Master - Anvari.Net
... • IDS does not need to know about security vulnerabilities in a particular system • the base-line defines normality; • don’t need to know the details of the construction of a buffer overflow packet. ...
... • IDS does not need to know about security vulnerabilities in a particular system • the base-line defines normality; • don’t need to know the details of the construction of a buffer overflow packet. ...
PPT_ch02
... Malware for Profit (continued) • Image spam cannot be easily filtered based on the content of the message • To detect image spam, one approach is to examine the context of the message and create a profile, asking questions such as: – Who sent the message? – What is known about the sender? – Where d ...
... Malware for Profit (continued) • Image spam cannot be easily filtered based on the content of the message • To detect image spam, one approach is to examine the context of the message and create a profile, asking questions such as: – Who sent the message? – What is known about the sender? – Where d ...
Security+ Guide to Network Security Fundamentals, Third Edition
... Malware for Profit (continued) • Image spam cannot be easily filtered based on the content of the message • To detect image spam, one approach is to examine the context of the message and create a profile, asking questions such as: – Who sent the message? – What is known about the sender? – Where d ...
... Malware for Profit (continued) • Image spam cannot be easily filtered based on the content of the message • To detect image spam, one approach is to examine the context of the message and create a profile, asking questions such as: – Who sent the message? – What is known about the sender? – Where d ...
Fundamentals of Computer Networking
... • Does provide a reliable connection between computers • will retransmit as necessary • Uses source and destination ports for addressing • Requires IP addressing to locate remote computer AE6382 ...
... • Does provide a reliable connection between computers • will retransmit as necessary • Uses source and destination ports for addressing • Requires IP addressing to locate remote computer AE6382 ...
slides
... a computer, regardless of age, income, or any other information for that matter The posterior probability P(H|X) is based on more information than the prior probability P(H) which is independent from X ...
... a computer, regardless of age, income, or any other information for that matter The posterior probability P(H|X) is based on more information than the prior probability P(H) which is independent from X ...
TCP/IP Networks - Northern Kentucky University
... – Looks like any other link layer device. – Full network processing is performed. – Sends packets to localhost for testing. ...
... – Looks like any other link layer device. – Full network processing is performed. – Sends packets to localhost for testing. ...
powerpoint lecture
... Learn how WANs use switched networks to communicate – Learn how devices can share a communication medium – Learn about DSL, cable modems, and satellite communications Connecting with Computer Science, 2e ...
... Learn how WANs use switched networks to communicate – Learn how devices can share a communication medium – Learn about DSL, cable modems, and satellite communications Connecting with Computer Science, 2e ...
Chapter 7: Computer Networks, the Internet, and the World Wide Web
... Computers connected together ...
... Computers connected together ...
Data Encryption Standard - gozips.uakron.edu
... Boot sector virus – code that compromises the segment in the hard disk containing the program used to start the computer Back door – an intentional design element of some software that allows developers of a system to gain access to the application for maintenance or technical problems Rootkit ...
... Boot sector virus – code that compromises the segment in the hard disk containing the program used to start the computer Back door – an intentional design element of some software that allows developers of a system to gain access to the application for maintenance or technical problems Rootkit ...
NetworkConcepts
... sending and receiving data. Devices on the network must be able to “talk the same language ” or use the same protocol. Two common protocols used today are: • NetBEUI : It is a protocol that broadcasts messages to every computer on the network. • TCP/IP : It is the protocol of the Internet and is req ...
... sending and receiving data. Devices on the network must be able to “talk the same language ” or use the same protocol. Two common protocols used today are: • NetBEUI : It is a protocol that broadcasts messages to every computer on the network. • TCP/IP : It is the protocol of the Internet and is req ...
Operating System Security Rules
... Since system administrators are called upon to help users with a variety of problems, they must be able to get at user files. This makes it important that system administrators be chosen carefully for their trustworthiness. Often system administrators are chosen strictly for their academic and exper ...
... Since system administrators are called upon to help users with a variety of problems, they must be able to get at user files. This makes it important that system administrators be chosen carefully for their trustworthiness. Often system administrators are chosen strictly for their academic and exper ...
Internet Hacking
... TCP/IP sequence stealing is the capturing of sequence numbers, which can be used to make an attacker's packets appear legitimate. A successful TCP/IP attack could allow an attacker to intercept transactions between two organizations, providing an opportunity for a man-in-the-middle attack. In som ...
... TCP/IP sequence stealing is the capturing of sequence numbers, which can be used to make an attacker's packets appear legitimate. A successful TCP/IP attack could allow an attacker to intercept transactions between two organizations, providing an opportunity for a man-in-the-middle attack. In som ...
Hands-On Ethical Hacking and Network Defense Second Edition
... • Do not attempt to access information – Cripples the network – Makes it vulnerable to other attacks ...
... • Do not attempt to access information – Cripples the network – Makes it vulnerable to other attacks ...
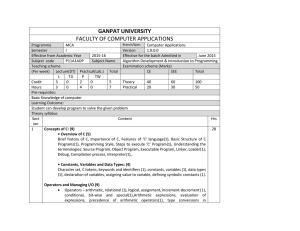
MCA_SEM_I_Syllabus_Details
... Introduction to Array, Concept of Dimensions in arrays, (1) Initialization values in an array, Overflow and Underflow, (2) Concepts in Multidimensional Array. (1) • Functions: (7) Need for user-defined functions, the form of c function, return values and their types, (1)calling a function, category ...
... Introduction to Array, Concept of Dimensions in arrays, (1) Initialization values in an array, Overflow and Underflow, (2) Concepts in Multidimensional Array. (1) • Functions: (7) Need for user-defined functions, the form of c function, return values and their types, (1)calling a function, category ...
2.1.1.a: Define a computer system
... 2.1.6.g: Explain the need for security measures in networks, such as user access levels, suitable passwords and encryption techniques. ...
... 2.1.6.g: Explain the need for security measures in networks, such as user access levels, suitable passwords and encryption techniques. ...
COMPUTER CRIME Computer crime
... – software that identifies encrypted files and may decrypt them Irfan View – reads image files Ingenium – semantic analysis software that searches for meaning rather than an exact ...
... – software that identifies encrypted files and may decrypt them Irfan View – reads image files Ingenium – semantic analysis software that searches for meaning rather than an exact ...
Question Info
... 10. You receive an e-mail message. The sender of the message claims to be a bank executive and wants your personal information to open an account for you. Which one of the following terms describes this activity? A. Spoofing B. Spying C. Hacking D. Phishing 11. You are unable to log on to your e-ma ...
... 10. You receive an e-mail message. The sender of the message claims to be a bank executive and wants your personal information to open an account for you. Which one of the following terms describes this activity? A. Spoofing B. Spying C. Hacking D. Phishing 11. You are unable to log on to your e-ma ...
Understanding the Methods of Network Attacks
... servers—external and internal. The external e-mail server acts as an e-mail relay to the internal e-mail server. Therefore, an attacker attempting to exploit an e-mail vulnerability would have to compromise both e-mail servers to affect the internal corporate e-mail. Also notice the use of a Network ...
... servers—external and internal. The external e-mail server acts as an e-mail relay to the internal e-mail server. Therefore, an attacker attempting to exploit an e-mail vulnerability would have to compromise both e-mail servers to affect the internal corporate e-mail. Also notice the use of a Network ...
Network Security Fundamentals
... • Campus area network (CAN) - A network connecting any number of buildings in an office or university complex (also referred to as a campus wide area network). • Intranet - A “private” network that is accessible only to authorized users. Many large corporations host an intranet to facilitate informa ...
... • Campus area network (CAN) - A network connecting any number of buildings in an office or university complex (also referred to as a campus wide area network). • Intranet - A “private” network that is accessible only to authorized users. Many large corporations host an intranet to facilitate informa ...
Current Internet Threats
... - Number of hosts which were alive during the test : 1 - Number of security holes found : 4 - Number of security warnings found : 18 - Number of security notes found : 4 ...
... - Number of hosts which were alive during the test : 1 - Number of security holes found : 4 - Number of security warnings found : 18 - Number of security notes found : 4 ...
Presentazione di PowerPoint
... Steal personal data Steal other people’s data Steal money Delete and modify data Steal identity Start illegal activities ...
... Steal personal data Steal other people’s data Steal money Delete and modify data Steal identity Start illegal activities ...
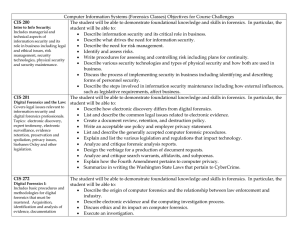
Computer Information Systems (Forensics Classes) Objectives for
... various protocols, responding to attacks on FTP, HTTP, DNS, HTTPS and SSH with advanced attack detection ...
... various protocols, responding to attacks on FTP, HTTP, DNS, HTTPS and SSH with advanced attack detection ...
chap04
... • Areas to inspect when trying to find the reason for a GPO not working as expected – Active Directory hierarchy – Order of Group Policy processing – Containers above and below OU that is causing problem – Group Policy’s Security tab ...
... • Areas to inspect when trying to find the reason for a GPO not working as expected – Active Directory hierarchy – Order of Group Policy processing – Containers above and below OU that is causing problem – Group Policy’s Security tab ...