Enabling the Interplanetary Internet
... the Mars network for the next decade, identified current and future network protocols to meet those needs, modeled and simulated the proposed architecture, and implemented flight-ready versions of the new protocols. The architecture identified for a next-generation Mars relay infrastructure includes ...
... the Mars network for the next decade, identified current and future network protocols to meet those needs, modeled and simulated the proposed architecture, and implemented flight-ready versions of the new protocols. The architecture identified for a next-generation Mars relay infrastructure includes ...
Acknowledgement Packet Format - IEEE Standards working groups
... Address List (AL) field – the list of addresses with pending messages (size dependent on PAS). Payload field – an optional SDU transmitted with the beacon. If a payload is present (after decoding, there is still some remaining bytes) the MAC sub-layer will send the MLME-BEACONNOTIFY.indication primi ...
... Address List (AL) field – the list of addresses with pending messages (size dependent on PAS). Payload field – an optional SDU transmitted with the beacon. If a payload is present (after decoding, there is still some remaining bytes) the MAC sub-layer will send the MLME-BEACONNOTIFY.indication primi ...
Selling an Idea or a Product
... TCP solution: “slow start”. Originally, window size = buffer space on remote end. Now, window size = control on how much to add to congestion. Start sending slowly. – If no timeout, slowly increase window size (throughput). – If a timeout occurs, it means there’s congestion, so cut window size (thro ...
... TCP solution: “slow start”. Originally, window size = buffer space on remote end. Now, window size = control on how much to add to congestion. Start sending slowly. – If no timeout, slowly increase window size (throughput). – If a timeout occurs, it means there’s congestion, so cut window size (thro ...
S_V07 - Raadio- ja sidetehnika instituut
... – New RTT = a (old RTT) + (1 - a) (new sample) – Recommended value for a: 0.8 - 0.9 • 0.875 for most TCP’s ...
... – New RTT = a (old RTT) + (1 - a) (new sample) – Recommended value for a: 0.8 - 0.9 • 0.875 for most TCP’s ...
An Enhanced Data Mining Technique for Energy Efficiency
... cars etc.) for the retrieval of sensory data from smart dust motes in comparison with the multi hop transfers to a centralized element. Mobile sink awakening through the network deployment region can collect the data from static sensor nodes over a single hop radio link when accessing within radio r ...
... cars etc.) for the retrieval of sensory data from smart dust motes in comparison with the multi hop transfers to a centralized element. Mobile sink awakening through the network deployment region can collect the data from static sensor nodes over a single hop radio link when accessing within radio r ...
3rd Edition: Chapter 4
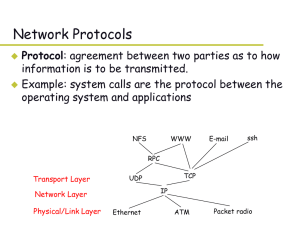
... IP address: subnet part (high order bits) host part (low order bits) What’s a subnet ? device interfaces with same subnet part of IP address can physically reach each other without intervening router ...
... IP address: subnet part (high order bits) host part (low order bits) What’s a subnet ? device interfaces with same subnet part of IP address can physically reach each other without intervening router ...
PPTX - gozips.uakron.edu
... • Basic problem: you can’t just send datagrams over the link! • We first consider how to encode bits into the signal at the source and recover bits at the receiving node • Once it is possible to transmit bits, we need to figure out how to package these bits into FRAME • Assume each node is able to r ...
... • Basic problem: you can’t just send datagrams over the link! • We first consider how to encode bits into the signal at the source and recover bits at the receiving node • Once it is possible to transmit bits, we need to figure out how to package these bits into FRAME • Assume each node is able to r ...
ANALYSIS OF LIGHTWEIGHT SYBIL ATTACK DETECTION
... A set of mobile nodes which can communicate directly with other nodes within its transmission range and use multihop routing for nodes outside its transmission range is called Mobile Ad hoc Network (MANET). The infrastructure less nature (bandwidth, memory and battery power) of MANET makes it suscep ...
... A set of mobile nodes which can communicate directly with other nodes within its transmission range and use multihop routing for nodes outside its transmission range is called Mobile Ad hoc Network (MANET). The infrastructure less nature (bandwidth, memory and battery power) of MANET makes it suscep ...
A Performance and Power Analysis of WK
... easier component reuse and better interoperability. Overall performance and scalability increase since the networking resources are shared. Scheduling of traffic on shared resources prevents latency increases on critical signals. Power efficiency is one of the most important concerns in NoC architec ...
... easier component reuse and better interoperability. Overall performance and scalability increase since the networking resources are shared. Scheduling of traffic on shared resources prevents latency increases on critical signals. Power efficiency is one of the most important concerns in NoC architec ...
Open resource - Homeland Security Digital Library
... population lives within 100 miles of the coast; 90% of the world’s commerce is seaborne, and 75% of that trade passes through a few, vulnerable, canals and international straits” [1]. Moreover, according to the International Maritime Organization (IMO), in the last two decades there has been a three ...
... population lives within 100 miles of the coast; 90% of the world’s commerce is seaborne, and 75% of that trade passes through a few, vulnerable, canals and international straits” [1]. Moreover, according to the International Maritime Organization (IMO), in the last two decades there has been a three ...
Sem 2 Chapter 8
... is dropped packets that result in a loss of data. In order to reduce data lost, ICMP messages must be sent to the source of the congestion. This type of ICMP message is called a sourcequench message. • The source-quench message notifies the sender of the congestion and asks the sender to reduce its ...
... is dropped packets that result in a loss of data. In order to reduce data lost, ICMP messages must be sent to the source of the congestion. This type of ICMP message is called a sourcequench message. • The source-quench message notifies the sender of the congestion and asks the sender to reduce its ...
3rd Edition: Chapter 4
... Link-state advertisements only in area each node has detailed area topology; only know direction (shortest path) to nets in other areas. Area border routers: “summarize” distances to nets in own area, advertise to other Area Border routers. Backbone routers: run OSPF routing limited to ...
... Link-state advertisements only in area each node has detailed area topology; only know direction (shortest path) to nets in other areas. Area border routers: “summarize” distances to nets in own area, advertise to other Area Border routers. Backbone routers: run OSPF routing limited to ...
The OSI Model: Understanding the Seven Layers of Computer
... Protocols, or rules, can do their work in either hardware or software or, as with most protocol stacks, in a combination of the two. The nature of these stacks is that the lower layers do their work in hardware or firmware (software that runs on specific hardware chips) while the higher layers work ...
... Protocols, or rules, can do their work in either hardware or software or, as with most protocol stacks, in a combination of the two. The nature of these stacks is that the lower layers do their work in hardware or firmware (software that runs on specific hardware chips) while the higher layers work ...
MPV2
... Having a large number of overlay nodes to act as SOAPs increases the bandwidth resources that an attacker must obtain to prevent legitimate traffic from accessing the overlay. SOS becomes a large distributed firewall that ...
... Having a large number of overlay nodes to act as SOAPs increases the bandwidth resources that an attacker must obtain to prevent legitimate traffic from accessing the overlay. SOS becomes a large distributed firewall that ...
Networking BASICS
... • A star bus topology is typically used to connect multiple hubs in star topologies with a bus topology and provides additional fault tolerance. A star ring topology is wired like a star, but functions like a ring. The packets in a star ring do not go directly to the next device on the ring, but ins ...
... • A star bus topology is typically used to connect multiple hubs in star topologies with a bus topology and provides additional fault tolerance. A star ring topology is wired like a star, but functions like a ring. The packets in a star ring do not go directly to the next device on the ring, but ins ...
PPT - Computer Science at Rutgers
... • Push: Special descriptor used for sharing with a firewalled servent ...
... • Push: Special descriptor used for sharing with a firewalled servent ...