presentation source
... computers working together as a unified computing resource illusion is one machine system can run on its own ...
... computers working together as a unified computing resource illusion is one machine system can run on its own ...
Chapter 5
... • Data is transmitted in one direction around the ring • Each workstation acts as a repeater to regenerate the signal and sends it on to the next node • No terminator needed • Most rings use the token method to determine who can transmit next. • A token is transmitted around the ring. A computer wis ...
... • Data is transmitted in one direction around the ring • Each workstation acts as a repeater to regenerate the signal and sends it on to the next node • No terminator needed • Most rings use the token method to determine who can transmit next. • A token is transmitted around the ring. A computer wis ...
Time Divided into two parts: Briefly talking about Midterm II, and
... x exist, you also don’t know what its IP address. The only thing you know is your successor. You also know if you go along the ring, you will definitely find out which is SuccessorNode(x). Then you just do the routing hop by hop via the successor until you hit SuccessorNode(x). When you get to the d ...
... x exist, you also don’t know what its IP address. The only thing you know is your successor. You also know if you go along the ring, you will definitely find out which is SuccessorNode(x). Then you just do the routing hop by hop via the successor until you hit SuccessorNode(x). When you get to the d ...
Brad`s Lecture on networks
... greater capacity, very fast, very reliable can be used over longer distances immune to electrical interference, small size but very expensive and hard to install ...
... greater capacity, very fast, very reliable can be used over longer distances immune to electrical interference, small size but very expensive and hard to install ...
II. The Let and Live Strategy
... There are cases when technology is not used exactly like how it was supposed to be used. In an MANET network, there might be nodes unwilling to participate on common interest, which is reliable network with end-to-end connectivity for all elements. These uncooperative nodes would accept the traffic ...
... There are cases when technology is not used exactly like how it was supposed to be used. In an MANET network, there might be nodes unwilling to participate on common interest, which is reliable network with end-to-end connectivity for all elements. These uncooperative nodes would accept the traffic ...
Transportation Layer (1)
... • Link: want to transfer data to Ethernet card 08.00.2b.2a.83.62 • Network: want to transfer data to IP host 128.2.222.85 • Transport: which entity you will try to address? – want to talk to one process on host 128.2.222.85. – what to do use? process ID? how many bits? What would be the problem when ...
... • Link: want to transfer data to Ethernet card 08.00.2b.2a.83.62 • Network: want to transfer data to IP host 128.2.222.85 • Transport: which entity you will try to address? – want to talk to one process on host 128.2.222.85. – what to do use? process ID? how many bits? What would be the problem when ...
LAN Transmission Equipment
... Manufacturer (Brand-name versus non Brand-name) Computer or network equipment bus type Operating system used by the computer Use of half- or full-duplex communications ...
... Manufacturer (Brand-name versus non Brand-name) Computer or network equipment bus type Operating system used by the computer Use of half- or full-duplex communications ...
Controller Area Network
... specific tasks like temperature monitoring, pressure monitoring, obstacle sensing, movement of the vehicle, speed control of the vehicle, fuel monitoring, displaying the digital values of various parameters being monitored by the slave nodes, raising alarms for any violation of the user constraints ...
... specific tasks like temperature monitoring, pressure monitoring, obstacle sensing, movement of the vehicle, speed control of the vehicle, fuel monitoring, displaying the digital values of various parameters being monitored by the slave nodes, raising alarms for any violation of the user constraints ...
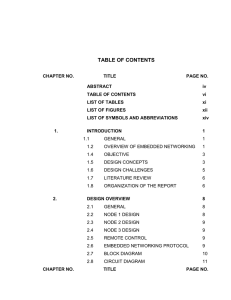
Chapter 3 OSI Model Worksheet In class lecture and handout.
... 2. This layer specifies how addresses are assigned and how packets of data are forwarded from one network to another toward the destination. ...
... 2. This layer specifies how addresses are assigned and how packets of data are forwarded from one network to another toward the destination. ...
Chapter 14
... Frame check sequence (as in HDLC) If frame OK and address matches receiver, send ACK Frame may be damaged by noise or by another station transmitting at the same time (collision) Any overlap of frames causes collision Max utilization 18% ...
... Frame check sequence (as in HDLC) If frame OK and address matches receiver, send ACK Frame may be damaged by noise or by another station transmitting at the same time (collision) Any overlap of frames causes collision Max utilization 18% ...
William Stallings Data and Computer Communications
... • Frame check sequence (as in HDLC) • If frame OK and address matches receiver, send ACK • Frame may be damaged by noise or by another station transmitting at the same time (collision) • Any overlap of frames causes collision • Max utilization 18% ...
... • Frame check sequence (as in HDLC) • If frame OK and address matches receiver, send ACK • Frame may be damaged by noise or by another station transmitting at the same time (collision) • Any overlap of frames causes collision • Max utilization 18% ...
Protocols - Teach ICT
... • LAN protocols refer to network operating systems. Access protocols determine how an attached device communicates with the network transmission medium (often cabling). ...
... • LAN protocols refer to network operating systems. Access protocols determine how an attached device communicates with the network transmission medium (often cabling). ...
Solution
... ANS: Each potential link is included into the network independently with a fixed probability. (1) Degree distribution is normal in contrast to the power distribution for real networks (2) No community structure in contrast to the community structure for real networks (3) No homophily in contrast to ...
... ANS: Each potential link is included into the network independently with a fixed probability. (1) Degree distribution is normal in contrast to the power distribution for real networks (2) No community structure in contrast to the community structure for real networks (3) No homophily in contrast to ...
Universität Stuttgart Communication Networks II Sample Solution
... Port Aggregation provides a couple of different configuration options that have to be the same on both switches. This has to be configured manually. (Not expected as an answer in the exam) ...
... Port Aggregation provides a couple of different configuration options that have to be the same on both switches. This has to be configured manually. (Not expected as an answer in the exam) ...
View File - UET Taxila
... Crate a layer when different abstraction is needed Each layer performs a well define function Functions of the layers chosen taking internationally ...
... Crate a layer when different abstraction is needed Each layer performs a well define function Functions of the layers chosen taking internationally ...
related work
... format and routing protocol A Roofnet node must also allocate IP addresses via DHCP to user hosts attached to the node's Ethernet port prevents hosts from connecting to each other through Roofnet ...
... format and routing protocol A Roofnet node must also allocate IP addresses via DHCP to user hosts attached to the node's Ethernet port prevents hosts from connecting to each other through Roofnet ...
View File
... Crate a layer when different abstraction is needed Each layer performs a well define function Functions of the layers chosen taking internationally ...
... Crate a layer when different abstraction is needed Each layer performs a well define function Functions of the layers chosen taking internationally ...
Transport Layer
... Segmentation - Transport layer protocols break large data units received from Session layer into smaller segments Maximum transmission unit (MTU): largest data unit a given network will carry Reassembly: process of reconstructing segmented data units Sequencing: method of identifying segments that b ...
... Segmentation - Transport layer protocols break large data units received from Session layer into smaller segments Maximum transmission unit (MTU): largest data unit a given network will carry Reassembly: process of reconstructing segmented data units Sequencing: method of identifying segments that b ...
Advantages and Disadvantages of Different Network Topologies
... The cable length is limited. This limits the number of stations that can be connected. This network topology can perform well only for a limited number of nodes. Ring Topology Advantage The data being transmitted between two nodes passes through all the intermediate nodes. A central server is not re ...
... The cable length is limited. This limits the number of stations that can be connected. This network topology can perform well only for a limited number of nodes. Ring Topology Advantage The data being transmitted between two nodes passes through all the intermediate nodes. A central server is not re ...
LAN - Redbrick
... port to digital form, and then retranslating them to line signals when sending them out on the other ports. – Possible to repeat signal between media segments that use different signaling techniques, such as 100BASETX/FX segments and 100BASE-T4 segments – Class II repeaters:- restricted to smaller t ...
... port to digital form, and then retranslating them to line signals when sending them out on the other ports. – Possible to repeat signal between media segments that use different signaling techniques, such as 100BASETX/FX segments and 100BASE-T4 segments – Class II repeaters:- restricted to smaller t ...