Curriculum Vitae
... Dealing with French, Belgian & German Total users 's escalations - Active Directory management - Administrative software test and validation process - Initiative : Development of a VBS-WSH script to improve the productivity of the whole team – still in use today - 5 agents team work March 2006 ...
... Dealing with French, Belgian & German Total users 's escalations - Active Directory management - Administrative software test and validation process - Initiative : Development of a VBS-WSH script to improve the productivity of the whole team – still in use today - 5 agents team work March 2006 ...
Lecture12
... of subjects to objects are in accordance with a security policy. To determine whether a specific access mode is allowed, the clearance of a subject is compared to the classification of the object (more precisely, to the combination of classification and set of compartments, making up the security le ...
... of subjects to objects are in accordance with a security policy. To determine whether a specific access mode is allowed, the clearance of a subject is compared to the classification of the object (more precisely, to the combination of classification and set of compartments, making up the security le ...
VPN in the spotlight of IT- Security
... “know how” to install and maintenance a virtual private network. Overall a VPN reaches the aimed protection targets and shows that locationindependent work is no longer a future dream. There are manifold applications of a VPN, to connect field managers with the company’s network, the connection of t ...
... “know how” to install and maintenance a virtual private network. Overall a VPN reaches the aimed protection targets and shows that locationindependent work is no longer a future dream. There are manifold applications of a VPN, to connect field managers with the company’s network, the connection of t ...
security in the post-Internet era
... Nebula existence proof: security in an open network DDOS attacks: defense-in-depth is a Good Thing controlling net devices is hard --hublets, wireless security via static IP configuration does not scale never underestimate non-technical barriers to progress 21 ...
... Nebula existence proof: security in an open network DDOS attacks: defense-in-depth is a Good Thing controlling net devices is hard --hublets, wireless security via static IP configuration does not scale never underestimate non-technical barriers to progress 21 ...
ASG-Sentry White Paper
... correlates large amounts of real-time message data sent by diverse types of computer systems, including Windows, all flavors of UNIX and Linux, as well as network routers, firewalls, application programs, and mainframe computers. Unlike the ASG-Sentry program, Correlog Server does not poll the netwo ...
... correlates large amounts of real-time message data sent by diverse types of computer systems, including Windows, all flavors of UNIX and Linux, as well as network routers, firewalls, application programs, and mainframe computers. Unlike the ASG-Sentry program, Correlog Server does not poll the netwo ...
Designing a future Internet: Architecture and requirements
... In a virtual network, facilities (routers, links, etc.) are virtualized and then used by higher-level service providers to implement different networks, possibly using very different architectures. ...
... In a virtual network, facilities (routers, links, etc.) are virtualized and then used by higher-level service providers to implement different networks, possibly using very different architectures. ...
Hackers and the Internet Seid Alimostafa Sanglakhi
... This could include the destruction or loss of critical information. All information is available on the victim computer. For this purpose, viruses have been reproduced in the system, and they use different tools such as diskettes and CD or mail to infect other users within a short time. A virus can ...
... This could include the destruction or loss of critical information. All information is available on the victim computer. For this purpose, viruses have been reproduced in the system, and they use different tools such as diskettes and CD or mail to infect other users within a short time. A virus can ...
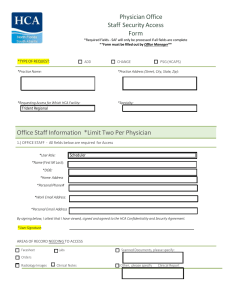
Physician Office Staff Security Access Form Office Staff Information
... 18. I understand that I will be assigned a unique identifier (e.g., 3-4 User ID) to track my access and use of Confidential Information and that the identifier is associated with my personal data provided as part of the initial and/or periodic credentialing and/or employment verification processes. ...
... 18. I understand that I will be assigned a unique identifier (e.g., 3-4 User ID) to track my access and use of Confidential Information and that the identifier is associated with my personal data provided as part of the initial and/or periodic credentialing and/or employment verification processes. ...
Computer and System Logging Policy
... Logs shall be reviewed on a regular and on-going basis. The frequency of review shall be determined according to the sensitivity of the information stored, the function of the system, and other system requirements as determined by the [Insert Appropriate Role]. Procedures should verify that logging ...
... Logs shall be reviewed on a regular and on-going basis. The frequency of review shall be determined according to the sensitivity of the information stored, the function of the system, and other system requirements as determined by the [Insert Appropriate Role]. Procedures should verify that logging ...
Threats and Attacks
... quantities of e-mail to target § Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network § Social engineering: using social skills to convince people to reveal access credentials or other valuable ...
... quantities of e-mail to target § Sniffers: program or device that monitors data traveling over network; can be used both for legitimate purposes and for stealing information from a network § Social engineering: using social skills to convince people to reveal access credentials or other valuable ...
Insert Title Here
... Escrow mechanisms are a security hazard If required, perform at key generation, in the physical presence of humans Physically export Key Encryption Key and protect Export other keys encrypted with Key Encryption Key ...
... Escrow mechanisms are a security hazard If required, perform at key generation, in the physical presence of humans Physically export Key Encryption Key and protect Export other keys encrypted with Key Encryption Key ...
Auditing (cont'd.) - Elgin Community College
... • Stop logged-on users from accessing files and folders that they are not assigned read or write permission to • Relatively easy to work around NTFS permissions • When you have physical access to the computer • To secure data on desktop computers and laptops, ...
... • Stop logged-on users from accessing files and folders that they are not assigned read or write permission to • Relatively easy to work around NTFS permissions • When you have physical access to the computer • To secure data on desktop computers and laptops, ...
presentation
... In this design, computers are connected via a single cable, but the end nodes also are connected to each other. In this design, the signal circulates through the network until it finds the intended recipient. If a network node is not configured properly, or it is down temporarily for another reason, ...
... In this design, computers are connected via a single cable, but the end nodes also are connected to each other. In this design, the signal circulates through the network until it finds the intended recipient. If a network node is not configured properly, or it is down temporarily for another reason, ...
Incident Response: Six Steps for Managing Cyber Breaches
... This is where your proactive sensitive data auditing against a predefined baseline of where your data is and should be stored can save you significant time. With the data map in hand, you are two giant steps closer to knowing which data was the likely target of the malware. The ability to scope the ...
... This is where your proactive sensitive data auditing against a predefined baseline of where your data is and should be stored can save you significant time. With the data map in hand, you are two giant steps closer to knowing which data was the likely target of the malware. The ability to scope the ...
Payment Card Industry Security Standards
... of full magnetic stripe data located on the back of a payment card. PA-DSS covers commercial payment applications, integrators and service providers. Merchants and service providers should use certified payment applications and should check with their acquiring financial institution to understand re ...
... of full magnetic stripe data located on the back of a payment card. PA-DSS covers commercial payment applications, integrators and service providers. Merchants and service providers should use certified payment applications and should check with their acquiring financial institution to understand re ...
Using port pairing to simplify transparent mode
... Using port pairing to simplify transparent mode When you create a port pair, all traffic accepted by one of the paired ports can only exit out the other port. Restricting traffic in this way simplifies your FortiGate configuration because security policies between these interfaces are preconfigured. ...
... Using port pairing to simplify transparent mode When you create a port pair, all traffic accepted by one of the paired ports can only exit out the other port. Restricting traffic in this way simplifies your FortiGate configuration because security policies between these interfaces are preconfigured. ...
Robust. Reliable. Factory Line. Industrial Security redefined protecting industrial networks
... concepts. The new mGuard factory line offers high-end industrial security in the form of an extremely powerful and fail-safe product portfolio, which is also ideal for high-availability scenarios and complex security architectures. Security for production The mGuard rs4000 is perfectly suited for th ...
... concepts. The new mGuard factory line offers high-end industrial security in the form of an extremely powerful and fail-safe product portfolio, which is also ideal for high-availability scenarios and complex security architectures. Security for production The mGuard rs4000 is perfectly suited for th ...
Penetration Testing Report - Network Intelligence India
... Filter User Input – Users input can have malicious characters which may result in attacks like SQL injection, XSS etc. Use stored procedures- To mitigate the risk from SQL injection, in addition to user input validation, stored procedures should also be used. Avoid username enumeration – Display con ...
... Filter User Input – Users input can have malicious characters which may result in attacks like SQL injection, XSS etc. Use stored procedures- To mitigate the risk from SQL injection, in addition to user input validation, stored procedures should also be used. Avoid username enumeration – Display con ...
Prerequisite Revision Review Prefix & Course #
... Has the Department gone through common course review? x□Yes □No □In process If Yes or In Process please use new rubric / numbers. Rationale The change will ensure students will have the proper background before attempting the course and allow for flexibility in scheduling. II. Endorsement/Approval ...
... Has the Department gone through common course review? x□Yes □No □In process If Yes or In Process please use new rubric / numbers. Rationale The change will ensure students will have the proper background before attempting the course and allow for flexibility in scheduling. II. Endorsement/Approval ...
D efe ns iv
... of advanced techniques used by the most sophisticated attackers to maintain stealth and security while minimizing their footprint and identity. Locating the Cyber Ninja ...
... of advanced techniques used by the most sophisticated attackers to maintain stealth and security while minimizing their footprint and identity. Locating the Cyber Ninja ...
Security Analysis of a Single Sign
... credentials,” demonstrates how an outside attacker may be able to freely make use of resources and services offered by service providers, since the attacker can successfully impersonate a legal user without holding a valid credential and thus violate the requirement of soundness for an SSO scheme. I ...
... credentials,” demonstrates how an outside attacker may be able to freely make use of resources and services offered by service providers, since the attacker can successfully impersonate a legal user without holding a valid credential and thus violate the requirement of soundness for an SSO scheme. I ...
OWASP`s Ten Most Critical Web Application Security Vulnerabilities
... Loss of authentication and access control for users ...
... Loss of authentication and access control for users ...
Shibboleth Access Management System
... containing video footage of historically important NASA space flights The web site’s interface must be adaptable for users with disabilities - A user with low vision prefers custom colors, font face, and font size. - A user with hand tremors might prefer bigger links and buttons. ...
... containing video footage of historically important NASA space flights The web site’s interface must be adaptable for users with disabilities - A user with low vision prefers custom colors, font face, and font size. - A user with hand tremors might prefer bigger links and buttons. ...