What is network management?
... In early days of the ARPANET, they used ping to detect the problem. When ARPANET turned into WWW, better tools to network management are needed. SNMP provided a systematic way of monitoring and managing a computer network. Three versions in SNMP SNMPv1 : The initial implementation of the SNMP protoc ...
... In early days of the ARPANET, they used ping to detect the problem. When ARPANET turned into WWW, better tools to network management are needed. SNMP provided a systematic way of monitoring and managing a computer network. Three versions in SNMP SNMPv1 : The initial implementation of the SNMP protoc ...
Distilling Data in a SIM: A Strategy for the Analysis
... data. It can include data from intrusion detection or protection systems (IDS/IPS), firewalls, servers, web servers, and other kinds of devices, including routers and switches. The data can comprise millions of events. This dataset must be reduced so that analysts can make sense of it and find the e ...
... data. It can include data from intrusion detection or protection systems (IDS/IPS), firewalls, servers, web servers, and other kinds of devices, including routers and switches. The data can comprise millions of events. This dataset must be reduced so that analysts can make sense of it and find the e ...
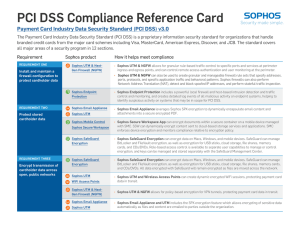
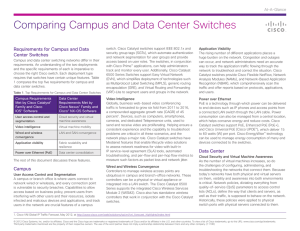
PCI DSS Compliance Reference Card
... ÌÌ Sophos SafeGuard Encryption can encrypt data on Macs, Windows, and mobile devices. SafeGuard can manage BitLocker and FileVault encryption, as well as encryption for USB sticks, cloud storage, file shares, memory cards, and CDs/DVDs. Role-based access control is available to separate user capabil ...
... ÌÌ Sophos SafeGuard Encryption can encrypt data on Macs, Windows, and mobile devices. SafeGuard can manage BitLocker and FileVault encryption, as well as encryption for USB sticks, cloud storage, file shares, memory cards, and CDs/DVDs. Role-based access control is available to separate user capabil ...
Network Reference Model for cdma2000 Spread Spectrum
... • the ability to duplicate and deliver information on the intercept subject to one or more Collection Functions as authorized for each law enforcement agency. • the ability to provide security to restrict access. ...
... • the ability to duplicate and deliver information on the intercept subject to one or more Collection Functions as authorized for each law enforcement agency. • the ability to provide security to restrict access. ...
SNMP Vulnerabilities - Department of Computer Science
... Apply a patch from your vendor. Disable any SNMP service that is not required; although CERT notes some products appear to be affected even if SNMP is disabled. Make use of firewall devices to block unauthorized SNMP access from the network perimeter. Use ingress filtering by blocking access to SNMP ...
... Apply a patch from your vendor. Disable any SNMP service that is not required; although CERT notes some products appear to be affected even if SNMP is disabled. Make use of firewall devices to block unauthorized SNMP access from the network perimeter. Use ingress filtering by blocking access to SNMP ...
M3AAWG Anti-Abuse Best Common Practices for Hosting and Cloud
... Train customer-facing staff in security awareness. Customer-facing teams such as support, sales and marketing do not face the majority of daily challenges that are the norm for the abuse or security teams. Training provides these teams with knowledge of when to tell a customer or prospect that thei ...
... Train customer-facing staff in security awareness. Customer-facing teams such as support, sales and marketing do not face the majority of daily challenges that are the norm for the abuse or security teams. Training provides these teams with knowledge of when to tell a customer or prospect that thei ...
Document
... Inconsistent log content (like recording only pieces of information) Inconsistent timestamps (especially when logging across multiple hosts) Inconsistent formats ( XML, plain text, binary) ...
... Inconsistent log content (like recording only pieces of information) Inconsistent timestamps (especially when logging across multiple hosts) Inconsistent formats ( XML, plain text, binary) ...
Tenable Malware Detection
... known botnet, and by comparing DNS entries to malicious URLs and IP addresses. Tenable SCCV is able to detect botnet hosts and activity on its own, independent of any AV or IDS product. Combination of Scan, Sniff and Log Correlation Using a multi-vector approach to detecting malware makes Tenable SC ...
... known botnet, and by comparing DNS entries to malicious URLs and IP addresses. Tenable SCCV is able to detect botnet hosts and activity on its own, independent of any AV or IDS product. Combination of Scan, Sniff and Log Correlation Using a multi-vector approach to detecting malware makes Tenable SC ...
Mobile Agent Security - Indian Institute of Technology
... An agent system is a platform that can create, interpret, execute, transfer and terminate agents. Like an agent, an agent system is associated with an authority that identifies the person or organization for whom the agent system acts. For example, an agent system with authority Bob implements Bob's ...
... An agent system is a platform that can create, interpret, execute, transfer and terminate agents. Like an agent, an agent system is associated with an authority that identifies the person or organization for whom the agent system acts. For example, an agent system with authority Bob implements Bob's ...
WiMAX Protocol - London South Bank University
... Most WiMax backers, including Clearwire in the United States (which has already built WiMax networks in many US cities), have signalled their intent to move across to LTE. It was never cost effective for WiMax networks to compete effectively against fixed-line broadband networks. What happened w ...
... Most WiMax backers, including Clearwire in the United States (which has already built WiMax networks in many US cities), have signalled their intent to move across to LTE. It was never cost effective for WiMax networks to compete effectively against fixed-line broadband networks. What happened w ...
Data Exfiltration and DNS
... Even some commercial services have popped up offering VPN service over DNS, thus allowing you to bypass many Wi-Fi security controls. Most of these tools have specific signatures that can be used for detection and mitigation. ...
... Even some commercial services have popped up offering VPN service over DNS, thus allowing you to bypass many Wi-Fi security controls. Most of these tools have specific signatures that can be used for detection and mitigation. ...
white paper
... Intrusion Prevention techniques. ZIMPERIUM provides advanced technology which operates in user-mode allowing instant BYOD deployment by using a new innovative technique called ‘non-intrusive packet monitoring’. This technique is optimized for mobile devices resulting in minimal battery, memory and C ...
... Intrusion Prevention techniques. ZIMPERIUM provides advanced technology which operates in user-mode allowing instant BYOD deployment by using a new innovative technique called ‘non-intrusive packet monitoring’. This technique is optimized for mobile devices resulting in minimal battery, memory and C ...
TCA Report Template - Transport Certification Australia
... In-Vehicle Unit (IVU) presented by transport operators through the Entry Options initiative TCA acknowledges that each transport operator is different. Therefore, this document should be treated as a general overview of the information required.Transport operators may also be requested by TCA to pro ...
... In-Vehicle Unit (IVU) presented by transport operators through the Entry Options initiative TCA acknowledges that each transport operator is different. Therefore, this document should be treated as a general overview of the information required.Transport operators may also be requested by TCA to pro ...
Foundation Fieldbus
... connection of multiple field instruments and processes and operator stations (HMI: Human-Machine Interfaces). They carry out control functions and enable monitoring by means of supervision software. Figure 1-1 shows how these three layers (Field, Fieldbus, and Supervisory System) interrelate. The FO ...
... connection of multiple field instruments and processes and operator stations (HMI: Human-Machine Interfaces). They carry out control functions and enable monitoring by means of supervision software. Figure 1-1 shows how these three layers (Field, Fieldbus, and Supervisory System) interrelate. The FO ...
Paper
... troubleshooting. The Cisco Nexus 1000V Series Switches provide the solution to these problems by providing visibility into the virtual machine environment while extending the features and functions of the Cisco Nexus portfolio. The Cisco Virtual Security Gateway (VSG) and Cisco Adaptive Security App ...
... troubleshooting. The Cisco Nexus 1000V Series Switches provide the solution to these problems by providing visibility into the virtual machine environment while extending the features and functions of the Cisco Nexus portfolio. The Cisco Virtual Security Gateway (VSG) and Cisco Adaptive Security App ...
SCTE 40 2011
... public interest by providing specifications, test methods and procedures that promote uniformity of product, interchangeability and ultimately the long term reliability of broadband communications facilities. These documents shall not in any way preclude any member or nonmember of SCTE from manufact ...
... public interest by providing specifications, test methods and procedures that promote uniformity of product, interchangeability and ultimately the long term reliability of broadband communications facilities. These documents shall not in any way preclude any member or nonmember of SCTE from manufact ...
VPN: Virtual Private Network
... the most widely supported VPN method among Windows users and it was created by Microsoft in association with other technology ...
... the most widely supported VPN method among Windows users and it was created by Microsoft in association with other technology ...
Forensic Analysis Reveals Data Leaks in HIPAA
... Personally Identifiable Information (“PII”) is information that could distinguish an individual. Protected Health Information (“PHI”) refers to individually identifiable health information such as a current medical condition that identifies an individual or which provides a reasonable basis to ident ...
... Personally Identifiable Information (“PII”) is information that could distinguish an individual. Protected Health Information (“PHI”) refers to individually identifiable health information such as a current medical condition that identifies an individual or which provides a reasonable basis to ident ...
PPT Version
... • In the latter case any group (con-federation) of carriers may decide on any root within a private or public DNS implementation. • Infrastructure ENUM is used (in most cases) for routing calls directly from origination networks to destination networks. • Therefore it is considered (at least for a g ...
... • In the latter case any group (con-federation) of carriers may decide on any root within a private or public DNS implementation. • Infrastructure ENUM is used (in most cases) for routing calls directly from origination networks to destination networks. • Therefore it is considered (at least for a g ...
How to Detect Zero-Day Malware And Limit Its Impact
... Anomalies can take many forms. They can be as simple as users logging in from an unusual geographic location, the same credit card being used in three widespread locations within a short period or an employee ID logging in to a corporate system at an unusual time. Security vendors are using big data ...
... Anomalies can take many forms. They can be as simple as users logging in from an unusual geographic location, the same credit card being used in three widespread locations within a short period or an employee ID logging in to a corporate system at an unusual time. Security vendors are using big data ...
POLICY Number: 0-501 Title: Information Technology Resources
... Each authorized user of a system shall have a unique login ID. Any ID which is used to access a system, and which does not provide a unique user identification, shall have access only to specific, restricted system resources. Access to services and/or resources will be suspended, and the appropriate ...
... Each authorized user of a system shall have a unique login ID. Any ID which is used to access a system, and which does not provide a unique user identification, shall have access only to specific, restricted system resources. Access to services and/or resources will be suspended, and the appropriate ...
Digi One TS/ PortServer TS 2/4 Setup Card
... This equipment has been tested and found to comply with the limits for Class A digital devices pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential environment. This equipment generates, uses, and can radiate r ...
... This equipment has been tested and found to comply with the limits for Class A digital devices pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential environment. This equipment generates, uses, and can radiate r ...