From Russia with Love: Behind the Trend Micro
... The techniques used to exploit the Macbook Air do not differ that much from those used against those browsing the Web on Windows machines, which shows that the attack was not targeted. All it required to succeed were an unpatched system and unsafe online behavior on the user’s part. Had the applicat ...
... The techniques used to exploit the Macbook Air do not differ that much from those used against those browsing the Web on Windows machines, which shows that the attack was not targeted. All it required to succeed were an unpatched system and unsafe online behavior on the user’s part. Had the applicat ...
Red Team Instrumentation
... approach to a privilege level below the Operating System – Operates on hardware platforms that support Intel VT-x – Provides secure data and key storage, decryption, and partial out-out-of-band execution – Secure against kernel attacks – Twelve months of R&D – Final release 4Q 2009 – Early adopters ...
... approach to a privilege level below the Operating System – Operates on hardware platforms that support Intel VT-x – Provides secure data and key storage, decryption, and partial out-out-of-band execution – Secure against kernel attacks – Twelve months of R&D – Final release 4Q 2009 – Early adopters ...
Document
... 2007, PeopleNet’s main technologies and products are as follows: Dynamic Password Authentication System with completely independent intellectual property rights, unified Identity Authentication Platform based on cloud, the Network Security Systems in Public area of Smart Cities, the innovative Secur ...
... 2007, PeopleNet’s main technologies and products are as follows: Dynamic Password Authentication System with completely independent intellectual property rights, unified Identity Authentication Platform based on cloud, the Network Security Systems in Public area of Smart Cities, the innovative Secur ...
Slide 1
... Restrict administrative privileges to operating systems and applications based on user duties. Such users should use a separate unprivileged account for email and web browsing. ...
... Restrict administrative privileges to operating systems and applications based on user duties. Such users should use a separate unprivileged account for email and web browsing. ...
MALWARE ALERT: PROTECT YOUR BUSINESS AND RAISE
... or network drive, and then demand a ransom for the delivery of a decryption key with which the company can retrieve its data. A hospital in California recently admitted to paying a ransom of $17,000 to retrieve its data. Data theft and the resulting damage Malware can also steal all kinds of data. F ...
... or network drive, and then demand a ransom for the delivery of a decryption key with which the company can retrieve its data. A hospital in California recently admitted to paying a ransom of $17,000 to retrieve its data. Data theft and the resulting damage Malware can also steal all kinds of data. F ...
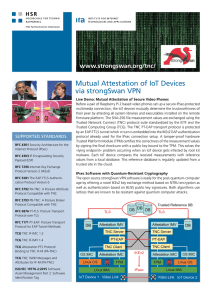
Mutual Attestation of IoT Devices via strongSwan VPN
... Trusted Network Connect (TNC) protocol suite standardized by the IETF and the Trusted Computing Group (TCG). The TNC PT-EAP transport protocol is protected by an EAP-TTLS tunnel which in turn is embedded into the IKEv2 EAP authentication protocol already used for the IPsec connection setup. A tamper ...
... Trusted Network Connect (TNC) protocol suite standardized by the IETF and the Trusted Computing Group (TCG). The TNC PT-EAP transport protocol is protected by an EAP-TTLS tunnel which in turn is embedded into the IKEv2 EAP authentication protocol already used for the IPsec connection setup. A tamper ...
Managed Network Anomaly Detection
... threats. This process includes analyzing traffic entering, leaving as well as within your network. Threat analysis of this kind is often like finding a needle in a hay stack and requires skills and understanding far beyond the normal abilities of most network professionals. No automated technology c ...
... threats. This process includes analyzing traffic entering, leaving as well as within your network. Threat analysis of this kind is often like finding a needle in a hay stack and requires skills and understanding far beyond the normal abilities of most network professionals. No automated technology c ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... Handoff is the process of changing the channel (frequency, time slot, spreading code, or combination of them) associated with the current connection while a call or data session is in progress. It is often initiated either by crossing a cell boundary or by deterioration in quality of the signal in t ...
... Handoff is the process of changing the channel (frequency, time slot, spreading code, or combination of them) associated with the current connection while a call or data session is in progress. It is often initiated either by crossing a cell boundary or by deterioration in quality of the signal in t ...
RS-232 Communications
... To Talk the Talk… We’ve mentioned that both devices must have the same speeds to talk, but they must also know to handle problems. The transmission rate of serial devices is called baud. It is the number of changes in the signal per second. ...
... To Talk the Talk… We’ve mentioned that both devices must have the same speeds to talk, but they must also know to handle problems. The transmission rate of serial devices is called baud. It is the number of changes in the signal per second. ...
MultiRack Setup Instruction
... The above diagram illustrates the various latencies in the SoundGrid system. Network latency occurs between the I/O device and the processing engine; driver latency is added between the network and the host computer on which the driver is installed. ASIO or Core Audio buffering is usually added betw ...
... The above diagram illustrates the various latencies in the SoundGrid system. Network latency occurs between the I/O device and the processing engine; driver latency is added between the network and the host computer on which the driver is installed. ASIO or Core Audio buffering is usually added betw ...
Introduction to Healthcare Information Technology
... Introduction to Healthcare Information Technology ...
... Introduction to Healthcare Information Technology ...
Example: Data Mining for the NBA - The University of Texas at Dallas
... multiple, overlapping ATIs at any layer. Furthermore, concrete diverse implementations may exist for the same or different ATIs (e.g., Intel TXT and AMD SVM at the hardware layer). One of the main design goals of the ATI Architecture is the active incorporation of diverse designs and implementations ...
... multiple, overlapping ATIs at any layer. Furthermore, concrete diverse implementations may exist for the same or different ATIs (e.g., Intel TXT and AMD SVM at the hardware layer). One of the main design goals of the ATI Architecture is the active incorporation of diverse designs and implementations ...
Towards a Trustworthy Android Ecosystem
... • All the studied tools found vulnerable to common transformations • At least 43% signatures are not based on ...
... • All the studied tools found vulnerable to common transformations • At least 43% signatures are not based on ...
Giovanna Sissa Osservatorio Tecnologico MIUR
... •It allows the students to learn more because they can better understand how computers and operating systems work; •It widens the learning spectrum of the students promoting the creation of different skills; •It makes possible to reuse obsolete hardware systems still available at school, thus helpin ...
... •It allows the students to learn more because they can better understand how computers and operating systems work; •It widens the learning spectrum of the students promoting the creation of different skills; •It makes possible to reuse obsolete hardware systems still available at school, thus helpin ...
MYDIGIPASS for Healthcare
... the healthcare ecosystem. From the time a patient logs onto a patient portal; to a physician reviewing that patient’s health information using an EHR system; to accessing the state’s prescription drug monitoring program, to electronically prescribing medication for that patient’s use, to submitting ...
... the healthcare ecosystem. From the time a patient logs onto a patient portal; to a physician reviewing that patient’s health information using an EHR system; to accessing the state’s prescription drug monitoring program, to electronically prescribing medication for that patient’s use, to submitting ...
Glossary of Terms, Abbreviations, and Acronyms
... Also referred to as “computer forensics.” As it relates to information security, the application of investigative tools and analysis techniques to gather evidence from computer resources to determine the cause of data compromises. ...
... Also referred to as “computer forensics.” As it relates to information security, the application of investigative tools and analysis techniques to gather evidence from computer resources to determine the cause of data compromises. ...
How medical device companies can safeguard
... emerging industries that China has identified in five-year plans. Currently the Chinese government, in coordination with stateowned enterprises, is funding a new program dubbed “Made in China 2025,” whose goals include capturing substantial global market-share over time. Advanced medical devices are ...
... emerging industries that China has identified in five-year plans. Currently the Chinese government, in coordination with stateowned enterprises, is funding a new program dubbed “Made in China 2025,” whose goals include capturing substantial global market-share over time. Advanced medical devices are ...
EXECUTIVE SUMMARY
... IMPORTANT: We are not recommending that antivirus protection in general be disabled. Nor are we recommending that ProfitStars program files be excluded from virus protection. We are recommending only that the data files for ProfitStars programs be excluded from real-time virus scans. If necessary, ...
... IMPORTANT: We are not recommending that antivirus protection in general be disabled. Nor are we recommending that ProfitStars program files be excluded from virus protection. We are recommending only that the data files for ProfitStars programs be excluded from real-time virus scans. If necessary, ...
CS 356 – Lecture 9 Malicious Code
... Mobile Code • programs that can be shipped unchanged to a variety of ...
... Mobile Code • programs that can be shipped unchanged to a variety of ...
Tara and Orcun
... Web Application Security (Scripting issues) Technical Vulnerabilities (Cross-site Scripting) Security Vulnerabilities (Denial of Service) Architectural/Logical Vulnerabilities (Information Leakage) ...
... Web Application Security (Scripting issues) Technical Vulnerabilities (Cross-site Scripting) Security Vulnerabilities (Denial of Service) Architectural/Logical Vulnerabilities (Information Leakage) ...
PrinterOn for Healthcare
... • With PrinterOn and a PrinterOn-enabled printer they can print: 1. Authenticate to the PrinterOn service and select the desired printer from the directory 2. Submit the print job through email, or PrinterOn mobile app or web upload or the PrintWhere® driver (Windows desktop only) 3. PrinterOn proce ...
... • With PrinterOn and a PrinterOn-enabled printer they can print: 1. Authenticate to the PrinterOn service and select the desired printer from the directory 2. Submit the print job through email, or PrinterOn mobile app or web upload or the PrintWhere® driver (Windows desktop only) 3. PrinterOn proce ...
Secure your remote access with VASCO and
... Combining Juniper Networks’ firewalls, VPN solutions and network access security appliances with VASCO’s DIGIPASS strong authentication enhances the security of your network and remote access, while remaining easy-to-use When employees use their PC, they want to read e-mail, use software and documen ...
... Combining Juniper Networks’ firewalls, VPN solutions and network access security appliances with VASCO’s DIGIPASS strong authentication enhances the security of your network and remote access, while remaining easy-to-use When employees use their PC, they want to read e-mail, use software and documen ...
Lawful Interception Offering
... Supports Non-Transparent Bearer Services (Data) RLP version 0, 1 and 2 according to 3GPP TR 24.022 ...
... Supports Non-Transparent Bearer Services (Data) RLP version 0, 1 and 2 according to 3GPP TR 24.022 ...
BDTIC www.BDTIC.com/infineon S e n s e & ... T P M S
... characteristics. With respect to any examples or hints given herein, any typical values stated herein and/or any information regarding the application of the device, Infineon Technologies hereby disclaims any and all warranties and liabilities of any kind, including without limitation, warranties of ...
... characteristics. With respect to any examples or hints given herein, any typical values stated herein and/or any information regarding the application of the device, Infineon Technologies hereby disclaims any and all warranties and liabilities of any kind, including without limitation, warranties of ...