ppt
... • The key challenge of building wide area P2P systems is a scalable and robust location service • Solutions covered in this lecture ...
... • The key challenge of building wide area P2P systems is a scalable and robust location service • Solutions covered in this lecture ...
Chapter 3 - Department of Computer and Information Science and
... delay increase or packet discard to detect congestion may erroneously signal congestion (i.e., not always reliable) [e.g., over wireless links] done end-to-end without network assistance TCP cuts down its window/rate ...
... delay increase or packet discard to detect congestion may erroneously signal congestion (i.e., not always reliable) [e.g., over wireless links] done end-to-end without network assistance TCP cuts down its window/rate ...
www.ijecs.in International Journal Of Engineering And Computer Science ISSN:2319-7242
... evenly distribute power dissipation among nodes [3].Wasim El-Hajj et.al proposed a fuzzy-based hierarchical energy efficient routing scheme (FEER) for large scale mobile ad-hoc networks which maximizes the lifetime of the network. Each node in the network is characterized by its residual energy, tra ...
... evenly distribute power dissipation among nodes [3].Wasim El-Hajj et.al proposed a fuzzy-based hierarchical energy efficient routing scheme (FEER) for large scale mobile ad-hoc networks which maximizes the lifetime of the network. Each node in the network is characterized by its residual energy, tra ...
Aalborg Universitet Droop-free Team-oriented Control for AC Distribution Systems
... module handles both active power sharing and frequency synchronization. 4) Unlike existing methods, the proposed technique does not require any frequency feedback or frequency measurement, which can help to improve dynamic response of the system. 5) A sparse communication network links the sources ( ...
... module handles both active power sharing and frequency synchronization. 4) Unlike existing methods, the proposed technique does not require any frequency feedback or frequency measurement, which can help to improve dynamic response of the system. 5) A sparse communication network links the sources ( ...
Optimizing Matrix Multiply - Dipartimento di Matematica
... • Routing algorithm (path used): • Example in 2D torus: all east-west then all north-south (avoids deadlock). • Switching strategy: • Circuit switching: full path reserved for entire message, like the telephone. • Packet switching: message broken into separatelyrouted packets, like the post office. ...
... • Routing algorithm (path used): • Example in 2D torus: all east-west then all north-south (avoids deadlock). • Switching strategy: • Circuit switching: full path reserved for entire message, like the telephone. • Packet switching: message broken into separatelyrouted packets, like the post office. ...
The OSI networking reference model.
... services or functions from other systems. These protocols may not be the actual application. For instance, Internet Explorer is an application that uses HTTP at Layer 7 to request Web pages. ...
... services or functions from other systems. These protocols may not be the actual application. For instance, Internet Explorer is an application that uses HTTP at Layer 7 to request Web pages. ...
Part III Network Layer
... Notification from sender to the receiver that the receiver should pass all data that it has to the application. Normally set by sender when the sender’s buffer is empty ...
... Notification from sender to the receiver that the receiver should pass all data that it has to the application. Normally set by sender when the sender’s buffer is empty ...
WEP Security - ODU Computer Science
... Takes advantage of defragmentation and IV reuse Takes advantage of knowledge of plaintext of at least first eight bytes of 802.11 data Each data includes 4 bytes of checksum An 802.11 frame can be divided into 16 segments The access point will defragment the frame before forwarding, allowing the tra ...
... Takes advantage of defragmentation and IV reuse Takes advantage of knowledge of plaintext of at least first eight bytes of 802.11 data Each data includes 4 bytes of checksum An 802.11 frame can be divided into 16 segments The access point will defragment the frame before forwarding, allowing the tra ...
GENIConnections
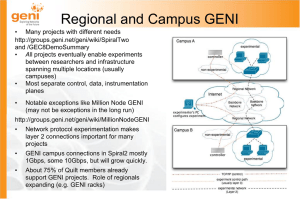
... Regional and Campus GENI • Many projects with different needs http://groups.geni.net/geni/wiki/SpiralTwo and /GEC8DemoSummary • All projects eventually enable experiments between researchers and infrastructure spanning multiple locations (usually campuses) • Most separate control, data, instrumentat ...
... Regional and Campus GENI • Many projects with different needs http://groups.geni.net/geni/wiki/SpiralTwo and /GEC8DemoSummary • All projects eventually enable experiments between researchers and infrastructure spanning multiple locations (usually campuses) • Most separate control, data, instrumentat ...
2. cross-layer control of real-time data transmission over wireless
... video transmission over pre-coded Orthogonal Frequency Division Multiplexing (OFDM) system, enhanced by adaptive vector channel allocation. Zou [53] proposed a MPEG-4 frame drop policy in order to save bandwidth of IEEE 802.11 WLAN in the DCF mode. Cross-layer approaches. According to the above revi ...
... video transmission over pre-coded Orthogonal Frequency Division Multiplexing (OFDM) system, enhanced by adaptive vector channel allocation. Zou [53] proposed a MPEG-4 frame drop policy in order to save bandwidth of IEEE 802.11 WLAN in the DCF mode. Cross-layer approaches. According to the above revi ...
OSI Reference Model
... locked into a single vendor’s equipment, and global networks like the Internet would have been impractical, if not impossible. Network models are organized into layers, with each layer representing a specific networking function. These functions are controlled by protocols, which are rules that gove ...
... locked into a single vendor’s equipment, and global networks like the Internet would have been impractical, if not impossible. Network models are organized into layers, with each layer representing a specific networking function. These functions are controlled by protocols, which are rules that gove ...
Introduction
... Can we explain how the networks were generated? What else? A still very young field! (What is the basic principles and what those principle will mean?) ...
... Can we explain how the networks were generated? What else? A still very young field! (What is the basic principles and what those principle will mean?) ...
P2P networks course
... Relevant data must be published to network, e.g. Client status How does this work? ...
... Relevant data must be published to network, e.g. Client status How does this work? ...
3. Ethernet - Faculty of Computer Science and Information Technology
... Ethernet Operation Legacy Ethernet Fast Ethernet Gigabit Ethernet Ethernet Switching ...
... Ethernet Operation Legacy Ethernet Fast Ethernet Gigabit Ethernet Ethernet Switching ...
Network Access Control for Mobile Ad Hoc Network
... – Any “bogus” packet that has incorrect authentication information will be filtered out immediately. – As a result, illegitimate nodes will be excluded from communication (routes). ...
... – Any “bogus” packet that has incorrect authentication information will be filtered out immediately. – As a result, illegitimate nodes will be excluded from communication (routes). ...
presentation source - University of Baltimore Home Page
... • Network Layer Address (IP address) – Assigned by network managers, or by programs such as DHCP, and placed in configuration files – Every network on the Internet is assigned a range of possible IP addresses for use on its network ...
... • Network Layer Address (IP address) – Assigned by network managers, or by programs such as DHCP, and placed in configuration files – Every network on the Internet is assigned a range of possible IP addresses for use on its network ...
network
... link, router resources (bandwidth, buffers) may be allocated to VC (dedicated resources = predictable ...
... link, router resources (bandwidth, buffers) may be allocated to VC (dedicated resources = predictable ...