* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Structure of Operating Systems
MTS system architecture wikipedia , lookup
Burroughs MCP wikipedia , lookup
Plan 9 from Bell Labs wikipedia , lookup
Distributed operating system wikipedia , lookup
Security-focused operating system wikipedia , lookup
Copland (operating system) wikipedia , lookup
Spring (operating system) wikipedia , lookup
Windows NT startup process wikipedia , lookup
Unix security wikipedia , lookup
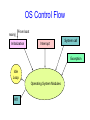
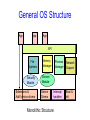
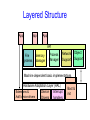
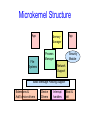
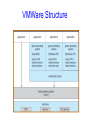
Operating System Structure Announcements • Make sure you are registered for CS 415 • First CS 415 project is up – Initial design documents due next Friday, February 2nd – Project due following Thursday, February 8th • Everyone should have access to CMS (http://cms3.csuglab.cornell.edu) – Check and contact me ([email protected]) or Bill Hogan ([email protected]) today if you do not have access to CMS • Also, everyone should have CSUGLab account – Contact Bill or I if you do not Review: Protecting Processes from Each Other • Problem: Run multiple applications in such a way that they are protected from one another • Goal: – Keep User Programs from Crashing OS – Keep User Programs from Crashing each other – [Keep Parts of OS from crashing other parts?] • (Some of the required) Mechanisms: – Dual Mode Operation – Address Translation (base/limit registers, page tables, etc) – Privileged instructions (set timer, I/O, etc) • Simple Policy: – Programs are not allowed to read/write memory of other Programs or of Operating System Review: Dual Mode Operation • Hardware provides at least two modes: – “Kernel” mode (or “supervisor” or “protected”) – “User” mode: Normal programs executed • Some instructions/ops prohibited in user mode: – Example: cannot modify page tables in user mode • Attempt to modify Exception generated • Transitions from user mode to kernel mode: – System Calls, Interrupts, Other exceptions Today’s Lectures • I/O subsystem and device drivers • Interrupts and traps • Protection, system calls and operating mode • OS structure • What happens when you boot a computer? Operating System Structure • An OS is just another kind of program running on the CPU – a process: – It has main() function that gets called only once (during boot) – Like any program, it consumes resources (such as memory) – Can do silly things (like generating an exception), etc. • But it is a very sophisticated program: – “Entered” from different locations in response to external events – Does not have a single thread of control • can be invoked simultaneously by two different events • e.g. sys call & an interrupt – It is not supposed to terminate – It can execute any instruction in the machine How do you start the OS? • Your computer has a very simple program pre-loaded in a special read-only memory – The Basic Input/Output Subsystem, or BIOS • When the machine boots, the CPU runs the BIOS • The BIOS, in turn, loads a “small” OS executable – From hard disk, CD-ROM, or whatever – Then transfers control to a standard start address in this image – The small version of the OS loads and starts the “big” version. • The two stage mechanism is used so that BIOS won’t need to understand the file system implemented by the “big” OS kernel • File systems are complex data structures and different kernels implement them in different ways • The small version of the OS is stored in a small, special-purpose file system that the BIOS does understand What does the OS do? • OS runs user programs, if available, else enters idle loop • In the idle loop: – OS executes an infinite loop (UNIX) – OS performs some system management & profiling – OS halts the processor and enter in low-power mode (notebooks) – OS computes some function (DEC’s VMS on VAX computed Pi) • OS wakes up on: – interrupts from hardware devices – traps from user programs – exceptions from user programs OS Control Flow main() From boot Initialization Interrupt System call Exception Idle Loop Operating System Modules RTI Operating System Structure • Simple Structure: MS-DOS – Written to provide the most functionality in the least space – Applications have direct control of hardware • Disadvantages: – Not modular – Inefficient – Low protection or security General OS Structure App App App API File Systems Security Module Extensions & Add’l device drivers Memory Manager Process Manager Network Support Service Module Device Drivers Interrupt handlers Monolithic Structure Boot & init Layered Structure • OS divided into number of layers – bottom layer (layer 0), is the hardware – highest (layer N) is the user interface – each uses functions and services of only lower-level layers • Advantages: – Simplicity of construction – Ease of debugging – Extensible • Disadvantages: – Defining the layers – Each layer adds overhead Layered Structure App App App API File Systems Memory Manager Process Manager Network Support Object Support Machine dependent basic implementations Hardware Adaptation Layer (HAL) Extensions & Device Interrupt Add’l device drivers Drivers handlers Boot & init Microkernel Structure • Moves as much from kernel into “user” space • User modules communicate using message passing • Benefits: – Easier to extend a microkernel – Easier to port the operating system to new architectures – More reliable (less code is running in kernel mode) – More secure – Example: Mach, QNX • Detriments: – Performance overhead of user to kernel space communication – Example: Evolution of Windows NT to Windows XP Microkernel Structure App File Systems Memory Manager Process Manager App Security Module Network Support Basic Message Passing Support Extensions & Add’l device drivers Device Drivers Interrupt handlers Boot & init Modules • Most modern OSs implement kernel modules – Uses object-oriented approach – Each core component is separate – Each talks to the others over known interfaces – Each is loadable as needed within the kernel • Overall, similar to layers but with more flexible • Examples: Solaris, Linux, MAC OS X UNIX structure Windows Structure Modern UNIX Systems MAC OS X Virtual Machines • Implements an observation that dates to Turing – One computer can “emulate” another computer – One OS can implement abstraction of a cluster of computers, each running its own OS and applications • Incredibly useful! – System building – Protection • Cons – implementation • Examples – VMWare, JVM VMWare Structure But is it real? • Can the OS know whether this is a real computer as opposed to a virtual machine? – It can try to perform a protected operation… but a virtual machine monitor (VMM) could trap those requests and emulate them – It could measure timing very carefully… but modern hardware runs at variable speeds • Bottom line: you really can’t tell! Modern version of this question • Can the “spyware removal” program tell whether it is running on the real computer, or in a virtual machine environment created just for it? – Basically: no, it can’t! • Vendors are adding “Trusted Computing Base” (TCB) technologies to help – Hardware that can’t be virtualized – We’ll discuss it later in the course





















![[Lecture 1, part 3] Kernel interaction with the hardware: Interrupt](http://s1.studyres.com/store/data/014183875_1-7af0f6b03bedcfbf8972c6054b446a98-150x150.png)








