AISE PoIS4E_PP_ch02_48
... • Illegal taking of another’s physical, electronic, or intellectual property • Physical theft is controlled relatively easily • Electronic theft is more complex problem; evidence of crime not readily apparent ...
... • Illegal taking of another’s physical, electronic, or intellectual property • Physical theft is controlled relatively easily • Electronic theft is more complex problem; evidence of crime not readily apparent ...
CHAPTER 1 THE INTRUSION DETECTION SYSTEM
... they allow network administrators to detect policy violations. These policy violations range from external attackers trying to gain unauthorized access to insiders abusing their access. ...
... they allow network administrators to detect policy violations. These policy violations range from external attackers trying to gain unauthorized access to insiders abusing their access. ...
Peer Router retains public key on routing table Route discovery
... While roving around the venue, visitors keep receiving propositions and suggestions when their terminals are located by nearby radio transmitters. Privacy-conscious visitors can opt to be anonymous. ...
... While roving around the venue, visitors keep receiving propositions and suggestions when their terminals are located by nearby radio transmitters. Privacy-conscious visitors can opt to be anonymous. ...
macro virus - University of Windsor
... from a Unix system. Several Linux viruses have been discovered. The Staog virus first appeared in 1996 and was written in assembly language by the VLAD virus writing group, the same group responsible for creating the first Windows 95 virus called Boza. Like the Boza virus, the Staog virus is a proof ...
... from a Unix system. Several Linux viruses have been discovered. The Staog virus first appeared in 1996 and was written in assembly language by the VLAD virus writing group, the same group responsible for creating the first Windows 95 virus called Boza. Like the Boza virus, the Staog virus is a proof ...
HSARPA Cyber Security R&D
... destined for any service or port in a target machine in order to prevent the spread of destructive code through networks and applications. These technologies should focus on detecting “zero day attacks”, the first appearance of malicious code for which no known defense has been constructed. 23 Septe ...
... destined for any service or port in a target machine in order to prevent the spread of destructive code through networks and applications. These technologies should focus on detecting “zero day attacks”, the first appearance of malicious code for which no known defense has been constructed. 23 Septe ...
Managing security risks and vulnerabilities
... resolution to help improve their security posture. These solutions can generate meaningful data from activity associated with people, data, applications and infrastructure, and then pull all of that data into a single repository. What’s more, organizations can apply advanced analytics to that data—w ...
... resolution to help improve their security posture. These solutions can generate meaningful data from activity associated with people, data, applications and infrastructure, and then pull all of that data into a single repository. What’s more, organizations can apply advanced analytics to that data—w ...
Chapter 12
... • Designed to make it easy for users to adjust their legacy applications to work with Windows 7 • Without having to know a lot about compatibility settings ...
... • Designed to make it easy for users to adjust their legacy applications to work with Windows 7 • Without having to know a lot about compatibility settings ...
Marc Visnick_Slides
... Not inherently nefarious; simply means: Non-searchable (by standard search engines) ...
... Not inherently nefarious; simply means: Non-searchable (by standard search engines) ...
Ch06-Firewalls
... private network that is referred to as an intranet. – For example, an organization may wish to allow employees access to the company network remotely but make it appear as though they are local to their system and even the Internet itself. – To accomplish this, the organization sets up a VPN endpoin ...
... private network that is referred to as an intranet. – For example, an organization may wish to allow employees access to the company network remotely but make it appear as though they are local to their system and even the Internet itself. – To accomplish this, the organization sets up a VPN endpoin ...
Cybersecurity for Critical Control Systems in the Power Industry
... In the second incident, a third-party technician installed software upgrades for a turbine control system using an infected USB drive. Consequently, the Mariposa virus spread to ten computers within the control systems network. The result was a delayed restart of the plant by three weeks. Human erro ...
... In the second incident, a third-party technician installed software upgrades for a turbine control system using an infected USB drive. Consequently, the Mariposa virus spread to ten computers within the control systems network. The result was a delayed restart of the plant by three weeks. Human erro ...
here - HOET
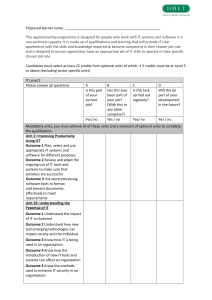
... Proposed learner name: _________________________________________________ This apprenticeship programme is designed for people who work with IT systems and software in a non-technical capacity. It is made up of qualifications and learning that will provide IT User apprentices with the skills and know ...
... Proposed learner name: _________________________________________________ This apprenticeship programme is designed for people who work with IT systems and software in a non-technical capacity. It is made up of qualifications and learning that will provide IT User apprentices with the skills and know ...
CCNPv5 Module 5 Lesson 1
... Inoculation: Start patching all systems and, if possible, scanning for vulnerable systems. Quarantine: Track down each infected machine inside your network. Disconnect, remove, or block infected machines from the network. Treatment: Clean and patch each infected system. Some worms may require comple ...
... Inoculation: Start patching all systems and, if possible, scanning for vulnerable systems. Quarantine: Track down each infected machine inside your network. Disconnect, remove, or block infected machines from the network. Treatment: Clean and patch each infected system. Some worms may require comple ...
Topic 2: Lesson 3 Intro to Firewalls
... Protect internal network from outside threats creates choke point from outside of network mechanism that permits access control between two or more networks come in various forms: hardware and software, usually a combination ...
... Protect internal network from outside threats creates choke point from outside of network mechanism that permits access control between two or more networks come in various forms: hardware and software, usually a combination ...
9781435420168_PPT_CH01
... Buffer overflow: application error occurs when more data is sent to buffer than it can handle; when buffer overflows, attacker can make target system execute instructions or attacker can take advantage of some other unintended consequence of the failure Timing attack: relatively new, works by ex ...
... Buffer overflow: application error occurs when more data is sent to buffer than it can handle; when buffer overflows, attacker can make target system execute instructions or attacker can take advantage of some other unintended consequence of the failure Timing attack: relatively new, works by ex ...
Firewalls: An Effective Solution for Internet Security
... personnel into providing information required to access systems. Intruders usually solicit password for user accounts, but information about the network infrastructure and the identity of individual hosts can also be the target of social engineering attacks. ...
... personnel into providing information required to access systems. Intruders usually solicit password for user accounts, but information about the network infrastructure and the identity of individual hosts can also be the target of social engineering attacks. ...
- Whatcom Community College
... • It is estimated that, by 2020, there will be as many as 50 billion or more Internetconnected devices (sensors, processors, actuators), most of these directly supporting the nation’s critical infrastructure systems. • Most of these will be controlled remotely, across the public Internet, from perso ...
... • It is estimated that, by 2020, there will be as many as 50 billion or more Internetconnected devices (sensors, processors, actuators), most of these directly supporting the nation’s critical infrastructure systems. • Most of these will be controlled remotely, across the public Internet, from perso ...
PowerPoint Slides
... Discuss techniques to prevent unauthorized computer access and use Identify safeguards against hardware theft and vandalism Explain the ways software manufacturers protect against software piracy Define encryption and explain why it is ...
... Discuss techniques to prevent unauthorized computer access and use Identify safeguards against hardware theft and vandalism Explain the ways software manufacturers protect against software piracy Define encryption and explain why it is ...
Public Key Encryption and Digital Signatures
... problems with allowable exports, and are not always allowed to talk about their work. • Is it desirable to have government able to crack all codes? • What is the tradeoff between privacy of law abiding citizens vs. the ability of terrorists and drug traffickers to communicate in secret? ...
... problems with allowable exports, and are not always allowed to talk about their work. • Is it desirable to have government able to crack all codes? • What is the tradeoff between privacy of law abiding citizens vs. the ability of terrorists and drug traffickers to communicate in secret? ...
Syllabus - Skills Commons
... implied, with respect to such information, including any information on linked sites, and including, but not limited to accuracy of the information or its completeness, timeliness, usefulness, adequacy, continued availability or ownership. ...
... implied, with respect to such information, including any information on linked sites, and including, but not limited to accuracy of the information or its completeness, timeliness, usefulness, adequacy, continued availability or ownership. ...
Oracle9i Security
... environments by defining the protocol for interaction between provisioning service components and agents representing provisioned services. ...
... environments by defining the protocol for interaction between provisioning service components and agents representing provisioned services. ...
ppt
... of the components of a communication system. A technique used to define or restrict the rights of individuals or application programs to obtain data from, or place data onto, a storage device. The definition or restriction of the rights of individuals or application programs to obtain data from, or ...
... of the components of a communication system. A technique used to define or restrict the rights of individuals or application programs to obtain data from, or place data onto, a storage device. The definition or restriction of the rights of individuals or application programs to obtain data from, or ...
IEEE 802.11 Overview and Meshed Networking
... A now out of range… E – F, ⅛ throughput F – G, ⅛ throughput ...
... A now out of range… E – F, ⅛ throughput F – G, ⅛ throughput ...
Protection Mechanisms
... All Internet Control Message Protocol (ICMP) data should be denied Telnet (terminal emulation) access to all internal servers from the public networks should be blocked When Web services are offered outside the firewall, HTTP traffic should be handled by some form of proxy access or DMZ archit ...
... All Internet Control Message Protocol (ICMP) data should be denied Telnet (terminal emulation) access to all internal servers from the public networks should be blocked When Web services are offered outside the firewall, HTTP traffic should be handled by some form of proxy access or DMZ archit ...
Integrate and Accelerate Endpoint Threat Defense
... methods to keep their endpoints—and data—safe. Even worse, explosive growth in endpoints and mobility have opened new potential attack vectors for cybercriminals and new places for malware to hide. In attempt to head off every potential point of weakness, many organizations now rely on a patchwork o ...
... methods to keep their endpoints—and data—safe. Even worse, explosive growth in endpoints and mobility have opened new potential attack vectors for cybercriminals and new places for malware to hide. In attempt to head off every potential point of weakness, many organizations now rely on a patchwork o ...
Guide to Firewalls and Network Security with Intrusion Detection and
... Importance of observing fundamental principles of network security when maintaining the firewall Importance of being able to manage the firewall remotely and having log files for review Responding to security incidents Advanced firewall functions ...
... Importance of observing fundamental principles of network security when maintaining the firewall Importance of being able to manage the firewall remotely and having log files for review Responding to security incidents Advanced firewall functions ...