Router/Switch Security
... Verify that access-class ACLs are used to control the sources from which sessions are going to be permitted. Verify idle session timeout ...
... Verify that access-class ACLs are used to control the sources from which sessions are going to be permitted. Verify idle session timeout ...
Circumvention Defense Network (CDN)
... Peer-to-Peer, Mixed Cascade, Onion Routing and LocalHost as well as other evasive circumvention tools designed to bypass Internet access controls. These tools are distributed in a variety of ways including through professional organizations, whose users can include younger professionals, students or ...
... Peer-to-Peer, Mixed Cascade, Onion Routing and LocalHost as well as other evasive circumvention tools designed to bypass Internet access controls. These tools are distributed in a variety of ways including through professional organizations, whose users can include younger professionals, students or ...
Do`s and Don`ts for web application developers
... Examine the data logged to determine if any sensitive information is being stored in the logs (e.g. userID, passwords). Review and remove, where possible, redundant, readable and downloadable files on a web server, such as old, backup and renamed files. Disable Autocomplete using AUTOCOMPLETE=OFF at ...
... Examine the data logged to determine if any sensitive information is being stored in the logs (e.g. userID, passwords). Review and remove, where possible, redundant, readable and downloadable files on a web server, such as old, backup and renamed files. Disable Autocomplete using AUTOCOMPLETE=OFF at ...
View
... Cryptography, Application of Cryptography, IT Act 2000 and Technology. Business : Classification of Internet Business Models, E- Business models, E- Commerce and Security, Online payment facilities, IT Act 2000 and E-Commerce, Electronic Contract: E-Agreement and Web Surfing, Terms of Service Contra ...
... Cryptography, Application of Cryptography, IT Act 2000 and Technology. Business : Classification of Internet Business Models, E- Business models, E- Commerce and Security, Online payment facilities, IT Act 2000 and E-Commerce, Electronic Contract: E-Agreement and Web Surfing, Terms of Service Contra ...
Final bits of OS - Department of Computer Science
... • Each TPM chip has a permanent key (the EK), and others are generated as needed. – The permanent key can be used to sign and prove where things come from. – Actually a private/public key pair, and the private part never leaves the dedicated hardware. ...
... • Each TPM chip has a permanent key (the EK), and others are generated as needed. – The permanent key can be used to sign and prove where things come from. – Actually a private/public key pair, and the private part never leaves the dedicated hardware. ...
Security at the level of key-value pairs in a NoSQL database
... data sets, such as NetFlow, log files, threat intelligence, e-mails, and even HR information. Sqrrl fuses this information together under a common data model, and analysts use our solution to look for patterns in the data. However, when we start working with these different data set we naturally sta ...
... data sets, such as NetFlow, log files, threat intelligence, e-mails, and even HR information. Sqrrl fuses this information together under a common data model, and analysts use our solution to look for patterns in the data. However, when we start working with these different data set we naturally sta ...
Word Template
... SandBlast Agent, extending post-infection protectionto enduser systems, to keep users safe no matter where they go. Malware contracted while roaming outside the network perimeter will be detected, and Command & Control activity blocked, With the addition of SandBlast Agent, additional information is ...
... SandBlast Agent, extending post-infection protectionto enduser systems, to keep users safe no matter where they go. Malware contracted while roaming outside the network perimeter will be detected, and Command & Control activity blocked, With the addition of SandBlast Agent, additional information is ...
Click here to view PowerPoint slides
... – Not restricted or paced by the rate at which physical objects of conventional warfare can be invented and manufactured – An accelerated “arms race” – Implementing and publishing countermeasures taxes the adversary’s main resource • Creativity with respect to new, unprecedented attacks ...
... – Not restricted or paced by the rate at which physical objects of conventional warfare can be invented and manufactured – An accelerated “arms race” – Implementing and publishing countermeasures taxes the adversary’s main resource • Creativity with respect to new, unprecedented attacks ...
WiFi Security: Keeping Your Information Private and Safe
... we go over today serve a purpose. They can be used to solve problems and for security testing. But these tools are also often used by cyber criminals for malicious purposes. ...
... we go over today serve a purpose. They can be used to solve problems and for security testing. But these tools are also often used by cyber criminals for malicious purposes. ...
Payment Card Industry Security Standards
... stores, processes, and/or transmits cardholder data. It covers technical and operational system components included in or connected to cardholder data. If your business accepts or processes payment cards, it must comply with the PCI DSS. ...
... stores, processes, and/or transmits cardholder data. It covers technical and operational system components included in or connected to cardholder data. If your business accepts or processes payment cards, it must comply with the PCI DSS. ...
Slide - ICNP
... – therefore need ability for users to provide profiles or call handling logic » who can reach a user, at which places, time and in what manner – issues of profile design, authentication, service scalability ...
... – therefore need ability for users to provide profiles or call handling logic » who can reach a user, at which places, time and in what manner – issues of profile design, authentication, service scalability ...
Wireless data transfer – GSM
... Data transfer in GSM • The "data over cellular" bearer services are part of the Phase 2 implementation of GSM • The basic data transfer technology is called CSD (Circuit Switched Data) • A GSM network’s data transfer facility allows the digital equivalent of modem transmissions - known as data stre ...
... Data transfer in GSM • The "data over cellular" bearer services are part of the Phase 2 implementation of GSM • The basic data transfer technology is called CSD (Circuit Switched Data) • A GSM network’s data transfer facility allows the digital equivalent of modem transmissions - known as data stre ...
Document
... marketing strategy. However, success of SMS marketing and high percentage of ROI is not guaranteed. Highly quality mobile number lists are critical to the success of SMS marketing campaigns. Without these, advertisers and brands face low performance and reduced ROI of their marketing campaigns. When ...
... marketing strategy. However, success of SMS marketing and high percentage of ROI is not guaranteed. Highly quality mobile number lists are critical to the success of SMS marketing campaigns. Without these, advertisers and brands face low performance and reduced ROI of their marketing campaigns. When ...
Acceptable Use Policy
... Company makes no guarantee regarding, and assumes no liability for, the security and integrity of content, data or information Users transmit, upload or download via the Products or over the Internet, or for any mistakes, defamation, slander, libel, omissions, falsehoods, obscenity, pornography, or ...
... Company makes no guarantee regarding, and assumes no liability for, the security and integrity of content, data or information Users transmit, upload or download via the Products or over the Internet, or for any mistakes, defamation, slander, libel, omissions, falsehoods, obscenity, pornography, or ...
the transitivity of trust problem in the interaction of android
... and Android programming concepts such as inner classes, GUI handling, and Android service binding. There are several directions for further research. First, we aim to support a more complete set of data sources and sinks as well as other concepts of the Android frame work such as pending intents, UR ...
... and Android programming concepts such as inner classes, GUI handling, and Android service binding. There are several directions for further research. First, we aim to support a more complete set of data sources and sinks as well as other concepts of the Android frame work such as pending intents, UR ...
LVRJ Case study
... actionable control panel for a single view of all user activity and security incidents across the Review-Journal LAN. About ConSentry Networks ConSentry Networks secures enterprise LANs with a purpose-built system that preserves data integrity, ensures network availability and supports regulatory co ...
... actionable control panel for a single view of all user activity and security incidents across the Review-Journal LAN. About ConSentry Networks ConSentry Networks secures enterprise LANs with a purpose-built system that preserves data integrity, ensures network availability and supports regulatory co ...
Data Governance Policy
... district, contractual third parties and agents of the district, and volunteers who have access to district data systems or data. This policy applies to all forms of Mountain Brook Schools’ data and information, including but not limited to: A. Speech, spoken face to face, or communicated by phone or ...
... district, contractual third parties and agents of the district, and volunteers who have access to district data systems or data. This policy applies to all forms of Mountain Brook Schools’ data and information, including but not limited to: A. Speech, spoken face to face, or communicated by phone or ...
Slide 1
... gateways and more time ensuring data was safe, he said. Dr Kaigham Gabriel, current head of the Defense Advanced Research Projects Agency, likened the current cybersecurity efforts of the US DoD to treading water in the middle of the ocean. All that did was slightly delay the day when the DoD drowne ...
... gateways and more time ensuring data was safe, he said. Dr Kaigham Gabriel, current head of the Defense Advanced Research Projects Agency, likened the current cybersecurity efforts of the US DoD to treading water in the middle of the ocean. All that did was slightly delay the day when the DoD drowne ...
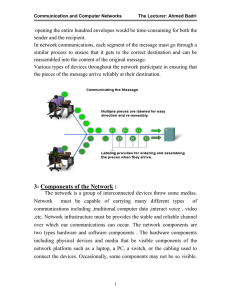
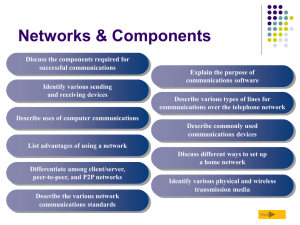
1-Introduction :
... The management of data as it flows through the network is also a role of the intermediary devices. These devices use the destination host address, in conjunction with information about the network interconnections, to determine the path that messages should take through the network. Processes runnin ...
... The management of data as it flows through the network is also a role of the intermediary devices. These devices use the destination host address, in conjunction with information about the network interconnections, to determine the path that messages should take through the network. Processes runnin ...
ACCEPTABLE USE POLICY Customer is expected to
... Customer agrees and acknowledges that the violation of this AUP by Customer’s subscribers, end-users or customers shall be deemed to be a violation by Customer of the AUP. Customer is solely responsible for the content of any postings, data, or transmissions using the Services ("Content"), or any ot ...
... Customer agrees and acknowledges that the violation of this AUP by Customer’s subscribers, end-users or customers shall be deemed to be a violation by Customer of the AUP. Customer is solely responsible for the content of any postings, data, or transmissions using the Services ("Content"), or any ot ...
OWASP Top 10 Privacy Risks
... • Are regular penetration tests performed focusing on privacy? • Are developers trained regarding web application security? • Are secure coding guidelines applied? • Is any of the used software out of date (server, DB, libraries)? How to improve? • Apply procedures like the Security Development Life ...
... • Are regular penetration tests performed focusing on privacy? • Are developers trained regarding web application security? • Are secure coding guidelines applied? • Is any of the used software out of date (server, DB, libraries)? How to improve? • Apply procedures like the Security Development Life ...
Slide 1
... wireless access points, routers, and hubs ISDN and DSL modems send and receive data from ISDN and DSL lines ...
... wireless access points, routers, and hubs ISDN and DSL modems send and receive data from ISDN and DSL lines ...
What is Beta Testing? - KV Institute of Management and Information
... Organizations standards, processes, systems, and plans are adequate to enable the organization ...
... Organizations standards, processes, systems, and plans are adequate to enable the organization ...
Architecting High-Security Systems for Multilateral
... competitors. Hence, producers of document viewers, web browsers, operating systems and other complex parts of software often do not have appropriate resources available to build sufficiently secure software for critical environments. Regardless of the development process, larger and more complex sof ...
... competitors. Hence, producers of document viewers, web browsers, operating systems and other complex parts of software often do not have appropriate resources available to build sufficiently secure software for critical environments. Regardless of the development process, larger and more complex sof ...