Computer Information Systems (Forensics Classes) Objectives for
... components, and the major types of DOS attacks and how to protect against them. • Discuss the process of auditing logs and how the audit process should be implemented. • Describe how to conduct a security audit and how to conduct a post-mortem analysis of an attack. The student will be able to demon ...
... components, and the major types of DOS attacks and how to protect against them. • Discuss the process of auditing logs and how the audit process should be implemented. • Describe how to conduct a security audit and how to conduct a post-mortem analysis of an attack. The student will be able to demon ...
Viruses - University of Windsor
... from a Unix system. Several Linux viruses have been discovered. The Staog virus first appeared in 1996 and was written in assembly language by the VLAD virus writing group, the same group responsible for creating the first Windows 95 virus called Boza. Like the Boza virus, the Staog virus is a proof ...
... from a Unix system. Several Linux viruses have been discovered. The Staog virus first appeared in 1996 and was written in assembly language by the VLAD virus writing group, the same group responsible for creating the first Windows 95 virus called Boza. Like the Boza virus, the Staog virus is a proof ...
View
... encryption DES, IDEA, algorithms, CBC, location of encryption devices key distribution. Unit-2 Message digest & checksums, Message authentication, message digests, Hash functions & SHA,CRCs.Public key systems:RSA,ddiffie –Helman,DSS ,key management.Intruders,intrusion techniques , inclusion detectio ...
... encryption DES, IDEA, algorithms, CBC, location of encryption devices key distribution. Unit-2 Message digest & checksums, Message authentication, message digests, Hash functions & SHA,CRCs.Public key systems:RSA,ddiffie –Helman,DSS ,key management.Intruders,intrusion techniques , inclusion detectio ...
Hands-On Ethical Hacking and Network Defense Second Edition
... – Prevents legitimate users from accessing network resources – Some forms do not involve computers ...
... – Prevents legitimate users from accessing network resources – Some forms do not involve computers ...
Computer Forensics
... information. Individuals are not going to go to great lengths to protect end systems with information that is already public knowledge; however on the other hand, information that is highly secretive and essential to productivity and functionality will be protected very well. The owner of those asse ...
... information. Individuals are not going to go to great lengths to protect end systems with information that is already public knowledge; however on the other hand, information that is highly secretive and essential to productivity and functionality will be protected very well. The owner of those asse ...
Mitigating DDoS Attacks
... Some DDoS attacks aims to completely deplete the resource of the victim, while others aims to degrade the quality of the victim’s service. ...
... Some DDoS attacks aims to completely deplete the resource of the victim, while others aims to degrade the quality of the victim’s service. ...
Chapter 8
... entity was not their final IP destination, as a result of which an attempt was made to find a route to forward them to that final destination. In entities which do not act as IP Gateways, this ...
... entity was not their final IP destination, as a result of which an attempt was made to find a route to forward them to that final destination. In entities which do not act as IP Gateways, this ...
Network Security: Intrusion Detection and Protection
... Attacks On the Normalizer: Stateholding attacks: The attacker tries to consume the normalizer’s memory by causing it to instantiate too many states. Common stateholding attacks are: SYN flooding: The attacker floods SYN packets so that the normalizer instantiates states for each connection. ACK flo ...
... Attacks On the Normalizer: Stateholding attacks: The attacker tries to consume the normalizer’s memory by causing it to instantiate too many states. Common stateholding attacks are: SYN flooding: The attacker floods SYN packets so that the normalizer instantiates states for each connection. ACK flo ...
Chapter 8
... entity was not their final IP destination, as a result of which an attempt was made to find a route to forward them to that final destination. In entities which do not act as IP Gateways, this ...
... entity was not their final IP destination, as a result of which an attempt was made to find a route to forward them to that final destination. In entities which do not act as IP Gateways, this ...
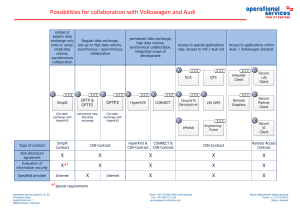
Possibilities for collaboration with Volkswagen
... With HyperKVS you have the possibility to save data directly to the platform, to link them to a design version and to make them available for the design engineer. Released data can be downloaded directly from HyperKVS. With HyperKVS you can view drawings on your screen. The drawing will be converted ...
... With HyperKVS you have the possibility to save data directly to the platform, to link them to a design version and to make them available for the design engineer. Released data can be downloaded directly from HyperKVS. With HyperKVS you can view drawings on your screen. The drawing will be converted ...
Lecture 5 - The University of Texas at Dallas
... “There are two types of RIM devices within each model class. The Exchange Edition is meant for use in a corporate environment while the Internet Edition works with standard POP email accounts. The Exchange Edition employs Triple-DES encryption to send and receive but the Internet Edition communicate ...
... “There are two types of RIM devices within each model class. The Exchange Edition is meant for use in a corporate environment while the Internet Edition works with standard POP email accounts. The Exchange Edition employs Triple-DES encryption to send and receive but the Internet Edition communicate ...
Red Hat enteRpRise Linux 6 seRveR: FeatuRes
... The new System Security Services Daemon (SSSD) provides centralized access to identity and authentication resources, and enables caching and offline support. SSSD presents a generalized interface to clients that need identity and authentication, and should be the service of choice for access to iden ...
... The new System Security Services Daemon (SSSD) provides centralized access to identity and authentication resources, and enables caching and offline support. SSSD presents a generalized interface to clients that need identity and authentication, and should be the service of choice for access to iden ...
6 - University of South Florida St. Petersburg
... to restrict content access from within network Essentially a set of scripts or programs restricting user access to certain networking protocols/Internet locations Primary focus to restrict internal access to external material Most common content filters restrict users from accessing non-busine ...
... to restrict content access from within network Essentially a set of scripts or programs restricting user access to certain networking protocols/Internet locations Primary focus to restrict internal access to external material Most common content filters restrict users from accessing non-busine ...
Huntsman Security updates trail-blazing cyber security analytics and
... Massive growth in interest around security analytics, threat management and automation has driven rapid evolution of Huntsman Security cyber risk solutions with new version released today. Sydney, May 31 2016. Huntsman Security (http://www.huntsmansecurity.com) today announced the latest release of ...
... Massive growth in interest around security analytics, threat management and automation has driven rapid evolution of Huntsman Security cyber risk solutions with new version released today. Sydney, May 31 2016. Huntsman Security (http://www.huntsmansecurity.com) today announced the latest release of ...
Hotspot Shield Baixaki
... Hotspot Shield Baixaki - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while b ...
... Hotspot Shield Baixaki - A virtual private network (VPN) extends a private network across a public network, such as the Internet. It enables a computer or network-enabled device to send and receive data across shared or public networks as if it were directly connected to the private network, while b ...
What Cyber Criminals Know Most People Don`t?
... remote management or monitoring of IT security functions delivered via remote security operations centers (SOCs), not through personnel onsite." The rise in frequency and complexity of attacks and the need for increasingly sophisticated security solutions have led to a new echelon of MSS that IDC is ...
... remote management or monitoring of IT security functions delivered via remote security operations centers (SOCs), not through personnel onsite." The rise in frequency and complexity of attacks and the need for increasingly sophisticated security solutions have led to a new echelon of MSS that IDC is ...
Study Material for MCA (SEM-V) Subject: Cyber Security and
... Where financial losses to the organization due to insider crimes are concerned often some difficulty is faced in estimating the losses because the financial impacts may not be detected by the victimized organization and no direct costs may be associated with the data theft. ...
... Where financial losses to the organization due to insider crimes are concerned often some difficulty is faced in estimating the losses because the financial impacts may not be detected by the victimized organization and no direct costs may be associated with the data theft. ...
information Security Blueprint
... Assessment Process”; “Agreed Upon Procedures” • Using the two documents, security team can develop sound strategy the design of good security architecture ...
... Assessment Process”; “Agreed Upon Procedures” • Using the two documents, security team can develop sound strategy the design of good security architecture ...
Slide 1
... States that a user should have only the privileges needed to do his job. Least privilege is enforced using a network device, such as a router with an access control list (ACL) which tells a computer operating system which access rights each user has to a particular object. ...
... States that a user should have only the privileges needed to do his job. Least privilege is enforced using a network device, such as a router with an access control list (ACL) which tells a computer operating system which access rights each user has to a particular object. ...
Computer Security, Ethics, and Privacy
... Discuss techniques to prevent unauthorized computer access and use Identify safeguards against hardware theft and vandalism Explain the ways software manufacturers protect against software piracy Define encryption and explain why it is ...
... Discuss techniques to prevent unauthorized computer access and use Identify safeguards against hardware theft and vandalism Explain the ways software manufacturers protect against software piracy Define encryption and explain why it is ...
Cafe Cracks: Attacks on Unsecured Wireless Networks
... This address can be for a DNS server from the ISP or another third-party. However, for attack purposed, the attack machine runs its own DNS server and supplies its address to clients using DHCP. This allows the attacker to redirect users to phishing sites using DNS. It is possible that users will ha ...
... This address can be for a DNS server from the ISP or another third-party. However, for attack purposed, the attack machine runs its own DNS server and supplies its address to clients using DHCP. This allows the attacker to redirect users to phishing sites using DNS. It is possible that users will ha ...
CIST 1601 Information Security Fundamentals
... It allows applications to access services or protocols to exchange data. Most programs, such as web browsers, interface with TCP/IP at this level. The most commonly used Application layer protocols are as follows: Hypertext Transfer Protocol is the protocol that is used by a web browser to communic ...
... It allows applications to access services or protocols to exchange data. Most programs, such as web browsers, interface with TCP/IP at this level. The most commonly used Application layer protocols are as follows: Hypertext Transfer Protocol is the protocol that is used by a web browser to communic ...
File
... Setup a weekly full system scan(important) If a virus has been detected, deal with it immediately. Update the software, then perform another full system scan. ...
... Setup a weekly full system scan(important) If a virus has been detected, deal with it immediately. Update the software, then perform another full system scan. ...
2012 Bond Planning Technology Project Update
... student use, additional software tools, and improved data analysis capabilities Significant investment in Computer & Devices Additional investment in educational technology innovation ...
... student use, additional software tools, and improved data analysis capabilities Significant investment in Computer & Devices Additional investment in educational technology innovation ...