GCSE-Computing-Summary
... i) describe the nature of the internet as a worldwide collection of computer networks j) describe the hardware needed to connect to the internet including modems, routers k) explain the need for IP addressing of resources on the internet and how this can be facilitated by the role of DNS services l) ...
... i) describe the nature of the internet as a worldwide collection of computer networks j) describe the hardware needed to connect to the internet including modems, routers k) explain the need for IP addressing of resources on the internet and how this can be facilitated by the role of DNS services l) ...
What is Penetration Testing?
... What is Penetration Testing? • A penetration test is a method of evaluating the security of a computer system or network by simulating an attack from a malicious source. • The process involves an active analysis of the system for any potential vulnerabilities that may result from poor or improper s ...
... What is Penetration Testing? • A penetration test is a method of evaluating the security of a computer system or network by simulating an attack from a malicious source. • The process involves an active analysis of the system for any potential vulnerabilities that may result from poor or improper s ...
EEE449 Assignment
... If you are using a PC running Windows 98,2000, XP, you may find out more about each of these commands by typing 'xxx /?' where xxx is the name of the command about which you wish to know more. For example 'ping /?' will usually provide information about how to use the ping command and what options a ...
... If you are using a PC running Windows 98,2000, XP, you may find out more about each of these commands by typing 'xxx /?' where xxx is the name of the command about which you wish to know more. For example 'ping /?' will usually provide information about how to use the ping command and what options a ...
Circumvention Defense Network (CDN)
... EdgeWave Leverages hundreds of frequently-reset virtual machines that are hosted in our scalable cloud data center to detect thousands of externally-hosted non-web servers used by various circumvention tools to proxy or re-route users’ web requests. We then correlate and filter these IP addresses ag ...
... EdgeWave Leverages hundreds of frequently-reset virtual machines that are hosted in our scalable cloud data center to detect thousands of externally-hosted non-web servers used by various circumvention tools to proxy or re-route users’ web requests. We then correlate and filter these IP addresses ag ...
An Immucor Technical Support Solution
... Yes, blud_direct utilizes the Secure Socket Layer (SSL) protocol, commonly used for secure transactions over the web. Additionally, the application uses 256-bit AES encryption to further secure the communication. Is there software loaded on our instrument computer? No. There is no software to load o ...
... Yes, blud_direct utilizes the Secure Socket Layer (SSL) protocol, commonly used for secure transactions over the web. Additionally, the application uses 256-bit AES encryption to further secure the communication. Is there software loaded on our instrument computer? No. There is no software to load o ...
1 Introduction
... infecting files on a network file system or a file system that is accessed by another computer such as file server’s files. Viruses are sometimes confused with worms. A worm, however, can spread itself to other computers without needing to be transferred as part of a host. A virus is a type of progr ...
... infecting files on a network file system or a file system that is accessed by another computer such as file server’s files. Viruses are sometimes confused with worms. A worm, however, can spread itself to other computers without needing to be transferred as part of a host. A virus is a type of progr ...
Threats in the Digital World
... White Hats are also called “ethical" hackers, such as the Axent (now Symantec) Tiger Team Black Hats disregard generally accepted social conventions and laws. Script kiddie is a derogatory term for a wannabe cracker who lacks programming skills and thus relies on prewritten scripts and toolkits for ...
... White Hats are also called “ethical" hackers, such as the Axent (now Symantec) Tiger Team Black Hats disregard generally accepted social conventions and laws. Script kiddie is a derogatory term for a wannabe cracker who lacks programming skills and thus relies on prewritten scripts and toolkits for ...
of network
... users and data (need to know). The effect of any security software packages that restrict or control access to files, records, or data items should be reviewed. Adequate user training on network security should be provided through self-teaching manuals, newsletters, policy statements, and short cour ...
... users and data (need to know). The effect of any security software packages that restrict or control access to files, records, or data items should be reviewed. Adequate user training on network security should be provided through self-teaching manuals, newsletters, policy statements, and short cour ...
5.Transport Layer
... provided by the network layer and specifically how the Internet uses IP to provide unreliable connectionless packet delivery service. Building on top of this, transport protocols must provide reliable end-to-end communication, independent of the underlying network used. In order to describe the serv ...
... provided by the network layer and specifically how the Internet uses IP to provide unreliable connectionless packet delivery service. Building on top of this, transport protocols must provide reliable end-to-end communication, independent of the underlying network used. In order to describe the serv ...
Bots and Botnets - IT Services Technical Notes
... Bot – nothing more than a remotely controlled program A collection of bots controlled at a central source are botnets Most bots have their origin in some segment of the IRC community Botnet controllers are either public IRC servers or custom private IRC servers ...
... Bot – nothing more than a remotely controlled program A collection of bots controlled at a central source are botnets Most bots have their origin in some segment of the IRC community Botnet controllers are either public IRC servers or custom private IRC servers ...
www.acotserver.com
... – Physical limitation • Designed to keep collision detection (CSMA/CD) working properly ...
... – Physical limitation • Designed to keep collision detection (CSMA/CD) working properly ...
Janos detailed overview 3/30/99 - University of Utah School of
... Investigate OS support for active networking ...
... Investigate OS support for active networking ...
janos-pimteam3-990330 - University of Utah School of Computing
... Investigate OS support for active networking ...
... Investigate OS support for active networking ...
Introduction to Computer Networking
... Introduction to Computer Networking The Internet today is a combination of both the star and tree structure. Local networks are configured as stars (ethernet) and these are interconnected in a tree (IP). Computers on the local ethernet network are connected by way of an ethernet switch. Each of the ...
... Introduction to Computer Networking The Internet today is a combination of both the star and tree structure. Local networks are configured as stars (ethernet) and these are interconnected in a tree (IP). Computers on the local ethernet network are connected by way of an ethernet switch. Each of the ...
Permissions
... What is Network Security? • According to Wikipedia: – “In the field of networking, the specialist area of network security consists of the provisions and policies adopted by the network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of the computer network ...
... What is Network Security? • According to Wikipedia: – “In the field of networking, the specialist area of network security consists of the provisions and policies adopted by the network administrator to prevent and monitor unauthorized access, misuse, modification, or denial of the computer network ...
Internet and Network Attacks
... Computer-related health issues, their preventions, and ways to keep the environment healthy Wireless security risks and safeguards ...
... Computer-related health issues, their preventions, and ways to keep the environment healthy Wireless security risks and safeguards ...
Discovering Computers 2008
... Computer-related health issues, their preventions, and ways to keep the environment healthy Wireless security risks and safeguards ...
... Computer-related health issues, their preventions, and ways to keep the environment healthy Wireless security risks and safeguards ...
Computer and Information Security
... • Is the web site I am downloading information from a legitimate one, or a fake? • How do I ensure that the person I just did a financial transaction denies having done it tomorrow or at a later time? • I want to buy some thing online, but I don’t want to let them charge my credit card before they d ...
... • Is the web site I am downloading information from a legitimate one, or a fake? • How do I ensure that the person I just did a financial transaction denies having done it tomorrow or at a later time? • I want to buy some thing online, but I don’t want to let them charge my credit card before they d ...
Essentials of Business Information Systems Chapter 7 Securing
... Technologies and Tools for Security Firewalls, Intrusion Detection Systems, and Antivirus Software • Firewall: • Combination of hardware and software that prevents unauthorized users from accessing private networks. Often resides on separate computer to prevent unauthorized access to network • Tech ...
... Technologies and Tools for Security Firewalls, Intrusion Detection Systems, and Antivirus Software • Firewall: • Combination of hardware and software that prevents unauthorized users from accessing private networks. Often resides on separate computer to prevent unauthorized access to network • Tech ...
New Network Topologies
... single circle of cable. There is no terminated ends Signals travel around the loop in one direction and pass through each computer. Unlike bus topology, each computer acts like a repeater to boost the signal and send it to the next computer. ...
... single circle of cable. There is no terminated ends Signals travel around the loop in one direction and pass through each computer. Unlike bus topology, each computer acts like a repeater to boost the signal and send it to the next computer. ...
A451 Computer Systems Checklist
... explain the different roles of computers in a client-server and a peer-to-peer network describe, using diagrams or otherwise, the ring, bus and star network topologies describe the differences between a local area network and a wide area network such as the internet explain the terms IP addressing, ...
... explain the different roles of computers in a client-server and a peer-to-peer network describe, using diagrams or otherwise, the ring, bus and star network topologies describe the differences between a local area network and a wide area network such as the internet explain the terms IP addressing, ...
Discovering Computers 2006
... Chapter 11 Objectives Describe the types of computer security risks ...
... Chapter 11 Objectives Describe the types of computer security risks ...
A Comparison of
... pcAnywhere™: pcAnywhere™ supports a wide variety of security features. But most users will not know how to set them up appropriately for maximum security, typically leaving the settings at default values. After a pcAnywhere™ session is closed, the connection information is still on the client system ...
... pcAnywhere™: pcAnywhere™ supports a wide variety of security features. But most users will not know how to set them up appropriately for maximum security, typically leaving the settings at default values. After a pcAnywhere™ session is closed, the connection information is still on the client system ...
Ch01_StudyGuide
... Manages information storage and retrieval, through devices such as hard disks and CD-ROMs Enables multimedia functions, such as accessing video clips and playing music At every level of operation, the operating system has the potential to provide security functions. For example, the operating sy ...
... Manages information storage and retrieval, through devices such as hard disks and CD-ROMs Enables multimedia functions, such as accessing video clips and playing music At every level of operation, the operating system has the potential to provide security functions. For example, the operating sy ...
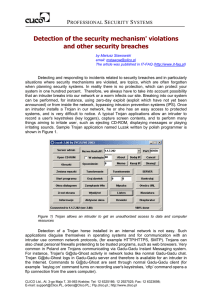
Detection of the security mechanism` violations and other
... explaining security breaches. The analysis of events logged by IDP/IDS systems is difficult because Internet worms generate many attacks and therefore well-thought-of intruders' attacks can go unspotted. The analysis of several thousands events recorded in an IPS/IDS log requires that a vendor of a ...
... explaining security breaches. The analysis of events logged by IDP/IDS systems is difficult because Internet worms generate many attacks and therefore well-thought-of intruders' attacks can go unspotted. The analysis of several thousands events recorded in an IPS/IDS log requires that a vendor of a ...