Lecture 1 - Electrical and Computer Engineering Department
... • Corollary to Moore’s Law: Cost halves every two years – In a decade you can buy a computer for less than its sales tax today --- Jim Gray ...
... • Corollary to Moore’s Law: Cost halves every two years – In a decade you can buy a computer for less than its sales tax today --- Jim Gray ...
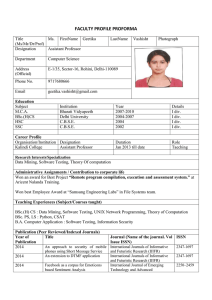
faculty profile proforma
... Data Mining, Software Testing, Theory Of computation Administrative Assignments / Contribution to corporate life Won an award for Best Project “Remote program compilation, execution and assessment system.” at Aricent Nalanda Training. Won best Employee Award at “Samsung Engineering Labs” in File Sys ...
... Data Mining, Software Testing, Theory Of computation Administrative Assignments / Contribution to corporate life Won an award for Best Project “Remote program compilation, execution and assessment system.” at Aricent Nalanda Training. Won best Employee Award at “Samsung Engineering Labs” in File Sys ...
Network Security Analysis Prepared By: cowave Communication
... to be contributed by not allowing any malicious programs to run. ...
... to be contributed by not allowing any malicious programs to run. ...
Chapter 5 Protecting Information Resources
... Travels from computer to computer in a network ◦ Does not usually erase data ...
... Travels from computer to computer in a network ◦ Does not usually erase data ...
IIDPS: An Internal Intrusion Detection and
... Over the past several years, the Internet environment has become more complex and untrusted. Enterprise networked systems are inevitably exposed to the increasing threats posed by hackers as well as malicious users internal to a network. IDS technology is one of the important tools used now-a-days, ...
... Over the past several years, the Internet environment has become more complex and untrusted. Enterprise networked systems are inevitably exposed to the increasing threats posed by hackers as well as malicious users internal to a network. IDS technology is one of the important tools used now-a-days, ...
This Article argues that intellectual property law stifles critical
... vulnerabilities. Researchers who discover flaws often face legal threats based on IP claims if they reveal findings to anyone other than the software’s vendor. Externalities and network effects cause vendors’ incentives to diverge from those that are socially optimal. Unlike previous scholarship, th ...
... vulnerabilities. Researchers who discover flaws often face legal threats based on IP claims if they reveal findings to anyone other than the software’s vendor. Externalities and network effects cause vendors’ incentives to diverge from those that are socially optimal. Unlike previous scholarship, th ...
security_6
... cyber-criminals who use email, popup messages or an imitation or copy of an existing legitimate webpage to trick users into providing sensitive personal information such as credit card numbers, bank account numbers, and passwords. ...
... cyber-criminals who use email, popup messages or an imitation or copy of an existing legitimate webpage to trick users into providing sensitive personal information such as credit card numbers, bank account numbers, and passwords. ...
Breaking Trust On The Internet
... • A computer virus is a small software program that spreads from one computer to another and interferes with computer operation. • A computer virus might corrupt or delete data on a computer, use an email program to spread the virus to other computers, or even delete everything on the hard disk. ...
... • A computer virus is a small software program that spreads from one computer to another and interferes with computer operation. • A computer virus might corrupt or delete data on a computer, use an email program to spread the virus to other computers, or even delete everything on the hard disk. ...
IT Essentials (CompTIA A+ certification)
... 4. Overview of Preventative Maintenance and Troubleshooting 5. Operating Systems 6. Networks 7. Laptops 8. Mobile Devices 9. Printers 10.Security 11.The IT Professional 12.Advanced Troubleshooting ...
... 4. Overview of Preventative Maintenance and Troubleshooting 5. Operating Systems 6. Networks 7. Laptops 8. Mobile Devices 9. Printers 10.Security 11.The IT Professional 12.Advanced Troubleshooting ...
• Overview of Cyber Security & need of cyber security • Introduction
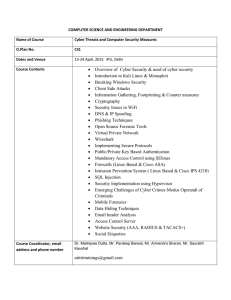
... COMPUTER SCIENCE AND ENGINEERING DEPARTMENT Name of Course ...
... COMPUTER SCIENCE AND ENGINEERING DEPARTMENT Name of Course ...
Position: Senior IA/Security Specialist, (Computer Network Defense
... robust cyber security management program and associated network defenses for NAVAIR networks. Responsibilities: • Conduct system administration, analysis, design, implementation, and operation for NAVAIR RDT&E and NMCI/NGEN networks • Recommend solutions as authorized/needed in accordance with cyber ...
... robust cyber security management program and associated network defenses for NAVAIR networks. Responsibilities: • Conduct system administration, analysis, design, implementation, and operation for NAVAIR RDT&E and NMCI/NGEN networks • Recommend solutions as authorized/needed in accordance with cyber ...
Open ended challenge rationale
... A virus or physical device that logs keystrokes to secretly capture private information such as passwords or credit card details. ...
... A virus or physical device that logs keystrokes to secretly capture private information such as passwords or credit card details. ...
Pan-Oston Company, a Houchens Industries Employee Owned
... Ensures that all computers and associated equipment are operational at all times Monitors hardware systems using operating systems and executes daily backups Performance duties associated with batch processing of jobs and distributes appropriate reports Solves commonly occurring operations problems ...
... Ensures that all computers and associated equipment are operational at all times Monitors hardware systems using operating systems and executes daily backups Performance duties associated with batch processing of jobs and distributes appropriate reports Solves commonly occurring operations problems ...
Department of Computer Science and Engineering
... communications and signal processing, information security, embedded systems design, computer architecture, multimedia networks, and WWW technologies, provide additional depth of knowledge from a wide spectrum of fields in computer science. The mission of the Department is clear: we are here to insp ...
... communications and signal processing, information security, embedded systems design, computer architecture, multimedia networks, and WWW technologies, provide additional depth of knowledge from a wide spectrum of fields in computer science. The mission of the Department is clear: we are here to insp ...
Digital Literacy – Computer Basics – Common Computer Terminology
... What is hardware? What do you use hardware for? What is a motherboard? What controls and manages the hardware connected to your computer? What is a GUI interface? What term is used to describe the hardware and the operating system together? What is a synonym for program? List four types of data that ...
... What is hardware? What do you use hardware for? What is a motherboard? What controls and manages the hardware connected to your computer? What is a GUI interface? What term is used to describe the hardware and the operating system together? What is a synonym for program? List four types of data that ...