Chord: A Scalable Peer-to-peer Lookup Service for Internet Applications Ion Stoica
... tree, much like DNS. Information about an object is stored in a particular leaf domain, and pointer caches provide search short cuts [22]. The Globe system handles high load on the logical root by partitioning objects among multiple physical root servers using hash-like techniques. Chord performs th ...
... tree, much like DNS. Information about an object is stored in a particular leaf domain, and pointer caches provide search short cuts [22]. The Globe system handles high load on the logical root by partitioning objects among multiple physical root servers using hash-like techniques. Chord performs th ...
Chord: A Scalable Peer-to-peer Lookup Service for Internet Applications Ion Stoica
... tree, much like DNS. Information about an object is stored in a particular leaf domain, and pointer caches provide search short cuts [22]. The Globe system handles high load on the logical root by partitioning objects among multiple physical root servers using hash-like techniques. Chord performs th ...
... tree, much like DNS. Information about an object is stored in a particular leaf domain, and pointer caches provide search short cuts [22]. The Globe system handles high load on the logical root by partitioning objects among multiple physical root servers using hash-like techniques. Chord performs th ...
PRP - EPFL
... However, a frame will not be discarded unless a second frame arrives from the other lane from that same source and sequence number and with the correct line identifier, which is not possible since a singly attached node is attached to one lane only (half ...
... However, a frame will not be discarded unless a second frame arrives from the other lane from that same source and sequence number and with the correct line identifier, which is not possible since a singly attached node is attached to one lane only (half ...
21-p2p
... – No constraints on how to choose ids for files => easy to have to files collide, creating “denial of service” (censorship) – Solution: have a id type that requires a private key signature that is verified when updating the file – Cache file on the reverse path of queries/publications => attempt to ...
... – No constraints on how to choose ids for files => easy to have to files collide, creating “denial of service” (censorship) – Solution: have a id type that requires a private key signature that is verified when updating the file – Cache file on the reverse path of queries/publications => attempt to ...
3rd Edition: Chapter 3
... Shared-tree: steiner tree steiner tree: minimum cost tree connecting all routers with attached group members problem is NP-complete excellent heuristics exists not used in practice: ...
... Shared-tree: steiner tree steiner tree: minimum cost tree connecting all routers with attached group members problem is NP-complete excellent heuristics exists not used in practice: ...
Transmission Control Protocol/Internet Protocol for the PC: an Ethernet implementation
... network. However, the thin-wire does allow direct connection to single boards in computers, ...
... network. However, the thin-wire does allow direct connection to single boards in computers, ...
Design and performance analysis of distributed
... wireless sensor network with uniformly distributed nodes. It is assumed that there is no central processing unit to optimally select the relay and that the nodes use their locally available knowledge, that is, their distances from the source as well as their backward channel gains, to compete with o ...
... wireless sensor network with uniformly distributed nodes. It is assumed that there is no central processing unit to optimally select the relay and that the nodes use their locally available knowledge, that is, their distances from the source as well as their backward channel gains, to compete with o ...
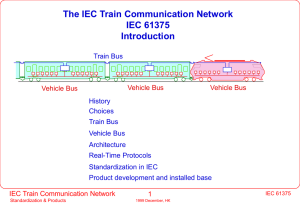
TCN Introduction
... (jumpers, connectors, discontinuities) operation without previous commissioning close following of UIC 556/ UIC557 leaflets The WTB features cost some overhead: two hardware channels and fritting voltage sources special digital signal processor for Manchester decoding unique link layer for inaugurat ...
... (jumpers, connectors, discontinuities) operation without previous commissioning close following of UIC 556/ UIC557 leaflets The WTB features cost some overhead: two hardware channels and fritting voltage sources special digital signal processor for Manchester decoding unique link layer for inaugurat ...
Networking Issues in Wireless Sensor Networks
... comparison of the cost of computation to communication in future platforms by Pottie and Kaiser [4] reveals that 3000 instructions can be executed for the same cost as the transmission of one bit over 100m. Energy conservation in such networks involves two dominant approaches to minimize communicati ...
... comparison of the cost of computation to communication in future platforms by Pottie and Kaiser [4] reveals that 3000 instructions can be executed for the same cost as the transmission of one bit over 100m. Energy conservation in such networks involves two dominant approaches to minimize communicati ...
3rd Edition: Chapter 1
... first packet bit transmitted, t = 0 last bit transmitted, t = L / R first packet bit arrives last packet bit arrives, send ACK last bit of 2nd packet arrives, send ACK last bit of 3rd packet arrives, send ACK ...
... first packet bit transmitted, t = 0 last bit transmitted, t = L / R first packet bit arrives last packet bit arrives, send ACK last bit of 2nd packet arrives, send ACK last bit of 3rd packet arrives, send ACK ...
Document in Word `97 Format
... b. Throughput keeps increasing gradually as offered load is increased c. Delay increases only gradually as offered load is increased d. Tokens occasionally get lost e. The recipient of a message strips the payload and inserts a free token onto the LAN Q6 Which of the following is NOT a characteristi ...
... b. Throughput keeps increasing gradually as offered load is increased c. Delay increases only gradually as offered load is increased d. Tokens occasionally get lost e. The recipient of a message strips the payload and inserts a free token onto the LAN Q6 Which of the following is NOT a characteristi ...
iWork ’08 Quick Tour
... Code 1 is used only by the destination host to show that not all of the fragments have arrived within a set time. Whenever a router receives a datagram with a time-to-live value of zero, it discards the datagram and sends a time-exceeded message to the original source. When the final destination doe ...
... Code 1 is used only by the destination host to show that not all of the fragments have arrived within a set time. Whenever a router receives a datagram with a time-to-live value of zero, it discards the datagram and sends a time-exceeded message to the original source. When the final destination doe ...
Chapter 5 on Link/MAC Layer - Department of Computer and
... seldom used on low bit-error link (fiber, some twisted pair) wireless links: high error rates • Q: why both link-level and end-end reliability? 5: DataLink Layer ...
... seldom used on low bit-error link (fiber, some twisted pair) wireless links: high error rates • Q: why both link-level and end-end reliability? 5: DataLink Layer ...
ppt - Course Website Directory
... Each packet contains a sequence number that is incremented for each new LSA packet sent by that source router. Each router keeps track of all the (source router, sequence) pairs it sees. When a new LSA packet comes in, it is checked against these pairs. If the received packet is new, it is forwarded ...
... Each packet contains a sequence number that is incremented for each new LSA packet sent by that source router. Each router keeps track of all the (source router, sequence) pairs it sees. When a new LSA packet comes in, it is checked against these pairs. If the received packet is new, it is forwarded ...
Next Generation Car Network - FlexRay
... provides bounded latency, and the dynamic segment helps meet varying bandwidth requirements that can emerge at system run time. The fixed-length static segment of a FlexRay frame transfers messages with a fixed-time-trigger method, and the dynamic segment transfers messages with a flexible, time-tri ...
... provides bounded latency, and the dynamic segment helps meet varying bandwidth requirements that can emerge at system run time. The fixed-length static segment of a FlexRay frame transfers messages with a fixed-time-trigger method, and the dynamic segment transfers messages with a flexible, time-tri ...
Introduction Lecture 1
... IPv4 address: a 32-bit number, usually written in dotted decimal form, that uniquely identifies an interface of some computer Host Address: another term for IP address Network: a group of hosts, all of which have an identical beginning position of their ip addresses. Network Number: a 32-bit number ...
... IPv4 address: a 32-bit number, usually written in dotted decimal form, that uniquely identifies an interface of some computer Host Address: another term for IP address Network: a group of hosts, all of which have an identical beginning position of their ip addresses. Network Number: a 32-bit number ...
3rd Edition, Chapter 5
... wireless links: high error rates • Q: why both link-level and end-end reliability? ...
... wireless links: high error rates • Q: why both link-level and end-end reliability? ...
Copper Media - WordPress.com
... sent on a mesh network can take any of several possible paths from source3 to destination. (Recall that even in a ring, although two cable paths exist, massages can only travel in one direction.) Some WANs. most notable the Internet, employ mesh routing. A mesh network in which every device connects ...
... sent on a mesh network can take any of several possible paths from source3 to destination. (Recall that even in a ring, although two cable paths exist, massages can only travel in one direction.) Some WANs. most notable the Internet, employ mesh routing. A mesh network in which every device connects ...