Survey of online attacks on E-Commerce sites
... 2.2 Vulnerabilities due to input validations: Buffer Overflow : A buffer overflow condition occurs when a program attempts to copy more data in a buffer than it can hold. Buffer overflow is probably the best known form of software security vulnerability. At the code level, buffer overflow vulnerabil ...
... 2.2 Vulnerabilities due to input validations: Buffer Overflow : A buffer overflow condition occurs when a program attempts to copy more data in a buffer than it can hold. Buffer overflow is probably the best known form of software security vulnerability. At the code level, buffer overflow vulnerabil ...
Computer Security, Ethics, and Privacy
... itself repeatedly, using up resources and possibly shutting down computer or network ...
... itself repeatedly, using up resources and possibly shutting down computer or network ...
A Preparing And Networking Of Virtual Network - Eagle
... (Hoagland, Conover, & Whitehouse, 2012). The registry list was quite extensive since the machine was connected in a workgroup and many of the connection configurations were done with other machines. By combining the use of above mentioned software, it was made pretty clear as to what kind of loophol ...
... (Hoagland, Conover, & Whitehouse, 2012). The registry list was quite extensive since the machine was connected in a workgroup and many of the connection configurations were done with other machines. By combining the use of above mentioned software, it was made pretty clear as to what kind of loophol ...
Computer Security: Principles and Practice, 1/e
... Hackers with minimal technical skill who primarily use existing attack toolkits • They likely comprise the largest number of attackers, including many criminal and activist attackers • Given their use of existing known tools, these attackers are the easiest to defend against • Also known as “script- ...
... Hackers with minimal technical skill who primarily use existing attack toolkits • They likely comprise the largest number of attackers, including many criminal and activist attackers • Given their use of existing known tools, these attackers are the easiest to defend against • Also known as “script- ...
WHAT IS EC SECURITY? - Joseph H. Schuessler, PhD
... “intruders”) from accessing any part of the EC system detection measures Ways to determine whether intruders attempted to break into the EC system; whether they were successful; and what they may have done information assurance (IA) The protection of information systems against unauthorized acce ...
... “intruders”) from accessing any part of the EC system detection measures Ways to determine whether intruders attempted to break into the EC system; whether they were successful; and what they may have done information assurance (IA) The protection of information systems against unauthorized acce ...
Resume - OPResume.com
... Maryland State Department of Education, Baltimore, Maryland Provided troubleshooting via telephone and in-person to 1550 internal and external customers, including the installation and configuration of software, password resets and first-line diagnosis/troubleshooting for computer hardware and softw ...
... Maryland State Department of Education, Baltimore, Maryland Provided troubleshooting via telephone and in-person to 1550 internal and external customers, including the installation and configuration of software, password resets and first-line diagnosis/troubleshooting for computer hardware and softw ...
Systeemanalyse in Ontwerpprojecten
... specialist IT-knowledge to be used legally with best intentions (e.g., information security experts) • Black hats or crackers: hackers with illegal intentions (e.g., distribution of copyrighted software, trying to shut down systems with distributed-denial-of-service (ddos) attacks) ...
... specialist IT-knowledge to be used legally with best intentions (e.g., information security experts) • Black hats or crackers: hackers with illegal intentions (e.g., distribution of copyrighted software, trying to shut down systems with distributed-denial-of-service (ddos) attacks) ...
Alexandra Roman - UIW3D Community Forums
... Client- a piece of computer hardware or software that accesses a service made available by a server Clip art- a collection of pictures or images that can be imported into a document or another program Clipboard- a reserved section of memory that is used as a temporary, behind-the- scenes staging are ...
... Client- a piece of computer hardware or software that accesses a service made available by a server Clip art- a collection of pictures or images that can be imported into a document or another program Clipboard- a reserved section of memory that is used as a temporary, behind-the- scenes staging are ...
Jorge Gomez Intro to Animation September 3, 2015 Input device
... Drive- (of a device) power or operate (another device). CentralProcessing Unit- is the electronic circuitry within a computer that carries out the instructions of a computer program by performing the basic arithmetic, logical, control and input/output (I/O) operations specified by the instructions. ...
... Drive- (of a device) power or operate (another device). CentralProcessing Unit- is the electronic circuitry within a computer that carries out the instructions of a computer program by performing the basic arithmetic, logical, control and input/output (I/O) operations specified by the instructions. ...
The Limits of Localization Using Signal Strength: A
... Localizing sensor nodes is the building block for high-level applications: Tracking, monitoring, and geometric-based routing Location-based services become more prevalent ...
... Localizing sensor nodes is the building block for high-level applications: Tracking, monitoring, and geometric-based routing Location-based services become more prevalent ...
Figure 6-1
... Confidentiality focuses on protecting against unauthorized disclosure of information to third parties. Integrity can be understood as preventing unauthorized modification of files. Availability means preventing unauthorized withholding of information from those who need it when they need it. ...
... Confidentiality focuses on protecting against unauthorized disclosure of information to third parties. Integrity can be understood as preventing unauthorized modification of files. Availability means preventing unauthorized withholding of information from those who need it when they need it. ...
Lab 5 - faraday - Eastern Mediterranean University
... one of the computers to view the shared folders. Now both computer show up on the other computers, unless firewall is preventing them from showing up. If you do not see your computers, then either configure your firewall to allow file sharing between them or temporarily shut the firewall down. Exerc ...
... one of the computers to view the shared folders. Now both computer show up on the other computers, unless firewall is preventing them from showing up. If you do not see your computers, then either configure your firewall to allow file sharing between them or temporarily shut the firewall down. Exerc ...
Securing Your Wireless Network - Homes and Lifestyles of Colorado
... wireless-ready computer can use your network. That means your neighbors, or even hackers lurking nearby, could "piggyback" on your network, or even access the information on your computer. And if an unauthorized person uses your network to commit a crime or send spam, the activity can be traced back ...
... wireless-ready computer can use your network. That means your neighbors, or even hackers lurking nearby, could "piggyback" on your network, or even access the information on your computer. And if an unauthorized person uses your network to commit a crime or send spam, the activity can be traced back ...
PA Blueprint- Computer Systems Networking PA 8148
... C. 4.7 GB D. 9.4 GB The ipconfig/all command is used to view a PCs A. MAC addressing information B. IP addressing information C. network connectivity D. Internet connection status A unique ''network number'' used in routing is contained in the A. MAC address B. physical address C. logical address D. ...
... C. 4.7 GB D. 9.4 GB The ipconfig/all command is used to view a PCs A. MAC addressing information B. IP addressing information C. network connectivity D. Internet connection status A unique ''network number'' used in routing is contained in the A. MAC address B. physical address C. logical address D. ...
Input device-computer hardware equipment used to provide data
... thread-a group of linked messages posted on an Internet forum that share a common subject or theme. Trojan horse-a program designed to breach the security of a computer system while ostensibly performing some innocuous function. ...
... thread-a group of linked messages posted on an Internet forum that share a common subject or theme. Trojan horse-a program designed to breach the security of a computer system while ostensibly performing some innocuous function. ...
security threats: a guide for small and medium
... Employees and end users within an organization may unknowingly introduce malware on the network when they run malicious executable code (EXE files). Sometimes they might receive an email with an attached worm or download spyware when visiting a malicious website. Alternatively, to get work done, emp ...
... Employees and end users within an organization may unknowingly introduce malware on the network when they run malicious executable code (EXE files). Sometimes they might receive an email with an attached worm or download spyware when visiting a malicious website. Alternatively, to get work done, emp ...
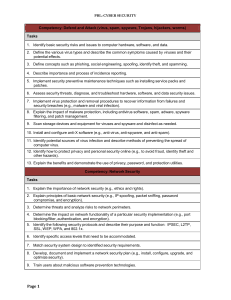
Competency: Defend and Attack (virus, spam, spyware - FBLA-PBL
... Computer Network Software Operations, Computer Applications, Information Technology Fundamentals, and Computer Information Systems Competency-Based Tasks/Competency Lists. 2009-2010. Virginia Department of Education. Richmond, VA. Computer Business Applications and Network Administration. 2001. Care ...
... Computer Network Software Operations, Computer Applications, Information Technology Fundamentals, and Computer Information Systems Competency-Based Tasks/Competency Lists. 2009-2010. Virginia Department of Education. Richmond, VA. Computer Business Applications and Network Administration. 2001. Care ...
Slide - Courses
... The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsof ...
... The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsof ...
Operating System Security Chapter 9 Operating System Security
... • Software bugs are a common security threat – Caused by sloppy programming – Provide opportunities to attackers by leaving system in an unexpected state, sometimes with high privilege levels – Best defense is to have well trained programmers and follow establish software development methods ...
... • Software bugs are a common security threat – Caused by sloppy programming – Provide opportunities to attackers by leaving system in an unexpected state, sometimes with high privilege levels – Best defense is to have well trained programmers and follow establish software development methods ...