Chapter 8 - William Stallings, Data and Computer
... stuffed pulses inserted at fixed locations in frame and removed at demultiplexer ...
... stuffed pulses inserted at fixed locations in frame and removed at demultiplexer ...
Intrusion Prevention System (IPS)
... If ETS or JDL alerts a TLC to a security problem, please address the issue promptly. Notify ETS when complete. ...
... If ETS or JDL alerts a TLC to a security problem, please address the issue promptly. Notify ETS when complete. ...
Chapter 1 THE INFORMATION AGE IN WHICH YOU LIVE Changing
... be, to have control over your own personal possessions, and not to be observed without your consent o Dimensions of privacy – Psychological: to have a sense of control – Legal: to be able to protect yourself ...
... be, to have control over your own personal possessions, and not to be observed without your consent o Dimensions of privacy – Psychological: to have a sense of control – Legal: to be able to protect yourself ...
Certifications authenticate Blancco´s high standards
... the high standards the MoD requires, special security specifications were set based on CESG’s standards. Blancco is currently the only DIPCOG approved product for selective data erasure and is highly recommended for use within the UK’s MoD. ...
... the high standards the MoD requires, special security specifications were set based on CESG’s standards. Blancco is currently the only DIPCOG approved product for selective data erasure and is highly recommended for use within the UK’s MoD. ...
Web Application Security
... in the form of a script, to a different end user. Can occur to web applications that use input from a user (without validation) in the output the application generates (e.g.: Forums, Blogs) Other users may not aware of the risk because the script comes from a trusted website. Script can access ...
... in the form of a script, to a different end user. Can occur to web applications that use input from a user (without validation) in the output the application generates (e.g.: Forums, Blogs) Other users may not aware of the risk because the script comes from a trusted website. Script can access ...
User Behavior based Anomaly Detection for Cyber
... All three methods can detect anomaly in the network but they have low detection rate and high false alarm rate. They cannot detect new anomaly. Behavior based anomaly detection helps solve this problem. Network Behavior Anomaly Detection (NBAD) is a way to enhance the security of proprietary network ...
... All three methods can detect anomaly in the network but they have low detection rate and high false alarm rate. They cannot detect new anomaly. Behavior based anomaly detection helps solve this problem. Network Behavior Anomaly Detection (NBAD) is a way to enhance the security of proprietary network ...
SMS-C 422 - ADYNA | smart technology
... The SMS-C-422 is made for applications where it is requirde to monitor analog or digital conditions or to switch devices remotely and where an own network and/or an internet connection is not available. It is especially designed for monitoring-tasks in the industry. With the SMS-C-422 it is possible ...
... The SMS-C-422 is made for applications where it is requirde to monitor analog or digital conditions or to switch devices remotely and where an own network and/or an internet connection is not available. It is especially designed for monitoring-tasks in the industry. With the SMS-C-422 it is possible ...
Vertical optimization of data transmission for mobile wireless terminals
... Optimization Strategies For The Mobile Device Interference Between TCP And The Wireless Link Simulation Setup: TCP Running Over The IEEE 802.11 MAC Optimizing The Uplink Retransmission On The TCP And MAC Layers ...
... Optimization Strategies For The Mobile Device Interference Between TCP And The Wireless Link Simulation Setup: TCP Running Over The IEEE 802.11 MAC Optimizing The Uplink Retransmission On The TCP And MAC Layers ...
DPI as a means of access segregation in a corporate
... IBM XGS5100 as NGFW device; Active Directory login event – pairing user with IP address; MacOS/*nix goes web-auth/kerberos way; No auth – no party; Network access based on “memberOf”: ...
... IBM XGS5100 as NGFW device; Active Directory login event – pairing user with IP address; MacOS/*nix goes web-auth/kerberos way; No auth – no party; Network access based on “memberOf”: ...
Chapter07
... Antivirus software and antispyware software share many similarities. First, antispyware software must be regularly updated defend against the most recent spyware attacks. Second, antispyware can be set to provide both continuous realtime monitoring as well as perform a complete scan of the entire c ...
... Antivirus software and antispyware software share many similarities. First, antispyware software must be regularly updated defend against the most recent spyware attacks. Second, antispyware can be set to provide both continuous realtime monitoring as well as perform a complete scan of the entire c ...
2003 Format - Google Project Hosting
... i.e. The desktop client is automatically updating upon launch, In cases of maintenance or version upgrade one's only need to update the server and the clients will be updated at launch without any manual intervention. (With exception to changes made at the mobile client code itself). ...
... i.e. The desktop client is automatically updating upon launch, In cases of maintenance or version upgrade one's only need to update the server and the clients will be updated at launch without any manual intervention. (With exception to changes made at the mobile client code itself). ...
Information Systems and Networks
... traveling over a network. When used legitimately, sniffers help identify potential network trouble spots or criminal activity on networks, but when used for criminal purposes, they can be damaging and very difficult to detect ...
... traveling over a network. When used legitimately, sniffers help identify potential network trouble spots or criminal activity on networks, but when used for criminal purposes, they can be damaging and very difficult to detect ...
IOSR Journal of Computer Engineering (IOSR-JCE) e-ISSN: 2278-0661,p-ISSN: 2278-8727 PP 10-14 www.iosrjournals.org
... Hence, there is need of capacity improvements in wireless communications. The term 4G is used broadly to include several types of broadband wireless access communication systems, not only cellular telephone systems. One of the terms used to describe 4G is MAGIC—Mobile multimedia, anytime anywhere, G ...
... Hence, there is need of capacity improvements in wireless communications. The term 4G is used broadly to include several types of broadband wireless access communication systems, not only cellular telephone systems. One of the terms used to describe 4G is MAGIC—Mobile multimedia, anytime anywhere, G ...
Ni1-103 Unauthorized Cell Phone in Correctional
... This is a reminder to all employees that possession of an unauthorized cell phone, or any other unauthorized communication device which allows a person to receive and/or send voice/text messages, is strictly prohibited inside any secure area of a correctional facility. Unauthorized cell phones in th ...
... This is a reminder to all employees that possession of an unauthorized cell phone, or any other unauthorized communication device which allows a person to receive and/or send voice/text messages, is strictly prohibited inside any secure area of a correctional facility. Unauthorized cell phones in th ...
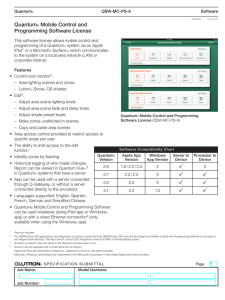
Quantum Mobile Control and Programming Software License
... Q-Admm is used to view the report in the Quantum versions prior to 3.2. Device must be equipped with a wired ethernet connection. Apple and iPad are trademarks of Apple Inc., registered in the U.S. and other countries. Microsoft, Windows, and Surface are trademarks of the Microsoft Corporation in th ...
... Q-Admm is used to view the report in the Quantum versions prior to 3.2. Device must be equipped with a wired ethernet connection. Apple and iPad are trademarks of Apple Inc., registered in the U.S. and other countries. Microsoft, Windows, and Surface are trademarks of the Microsoft Corporation in th ...
Security Agents for Network Traffic Analysis
... runtime. When an agent needs to execute on the runtime, the runtime creates a new thread which executes the agent’s program. ...
... runtime. When an agent needs to execute on the runtime, the runtime creates a new thread which executes the agent’s program. ...
The Advanced Penetration Testing Boot Camp
... Data leakage filled the headlines in 2008 as corporations and government proved themselves to be lax in protecting their confidential data. • Organizations of all sizes are finding that today’s mobile and collaborative workforce needs access to information inside and outside the office, along with t ...
... Data leakage filled the headlines in 2008 as corporations and government proved themselves to be lax in protecting their confidential data. • Organizations of all sizes are finding that today’s mobile and collaborative workforce needs access to information inside and outside the office, along with t ...
MetaOS Concept • MetaOS developed by Ambient Computing to
... • Operators with different responsibilities can customize views for monitoring, investigation, management • Allows rapid deployment of new sensor processing applications ...
... • Operators with different responsibilities can customize views for monitoring, investigation, management • Allows rapid deployment of new sensor processing applications ...
Data Confidentiality
... consist of data about each stage of any transaction, logs are maintained automatically by the system allow the network manager to examine patterns of use audit logs track: – who did what, – at which workstation, – when it occurred. ...
... consist of data about each stage of any transaction, logs are maintained automatically by the system allow the network manager to examine patterns of use audit logs track: – who did what, – at which workstation, – when it occurred. ...
Section for introduction % \section{Introduction} Over the last several
... modifying the startup configuration file to persist execution across reboots of the Android device. At this level of execution, it would be possible for such a process with root access to attain and transmit sensitive personal information including current GPS coordinates, call logs, the phone book, ...
... modifying the startup configuration file to persist execution across reboots of the Android device. At this level of execution, it would be possible for such a process with root access to attain and transmit sensitive personal information including current GPS coordinates, call logs, the phone book, ...
Distributed Data Dissemination Server
... Push-Pull server model allowing data access from heterogeneous clients Supports Historic & Real-Time Queries Attribute based data discovery Multi-Server capability Client-side libraries available in C, C++, and Java ...
... Push-Pull server model allowing data access from heterogeneous clients Supports Historic & Real-Time Queries Attribute based data discovery Multi-Server capability Client-side libraries available in C, C++, and Java ...
A safe mobile agent system for distributed intrusion detection
... runtime. When an agent needs to execute on the runtime, the runtime creates a new thread which executes the agent’s program. ...
... runtime. When an agent needs to execute on the runtime, the runtime creates a new thread which executes the agent’s program. ...
Chapter 4
... 15. A wireless access point that is secretly installed in an office without the employer’s permission is known as a(n) _____. rogue access point 16. Explain how a disassociation frame DoS attack functions. An attacker can pretend to be an access point and send a forged disassociation frame to a wire ...
... 15. A wireless access point that is secretly installed in an office without the employer’s permission is known as a(n) _____. rogue access point 16. Explain how a disassociation frame DoS attack functions. An attacker can pretend to be an access point and send a forged disassociation frame to a wire ...
ICT & Prog
... You are responsible for what is covered in class – even if you don’t show up Deficiency in attendance may lead to termination or relegation You are encouraged to help each other with your homework assignments – but you must turn in your own work If you are found to be cheating, you will fail at leas ...
... You are responsible for what is covered in class – even if you don’t show up Deficiency in attendance may lead to termination or relegation You are encouraged to help each other with your homework assignments – but you must turn in your own work If you are found to be cheating, you will fail at leas ...
If you are requesting an upgrade for existing equipment (hardware
... Office Location Phone Number Full Time or Part Time Administrator, Faculty, Staff, Student, Other 2.2. If this is a piece of equipment to be upgraded please list: Model of current equipment Current LCC Tag # What task do you perform that requires the upgrade? 2.3. What new equipment are you requesti ...
... Office Location Phone Number Full Time or Part Time Administrator, Faculty, Staff, Student, Other 2.2. If this is a piece of equipment to be upgraded please list: Model of current equipment Current LCC Tag # What task do you perform that requires the upgrade? 2.3. What new equipment are you requesti ...