* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Securing rendezvous process in PURSUIT
Asynchronous Transfer Mode wikipedia , lookup
Computer network wikipedia , lookup
Computer security wikipedia , lookup
Wireless security wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Wake-on-LAN wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Network tap wikipedia , lookup
Airborne Networking wikipedia , lookup
Distributed firewall wikipedia , lookup
Packet switching wikipedia , lookup
Deep packet inspection wikipedia , lookup
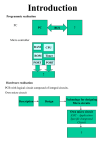
Security: Packet Level Authentication and Pub/Sub Security Solution Dr. Dmitrij Lagutin Helsinki Institute for Information Technology (HIIT) 4.10.2011 Contents • Security goals in a clean slate publish/subscribe network • Packet Level Authentication (PLA) • Securing rendezvous process in PURSUIT • Conclusions Security goals in a clean slate publish/subscribe network • We want to avoid problems of the original Internet, security should be considered in every part of the network design from the start – Identifiers, rendezvous, forwarding, etc. – Attacker can be anywhere in the network • Basic security goals for the network – Availability, unwanted traffic should be prevented on all levels, as close to the source as possible – Integrity – Reasonable trade-off between privacy and accountability – Scalability Security goals in a clean slate publish/subscribe network • Clean slate publish/subscribe approach makes security somehow easier compared to IP – Self-certifying identifiers – Authenticity and integrity of the publication can be independently verified • Publish and subscribe operations instead of connections – Receiver, instead of the sender, is in control – No data should be transmitted without an explicit subscription Contents • Security goals in a clean slate publish/subscribe network • Packet Level Authentication (PLA) • Securing rendezvous process in PURSUIT • Conclusions Packet Level Authentication (PLA) • Traditional end-to-end solutions such as IPSec and HIP do not offer enough protection, they are not effective if the network infrastructure is attacked and is unable to deliver packets • Capability-based solutions (SIFF, TVA, Fastpass) establish a single protected path in the network – Require state in routers – Not effective if some packets take alternative paths • There is a clear need for hop-by-hop security solution, where security policies can be enforced at every hop in the network Packet Level Authentication (PLA) • PLA is a novel method for providing availability on the network layer – Originally PLA was designed for IP networks, however it can be used with any network layer protocol • Good analogy is a paper currency: authenticity of the paper bill can be verified using built-in security measures (watermark, hologram, etc..) – Similarly, PLA allows any node to independently verify authenticity and validity of any packet Packet Level Authentication (PLA) • Sender adds an own header to packets, containing sender’s cryptographic identity, certificate from the trusted third party, signature over the packet and other fields – Using this information, intermediate nodes can verify integrity and authenticity of the traffic – Is the packet original and unique? – Has it been sent by an authorized sender? • PLA header is added on top of the network layer (e.g., IP) header – PLA is transparent to higher layer protocols and can be used with other security solutions such as IPSec and HIP PLA: Header • PLA offers two levels of protection – Cryptographic signatures provide integrity protection on the network layer – Trust management system provides accountability, and allows removal of malicious nodes from the network • All users in the network are authorized by trusted third parties PLA Header PLA Header • Signature by sender's private key together with a sender's public key are used to check authenticity of the packet • Trusted third party (TTP) authorizes the sender through the certificate • Timestamp is used to detect delayed packets which may be a sign of a replay attack • Monotonically increasing sequence number is used to detect duplicated packets PLA: Trusted Third Parties • Simply signing packets is not enough by itself – Attacker may generate a large amount of identities • Trusted Third Party (TTP) provides higher layer protection – Authorizes the user's public key, i.e., permission to use the network – Binds cryptographic identity with a real identity – Allows more efficient trust management, no need to trust in individual users, trusting in a TTP is enough in most cases – Various organizations (operator, company, country) may have an own TTP PLA: Trusted Third Parties • TTP certificates use standard certificate format with rights, validity time, and so on • TTP certificate types – Normal traffic certificate, short validity time (hours or minutes) – Priority certificate, for network management and authorities – Signalling certificate, limited rights, long validity time (years) – Self-signed certificate, used in the very beginning of the bootstrapping phase PLA: Cryptographic solutions and performance • PLA uses elliptic curve cryptography (ECC) due to its compact keys – 163-bit ECC key is as strong as 1024-bit RSA key – The total size of the PLA header is about 1000 bits • A dedicated hardware is necessary for verifying signatures at wire speed – FPGA based proof-of-concept accelerator can perform 166,000 verifications per second – Hardcopy based 90 nm ASIC can verify 850,000 packets/s, corresponding to 5 Gbps of average traffic – Power consumption is only 26 μJ/verification (less than the cost of wireless communication) PLA: Cryptographic solutions and performance • Worldwide bandwidth consumption was 21,367 PB per month in 2010 – If we assume: 4,650 bits per packet, 12 hops per route – Then signing and verifying every packet at every hop in the Internet using Hardcopy ASIC would consume about 4.5 MW of power (output of a large wind turbine) • 65 nm ASIC with some optimization produces significantly better performance and power consumption – 1.12 mm2 block running at 600 MHz, can perform 195,000 verifications with a power consumption of 500 mW => 2.56 μJ/verification – Power consumption of cryptographic operations would drop to 450 kW for the whole Internet PLA: Other applications • Having strong per-packet signatures allows PLA to be used for several other applications • Sequence number can be used for secure per-packet and per-bandwidth billing • Securing higher level protocols such as MIH (media independent handover) without excessive signalling • Controlling incoming connections, no data connection can be established without an explicit permission from the receiver • Good balance between a privacy and accountability without extensive data retention by operators PLA: Wireless authentication • User authentication and roaming, especially useful in wireless networks, for example: – Network bootstrapping messages are protected by PLA. Base stations would check if the user is authorized by a trusted TTP (e.g. Aalto's TTP) – Authentication is done at the bootstrapping phase. Afterwards, a symmetric session key can be used to secure further traffic. • No manual intervention, such as entering passwords or credit card information, is needed from users • No signalling to the external authentication server is necessary if the TTP is known by the base station Contents • Security goals in a clean slate publish/subscribe network • Packet Level Authentication (PLA) • Securing rendezvous process in PURSUIT • Conclusions Securing the rendezvous process in PURSUIT • Main concepts revisited – Publisher creates the publication, which is delivered to the subscriber – Data source serves the publication – Scopes control how publications are disseminated – Rendezvous system serves scopes, data sources and subscribers • Data source and publisher are often the same entity • Self-certifying (P:L) identifiers for Rid and Sid Securing the rendezvous process in PURSUIT Securing the rendezvous process in PURSUIT • Goal: protect the data source and rendezvous system from unwanted traffic • Rendezvous signalling messages are protected by PLA • Standard certificates between various parties are used, in the following example: – CX denotes the certificate from the access network the to the subscriber (permission to use the network and a proof of a topological location) – CY denotes a similar certificate given to the data source Securing the rendezvous process in PURSUIT Securing the rendezvous process in PURSUIT • 0. Scope and data source mutually authenticate each other (to host publication <Sid:Rid>) • 1. Publication is published by the data source • 2. & 3. Subscriber receives data source's location with all relevant certificates from the rendezvous system • 4. Subscription request is sent towards the data source with all relevant certificates • 5. Publication is transmitted Securing the rendezvous process in PURSUIT • Using certificates included in the subscription messages, intermediate nodes can verify that: – Subscriber and data source are valid entities in the network – Subscriber wants to receive the publication – Data source has been authorized by the scope and is willing to host the publication – Optionally: subscriber has a right to request the publication • Invalid subscription requests are dropped before they reach the data source Securing the rendezvous process in PURSUIT • ECC allows inclusion of full keys in Rid/Sids – Less bandwidth overhead • Fully independent verification of rendezvous and subscription messages – Access control is also supported • The network can easily limit the amount of allowed rendezvous or subscription messages – Protects the rendezvous system and data sources • zFilters can be used to prevent DoS attacks on the forwarding layer Conclusions • A good network layer security is necessary in addition to the end-to-end security • PLA is novel security solution for providing availability on the network layer – Allow independent verification of packets – Suitable for different kinds of networks (IP, PURSUIT, etc.) • Main security components of PURSUIT – Self-certifying identifiers – Securing rendezvous process through certificates and PLA – Forwarding security through zFilters References • D. Lagutin. Securing the Internet with Digital Signatures, Doctoral dissertation. – http://lib.tkk.fi/Diss/2010/isbn9789526034652/ – Overview of the PLA • D. Lagutin and S. Tarkoma. Cryptographic signatures on the network layer - an alternative to the ISP data retention, ISCC 2010. – http://ieeexplore.ieee.org/xpl/freeabs_all.jsp?arnumber=5546745 – Using PLA to achieve balance between security and accountability, removing the need for extensive data retention • D. Lagutin, et al. Roles and security in a publish/subscribe network architecture, ISCC 2010. – http://ieeexplore.ieee.org/xpl/freeabs_all.jsp?arnumber=5546746 – Security solution for a clean-slate publish/subscribe network