Database Administration (DBA)
... Archives • An archive is a place where corporate data is kept. • Information in an archive is removed from the database and stored in the archive for future reference. • Archives are usually kept in a mass-storage device like a disk, tape, CD, or a DVD. • It is important such archives be kept off-s ...
... Archives • An archive is a place where corporate data is kept. • Information in an archive is removed from the database and stored in the archive for future reference. • Archives are usually kept in a mass-storage device like a disk, tape, CD, or a DVD. • It is important such archives be kept off-s ...
Evaluation and Assurance - NYU Polytechnic School of
... • Instead, systems are sometimes built from enclaves of workstations and network elements Within the enclave everything is at one level Commercial Off The Shelf (COTS) products (workstations, network elements) can be used C2 (Orange book) or lower EAL (common criteria) is OK Enclaves can be ...
... • Instead, systems are sometimes built from enclaves of workstations and network elements Within the enclave everything is at one level Commercial Off The Shelf (COTS) products (workstations, network elements) can be used C2 (Orange book) or lower EAL (common criteria) is OK Enclaves can be ...
the catalogue here
... to help you efficiently mitigate the risks of attacks and data breaches across the spectrum of end-user platforms, from smartphones to tablets, and laptops to removable drives. Trend Micro Enterprise Data Protection simplifies data security in today’s complex mobile environments by integrating data ...
... to help you efficiently mitigate the risks of attacks and data breaches across the spectrum of end-user platforms, from smartphones to tablets, and laptops to removable drives. Trend Micro Enterprise Data Protection simplifies data security in today’s complex mobile environments by integrating data ...
AISE PoIS4E_PP_ch02_57
... • For instance, a small business may start by using an e-mail service provided by an ISP and augmented with a personal encryption tool. When an organization grows , it must develop additional security services. For example, – organizational growth could lead to the need for: ...
... • For instance, a small business may start by using an e-mail service provided by an ISP and augmented with a personal encryption tool. When an organization grows , it must develop additional security services. For example, – organizational growth could lead to the need for: ...
CompTIA Security (SY0-401)
... Risks associated with Cloud Computing and Virtualization Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
... Risks associated with Cloud Computing and Virtualization Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
slides - cse.sc.edu
... 1. Dormant phase: the virus is idle. (not all viruses have this stage) 2. Propagation phase: the virus places an identical copy of itself into other programs of into certain system areas. 3. Triggering phase: the virus is activated to perform the function for which it was created. 4. Execution phase ...
... 1. Dormant phase: the virus is idle. (not all viruses have this stage) 2. Propagation phase: the virus places an identical copy of itself into other programs of into certain system areas. 3. Triggering phase: the virus is activated to perform the function for which it was created. 4. Execution phase ...
A Study on The Information Gathering Method for
... administrative purposes. In addition, it can reveal old versions of files or artifacts such as undeleted, obsolete scripts, crafted during the test/development phase or as the result of maintenance. 6. Analysis of Error Codes: During a penetration test, web applications may divulge information that ...
... administrative purposes. In addition, it can reveal old versions of files or artifacts such as undeleted, obsolete scripts, crafted during the test/development phase or as the result of maintenance. 6. Analysis of Error Codes: During a penetration test, web applications may divulge information that ...
Ingen bildrubrik
... Integrated FT/10 LonWorks® field bus Integrated X10 interface Integrated GSM/GPRS module for SMS messaging and host communication Integrated backup power - up to 60 hours ...
... Integrated FT/10 LonWorks® field bus Integrated X10 interface Integrated GSM/GPRS module for SMS messaging and host communication Integrated backup power - up to 60 hours ...
Firewalls
... Identify the various approaches to remote and dial-up access protection—that is, how these connection methods can be controlled to assure confidentiality of information, and the authentication and authorization of users Explain content filtering technology Describe the technology that enables ...
... Identify the various approaches to remote and dial-up access protection—that is, how these connection methods can be controlled to assure confidentiality of information, and the authentication and authorization of users Explain content filtering technology Describe the technology that enables ...
Security policy design with IPSec
... Network security design can be compared to the design of software, and many of the principles that have been developed and used over the years can be used (Porto and De Geus 2003:1). It is unfortunate that many software products are developed using what might be termed a ‘build and fix’ model. This ...
... Network security design can be compared to the design of software, and many of the principles that have been developed and used over the years can be used (Porto and De Geus 2003:1). It is unfortunate that many software products are developed using what might be termed a ‘build and fix’ model. This ...
Firewall and VPNs - Ohio State Computer Science and Engineering
... Best Practices for Firewalls All traffic from trusted network is allowed out Firewall device never directly accessed from public network Simple Mail Transport Protocol (SMTP) data allowed to pass through firewall Internet Control Message Protocol (ICMP) data denied Telnet access to intern ...
... Best Practices for Firewalls All traffic from trusted network is allowed out Firewall device never directly accessed from public network Simple Mail Transport Protocol (SMTP) data allowed to pass through firewall Internet Control Message Protocol (ICMP) data denied Telnet access to intern ...
6 - Computer Science and Engineering
... Best Practices for Firewalls All traffic from trusted network is allowed out Firewall device never directly accessed from public network Simple Mail Transport Protocol (SMTP) data allowed to pass through firewall Internet Control Message Protocol (ICMP) data denied Telnet access to intern ...
... Best Practices for Firewalls All traffic from trusted network is allowed out Firewall device never directly accessed from public network Simple Mail Transport Protocol (SMTP) data allowed to pass through firewall Internet Control Message Protocol (ICMP) data denied Telnet access to intern ...
ppt
... may use client IP affinity to insure that requests from the same client are repeatedly satisfied by the same server during this session. The trade off is that the load may be unevenly distributed. This organization is still robust to failure though. 10. What is the difference between network and app ...
... may use client IP affinity to insure that requests from the same client are repeatedly satisfied by the same server during this session. The trade off is that the load may be unevenly distributed. This organization is still robust to failure though. 10. What is the difference between network and app ...
Lecture 1 - Tarek Sobh
... uniform logical view of information storage. It maps files onto physical media, and accesses these files via the storage devices. ...
... uniform logical view of information storage. It maps files onto physical media, and accesses these files via the storage devices. ...
Windows Rootkit Overview
... User mode rootkits involve system hooking in the user or application space. Whenever an application makes a system call, the execution of that system call follows a predetermined path and a Windows rootkit can hijack the system call at many points along that path. One of the most common user mode te ...
... User mode rootkits involve system hooking in the user or application space. Whenever an application makes a system call, the execution of that system call follows a predetermined path and a Windows rootkit can hijack the system call at many points along that path. One of the most common user mode te ...
Manage security settings with Action Center
... designed to damage a computer system without the owner’s knowledge or agreement. Malware is short for malicious software and includes computer viruses, spyware, worms, and Trojan horses, or any other unwanted or malicious software. Spyware برامج التجسسis a type of malware that can be installed on ...
... designed to damage a computer system without the owner’s knowledge or agreement. Malware is short for malicious software and includes computer viruses, spyware, worms, and Trojan horses, or any other unwanted or malicious software. Spyware برامج التجسسis a type of malware that can be installed on ...
Click for PDF - Cyber Security Services
... Disable local administrator accounts to prevent network propagation using compromised local administrator credentials that are shared by several workstations. ...
... Disable local administrator accounts to prevent network propagation using compromised local administrator credentials that are shared by several workstations. ...
Commiting a Rule Tree
... •Unix possesses much greater processing power than Windows. • Unix is the leader in serving the Web. About 90% of the Internet relies on Unix operating systems running on Apache, the world's most widely used Web server. • Software upgrades from Microsoft often require the user to purchase new or mor ...
... •Unix possesses much greater processing power than Windows. • Unix is the leader in serving the Web. About 90% of the Internet relies on Unix operating systems running on Apache, the world's most widely used Web server. • Software upgrades from Microsoft often require the user to purchase new or mor ...
6 - Kuroski
... Best Practices for Firewalls All traffic from trusted network is allowed out Firewall device never directly accessed from public network Simple Mail Transport Protocol (SMTP) data allowed to pass through firewall Internet Control Message Protocol (ICMP) data denied Telnet access to intern ...
... Best Practices for Firewalls All traffic from trusted network is allowed out Firewall device never directly accessed from public network Simple Mail Transport Protocol (SMTP) data allowed to pass through firewall Internet Control Message Protocol (ICMP) data denied Telnet access to intern ...
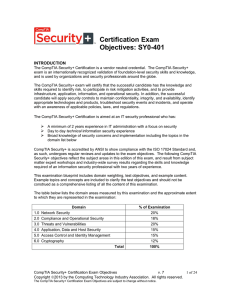
Certification Exam Objectives: SY0-401
... • Risks associated with Cloud Computing and Virtualization • Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
... • Risks associated with Cloud Computing and Virtualization • Recovery time objective and recovery point objective 2.2 Summarize the security implications of integrating systems and data with third ...
File
... In default discard policy initially, everything is blocked, and services must be added on a caseby-case basis. The default forward policy increases ease of use for end users but provides reduced security. One advantage of a packet-filtering router is its simplicity and transparent to users and a ...
... In default discard policy initially, everything is blocked, and services must be added on a caseby-case basis. The default forward policy increases ease of use for end users but provides reduced security. One advantage of a packet-filtering router is its simplicity and transparent to users and a ...
Security+ Guide to Network Security Fundamentals, Third Edition
... A low-level system program that uses a __________________ designed to monitor and ______________________ on a desktop system, server, or even a PDA or cell phone ...
... A low-level system program that uses a __________________ designed to monitor and ______________________ on a desktop system, server, or even a PDA or cell phone ...