Types of Attacks - Digital Locker and Personal Web Space
... • A connection to a Windows inter-process communication share (IPC$) – Systems prior to XP and Server 2003 are vulnerable. – Used by a variety of exploit tools and malware. – No patch is available. • Options to counter the vulnerability – Upgrade systems to Windows XP or newer version – Only allow t ...
... • A connection to a Windows inter-process communication share (IPC$) – Systems prior to XP and Server 2003 are vulnerable. – Used by a variety of exploit tools and malware. – No patch is available. • Options to counter the vulnerability – Upgrade systems to Windows XP or newer version – Only allow t ...
Cobrador – Channeler brochure
... The conceptual question to be asked: Can we trust security checkpoints exclusively to preempt cyber attacks at the periphery layer of our networks? ...
... The conceptual question to be asked: Can we trust security checkpoints exclusively to preempt cyber attacks at the periphery layer of our networks? ...
- SlideBoom
... A. They compare the 5-tuple of each incoming packet against configurable rules. B. They cannot track connections. C. They are designed to work most efficiently with stateless protocols such as HTTP or HTTPS. D. Cisco IOS cannot implement them because the platform is stateful by nature. E. The Cisco ...
... A. They compare the 5-tuple of each incoming packet against configurable rules. B. They cannot track connections. C. They are designed to work most efficiently with stateless protocols such as HTTP or HTTPS. D. Cisco IOS cannot implement them because the platform is stateful by nature. E. The Cisco ...
Slide 1
... These programs disrupt the normal function of a computer system through harmless pranks or by destroying files on the infected computer. They come in several types: • Boot Sector – attaches to the section of a hard disk or floppy disk that boots a computer. • File Infector – attach themselves to cer ...
... These programs disrupt the normal function of a computer system through harmless pranks or by destroying files on the infected computer. They come in several types: • Boot Sector – attaches to the section of a hard disk or floppy disk that boots a computer. • File Infector – attach themselves to cer ...
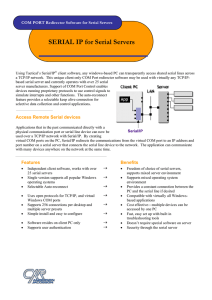
SERIAL-IP COM PORT Redirector Software for Serial Servers
... virtual COM ports on the PC, Serial/IP redirects the communications from the virtual COM port to an IP address and port number on a serial server that connects the serial line device to the network. The application can communicate with many devices anywhere on the network at the same time. ...
... virtual COM ports on the PC, Serial/IP redirects the communications from the virtual COM port to an IP address and port number on a serial server that connects the serial line device to the network. The application can communicate with many devices anywhere on the network at the same time. ...
Threats To Windows Users and Countermeasures
... the growing number of home PC threats. This threat affects users of other operating systems as well. The 'always on' and no 'connection setup' waiting features which are much preferred by users actually make this kind of connection more susceptible to attacks. Though, a user has closed the browser a ...
... the growing number of home PC threats. This threat affects users of other operating systems as well. The 'always on' and no 'connection setup' waiting features which are much preferred by users actually make this kind of connection more susceptible to attacks. Though, a user has closed the browser a ...
Web Services Security: Bells and Thistles
... Symmetric and asymmetric Key Encryption End-to-end encryption ...
... Symmetric and asymmetric Key Encryption End-to-end encryption ...
Security & Cryptography
... Network Address Translation (NAT) allows a network to use one set of addresses internally and a different set when dealing with external networks. It helps conceal internal network and force connections to go through choke point. Router does the extra work required for address translation. ...
... Network Address Translation (NAT) allows a network to use one set of addresses internally and a different set when dealing with external networks. It helps conceal internal network and force connections to go through choke point. Router does the extra work required for address translation. ...
Attacks and vulnerabilities
... Social Engineering (Vulnerability) Manipulate the weakest link of cybersecurity – the user – to gain access to otherwise prohibited resources Defense: Train personnel to resist the tactics of software engineering ...
... Social Engineering (Vulnerability) Manipulate the weakest link of cybersecurity – the user – to gain access to otherwise prohibited resources Defense: Train personnel to resist the tactics of software engineering ...
Cryptanalysis of Stream Cipher
... No security reduction but easy to analyze Not resistant to nonce reuse No incremental tags Flexible implementation sizes: 128/256 Performance: speed/size ...
... No security reduction but easy to analyze Not resistant to nonce reuse No incremental tags Flexible implementation sizes: 128/256 Performance: speed/size ...
Security+ Guide to Network Security Fundamentals, Third
... Determining vulnerabilities often depends upon the background and experience of the assessor ...
... Determining vulnerabilities often depends upon the background and experience of the assessor ...
protect a system from cyber attacks?
... access for remote diagnostics or maintenance. The suppliers frequently leave ports open on the equipment to simplify their tasks, giving the attacker access to the equipment and links to control system network. ...
... access for remote diagnostics or maintenance. The suppliers frequently leave ports open on the equipment to simplify their tasks, giving the attacker access to the equipment and links to control system network. ...
Apply encryption to network and system security
... Encryption is the process of taking some information or data, manipulating or changing its format in a way that stops it from being used or read by unauthorized people or systems. Encryption involves scrambling data so that it needs to be unscrambled, or decrypted, to be read. Encryption can be appl ...
... Encryption is the process of taking some information or data, manipulating or changing its format in a way that stops it from being used or read by unauthorized people or systems. Encryption involves scrambling data so that it needs to be unscrambled, or decrypted, to be read. Encryption can be appl ...
Authentication and Remote Access
... • Discuss the methods and protocols for remote access to networks. • Explain authentication methods and the security implications in their use. • Implement virtual private networks (VPNs) and their security aspects. • Describe Internet Protocol Security (IPsec) and its use in securing communications ...
... • Discuss the methods and protocols for remote access to networks. • Explain authentication methods and the security implications in their use. • Implement virtual private networks (VPNs) and their security aspects. • Describe Internet Protocol Security (IPsec) and its use in securing communications ...
Computer Crimes - Crime Prevention HQ
... lotteries, phishing, information/adult services, and Nigerian money offers. ● A growing number of foreign crooks are scamming U.S. consumers via the Internet. ● Wiring money has become the most common method of payment in Internet fraud. ...
... lotteries, phishing, information/adult services, and Nigerian money offers. ● A growing number of foreign crooks are scamming U.S. consumers via the Internet. ● Wiring money has become the most common method of payment in Internet fraud. ...
EE-EmbeddedOperatingSystems-II
... HTTP : Android has org.apache.http package that has the core interfaces and classes of the HTTP components. HTTPS & SSL: Android provides javax.net.ssl package that has all the classes and interfaces needed to implement and program the Secure Socket abstraction based on the SSL protocol SSSLv3.0 or ...
... HTTP : Android has org.apache.http package that has the core interfaces and classes of the HTTP components. HTTPS & SSL: Android provides javax.net.ssl package that has all the classes and interfaces needed to implement and program the Secure Socket abstraction based on the SSL protocol SSSLv3.0 or ...
An Immucor Technical Support Solution
... Yes, blud_direct utilizes the Secure Socket Layer (SSL) protocol, commonly used for secure transactions over the web. Additionally, the application uses 256-bit AES encryption to further secure the communication. Is there software loaded on our instrument computer? No. There is no software to load o ...
... Yes, blud_direct utilizes the Secure Socket Layer (SSL) protocol, commonly used for secure transactions over the web. Additionally, the application uses 256-bit AES encryption to further secure the communication. Is there software loaded on our instrument computer? No. There is no software to load o ...
Slide 1
... Mobile workforce extending the edge of corporate network to a user’s laptop: • User laptop at airport/ hotel can be compromised and serve as a bridge to corporate backbone ...
... Mobile workforce extending the edge of corporate network to a user’s laptop: • User laptop at airport/ hotel can be compromised and serve as a bridge to corporate backbone ...
Hands-On Ethical Hacking and Network Security
... Most companies have Wireless LANs (WLANs) that connect to their wired network ...
... Most companies have Wireless LANs (WLANs) that connect to their wired network ...
Effective Database Security Database Top 10 Threats
... • Definition: Attacks that affect the availability of information from the database to users – A general type of attack, many technique exists: • Specific vulnerabilities: SQL injection, platform vulnerabilities, database vulnerabilities • Resource oriented attacks: Exhaustion of specific resources ...
... • Definition: Attacks that affect the availability of information from the database to users – A general type of attack, many technique exists: • Specific vulnerabilities: SQL injection, platform vulnerabilities, database vulnerabilities • Resource oriented attacks: Exhaustion of specific resources ...
PCI Self-Assessment Questionnaire
... All personally identifiable data about the cardholder and relationship to the Member (i.e., account number, expiration date, data provided by the Member, other electronic data gathered by the merchant/agent, and so on). This term also accounts for other personal insights gathered about the cardholde ...
... All personally identifiable data about the cardholder and relationship to the Member (i.e., account number, expiration date, data provided by the Member, other electronic data gathered by the merchant/agent, and so on). This term also accounts for other personal insights gathered about the cardholde ...
Database Security
... Unauthorized disclosure Unauthorized modification Denial of service attacks ...
... Unauthorized disclosure Unauthorized modification Denial of service attacks ...
Raz-Lee Solution Brief
... security policy for enterprise environments. Organizations gain visibility into all database activity, including local privileged access and sophisticated attacks from within the database. McAfee Database Activity Monitoring helps protect valuable, sensitive data from external threats and malicious ...
... security policy for enterprise environments. Organizations gain visibility into all database activity, including local privileged access and sophisticated attacks from within the database. McAfee Database Activity Monitoring helps protect valuable, sensitive data from external threats and malicious ...