notes - University of Arizona Computer Science
... Multi-programmed: OS runs multiple processes simultaneously Process: running program Timeshared: multiple users share the system simultaneously ...
... Multi-programmed: OS runs multiple processes simultaneously Process: running program Timeshared: multiple users share the system simultaneously ...
Lecture-2
... I/O operations - A running program may require I/O, which may involve a file or an I/O device. File-system manipulation - The file system is of particular interest. Obviously, programs need to read and write files and directories, create and delete them, search them, list file Information, permi ...
... I/O operations - A running program may require I/O, which may involve a file or an I/O device. File-system manipulation - The file system is of particular interest. Obviously, programs need to read and write files and directories, create and delete them, search them, list file Information, permi ...
COSC A365 Chapter 1
... Process termination requires reclaim of any reusable resources Program is passive, process is active, unit of work within system Single-threaded process has one program counter specifying location of next instruction to execute ...
... Process termination requires reclaim of any reusable resources Program is passive, process is active, unit of work within system Single-threaded process has one program counter specifying location of next instruction to execute ...
Section for Related Work % \section{Related Work} Rootkit detection
... in the context of servers and personal computers. However, there has been little research to date with respect to rootkit detection or prevention methods on smartphones such as Android. But, given the fact that the Android framework is built on top of the Linux kernel, many of the proposed methods t ...
... in the context of servers and personal computers. However, there has been little research to date with respect to rootkit detection or prevention methods on smartphones such as Android. But, given the fact that the Android framework is built on top of the Linux kernel, many of the proposed methods t ...
Scheduling Scheduling Criteria Scheduling algorithms Shortest Job
... Solution: Increase priority of processes after a while (Ageing) Eike Ritter ...
... Solution: Increase priority of processes after a while (Ageing) Eike Ritter ...
HDD for Operating System Concepts
... Education and Research Department, Infosys Technologies Limited. This document is not for general distribution and is meant for use only for the person they are specifically issued to. This document shall not be loaned to anyone, within or outside Infosys, including its customers. Copying or unautho ...
... Education and Research Department, Infosys Technologies Limited. This document is not for general distribution and is meant for use only for the person they are specifically issued to. This document shall not be loaned to anyone, within or outside Infosys, including its customers. Copying or unautho ...
Module 3: Operating
... and reading to the same memory addresses. Processes use map memory system calls to access memory owned by other processes. Both processes must agree to remove O.S. memory restriction so that they can access the same region of memory. The processes are responsible for the form and location of the dat ...
... and reading to the same memory addresses. Processes use map memory system calls to access memory owned by other processes. Both processes must agree to remove O.S. memory restriction so that they can access the same region of memory. The processes are responsible for the form and location of the dat ...
Introduction to Operating Systems
... Unix rewritten in C programming language (1974) Unix utility programs written by students at colleges and universities (continues today) Unix used to share research and data (foundation of the Internet and the WWW) Linus Torvalds orchestrated development of an operating system based on Unix, but abl ...
... Unix rewritten in C programming language (1974) Unix utility programs written by students at colleges and universities (continues today) Unix used to share research and data (foundation of the Internet and the WWW) Linus Torvalds orchestrated development of an operating system based on Unix, but abl ...
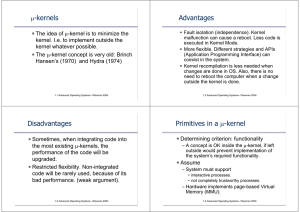
μ-kernels Advantages Disadvantages Primitives in a μ
... The µ-kernel design is extensively depending on the CPU structure. The only µ-kernel feature that can be portable is the scheduler. Large monolithic kernel can have many more portable features. In the early 70's, large portions of the kernel have been started to be written in C, so they could be por ...
... The µ-kernel design is extensively depending on the CPU structure. The only µ-kernel feature that can be portable is the scheduler. Large monolithic kernel can have many more portable features. In the early 70's, large portions of the kernel have been started to be written in C, so they could be por ...
B - Chulmleigh ICT Department
... Worksheet 1.1B What is an operating system? crossword Across 4 This is the part of the operating system that allows the user and the computer to communicate with each other. 5 Pieces of software that allow an operating system to communicate with peripheral devices. 6 A series of the most widely use ...
... Worksheet 1.1B What is an operating system? crossword Across 4 This is the part of the operating system that allows the user and the computer to communicate with each other. 5 Pieces of software that allow an operating system to communicate with peripheral devices. 6 A series of the most widely use ...
Spawn server
... • One unique approach to the organization of multiple communicating processes that fos takes is the use of a naming and lookup scheme. • Processes are able to register a particular name for their mailbox. This namespace is a hierarchical URI(uniform resource identifier) much like a web address or fi ...
... • One unique approach to the organization of multiple communicating processes that fos takes is the use of a naming and lookup scheme. • Processes are able to register a particular name for their mailbox. This namespace is a hierarchical URI(uniform resource identifier) much like a web address or fi ...
File-System
... information needed for remote computing In Windows CIFS (common internet file system), network information is used with user authentication to create a network login. A newer version is called active directory. One distributed LDAP (lightweight directory-access protocol) could be used by an orga ...
... information needed for remote computing In Windows CIFS (common internet file system), network information is used with user authentication to create a network login. A newer version is called active directory. One distributed LDAP (lightweight directory-access protocol) could be used by an orga ...
Slides
... I/O operations - A running program may require I/O, which may involve a file or an I/O device File-system manipulation - The file system is of particular interest. Obviously, programs need to read and write files and directories, create and delete them, search them, list file Information, permission ...
... I/O operations - A running program may require I/O, which may involve a file or an I/O device File-system manipulation - The file system is of particular interest. Obviously, programs need to read and write files and directories, create and delete them, search them, list file Information, permission ...
Computer Science - Rainhill High School
... Understand that there are two ways to manage files and folders Be able to move, copy, rename and delete files and folders at a command prompt Be able to identify advantages and disadvantages of both graphical and command line methods for managing files and folders Understand the link between the GUI ...
... Understand that there are two ways to manage files and folders Be able to move, copy, rename and delete files and folders at a command prompt Be able to identify advantages and disadvantages of both graphical and command line methods for managing files and folders Understand the link between the GUI ...
pentest
... Response time - amount of time it takes from when a request was submitted until the first response is ...
... Response time - amount of time it takes from when a request was submitted until the first response is ...
Operating Systems - School of Computer Science, University of
... Protection - any mechanism for controlling access of processes or users to resources defined by the OS Security - defense of the system against internal and external attacks Huge range, including denial-of-service, worms, viruses, identity theft, theft of service ...
... Protection - any mechanism for controlling access of processes or users to resources defined by the OS Security - defense of the system against internal and external attacks Huge range, including denial-of-service, worms, viruses, identity theft, theft of service ...
ppt
... • PlanetLab can be easily extended • Researchers can create their own infrastructure services for PlanetLab – Services that help maintain PlanetLab itself – Slice creation, performance monitoring, ...
... • PlanetLab can be easily extended • Researchers can create their own infrastructure services for PlanetLab – Services that help maintain PlanetLab itself – Slice creation, performance monitoring, ...
the case for embedded linux
... Windows. However, it has also found a place in the network applications, acting as an office router, Internet firewall or as web and mail servers. Several Internet service providers have built their business on Linux by using it as their service engines. It is also finding its way in many other area ...
... Windows. However, it has also found a place in the network applications, acting as an office router, Internet firewall or as web and mail servers. Several Internet service providers have built their business on Linux by using it as their service engines. It is also finding its way in many other area ...
Distributed File Systems
... whenever two peers shared a common endianness in their machinearchitectures. An industry-group called the Network Computing Forum formed (March 1987) in an (ultimately unsuccessful) attempt to reconcile the two network-computing environments. Later, Sun and AT&T announced that the two firms would jo ...
... whenever two peers shared a common endianness in their machinearchitectures. An industry-group called the Network Computing Forum formed (March 1987) in an (ultimately unsuccessful) attempt to reconcile the two network-computing environments. Later, Sun and AT&T announced that the two firms would jo ...
Server Installation - gozips.uakron.edu
... recognized on the Internet In Linux, the hostname can exist on more than one computer ...
... recognized on the Internet In Linux, the hostname can exist on more than one computer ...
ch02services
... Operating System Design: Layered Approach A common approach to design is to make it hierarchical ...
... Operating System Design: Layered Approach A common approach to design is to make it hierarchical ...
Distributed Systems --- Distribution and Operating Systems
... I This part of the course will be chiefly concerned with the components of a modern operating system which allow for distributed systems I We will examine the design of an operating system within the context that we expect it to be used as part of a network of communicating peers, even if only as a ...
... I This part of the course will be chiefly concerned with the components of a modern operating system which allow for distributed systems I We will examine the design of an operating system within the context that we expect it to be used as part of a network of communicating peers, even if only as a ...
Introduction to Linux
... 8-Setup Linux for scientific purpose start with Linux (tutorial session) ...
... 8-Setup Linux for scientific purpose start with Linux (tutorial session) ...
Plan 9 from Bell Labs
.png?width=300)
Plan 9 from Bell Labs is a distributed operating system, originally developed by the Computing Sciences Research Center at Bell Labs between the mid-1980s and 2002. It takes some of the principles of Unix, developed in the same research group, but extends these to a networked environment with graphics terminals.In Plan 9, virtually all computing resources, including files, network connections, and peripheral devices, are represented through the file system rather than specialized interfaces. A unified network protocol called 9P ties a network of computers running Plan 9 together, allowing them to share all resources so represented.The name Plan 9 from Bell Labs is a reference to the Ed Wood 1959 cult science fiction Z-movie Plan 9 from Outer Space. Also, Glenda, the Plan 9 Bunny, is presumably a reference to Wood's film Glen or Glenda. The system continues to be used and developed by operating system researchers and hobbyists.