Effective Log Management - National Cyber Security Centre
... server. Depending on the objectives of the attacker, SQLi attacks can be used to display the contents of protected database tables, add new user accounts to enable direct remote access, provide the ability to upload and execute attack tools and can even provide full remote desktop access to the serv ...
... server. Depending on the objectives of the attacker, SQLi attacks can be used to display the contents of protected database tables, add new user accounts to enable direct remote access, provide the ability to upload and execute attack tools and can even provide full remote desktop access to the serv ...
Slides
... Q: How does ASN.1 work? A: ASN.1 is an encoding standard. It defines how you encode data for different types: how to send an integer, a string, a bit string, an object-id, a real number, a null, etc. It also tries to minimize the space it takes to encode things. As a result, it is barf-making. A tru ...
... Q: How does ASN.1 work? A: ASN.1 is an encoding standard. It defines how you encode data for different types: how to send an integer, a string, a bit string, an object-id, a real number, a null, etc. It also tries to minimize the space it takes to encode things. As a result, it is barf-making. A tru ...
Wireless/Cellular Technologies
... • mobile telephony offering the traditional bandwidth of 3.1 kHz • Emergency number common number throughout Europe (112); mandatory for all service providers; free of charge; connection with the highest priority (preemption of other connections possible) ...
... • mobile telephony offering the traditional bandwidth of 3.1 kHz • Emergency number common number throughout Europe (112); mandatory for all service providers; free of charge; connection with the highest priority (preemption of other connections possible) ...
What is an L3 Master Device?
... metadata as needed based on relevant features. If it returns NULL, the skb is consumed by the l3mdev driver and no further processing is done. Since the l3_out hook is called before dst_output, an l3mdev driver can change the dst attached to the skb thereby impacting the next function (dst->output) ...
... metadata as needed based on relevant features. If it returns NULL, the skb is consumed by the l3mdev driver and no further processing is done. Since the l3_out hook is called before dst_output, an l3mdev driver can change the dst attached to the skb thereby impacting the next function (dst->output) ...
Success story: China Telecom e-surfing cloud storage
... backup solution with better cost performance and lower total cost of ownership (TCO). Compared with traditional backup solutions using physical or virtual tape libraries, a cloud storage backup solution incorporates many advanced functions: Deduplication reduces users' needs for device procurement, ...
... backup solution with better cost performance and lower total cost of ownership (TCO). Compared with traditional backup solutions using physical or virtual tape libraries, a cloud storage backup solution incorporates many advanced functions: Deduplication reduces users' needs for device procurement, ...
Copyright © 2011 NMEA
... Existing & functioning NMEA 0183 installation on-board Upgrading some (but not all) electronics on-board Important data may only be available via NMEA 0183 EX- New NMEA 0183 Heading sensor installed last month • This information that is needed on N2k network ...
... Existing & functioning NMEA 0183 installation on-board Upgrading some (but not all) electronics on-board Important data may only be available via NMEA 0183 EX- New NMEA 0183 Heading sensor installed last month • This information that is needed on N2k network ...
Group 1C
... • Supervisor has assigned us the task of gathering evidence of illicit activity on a host machine. • Supervisor expresses concerns that a particular server has been infiltrated in the past. And So... – We need to be able to detect any intrusions – We need to be able to gather enough information abou ...
... • Supervisor has assigned us the task of gathering evidence of illicit activity on a host machine. • Supervisor expresses concerns that a particular server has been infiltrated in the past. And So... – We need to be able to detect any intrusions – We need to be able to gather enough information abou ...
Topics
... Information privacy: the right of individuals or organizations to control the information that is collected about them consider all of the websites at which you have set up accounts and the personal information you provided at each site consider that some websites track the pages you visit and ...
... Information privacy: the right of individuals or organizations to control the information that is collected about them consider all of the websites at which you have set up accounts and the personal information you provided at each site consider that some websites track the pages you visit and ...
An Overview of Broadband Over Power Line
... • Hardware: DSL requires modems and splitters for endusers; carriers use DSLAMs (digital subscriber line access multiplexers) • Differences between xDSL technologies: speed, operating distance, applications, ratio between up and downstream • Different approaches: ATM-based ADSL, ISDN DSL. • The impo ...
... • Hardware: DSL requires modems and splitters for endusers; carriers use DSLAMs (digital subscriber line access multiplexers) • Differences between xDSL technologies: speed, operating distance, applications, ratio between up and downstream • Different approaches: ATM-based ADSL, ISDN DSL. • The impo ...
Chapter12-Security
... • While computer systems today have some of the best security systems ever, they are more vulnerable than ever before • This vulnerability stems from the world-wide access to computer systems via the Internet • Computer and network security comes in many forms, including encryption algorithms, acces ...
... • While computer systems today have some of the best security systems ever, they are more vulnerable than ever before • This vulnerability stems from the world-wide access to computer systems via the Internet • Computer and network security comes in many forms, including encryption algorithms, acces ...
A Technical Introduction to NGSCB Security Summit East 2003
... But only one at a time Each nexus gets the same services The hardware keeps nexus secrets separate Nothing about this architecture prevents any nexus from running; however, the owner can control which nexuses are allowed to run ...
... But only one at a time Each nexus gets the same services The hardware keeps nexus secrets separate Nothing about this architecture prevents any nexus from running; however, the owner can control which nexuses are allowed to run ...
Chapter 12
... • While computer systems today have some of the best security systems ever, they are more vulnerable than ever before • This vulnerability stems from the worldwide access to computer systems via the Internet • Computer and network security comes in many forms, including encryption algorithms, access ...
... • While computer systems today have some of the best security systems ever, they are more vulnerable than ever before • This vulnerability stems from the worldwide access to computer systems via the Internet • Computer and network security comes in many forms, including encryption algorithms, access ...
Slide 1
... Mobile workforce extending the edge of corporate network to a user’s laptop: • User laptop at airport/ hotel can be compromised and serve as a bridge to corporate backbone ...
... Mobile workforce extending the edge of corporate network to a user’s laptop: • User laptop at airport/ hotel can be compromised and serve as a bridge to corporate backbone ...
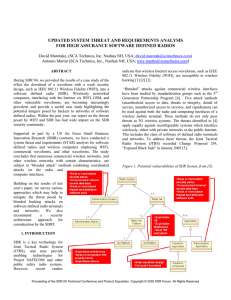
updated system threat and requirements analysis for high assurance
... hacking [1] [2] [3]. “Blended” attacks against commercial wireless interfaces have been studied by standardization groups such as the 3rd Generation Partnership Program [4]. Five attack methods (unauthorized access to data, threats to integrity, denial of service, unauthorized access to services, an ...
... hacking [1] [2] [3]. “Blended” attacks against commercial wireless interfaces have been studied by standardization groups such as the 3rd Generation Partnership Program [4]. Five attack methods (unauthorized access to data, threats to integrity, denial of service, unauthorized access to services, an ...
Control System Specification
... should be added per the individual system requirements. Several additional sections are referenced here and ...
... should be added per the individual system requirements. Several additional sections are referenced here and ...
Strategies Simplified Australian Signals Directorate
... Patching protects networks from vulnerabilities not previously identified in the applications. Also known as exploits, these vulnerabilities enable adversaries to execute malicious code, which can result in significant consequences for the organisation. Exploits are so common that adversaries can bu ...
... Patching protects networks from vulnerabilities not previously identified in the applications. Also known as exploits, these vulnerabilities enable adversaries to execute malicious code, which can result in significant consequences for the organisation. Exploits are so common that adversaries can bu ...
Information Security Office
... • Need a device capable of receiving an 802.11b signal (the wireless standard) • A device capable of locating itself on a map • Software that will log data from the second when a network is detected by the first. • You then move these devices from place to place, letting them do their job. • Over ti ...
... • Need a device capable of receiving an 802.11b signal (the wireless standard) • A device capable of locating itself on a map • Software that will log data from the second when a network is detected by the first. • You then move these devices from place to place, letting them do their job. • Over ti ...
Translation
... local services. – ___2.LBS was originally developed by mobile carriers in partnership with mobile content providers. – ___3.GPS and GSM can’t work indoors. – ___4.LBS and SMS can be used in combination to provide location-based mobile advertising. – ___5.Bluetooth, UWB, RFID and Wi-Fi can be used in ...
... local services. – ___2.LBS was originally developed by mobile carriers in partnership with mobile content providers. – ___3.GPS and GSM can’t work indoors. – ___4.LBS and SMS can be used in combination to provide location-based mobile advertising. – ___5.Bluetooth, UWB, RFID and Wi-Fi can be used in ...
NENA NG911 arch for SDO workshop
... How the access network provides location Exchange an identifier of some kind, implicitly (e.g. what port on the switch) or explicitly (e.g. MAC address, IP address) for location Location can be civic or geo Current discussion on whether it can be a reference (e.g. URI) which must be dereferenced by ...
... How the access network provides location Exchange an identifier of some kind, implicitly (e.g. what port on the switch) or explicitly (e.g. MAC address, IP address) for location Location can be civic or geo Current discussion on whether it can be a reference (e.g. URI) which must be dereferenced by ...
PCI DSS glossary of terms - PCI Security Standards Council
... (2) For Discover, JCB, MasterCard, and Visa payment cards, the second type of card verification value or code is the rightmost three-digit value printed in the signature panel area on the back of the card. For American Express payment cards, the code is a four-digit unembossed number printed above t ...
... (2) For Discover, JCB, MasterCard, and Visa payment cards, the second type of card verification value or code is the rightmost three-digit value printed in the signature panel area on the back of the card. For American Express payment cards, the code is a four-digit unembossed number printed above t ...
Anti-Virus - F5 Application Brief
... addition of resources, which leaves organizations with less than optimal protection and performance, and a single point of failure in the network. Organizations should consider the following challenges when deploying anti-virus systems: Providing high availability - Although infected or suspicious fi ...
... addition of resources, which leaves organizations with less than optimal protection and performance, and a single point of failure in the network. Organizations should consider the following challenges when deploying anti-virus systems: Providing high availability - Although infected or suspicious fi ...
Adding Location-Based Services to Existing Architectures
... As described in Examples 1 and 2, the user’s LBS application will be sent information detailing the “location estimate” of a particular mobile subscriber. The information received will include “geographical information,” as described in [3GPP TS 09.02]. “Geographical information” gives the location ...
... As described in Examples 1 and 2, the user’s LBS application will be sent information detailing the “location estimate” of a particular mobile subscriber. The information received will include “geographical information,” as described in [3GPP TS 09.02]. “Geographical information” gives the location ...
Acceptable Use Policy for IT
... Any information that is particularly sensitive or vulnerable must be encrypted and/or securely stored so that unauthorised access is prevented (or at least made extremely difficult). However this must be done in a way that does not prevent–or risk preventing–legitimate access by all properly-authori ...
... Any information that is particularly sensitive or vulnerable must be encrypted and/or securely stored so that unauthorised access is prevented (or at least made extremely difficult). However this must be done in a way that does not prevent–or risk preventing–legitimate access by all properly-authori ...