quick start guide for eldes esim110 users
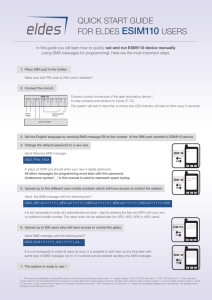
... FOR ELDES ESIM110 USERS In this guide you will learn how to quickly set and run ESIM110 device manually (using SMS messages for programming). Here are the most important steps: ...
... FOR ELDES ESIM110 USERS In this guide you will learn how to quickly set and run ESIM110 device manually (using SMS messages for programming). Here are the most important steps: ...
security_6
... Other Security and Privacy Concerns in EC Some of the methods used in market research and for tracking customers: ...
... Other Security and Privacy Concerns in EC Some of the methods used in market research and for tracking customers: ...
Chapter 14 - William Stallings, Data and Computer Communications
... cellular telephone networks Analog traffic channels Designed to be an extension of the public switched telephone networks The most widely deployed system was the Advanced Mobile Phone Service (AMPS) ...
... cellular telephone networks Analog traffic channels Designed to be an extension of the public switched telephone networks The most widely deployed system was the Advanced Mobile Phone Service (AMPS) ...
How mobile communications work
... • Mobile security or mobile phone security has become increasingly important in mobile computing. It is of particular concern as it relates to the security of personal information now stored on smartphones. • All smartphones, as computers, are preferred targets of attacks. These attacks exploit weak ...
... • Mobile security or mobile phone security has become increasingly important in mobile computing. It is of particular concern as it relates to the security of personal information now stored on smartphones. • All smartphones, as computers, are preferred targets of attacks. These attacks exploit weak ...
Real Systems - e
... VizKey™ - visual database and analysis environment. The Suite includes database, visualization, analysis methods, visual engines and external data connectivity. Ideal tool for law enforcement institutions that need to analyzing large quantities of complex data in order to investigate crime and detec ...
... VizKey™ - visual database and analysis environment. The Suite includes database, visualization, analysis methods, visual engines and external data connectivity. Ideal tool for law enforcement institutions that need to analyzing large quantities of complex data in order to investigate crime and detec ...
SEMİ CONDUCTOR DEVİCE PHYSİCS
... • The flux equation • The Einstein relation • Total current density • Carrier recombination and diffusion length ...
... • The flux equation • The Einstein relation • Total current density • Carrier recombination and diffusion length ...
Now - ThreatMetrix
... a mobile banking app which facilitates P2P money lending, investment and mobile wallet services. Mobile banking transactions continue to grow globally as consumers migrate away from desktop-only banking, to the convenience, immediacy and portability of mobile. Cybercriminals, however are following s ...
... a mobile banking app which facilitates P2P money lending, investment and mobile wallet services. Mobile banking transactions continue to grow globally as consumers migrate away from desktop-only banking, to the convenience, immediacy and portability of mobile. Cybercriminals, however are following s ...
Call for Papers: HotPlanet 2015 6th International Workshop on Hot
... inherently led to a number of security, privacy and ethical issues as well as new systems, networking, and application challenges. This 6th HotPlanet workshop will bring together networking, wireless, mobile computing and systems research to understand the challenges ahead and advance the dialogue o ...
... inherently led to a number of security, privacy and ethical issues as well as new systems, networking, and application challenges. This 6th HotPlanet workshop will bring together networking, wireless, mobile computing and systems research to understand the challenges ahead and advance the dialogue o ...
Dan A CSC 345 Term Paper
... Today’s modern mobile devices boast a large array of features, including wireless internet connectivity, GPS navigation, video and audio recording, and music playing. Along with the bevy of features, there are also numerous ways to exploit these mobile devices. Below, some of these exploits will be ...
... Today’s modern mobile devices boast a large array of features, including wireless internet connectivity, GPS navigation, video and audio recording, and music playing. Along with the bevy of features, there are also numerous ways to exploit these mobile devices. Below, some of these exploits will be ...
Web tracking resolution
... while using various services of the information society on the Internet, are increasingly combined, correlated and analysed by different actors for various purposes ranging from charitable to commercial purposes of the different actors offering such services or ...
... while using various services of the information society on the Internet, are increasingly combined, correlated and analysed by different actors for various purposes ranging from charitable to commercial purposes of the different actors offering such services or ...
Open ended challenge rationale
... Software intended to infiltrate and damage or disable computers. Shortened form of malicious software. ...
... Software intended to infiltrate and damage or disable computers. Shortened form of malicious software. ...
Artificial Intelligence Engineer
... 3+ years hands on experience in AI, ML, DL, and DM 5+ years experience in enterprise-grade software engineering 2+ years experience working with network-related data and cyber security products ...
... 3+ years hands on experience in AI, ML, DL, and DM 5+ years experience in enterprise-grade software engineering 2+ years experience working with network-related data and cyber security products ...