can access a network is typically left to the manufacturer of the access ...
01 - Quick Heal
... What does it do? • It allows attackers to remotely access an infected system. • Systems infected by this worm can be used to launch distributed denial of service (DDoS) attacks. • It may be used to install additional Trojan malware or other forms of malicious software. • It might also open ports on ...
... What does it do? • It allows attackers to remotely access an infected system. • Systems infected by this worm can be used to launch distributed denial of service (DDoS) attacks. • It may be used to install additional Trojan malware or other forms of malicious software. • It might also open ports on ...