Computer Systems Security
... other security mechanisms in place Originally, backdoors were used by developers as a legitimate way of accessing an application, but soon after they were implemented by attackers who would use backdoors to make changes to operating systems, websites, and network devices Quite often, it is installed ...
... other security mechanisms in place Originally, backdoors were used by developers as a legitimate way of accessing an application, but soon after they were implemented by attackers who would use backdoors to make changes to operating systems, websites, and network devices Quite often, it is installed ...
Srini Devadas, MIT Computer Science and Artificial Intelligence Lab
... similar to performance and energy • Attackers take a holistic view by attacking any component or interface of system • Diverse threat models dictate different desirable security properties – Viruses and worms: Bug-free programs – Denial-of-Service attacks: Redundant resources – Cyberphysical attacks ...
... similar to performance and energy • Attackers take a holistic view by attacking any component or interface of system • Diverse threat models dictate different desirable security properties – Viruses and worms: Bug-free programs – Denial-of-Service attacks: Redundant resources – Cyberphysical attacks ...
Network Security Management.pdf
... and taking actions to close it are high. Using a tool to help in these tasks will reduce errors, saves costs by eliminating redundant actions, streamlines actions by prioritizing between multiple bugs and actions. It also gives you a chance to plan ahead (“what if I find a problem with a web server? ...
... and taking actions to close it are high. Using a tool to help in these tasks will reduce errors, saves costs by eliminating redundant actions, streamlines actions by prioritizing between multiple bugs and actions. It also gives you a chance to plan ahead (“what if I find a problem with a web server? ...
Computer Ethics
... program that can copy itself and infect a computer. The term "virus" is also commonly but erroneously used to refer to other types of malware, adware, and spyware programs that do not have the reproductive ability. ...
... program that can copy itself and infect a computer. The term "virus" is also commonly but erroneously used to refer to other types of malware, adware, and spyware programs that do not have the reproductive ability. ...
Security Resume - Kirubha Shankar Murugesan
... Experience with networking protocols such as BGP, OSPF, etc. Network Security Tools and Algorithms(Python): Jan 2016 - Apr 2016 Ornamented both the RSA and MD5 algorithm with optimum speed and efficiency. Studied various Penetration testing techniques using Kali OS that can be applied to any n ...
... Experience with networking protocols such as BGP, OSPF, etc. Network Security Tools and Algorithms(Python): Jan 2016 - Apr 2016 Ornamented both the RSA and MD5 algorithm with optimum speed and efficiency. Studied various Penetration testing techniques using Kali OS that can be applied to any n ...
CIS 203 Artificial Intelligence
... 4) “Besides AI-powered heuristics, other IS systems like firewalls and intrusion prevention systems (IPS) are also tapping into AI. “ For example, new intrusion prevention systems are now able to stop attacks as they happen - a huge leap from older intrusion detection systems (IDS) that merely notif ...
... 4) “Besides AI-powered heuristics, other IS systems like firewalls and intrusion prevention systems (IPS) are also tapping into AI. “ For example, new intrusion prevention systems are now able to stop attacks as they happen - a huge leap from older intrusion detection systems (IDS) that merely notif ...
Neal Ziring Very Short Bio
... Mr. Neal Ziring is the Technical Director for the National Security Agency’s Capabilities Directorate, serving as a technical advisor to the Capabilities Director, Deputy Director, and other senior leadership. Mr. Ziring is responsible for setting the technical direction across many parts of the cap ...
... Mr. Neal Ziring is the Technical Director for the National Security Agency’s Capabilities Directorate, serving as a technical advisor to the Capabilities Director, Deputy Director, and other senior leadership. Mr. Ziring is responsible for setting the technical direction across many parts of the cap ...
Computer Science, MSCS - Northeastern University
... Computer Science, MSCS Northeastern University’s Master of Science in Computer Science is designed to prepare students for a variety of careers in computer science. The program combines both computing and important application domains—enabling you to increase your broad-based knowledge in the field ...
... Computer Science, MSCS Northeastern University’s Master of Science in Computer Science is designed to prepare students for a variety of careers in computer science. The program combines both computing and important application domains—enabling you to increase your broad-based knowledge in the field ...
Computer GEEK - Ideas
... and other functions such as printing depends on servers. Close to 100% reliability is essential. ...
... and other functions such as printing depends on servers. Close to 100% reliability is essential. ...
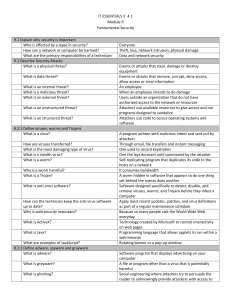
IT ESSENTIALS V. 4.1 Module 9 Fundamental Security 9.1 Explain
... personal information Monitors activity on the computer and sends this information to the organization responsible for launching the spyware A form of attack that prevents users from accessing normal services because the system is busy responding to abnormally large amounts of requests Ping of death; ...
... personal information Monitors activity on the computer and sends this information to the organization responsible for launching the spyware A form of attack that prevents users from accessing normal services because the system is busy responding to abnormally large amounts of requests Ping of death; ...
Securing Information Systems
... • Firewalls: Hardware and software controlling flow of incoming and outgoing network traffic – Packet Filtering examines selected fields in the headers of data packets flowing back and forth from network and the Internet – Stateful inspection provides additional security by determining whether packe ...
... • Firewalls: Hardware and software controlling flow of incoming and outgoing network traffic – Packet Filtering examines selected fields in the headers of data packets flowing back and forth from network and the Internet – Stateful inspection provides additional security by determining whether packe ...
ch 5 - sm.luth.se
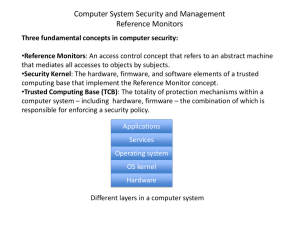
... Three fundamental concepts in computer security: •Reference Monitors: An access control concept that refers to an abstract machine that mediates all accesses to objects by subjects. •Security Kernel: The hardware, firmware, and software elements of a trusted computing base that implement the Referen ...
... Three fundamental concepts in computer security: •Reference Monitors: An access control concept that refers to an abstract machine that mediates all accesses to objects by subjects. •Security Kernel: The hardware, firmware, and software elements of a trusted computing base that implement the Referen ...
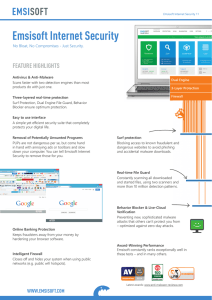
Emsisoft Internet Security
... Blocker ensure optimum protection. Easy to use interface A simple yet efficient security suite that completely protects your digital life. Removal of Potentially Unwanted Programs ...
... Blocker ensure optimum protection. Easy to use interface A simple yet efficient security suite that completely protects your digital life. Removal of Potentially Unwanted Programs ...
chapter 5 – basic security
... all attacks do damage or prevent legitimate users from having access to resources. Many threats are designed to collect information about users which can be used for advertising, marketing and research purposes. These include Spyware, Tracking Cookies, Adware and Pop-ups. While these may not damage ...
... all attacks do damage or prevent legitimate users from having access to resources. Many threats are designed to collect information about users which can be used for advertising, marketing and research purposes. These include Spyware, Tracking Cookies, Adware and Pop-ups. While these may not damage ...
Networking & Security
... Computer Access Information from misusage (Password, Digital Ids, Account No., Credit Card Nos. etc.) ...
... Computer Access Information from misusage (Password, Digital Ids, Account No., Credit Card Nos. etc.) ...
EFF / TCPA Roundtable - Oxford Internet Institute
... the total network is the real action the computers are no longer the motivating item as in the early days no longer can we develop computers without paying attention to the networks no longer can we develop networks without wondering if our computer architectures are OK ...
... the total network is the real action the computers are no longer the motivating item as in the early days no longer can we develop computers without paying attention to the networks no longer can we develop networks without wondering if our computer architectures are OK ...
Computer Concepts And Applications CIS-107-TE
... This TECEP® tests content covered in a one-semester course in computer concepts and applications. It focuses on an overview of computers, including historical development; hardware; application software; communications; Internet use; how to purchase, install, and maintain a computer; information sys ...
... This TECEP® tests content covered in a one-semester course in computer concepts and applications. It focuses on an overview of computers, including historical development; hardware; application software; communications; Internet use; how to purchase, install, and maintain a computer; information sys ...
Acceptable Use Policy (AUP)
... Security is a high priority due to the number of users. Identified security problems should be reported to a system administrator or appropriate teacher immediately and not shared with other users. Attempts to log on as another user may result in cancellation of user privileges. Any user identified ...
... Security is a high priority due to the number of users. Identified security problems should be reported to a system administrator or appropriate teacher immediately and not shared with other users. Attempts to log on as another user may result in cancellation of user privileges. Any user identified ...
Computer Science 335
... • Many issues occur in a number of places • Understanding it once can be leveraged into the understanding of numerous features • Keep these issues at the forefront of learning • Many of your experiences will be similar but the wrong one. Be careful. Ask questions. • OSI model is not only a tool for ...
... • Many issues occur in a number of places • Understanding it once can be leveraged into the understanding of numerous features • Keep these issues at the forefront of learning • Many of your experiences will be similar but the wrong one. Be careful. Ask questions. • OSI model is not only a tool for ...
Why Cryptography is Harder Than It Looks
... – Motivation of attackers • Vast knowledge and free time • Few financial resources and / or vendetta ...
... – Motivation of attackers • Vast knowledge and free time • Few financial resources and / or vendetta ...
recr_presentation_oldest - Computer Science and Engineering
... • Intelligent Memory Devices (IRAM) – Processing unit embedded in the ...
... • Intelligent Memory Devices (IRAM) – Processing unit embedded in the ...
Systems Security
... The basic computer infrastructure, ranging from consumer desktops to business servers are under continual attack from a variety of miscreants (or “hackers”) for both fun and monetary gain. The design of computer systems have allowed many vulnerabilities to exist and the attacks exploit these vulnera ...
... The basic computer infrastructure, ranging from consumer desktops to business servers are under continual attack from a variety of miscreants (or “hackers”) for both fun and monetary gain. The design of computer systems have allowed many vulnerabilities to exist and the attacks exploit these vulnera ...