Chapter 8: Network Security
... Websites have also been subject to Denial of Service (DoS) attacks, during which would-be customers are unable to access the website because it is being overwhelmed by bogus requests. Ensuring a degree of access is called availability. ...
... Websites have also been subject to Denial of Service (DoS) attacks, during which would-be customers are unable to access the website because it is being overwhelmed by bogus requests. Ensuring a degree of access is called availability. ...
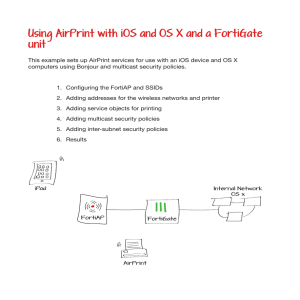
Using AirPrint with iOS and OS X and a FortiGate unit
... AirPrint printer and enable DHCP Server. ...
... AirPrint printer and enable DHCP Server. ...
Lottery`s Log Management Business Objectives
... Lottery’s Log Management Business Objectives 1. Security Operations: Security policies and systems are operating as planned 2. IT Operations: Determine whether IT operations can be improved and whether they are susceptible to issues 3. Forensics: Capture admissible proof that could serve as evidenc ...
... Lottery’s Log Management Business Objectives 1. Security Operations: Security policies and systems are operating as planned 2. IT Operations: Determine whether IT operations can be improved and whether they are susceptible to issues 3. Forensics: Capture admissible proof that could serve as evidenc ...
Hands-On Ethical Hacking and Network Security
... Most companies have Wireless LANs (WLANs) that ...
... Most companies have Wireless LANs (WLANs) that ...
Security - Ingate Systems
... Generally consists of the concerted efforts to prevent SIP communications service from functioning efficiently or at all, temporarily or indefinitely One common method of attack involves saturating the target (victim) IP-PBX with external communications requests, such that it cannot respond to l ...
... Generally consists of the concerted efforts to prevent SIP communications service from functioning efficiently or at all, temporarily or indefinitely One common method of attack involves saturating the target (victim) IP-PBX with external communications requests, such that it cannot respond to l ...
VIRTUAL PRIVATE NETWORK
... Data Encryption Data sent and received over the Internet must be encrypted for privacy Microsoft Implementation of these protocols uses IPSec encryption to protect the data stream from the client to the tunnel server. ...
... Data Encryption Data sent and received over the Internet must be encrypted for privacy Microsoft Implementation of these protocols uses IPSec encryption to protect the data stream from the client to the tunnel server. ...
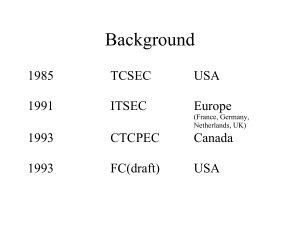
Common Criteria
... IT security evaluation. • Provides constructs for defining and selecting security objectives • Provides guidelines for writing high-level specifications ...
... IT security evaluation. • Provides constructs for defining and selecting security objectives • Provides guidelines for writing high-level specifications ...
Springfield Data Center Program Alignment
... Security Incident and Event Management system *Log Management: Collects, stores, and mines all network, security, and application information from IT infrastructures. * Threat Management: Correlates and detects threats across heterogeneous network and security technologies. * Compliance Management: ...
... Security Incident and Event Management system *Log Management: Collects, stores, and mines all network, security, and application information from IT infrastructures. * Threat Management: Correlates and detects threats across heterogeneous network and security technologies. * Compliance Management: ...
PCI DSS glossary of terms - PCI Security Standards Council
... Also known as Card Validation Code or Value, or Card Security Code. Refers to either: (1) magnetic-stripe data, or (2) printed security features. (1) Data element on a card's magnetic stripe that uses secure cryptographic processes to protect data integrity on the stripe, and reveals any alteration ...
... Also known as Card Validation Code or Value, or Card Security Code. Refers to either: (1) magnetic-stripe data, or (2) printed security features. (1) Data element on a card's magnetic stripe that uses secure cryptographic processes to protect data integrity on the stripe, and reveals any alteration ...
Joshua White - Everis Inc.
... IP spoofing is a technique used to gain unauthorized access to computers/networks The attacker sends messages to a computer using a forged IP address indicating that the message is coming from a trusted host ...
... IP spoofing is a technique used to gain unauthorized access to computers/networks The attacker sends messages to a computer using a forged IP address indicating that the message is coming from a trusted host ...
4061_26
... • When it infected a machine that had already been infected, 1/7 of the time it created another copy, anyhow – To bypass admins creating a fake copy to thwart the worm ...
... • When it infected a machine that had already been infected, 1/7 of the time it created another copy, anyhow – To bypass admins creating a fake copy to thwart the worm ...
Master - Anvari.Net
... • Often shared technologies between stateful inspection and signature recognition (“looking deep into the packet”) • Inline network IDS allows for instant access control policy modification ...
... • Often shared technologies between stateful inspection and signature recognition (“looking deep into the packet”) • Inline network IDS allows for instant access control policy modification ...
What is Security?
... What Is Network Security? Security is a continuous process of protecting an object from attack. That object may be a person, an organization such as a business, or property such as a computer system or a file. In a distributed computer system such as a network, the protection covers physical and no ...
... What Is Network Security? Security is a continuous process of protecting an object from attack. That object may be a person, an organization such as a business, or property such as a computer system or a file. In a distributed computer system such as a network, the protection covers physical and no ...
Slide 1
... • These devices securely encrypt cardholder data for transport over a network rendering it unreadable and as a result valueless to data thieves who frequently attempt to intercept the data while it is in transit to the processor. • Each encrypted card reader is injected with an encryption key, uniqu ...
... • These devices securely encrypt cardholder data for transport over a network rendering it unreadable and as a result valueless to data thieves who frequently attempt to intercept the data while it is in transit to the processor. • Each encrypted card reader is injected with an encryption key, uniqu ...
Juniper and Vectra Networks Add New Class of Advanced
... traffic must be continuously monitored for threat activity. Once potential attacks are identified, the threat must be contained and malicious activity blocked. Solution Juniper and Vectra’s joint solution adds a new class of advanced persistent threat (APT) defense, delivering real-time detection an ...
... traffic must be continuously monitored for threat activity. Once potential attacks are identified, the threat must be contained and malicious activity blocked. Solution Juniper and Vectra’s joint solution adds a new class of advanced persistent threat (APT) defense, delivering real-time detection an ...
Spec Sheet - NetComm Wireless
... Enjoy extended WiFi coverage with high-speed WiFi N, or connect up to four wired devices via the Gigabit Ethernet ports. The device also features a USB 2.0 port for external hard drive storage or an alternate Internet source with a compatible 3G/4G USB modem. The VoIP phone port allows users to make ...
... Enjoy extended WiFi coverage with high-speed WiFi N, or connect up to four wired devices via the Gigabit Ethernet ports. The device also features a USB 2.0 port for external hard drive storage or an alternate Internet source with a compatible 3G/4G USB modem. The VoIP phone port allows users to make ...
XML: Part - Houston Community College System
... (SSL)/Transport Layer Security (TLS), IP Security (IPSec), and Secure/Multipurpose Internet Mail ...
... (SSL)/Transport Layer Security (TLS), IP Security (IPSec), and Secure/Multipurpose Internet Mail ...
compatible-development-of
... under intense academic scrutiny which motivated the modern understanding of block ciphers and their cryptanalysis. Diffie and Hellman publish New Directions in Cryptography. Phil Zimmermann releases the public key encryption program PGP along with its source code, which quickly appears on the Intern ...
... under intense academic scrutiny which motivated the modern understanding of block ciphers and their cryptanalysis. Diffie and Hellman publish New Directions in Cryptography. Phil Zimmermann releases the public key encryption program PGP along with its source code, which quickly appears on the Intern ...
Intrusion Detection Technique by using K
... by using K-means, Fuzzy Neural Network and SVM classifiers. ...
... by using K-means, Fuzzy Neural Network and SVM classifiers. ...
LAN - IT352 : Network Security
... • By creating separate security zones, we will be able to enforce security policy with the appropriate firewall rules and layer 3 access lists. • This design lacks is the infrastructure for managing network. • These servers will form the foundation of our network management and security, a separate ...
... • By creating separate security zones, we will be able to enforce security policy with the appropriate firewall rules and layer 3 access lists. • This design lacks is the infrastructure for managing network. • These servers will form the foundation of our network management and security, a separate ...
Security management
... implementation and enforcement – It should be developed and used to integrated security into all business function and process – It should be derived from and support all legislation and regulation applicable to the company ...
... implementation and enforcement – It should be developed and used to integrated security into all business function and process – It should be derived from and support all legislation and regulation applicable to the company ...
Role of Web Application Vulnerabilities in Information
... More of white box testing Learn from previous learning experience ...
... More of white box testing Learn from previous learning experience ...
No Slide Title - ECE Users Pages - Georgia Institute of Technology
... viruses; port scanning; disrupting services; damaging files; or intentional destruction of or damage to equipment, software, or data. ECE 4883 - Internetwork Security ...
... viruses; port scanning; disrupting services; damaging files; or intentional destruction of or damage to equipment, software, or data. ECE 4883 - Internetwork Security ...
Managing the Digital Firm
... Criteria for Determining Control Structure • Importance of data • Cost effectiveness of control technique ...
... Criteria for Determining Control Structure • Importance of data • Cost effectiveness of control technique ...