ASG-Sentry White Paper
... This approach is useful in extending the range of monitoring at an ASGSentry site, such as to include non-SNMP devices, as well as mainframes. Specifically, ASG-Sentry can use "Trap Alarms" to show CorreLog data on ASG-Sentry Maps and screens. CorreLog serves as an "adaptor / extender" to ASG-Sentry ...
... This approach is useful in extending the range of monitoring at an ASGSentry site, such as to include non-SNMP devices, as well as mainframes. Specifically, ASG-Sentry can use "Trap Alarms" to show CorreLog data on ASG-Sentry Maps and screens. CorreLog serves as an "adaptor / extender" to ASG-Sentry ...
Press text in WinWord format
... euromicron AG is an all-in solution provider for communications, transmission, data and security networks. The network infrastructures of euromicron integrate voice, image and data transfer in wireless mode, via copper cabling, and by means of fiber optic technology. euromicron develops its market-l ...
... euromicron AG is an all-in solution provider for communications, transmission, data and security networks. The network infrastructures of euromicron integrate voice, image and data transfer in wireless mode, via copper cabling, and by means of fiber optic technology. euromicron develops its market-l ...
ABET - Regis University: Academic Web Server for Faculty
... • The role of ethics in an organization is an important component of the culture of an organization and impacts the way Information Technology develops, manages, and distributes data. • Based on the readings this week as well as your own personal experiences, write a three-to-five page paper on the ...
... • The role of ethics in an organization is an important component of the culture of an organization and impacts the way Information Technology develops, manages, and distributes data. • Based on the readings this week as well as your own personal experiences, write a three-to-five page paper on the ...
Quality Attributes of Web Software Applications – Jeff Offutt
... Criteria for success Technology changes ...
... Criteria for success Technology changes ...
Data Communication & Networking
... Given time limit to reach destination Advantages of bus design Requires less cable than other topologies Easy to install and extend bus with a workstation Disadvantages of bus topology ...
... Given time limit to reach destination Advantages of bus design Requires less cable than other topologies Easy to install and extend bus with a workstation Disadvantages of bus topology ...
Overview of Knowledge Discovery in Databases Process and Data
... Development of more effective early warning systems (EWSs) for various applications have been possible during the past decade due to advancements in information, detection, data mining (DM) and surveillance technologies. These application areas include economy, banking, finance, health care, bioinfo ...
... Development of more effective early warning systems (EWSs) for various applications have been possible during the past decade due to advancements in information, detection, data mining (DM) and surveillance technologies. These application areas include economy, banking, finance, health care, bioinfo ...
01-Overview
... with little overhead for error control anything from 10Mbps to Gbps constant data rate using packet switching technique with multiple virtual circuits ...
... with little overhead for error control anything from 10Mbps to Gbps constant data rate using packet switching technique with multiple virtual circuits ...
Breach Detection in Healthcare
... regulations that are broader in reach than ever before. Today’s penalties for data breaches increase, notification requirements are more stringent, and enforcement agencies have new incentives for taking action against organizations that fail to protect healthcare privacy. Next to that, the require ...
... regulations that are broader in reach than ever before. Today’s penalties for data breaches increase, notification requirements are more stringent, and enforcement agencies have new incentives for taking action against organizations that fail to protect healthcare privacy. Next to that, the require ...
Caldicott - Acute Trusts Knowledge base
... The CTP should undertake regular audits of mobile and/or teleworking arrangements, ensuring that all users are approved that, all mobile device and removable media assets can be accounted for, that secure remote access is possible and used, and that any sensitive or confidential information includin ...
... The CTP should undertake regular audits of mobile and/or teleworking arrangements, ensuring that all users are approved that, all mobile device and removable media assets can be accounted for, that secure remote access is possible and used, and that any sensitive or confidential information includin ...
Network Device Security Options
... Description of Ricoh Network Security Options available for MFP and Printer Products Network Port Security (ability to close unused network ports) Typically, network-enabled systems from all office equipment vendors are shipped to the customer with all the network ports “open,” making it as easy a ...
... Description of Ricoh Network Security Options available for MFP and Printer Products Network Port Security (ability to close unused network ports) Typically, network-enabled systems from all office equipment vendors are shipped to the customer with all the network ports “open,” making it as easy a ...
Delivering Value Through Non-Traditional Responsibilities
... • HTM must play a role • EXPENSIVE solutions – curb expense through management, config changes, adds/deletes ...
... • HTM must play a role • EXPENSIVE solutions – curb expense through management, config changes, adds/deletes ...
GFI EndPointSecurity
... » The product enhances the file type checking functionality by delivering data aware control of files transiting the endpoints on removable devices » Content awareness supports configuration of the search values in the form of regular expressions or dictionary files » The product ships with a set of ...
... » The product enhances the file type checking functionality by delivering data aware control of files transiting the endpoints on removable devices » Content awareness supports configuration of the search values in the form of regular expressions or dictionary files » The product ships with a set of ...
Chapter 13: Wireless Networks
... Communication facilities must be installed at low initial cost. The same information must be broadcast to many locations. ...
... Communication facilities must be installed at low initial cost. The same information must be broadcast to many locations. ...
Symbian - T-Dose
... • Renamed due to virus problems • Introduces mandatory signing – Binary break ...
... • Renamed due to virus problems • Introduces mandatory signing – Binary break ...
Introduction to Predictive Data Analytics
... What predictive data analytics wants to achieve: data to patterns (models) What machine learning can achieve: a set of historical examples (data) to models Machine learning techniques in predictive data analytics automatically learn a model of the relationship between a set of descriptive features a ...
... What predictive data analytics wants to achieve: data to patterns (models) What machine learning can achieve: a set of historical examples (data) to models Machine learning techniques in predictive data analytics automatically learn a model of the relationship between a set of descriptive features a ...
Glenbriar TakeStock! - Glenbriar Technologies Inc.
... • Provides a secure import/export facility that controls exchange between classified networks • Provides a guarded data feed that has flexible interfaces to allow integration with outside applications ...
... • Provides a secure import/export facility that controls exchange between classified networks • Provides a guarded data feed that has flexible interfaces to allow integration with outside applications ...
Ch10
... Software agents are loaded onto each network device that will be managed using SNMP. Each agent monitors network traffic and stores that information in its management information base (MIB). In addition, a computer with the SNMP management software, known as the SNMP management station, must also be ...
... Software agents are loaded onto each network device that will be managed using SNMP. Each agent monitors network traffic and stores that information in its management information base (MIB). In addition, a computer with the SNMP management software, known as the SNMP management station, must also be ...
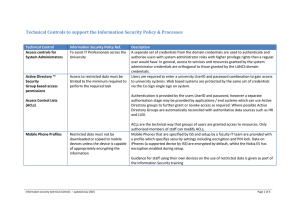
Technical Controls to support the Information
... decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With this capability users obtain the correct level of access that their computer/device is ...
... decision about what level of network access to allow them based on various criteria such as machine status (i.e. whether known to be virus infected user rights and departmental preference for access level.). With this capability users obtain the correct level of access that their computer/device is ...
The Need for Security
... Amit Yoran, former director of The Department of Homeland Security’s National Cyber Security Division “ only by improving the quality of our software and reducing the number of flaws can we hope to be successful in our security efforts” ...
... Amit Yoran, former director of The Department of Homeland Security’s National Cyber Security Division “ only by improving the quality of our software and reducing the number of flaws can we hope to be successful in our security efforts” ...
multimedia in mobile
... Internet, and develop it into a mobile multimedia service, which can handle not only voice and data but also image communications. 3.1G to 3G mobile communication technologies are mainly optimized for voice communication, using circuit switched networks. To provide high transmission mobile services ...
... Internet, and develop it into a mobile multimedia service, which can handle not only voice and data but also image communications. 3.1G to 3G mobile communication technologies are mainly optimized for voice communication, using circuit switched networks. To provide high transmission mobile services ...
AN189 Balanced modulator/demodulator applications
... Amplifying and limiting of the AM carrier is accomplished by IF gain block providing 55dB of gain or higher with limiting of 400µV. The limited carrier is then applied to the detector at the carrier ports to provide the desired switching function. The signal is then ...
... Amplifying and limiting of the AM carrier is accomplished by IF gain block providing 55dB of gain or higher with limiting of 400µV. The limited carrier is then applied to the detector at the carrier ports to provide the desired switching function. The signal is then ...
Disclaimer - euphore home page
... liability or responsibility for the accuracy, completeness, or usefulness of any information, analysis procedure, tools or process descriptions disclosed. Security We inform the users of these Web pages that for site security purposes, as well as to ensure that this service remains available to all ...
... liability or responsibility for the accuracy, completeness, or usefulness of any information, analysis procedure, tools or process descriptions disclosed. Security We inform the users of these Web pages that for site security purposes, as well as to ensure that this service remains available to all ...
19-DS-05-2016_OZGUR
... management of the international goods supply chain trade movements • SEC-19-BES-2016: Data fusion for maritime security applications • DS-05-2016: EU Cooperation and International Dialogues in Cybersecurity and Privacy Research and Innovation • DS-06-2017: Cryptography • DS-08-2017: Privacy, Data Pr ...
... management of the international goods supply chain trade movements • SEC-19-BES-2016: Data fusion for maritime security applications • DS-05-2016: EU Cooperation and International Dialogues in Cybersecurity and Privacy Research and Innovation • DS-06-2017: Cryptography • DS-08-2017: Privacy, Data Pr ...