IEEE CONFERENCE ON COMMUNICATION TECHNOLOGIES
... planning to hold an International Conference on Communications Technologies (ComTech-2017), at its campus, in collaboration with IEEE and related industrial partners in April 2017. Conference Chair Dr.Abdul Rauf Conference Co-Chair: Dr.Asif Masood DEADLINES ...
... planning to hold an International Conference on Communications Technologies (ComTech-2017), at its campus, in collaboration with IEEE and related industrial partners in April 2017. Conference Chair Dr.Abdul Rauf Conference Co-Chair: Dr.Asif Masood DEADLINES ...
DataXtend RE (DXRE) enables enterprises to distribute data
... distributed databases, whether your enterprise needs simple data replication or a complete synchronisation solution. With DXRE, users don’t have to be connected to a network to access data. Remote offices with limited or variable bandwidth and mobile users with limited periods of connectivity can bo ...
... distributed databases, whether your enterprise needs simple data replication or a complete synchronisation solution. With DXRE, users don’t have to be connected to a network to access data. Remote offices with limited or variable bandwidth and mobile users with limited periods of connectivity can bo ...
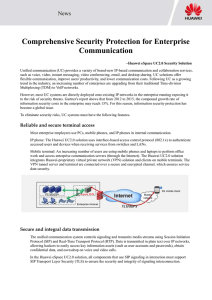
Comprehensive Security Protection for
... work and access enterprise communication servers (through the Internet). The Huawei UC2.0 solution integrates Huawei-proprietary virtual private network (VPN) solution and clients on mobile terminals. The VPN tunnel server and terminal are connected over a secure and encrypted channel, which ensures ...
... work and access enterprise communication servers (through the Internet). The Huawei UC2.0 solution integrates Huawei-proprietary virtual private network (VPN) solution and clients on mobile terminals. The VPN tunnel server and terminal are connected over a secure and encrypted channel, which ensures ...
Chapter 8
... for batch transmission to host computer CONTROLLER: Computer controls interface between CPU and peripheral devices MULTIPLEXER: Allows channel to carry multiple sources simultaneously ...
... for batch transmission to host computer CONTROLLER: Computer controls interface between CPU and peripheral devices MULTIPLEXER: Allows channel to carry multiple sources simultaneously ...
Dashlane -- Fact Sheet Express Login and Security Dashboard: As a
... information, enabling users to transact seamlessly and quickly across the web. Its patented click-to-pay technology – no typing required! – allows consumers to make buying as easy as possible, throughout the web. Dashlane’s check-out product does not require a custom build or partnership with any we ...
... information, enabling users to transact seamlessly and quickly across the web. Its patented click-to-pay technology – no typing required! – allows consumers to make buying as easy as possible, throughout the web. Dashlane’s check-out product does not require a custom build or partnership with any we ...
Endpoint Security Device Control (formerly Sanctuary)
... To enhance productivity, organizations need to provide employees and partners access to data. With more employees working remotely, access is required from outside the network. But the potential impact of data loss, be it accidental or malicious, is a very real concern. And today, removable media / ...
... To enhance productivity, organizations need to provide employees and partners access to data. With more employees working remotely, access is required from outside the network. But the potential impact of data loss, be it accidental or malicious, is a very real concern. And today, removable media / ...
Document
... Creating an exception process (both opt-in and opt-out) with appropriate vetting, risk assessment, and functional and technical management approval. Access to systems from off-site locations, especially during emergencies. ...
... Creating an exception process (both opt-in and opt-out) with appropriate vetting, risk assessment, and functional and technical management approval. Access to systems from off-site locations, especially during emergencies. ...
Cisco on Cisco Chevron Presentation
... an end-to-end secure borderless architecture for on-boarding mobile devices around the globe • Shared our connected workplace strategy enabling ...
... an end-to-end secure borderless architecture for on-boarding mobile devices around the globe • Shared our connected workplace strategy enabling ...
1 Supporting information for Ultrafast dynamics of carrier mobility in
... the exciton has to undergo dissociation (charge transfer) before both carriers can drift separately. 2) Charge transfer states In principle the charge carrier contribution ∆ECC(t) includes coulombically bound charge pairs (CT states), if they are present. The small number of charge pairs created by ...
... the exciton has to undergo dissociation (charge transfer) before both carriers can drift separately. 2) Charge transfer states In principle the charge carrier contribution ∆ECC(t) includes coulombically bound charge pairs (CT states), if they are present. The small number of charge pairs created by ...
Chapter 2: Introduction to Microprocessor
... It is composed of collection of files that are linked in such a way that information from one of the files may be combined with information from other files so that a user may receive the exact required information. ...
... It is composed of collection of files that are linked in such a way that information from one of the files may be combined with information from other files so that a user may receive the exact required information. ...
Chapter 1 - William Stallings, Data and Computer
... # For six devices connected in mesh, how many cables are needed? How many ports are needed for each device? # What is the consequence if a connection fails for five devices arranged in: a) Mesh b) Star (excluding hub) c) Bus d) Ring ...
... # For six devices connected in mesh, how many cables are needed? How many ports are needed for each device? # What is the consequence if a connection fails for five devices arranged in: a) Mesh b) Star (excluding hub) c) Bus d) Ring ...
Security strategy
... information technology assets. This will cover the physical configuration, software, and information handling and user practices. All organisations suffer from breaches of security. These can range from innocent attempts to access restricted resources to deliberate and prolonged attempts on computer ...
... information technology assets. This will cover the physical configuration, software, and information handling and user practices. All organisations suffer from breaches of security. These can range from innocent attempts to access restricted resources to deliberate and prolonged attempts on computer ...
Chapter 1 - William Stallings, Data and Computer
... between source and destination used for terminal to computer and computer to computer communications ...
... between source and destination used for terminal to computer and computer to computer communications ...
"rooting"?
... Android: Rooting is the process of gaining administrative or privileged access for the Android OS. As the Android OS is based on the Linux Kernel, rooting a device is analogous to gaining access to administrative, root user-equivalent, permissions on Linux. Unlike iOS, rooting is (usually) not requi ...
... Android: Rooting is the process of gaining administrative or privileged access for the Android OS. As the Android OS is based on the Linux Kernel, rooting a device is analogous to gaining access to administrative, root user-equivalent, permissions on Linux. Unlike iOS, rooting is (usually) not requi ...
Cisco Discovery 1 Module 08 Quiz Picture Descriptions
... Data loss Identity theft Information theft Data manipulation Disruption of service. ...
... Data loss Identity theft Information theft Data manipulation Disruption of service. ...
Seminar Announcement - CS/NVC Home
... queries are useful in many application domains, including Network Management and Intrusion Detection, Web Monitoring, Sensor Network applications, and various financial and business applications. In this talk, we will first briefly discuss some of these applications and general technical challenges ...
... queries are useful in many application domains, including Network Management and Intrusion Detection, Web Monitoring, Sensor Network applications, and various financial and business applications. In this talk, we will first briefly discuss some of these applications and general technical challenges ...
Mobile Device Policy - University of Canterbury
... 6. Password/pin security must be enabled on the mobile to secure the device and data stored on the device. This will be set by the telecommunications team within the Operations and Infrastructure group. 7. Devices with wireless capability must be set up to use the University wireless network when wi ...
... 6. Password/pin security must be enabled on the mobile to secure the device and data stored on the device. This will be set by the telecommunications team within the Operations and Infrastructure group. 7. Devices with wireless capability must be set up to use the University wireless network when wi ...
E-Surveillance and User Privacy
... visas and other travel and entry documents that use biometric identifiers" shall be issued to aliens by October 26, 2004. The Immigration and Naturalization Service (INS) and the State Department currently are evaluating biometrics for use in U.S. border control pursuant to EBSVERA. ...
... visas and other travel and entry documents that use biometric identifiers" shall be issued to aliens by October 26, 2004. The Immigration and Naturalization Service (INS) and the State Department currently are evaluating biometrics for use in U.S. border control pursuant to EBSVERA. ...
Word
... - What is ________________________ and where it is stored - Virtual memory - OS will send message when RAM is full Provides the interface for storage devices and _____________________________________ on those devices - in charge of formatting disks - creates sectors and clusters - creates F.A.T. or ...
... - What is ________________________ and where it is stored - Virtual memory - OS will send message when RAM is full Provides the interface for storage devices and _____________________________________ on those devices - in charge of formatting disks - creates sectors and clusters - creates F.A.T. or ...
ICBA Encourages Consumers to Protect their Data during Cyber
... Remain cautious of someone who isn’t who they say they are or if the name and area don’t match what appears on caller ID. This is often how spoofing occurs. ...
... Remain cautious of someone who isn’t who they say they are or if the name and area don’t match what appears on caller ID. This is often how spoofing occurs. ...
Insert Picture Here
... All Berkeley DB Products… • …are libraries • Run in the same address space as the application • Small footprint – on the order of half a megabyte • No client/server abstraction ...
... All Berkeley DB Products… • …are libraries • Run in the same address space as the application • Small footprint – on the order of half a megabyte • No client/server abstraction ...