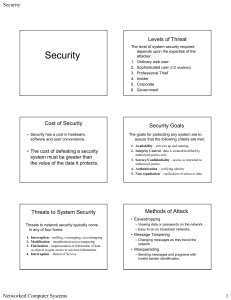
Blueprint For Security Chapter 6
... Benchmark and monitor the status of key system files and detect when intruder creates, modifies, or deletes files Most HIDSs work on the principle of configuration or change management Advantage over NIDS: can usually be installed so that it can access information encrypted when traveling over ...
... Benchmark and monitor the status of key system files and detect when intruder creates, modifies, or deletes files Most HIDSs work on the principle of configuration or change management Advantage over NIDS: can usually be installed so that it can access information encrypted when traveling over ...
Security Assessment Questionnaire
... This is an assessment of the functionality and resilience of the compiled application to known threats. This assessment focuses on the compiled and installed elements of the entire system: how the application components are deployed, communicate or otherwise interact with both the user and server en ...
... This is an assessment of the functionality and resilience of the compiled application to known threats. This assessment focuses on the compiled and installed elements of the entire system: how the application components are deployed, communicate or otherwise interact with both the user and server en ...
Information Assurance Awareness, Training, Education at the U.S.
... “An effective information security program should include … security awareness training to inform personnel of the information security risks associated with their activities and responsibilities in complying with organizational policies and procedures designed to reduce these risks” ...
... “An effective information security program should include … security awareness training to inform personnel of the information security risks associated with their activities and responsibilities in complying with organizational policies and procedures designed to reduce these risks” ...
Slides on Security
... from the outside world into a private network. • Firewalls can be implemented in a router. • A firewall can restrict certain types of traffic activity on a network based on: – Source or destination IP address – Port number – Protocol – data contents (virus scanning) ...
... from the outside world into a private network. • Firewalls can be implemented in a router. • A firewall can restrict certain types of traffic activity on a network based on: – Source or destination IP address – Port number – Protocol – data contents (virus scanning) ...
Project proposal
... • In short, to get any functionality out of a Bluetooth device, one needs to implement pretty high stack of protocol layers, quite similar to OSI referent model • If you buy a Bluetooth device, you get that stack already implemented, and it exposes profiles(services) to the user, such as Serial port ...
... • In short, to get any functionality out of a Bluetooth device, one needs to implement pretty high stack of protocol layers, quite similar to OSI referent model • If you buy a Bluetooth device, you get that stack already implemented, and it exposes profiles(services) to the user, such as Serial port ...
Slide 1
... attached to the Internet you need to add packet filters to the Internet interface that only allow VPN traffic to and from the IP address of the VPN server's interface on the Internet. For inbound traffic, when the tunneled data is decrypted by the VPN server it is forwarded to the firewall, which em ...
... attached to the Internet you need to add packet filters to the Internet interface that only allow VPN traffic to and from the IP address of the VPN server's interface on the Internet. For inbound traffic, when the tunneled data is decrypted by the VPN server it is forwarded to the firewall, which em ...
Example: Data Mining for the NBA - The University of Texas at Dallas
... multiple, overlapping ATIs at any layer. Furthermore, concrete diverse implementations may exist for the same or different ATIs (e.g., Intel TXT and AMD SVM at the hardware layer). One of the main design goals of the ATI Architecture is the active incorporation of diverse designs and implementations ...
... multiple, overlapping ATIs at any layer. Furthermore, concrete diverse implementations may exist for the same or different ATIs (e.g., Intel TXT and AMD SVM at the hardware layer). One of the main design goals of the ATI Architecture is the active incorporation of diverse designs and implementations ...
module_70
... includes the public key of the server. The public key is certified by some certification authority, which means that the public key is encrypted by a CA private key. Browser has a list of CAs and their public keys. It uses the corresponding key to decrypt the certification and finds the server publi ...
... includes the public key of the server. The public key is certified by some certification authority, which means that the public key is encrypted by a CA private key. Browser has a list of CAs and their public keys. It uses the corresponding key to decrypt the certification and finds the server publi ...
abidah
... IPv4 firewall has to open for protocol 41 (IPv6) and protocol 58 (ICMPv6) at the remote end of the tunnel. ...
... IPv4 firewall has to open for protocol 41 (IPv6) and protocol 58 (ICMPv6) at the remote end of the tunnel. ...
Title Size 30PT
... and anomaly-based inspection. Snort is the most widely deployed IDS/IPS technology worldwide. With millions of downloads and nearly 400,000 registered users, Snort has become the de facto standard for IPS. See more at http://www.snort.org. Never designed to be application aware Presentation_ID ...
... and anomaly-based inspection. Snort is the most widely deployed IDS/IPS technology worldwide. With millions of downloads and nearly 400,000 registered users, Snort has become the de facto standard for IPS. See more at http://www.snort.org. Never designed to be application aware Presentation_ID ...
J - The Brad Blog
... the phrase "clear error messages" being returned from Hart's products in general. - Compuware was unable to modify the MBB vote storage cards trying to use the Windows file system. The report suggests that this cannot be done, and it cannot, but this gives the impression that such information is hi ...
... the phrase "clear error messages" being returned from Hart's products in general. - Compuware was unable to modify the MBB vote storage cards trying to use the Windows file system. The report suggests that this cannot be done, and it cannot, but this gives the impression that such information is hi ...
QUESTION DRILL APPLICATIONS DEVELOPMENT 020504
... D: SQL is not vulnerable to dead locks since it supports concurrent transaction through transaction management. 88. When a database system supports transaction management, which of the following is it still vulnerable to, because users have access to data cells? A: Databases may be still vulnerable ...
... D: SQL is not vulnerable to dead locks since it supports concurrent transaction through transaction management. 88. When a database system supports transaction management, which of the following is it still vulnerable to, because users have access to data cells? A: Databases may be still vulnerable ...
Certified Penetration Testing Specialist
... their expertise by practicing what they teach because we believe that an equal emphasis on theoretical and real world experience is essential for effective knowledge transfer to you, the student. The CPTS presents information on the latest vulnerabilities and defenses. This class also enhances the b ...
... their expertise by practicing what they teach because we believe that an equal emphasis on theoretical and real world experience is essential for effective knowledge transfer to you, the student. The CPTS presents information on the latest vulnerabilities and defenses. This class also enhances the b ...
Introduction to Information Security Chapter N
... and targets any of several vulnerabilities known to hackers or left over from previous exploits Web Browsing - If the infected system has write access to any Web pages, it makes all Web content files infectious, so that users who browse to those pages become infected Virus - Each infected machin ...
... and targets any of several vulnerabilities known to hackers or left over from previous exploits Web Browsing - If the infected system has write access to any Web pages, it makes all Web content files infectious, so that users who browse to those pages become infected Virus - Each infected machin ...
Introduction to Healthcare Information Technology
... • Cryptography transforms information into a secure form so that unauthorized persons cannot access it • Symmetric cryptography uses a single key to encrypt and decrypt a message • Asymmetric cryptography uses two keys: a public and a private key • Cryptography can be applied through hardware or sof ...
... • Cryptography transforms information into a secure form so that unauthorized persons cannot access it • Symmetric cryptography uses a single key to encrypt and decrypt a message • Asymmetric cryptography uses two keys: a public and a private key • Cryptography can be applied through hardware or sof ...
The Top Seven Security Problems of 802.11 Wireless
... security audits, AirMagnet 1.5 also records alarms when it spots devices that are not using strong security measures, such as VPNs or 802.1x. Problem #2: "Rogue" Access Points Easy access to wireless LANs is coupled with easy deployment. When combined, these two characteristics can cause headaches f ...
... security audits, AirMagnet 1.5 also records alarms when it spots devices that are not using strong security measures, such as VPNs or 802.1x. Problem #2: "Rogue" Access Points Easy access to wireless LANs is coupled with easy deployment. When combined, these two characteristics can cause headaches f ...
Information Security Incident Management
... •An attack that will try to use any privileges and information available to both legitimate and non legitimate users to gain access to confidential information •An approach that will try to exploit every weaknesses of your systems both internal, external, application and physical •A formalized opera ...
... •An attack that will try to use any privileges and information available to both legitimate and non legitimate users to gain access to confidential information •An approach that will try to exploit every weaknesses of your systems both internal, external, application and physical •A formalized opera ...
here - Help Net Security
... changes that affect the degree of risk that management has previously accepted. Effort is required by all organisations to safeguard information resources and reduce risks to a prudent level. ...
... changes that affect the degree of risk that management has previously accepted. Effort is required by all organisations to safeguard information resources and reduce risks to a prudent level. ...
Network Security Policy in the Work Place
... • Outside of a physical network asset, there should be cameras monitoring to see who enters and attempts to access the location. • This will enable a company or organization to detect when someone enters a sensitive location, as well as evidence in the result of an attack. ...
... • Outside of a physical network asset, there should be cameras monitoring to see who enters and attempts to access the location. • This will enable a company or organization to detect when someone enters a sensitive location, as well as evidence in the result of an attack. ...
Security+ Guide to Network Security Fundamentals, Third
... protects the integrity, confidentiality, and availability of information on the devices that store, manipulate, and transmit the information through products, people, and procedures The main goals of information security are to prevent data theft, thwart identity theft, avoid the legal consequences ...
... protects the integrity, confidentiality, and availability of information on the devices that store, manipulate, and transmit the information through products, people, and procedures The main goals of information security are to prevent data theft, thwart identity theft, avoid the legal consequences ...
Top Ten Database Security Threats
... of database activity represents a serious organizational risk at many levels. Additionally, organizations with weak (or sometimes non-existent) database audit mechanisms also find that they are at odds with industry and government regulatory requirements. SarbanesOxley (SOX), which seeks to prevent ...
... of database activity represents a serious organizational risk at many levels. Additionally, organizations with weak (or sometimes non-existent) database audit mechanisms also find that they are at odds with industry and government regulatory requirements. SarbanesOxley (SOX), which seeks to prevent ...
SureView® Analytics Security Operations
... situation. The timely process of internal approvals for access to information from multiple divisions across the enterprise is bypassed, as SureView Analytics’ unobtrusive search capability does not ingest mass data into one central location. SureView Analytics does not copy the data source, but mer ...
... situation. The timely process of internal approvals for access to information from multiple divisions across the enterprise is bypassed, as SureView Analytics’ unobtrusive search capability does not ingest mass data into one central location. SureView Analytics does not copy the data source, but mer ...
Resource - Rogue Wave Software
... The best way to minimize the risks associated with the use of OSS is to create an OSS policy to govern your organization’s use of OSS, including OSS acquisition, provisioning, and tracking. Here again, tools are available, such as OpenLogic, which helps create and manage policy, maintains a database ...
... The best way to minimize the risks associated with the use of OSS is to create an OSS policy to govern your organization’s use of OSS, including OSS acquisition, provisioning, and tracking. Here again, tools are available, such as OpenLogic, which helps create and manage policy, maintains a database ...
Data Governance Policy
... 2. Unauthorized disclosure of a log-in code (User ID and password). 3. An attempt to obtain a log-in code or password that belongs to another person. 4. An attempt to use another person's log-in code or password. 5. Unauthorized use of an authorized password to invade student or employee privacy by ...
... 2. Unauthorized disclosure of a log-in code (User ID and password). 3. An attempt to obtain a log-in code or password that belongs to another person. 4. An attempt to use another person's log-in code or password. 5. Unauthorized use of an authorized password to invade student or employee privacy by ...