ECE 117-2426
... processing a large number of signals [2]. Each of nodes in this network is passes their data through the wireless network to a concentrator device. In the concentrator unit, all received data from each node is decoded and then will be sent to transfer unit. ...
... processing a large number of signals [2]. Each of nodes in this network is passes their data through the wireless network to a concentrator device. In the concentrator unit, all received data from each node is decoded and then will be sent to transfer unit. ...
Introduction - McMaster University > ECE
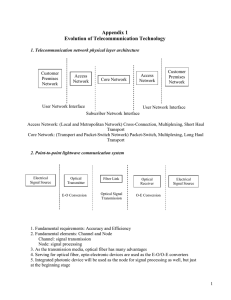
... (sampling rate 8000/s, 8-bit coding) at 64Kb/s named as Digital Signal level 0 (DS0). A frame is defined as the time length required for a single sample: 125s, therefore, a DS0 frame contains 8 bits or 1 byte. TDM: At the User-to-Network Interface (UNI) where the user signal (64Kb/s data stream org ...
... (sampling rate 8000/s, 8-bit coding) at 64Kb/s named as Digital Signal level 0 (DS0). A frame is defined as the time length required for a single sample: 125s, therefore, a DS0 frame contains 8 bits or 1 byte. TDM: At the User-to-Network Interface (UNI) where the user signal (64Kb/s data stream org ...
Network Forensics Tracking Hackers Through Cyberspace.
... physical description so that you know what to look for 2. For clients, identify the WAP that the station is associated with (by SSID) ...
... physical description so that you know what to look for 2. For clients, identify the WAP that the station is associated with (by SSID) ...
Computer Networks - E-Resources
... Metropolitan area network - This is a larger network that connects computer users in a particular geographic area or region. For example a large university may have a network so large that it may be classified as a MAN. The MAN network usually exist to provide connectivity to local ISPs, cable TV, o ...
... Metropolitan area network - This is a larger network that connects computer users in a particular geographic area or region. For example a large university may have a network so large that it may be classified as a MAN. The MAN network usually exist to provide connectivity to local ISPs, cable TV, o ...
GSC-16 PowerPoint Template
... Highlight of Current Activities Standardization about Home Networking (HN) in Japan ...
... Highlight of Current Activities Standardization about Home Networking (HN) in Japan ...
powerpoint
... • There are lots of different views of a network – System Area Network (computers in the same room) – Local Area Network (computers in the same building) – Wide Area Network (computers on the same planet) ...
... • There are lots of different views of a network – System Area Network (computers in the same room) – Local Area Network (computers in the same building) – Wide Area Network (computers on the same planet) ...
r01
... • Positive transition for 0, negative for 1 • Transition every cycle communicates clock (but need 2 transition times per bit) • DC balance has good electrical properties ...
... • Positive transition for 0, negative for 1 • Transition every cycle communicates clock (but need 2 transition times per bit) • DC balance has good electrical properties ...
Link Layer - Instituto Tecnológico de Morelia
... control, etc – extracts datagram, passes to upper layer at receiving side ...
... control, etc – extracts datagram, passes to upper layer at receiving side ...
Low-Power DoS Attacks in Data Wireless LANs and Countermeasures
... Sharing sensed data Military: Data/Video streaming from UAV, multicasting of command decisions ...
... Sharing sensed data Military: Data/Video streaming from UAV, multicasting of command decisions ...
Data Communications and Computer Networks
... Instead of creating each protocol in isolation, protocols are designed in complete, cooperative sets called suites or families ...
... Instead of creating each protocol in isolation, protocols are designed in complete, cooperative sets called suites or families ...
Mr. Atif_Kamal_P2P Routing Algorithms
... Security of data in an environment with heterogeneous trust Anonymity, deniability and resistance to censorship ...
... Security of data in an environment with heterogeneous trust Anonymity, deniability and resistance to censorship ...
Document
... There are alternative channels between nodes. Several nodes can transmit at a time and data can be redirected when some channels are busy. The extra cabling makes this an expensive type of network to set up but it is very robust. CS Topic 4 - Networks v2 ...
... There are alternative channels between nodes. Several nodes can transmit at a time and data can be redirected when some channels are busy. The extra cabling makes this an expensive type of network to set up but it is very robust. CS Topic 4 - Networks v2 ...
CSC311_UNIT1_Part2
... router) has a pair of addresses (logical and physical) for each connection. In this case, each computer is connected to only one link and therefore has only one pair of addresses. Each router, however, is connected to three networks (only two are shown in the figure). So each router has three pairs ...
... router) has a pair of addresses (logical and physical) for each connection. In this case, each computer is connected to only one link and therefore has only one pair of addresses. Each router, however, is connected to three networks (only two are shown in the figure). So each router has three pairs ...
Chapter two - UniMAP Portal
... switching nodes. • Switching nodes do not concern with content of data. Their purpose is to provide a switching facility that will move the data from node to node until they reach their destination (the end device). • A collection of nodes and connections forms a communications network. • In a switc ...
... switching nodes. • Switching nodes do not concern with content of data. Their purpose is to provide a switching facility that will move the data from node to node until they reach their destination (the end device). • A collection of nodes and connections forms a communications network. • In a switc ...
ppt - Carnegie Mellon School of Computer Science
... What distinguish different types of networks? » The services they provide What distinguish the services? » Rich of the services ...
... What distinguish different types of networks? » The services they provide What distinguish the services? » Rich of the services ...
15-LANOverview8
... optical fiber may be used out to 500m physically star, logically bus transmission from a station seen by all others if two stations transmit at the same time have a ...
... optical fiber may be used out to 500m physically star, logically bus transmission from a station seen by all others if two stations transmit at the same time have a ...
radio frequency identification based smart security
... independent mobile nodes that can transmit information to each other via radio waves. The nodes with in an radio range can directly transmit an information whereas others need the aid of intermediate nodes to route their packets. These networks are It is a fully distributed network and can work at a ...
... independent mobile nodes that can transmit information to each other via radio waves. The nodes with in an radio range can directly transmit an information whereas others need the aid of intermediate nodes to route their packets. These networks are It is a fully distributed network and can work at a ...
Ethernet - GITAM University
... TCP (Transmission Control Protocol) is the main transport protocol utilized in IP networks. The TCP protocol exists on the Transport Layer of the OSI Model. • The TCP protocol is a connection-oriented protocol which provides end-to-end reliability. • Internet protocol is the set of techniques used b ...
... TCP (Transmission Control Protocol) is the main transport protocol utilized in IP networks. The TCP protocol exists on the Transport Layer of the OSI Model. • The TCP protocol is a connection-oriented protocol which provides end-to-end reliability. • Internet protocol is the set of techniques used b ...
Lecture 20
... seldom used on low bit-error link (fiber, some twisted pair) wireless links: high error rates • Q: why both link-level and end-end reliability? 5: DataLink Layer ...
... seldom used on low bit-error link (fiber, some twisted pair) wireless links: high error rates • Q: why both link-level and end-end reliability? 5: DataLink Layer ...
chord - CSE, IIT Bombay
... that increase linearly with the number of keys • Association of keys with Virtual Nodes Makes the number of keys per node more uniform and Significantly improves load balance • Asymptotic value of query path length not affected much • Total identifier space covered remains same on average • Worst-ca ...
... that increase linearly with the number of keys • Association of keys with Virtual Nodes Makes the number of keys per node more uniform and Significantly improves load balance • Asymptotic value of query path length not affected much • Total identifier space covered remains same on average • Worst-ca ...