UNIX Foundations - Computer Science
... Update the u area to refer to the new ATM & Swap space Add the child to the set of processes sharing the text region of the program Duplicate the parent’s data and stack regions update ATM to refer to these new pages. Acquire references to shared resources inherited by the child Initialize ...
... Update the u area to refer to the new ATM & Swap space Add the child to the set of processes sharing the text region of the program Duplicate the parent’s data and stack regions update ATM to refer to these new pages. Acquire references to shared resources inherited by the child Initialize ...
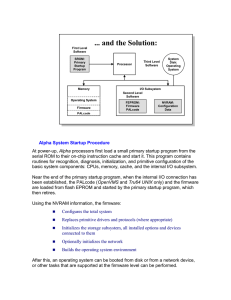
Alpha System Startup Procedure
... when testing application compatibility across different versions of Windows NT. Each time you install a separate version of Windows NT, a new operating system selection is created. Although you can start any of the installed versions of Windows NT, one of the installed versions must be the primary o ...
... when testing application compatibility across different versions of Windows NT. Each time you install a separate version of Windows NT, a new operating system selection is created. Although you can start any of the installed versions of Windows NT, one of the installed versions must be the primary o ...
1. Introduction
... • Use hardware & software facilities, that research institutes in the world have, to solve very complicated scientific research and computational problems. ...
... • Use hardware & software facilities, that research institutes in the world have, to solve very complicated scientific research and computational problems. ...
GX3512131216
... Root File System: File system will tell how the files are arranged in the internal standard storage devices. In embedded Linux, kernel treats everything as a file even the input and output devices also. In embedded Linux, Root is the parent directory it contains other sub directories like dev, lib, ...
... Root File System: File system will tell how the files are arranged in the internal standard storage devices. In embedded Linux, kernel treats everything as a file even the input and output devices also. In embedded Linux, Root is the parent directory it contains other sub directories like dev, lib, ...
What is GNU/Linux?
... Advanced graphical user interface. Linux uses a standard, network transparent X-windowing system with a "window manager" (typically KDE or GNOME but several are available). ...
... Advanced graphical user interface. Linux uses a standard, network transparent X-windowing system with a "window manager" (typically KDE or GNOME but several are available). ...
2.01
... Exact type and amount of information vary according to OS and call Three general methods used to pass parameters to the OS Simplest: pass the parameters in registers In some cases, may be more parameters than registers Parameters stored in a block, or table, in memory, and address of block p ...
... Exact type and amount of information vary according to OS and call Three general methods used to pass parameters to the OS Simplest: pass the parameters in registers In some cases, may be more parameters than registers Parameters stored in a block, or table, in memory, and address of block p ...
Lecture 6 File Systems
... 2. The directory entry must be of variable size, resulting in more complicated space management. ...
... 2. The directory entry must be of variable size, resulting in more complicated space management. ...
Microkernel Operating Systems
... programming errors in operating system code Goal: Show that common OS errors in a properly isolated extension cannot propagate and damage the system. Method: Inject faults into an extension in order to induce a failure, and observe how the system is affected. ...
... programming errors in operating system code Goal: Show that common OS errors in a properly isolated extension cannot propagate and damage the system. Method: Inject faults into an extension in order to induce a failure, and observe how the system is affected. ...
資工系網媒所NEWS實驗室
... Protection – any mechanism for controlling access of processes or users to resources defined by the OS Security – defense of the system against internal and external attacks Huge range, including denial-of-service, worms, viruses, identity theft, theft of service ...
... Protection – any mechanism for controlling access of processes or users to resources defined by the OS Security – defense of the system against internal and external attacks Huge range, including denial-of-service, worms, viruses, identity theft, theft of service ...
C Programming under Linux
... The origins of Linux are in an operating system called UNICS c. 1969. This system developed into UNIX through the 70s – in parallel with a new programming language written for its operating system, C. Unix was developed initially on hugely expensive computers costing millions of $, £ or Euros. Unix ...
... The origins of Linux are in an operating system called UNICS c. 1969. This system developed into UNIX through the 70s – in parallel with a new programming language written for its operating system, C. Unix was developed initially on hugely expensive computers costing millions of $, £ or Euros. Unix ...
Slides
... likelihood of human error when entering command lines, i.e. typos and missing file names. ...
... likelihood of human error when entering command lines, i.e. typos and missing file names. ...
What Is Operating System? Operating Systems, System Calls, and Buffered I/O
... • Protection & security: make the machine safe (COS318) File System ...
... • Protection & security: make the machine safe (COS318) File System ...
Lecture 1 - Department of Computer Science
... • Memory Manager: tracks program’s location and progress as it is executed by the Processor Manager • Processor Manager: receives a ‘finished’ message when the program has finished executing and forwards this message to the Device Manager which displays the message on the monitor ...
... • Memory Manager: tracks program’s location and progress as it is executed by the Processor Manager • Processor Manager: receives a ‘finished’ message when the program has finished executing and forwards this message to the Device Manager which displays the message on the monitor ...
The Macintosh File System (continued)
... • Equipped with security features that meet the U.S. government’s C2 security specifications – high-level, “top secret” standards for data protection, system auditing, and system access ...
... • Equipped with security features that meet the U.S. government’s C2 security specifications – high-level, “top secret” standards for data protection, system auditing, and system access ...
Introduction to CS-4513
... • If (my distance to network > neighbor’s distance to network + my distance to neighbor), then … • … update my table entry for that network so that neighbor is ...
... • If (my distance to network > neighbor’s distance to network + my distance to neighbor), then … • … update my table entry for that network so that neighbor is ...
PowerPoint Presentation - Interfaces By: Ben Griffin and
... Today, most users prefer the graphical user interface (GUI) offered by Windows, Mac OS, BeOS, and others. Typically, most of today's Unix-based systems offer both a command line interface and a graphical user interface. ...
... Today, most users prefer the graphical user interface (GUI) offered by Windows, Mac OS, BeOS, and others. Typically, most of today's Unix-based systems offer both a command line interface and a graphical user interface. ...
Chapter 1
... I/O devices and the CPU can execute concurrently. Each device controller is in charge of a particular device type. Depending on the device controller, there may be more than one attached device. For example seven or more devices can be attached to a SCSI (small computer system interface) controlle ...
... I/O devices and the CPU can execute concurrently. Each device controller is in charge of a particular device type. Depending on the device controller, there may be more than one attached device. For example seven or more devices can be attached to a SCSI (small computer system interface) controlle ...
PPT Chapter 01
... Abstract view of a resource taken by a program Supported by OS through use of a real resource Same real resource may support several virtual ones Started with the use of virtual devices • E.g., a print server ...
... Abstract view of a resource taken by a program Supported by OS through use of a real resource Same real resource may support several virtual ones Started with the use of virtual devices • E.g., a print server ...
QNX OS for Security
... running even after faults. No other commercial RTOS provides such a high level of fault containment and recovery. ...
... running even after faults. No other commercial RTOS provides such a high level of fault containment and recovery. ...
Ceng 334 - Operating Systems
... • An input queue is where hardware generated messages such as mouse clicks and keystrokes are stored for app retrieveal • Win95 assigns each application its own input queue • In Windows 3.x there is only one input queue so a misbehaving process may delay all other applications Ceng 334 - Operating S ...
... • An input queue is where hardware generated messages such as mouse clicks and keystrokes are stored for app retrieveal • Win95 assigns each application its own input queue • In Windows 3.x there is only one input queue so a misbehaving process may delay all other applications Ceng 334 - Operating S ...
Thread - Nipissing University Word
... Presents users (and applications) with an integrated computing ...
... Presents users (and applications) with an integrated computing ...
Chapter 2 – outline
... possible to locate files based on a description of their content. MAC OS (127) One of the first GUIs, making it easy even for novice computer users to move and delete files. Designed to run with Apple computers. Not nearly as widely used as the Windows operating system. Fewer application pro ...
... possible to locate files based on a description of their content. MAC OS (127) One of the first GUIs, making it easy even for novice computer users to move and delete files. Designed to run with Apple computers. Not nearly as widely used as the Windows operating system. Fewer application pro ...
Things to Know while installing Linux OS
... is an enterprise-level storage network of several (often, hundreds) of hard drives managed by an intelligent device. This allows for maximally efficient use of all available storage space, lowering total costs of ownership (TCO) and increasing return on investment (ROI). Most importantly, if a drive ...
... is an enterprise-level storage network of several (often, hundreds) of hard drives managed by an intelligent device. This allows for maximally efficient use of all available storage space, lowering total costs of ownership (TCO) and increasing return on investment (ROI). Most importantly, if a drive ...
Plan 9 from Bell Labs
.png?width=300)
Plan 9 from Bell Labs is a distributed operating system, originally developed by the Computing Sciences Research Center at Bell Labs between the mid-1980s and 2002. It takes some of the principles of Unix, developed in the same research group, but extends these to a networked environment with graphics terminals.In Plan 9, virtually all computing resources, including files, network connections, and peripheral devices, are represented through the file system rather than specialized interfaces. A unified network protocol called 9P ties a network of computers running Plan 9 together, allowing them to share all resources so represented.The name Plan 9 from Bell Labs is a reference to the Ed Wood 1959 cult science fiction Z-movie Plan 9 from Outer Space. Also, Glenda, the Plan 9 Bunny, is presumably a reference to Wood's film Glen or Glenda. The system continues to be used and developed by operating system researchers and hobbyists.