* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Securing Cyber Space: Safeguarding Access to Critical Resources Peter Hager, CEO
Survey
Document related concepts
Transcript
Securing Cyber Space: Safeguarding
Access to Critical Resources
Peter Hager, CEO
Earl Rasmussen, President
Vanguard Security and Compliance Conference
June 25, 2012
Net‘Q brings Security into the Net
Copyright Net`Q GmbH, 2000-2012
Page 0
Agenda
Changing Environment
Mainframes, the Internet, the Cloud
Increased Security Threats
Security Cases
Impact
Solutions
Summary
Copyright Net`Q GmbH, 2000-2012
Page 1
Role of Mainframes
Over 70% of World’s Critical information
Major Industry/Government reliance:
Finance
Energy
Retail
Telecommunications
Transportation
Government
Cloud Computing Environment
Copyright Net`Q GmbH, 2000-2012
Page 2
Role of Mainframes
70 percent of all corporate data and 75 percent of
all business logic still resides on mainframe
Executing nearly 30 billion transactions a day
valued at over $1 trillion a week
Running $30 trillion of applications
73 Percent of Organizations confirm that the
Mainframe is part of their Cloud Computing
Strategy
Over 60% of World-wide WAN Traffic is SNA
Based
Copyright Net`Q GmbH, 2000-2012
Page 3
Millions invested in protecting mainframes
Yet …..
Estimates are that 90% of mainframes
worldwide are insecure
And ….
Nearly 95% are interconnected
Copyright Net`Q GmbH, 2000-2012
Page 4
Increased Security Threats
“New technologies that enhanced the availability of SNA
with more dynamic network recovery and the use of the
faster IP infrastructure has “opened” the SNA networking
environment. “
“Organized crime and unorthodox governments have the
resources to hire career IT criminals that have the
sophistication to attack a SNA network in order to find a big
prize.”
Source: “Securing an SNA Environment for the 21st century”, White Paper, IBM, 2008
Copyright Net`Q GmbH, 2000-2012
Page 5
2011 Breaches Continue to Grow
Incidents skyrocketed to over 174 million records
94% of Data breaches on servers
58% of Breaches Involved activist groups
98% of Breaches from external agents
81% of Breaches involved hacking
69% of Breached records involved malware
92% of Breaches were discovered by third parties
Source: Verizon 2012 Data Breach Investigation Report
Copyright Net`Q GmbH, 2000-2012
Page 6
Small-Medium Business
Targeted
Over 55% of SMB experienced fraud attacks.
50% experienced multiple incidents.
80% of attacks were undetected by the bank.
87% failed to recover from lost funds.
40% of those compromised changed banks.
Only 30% of SMBs feel banks are adequately safeguarding
their accounts.
Source: Guardian Analytics and Ponemon Institute
Copyright Net`Q GmbH, 2000-2012
Page 7
Cyber Crime Targets
Banking and Finance
Hospitality
Retail
Manufacturing
Government
Telecommunications
Health Care
Energy
Copyright Net`Q GmbH, 2000-2012
Page 8
The Risk – Are You Safe?
There are two types of companies: Those that have been
hacked and those that have been hacked but do not know it!!
Bank of Scotland
TJX
Google
Adverse Economic Impacts
HBGary
Heartland Payment Systems
Loss of Sensitive Data
Health Net
DuPont
Compromised Intellectual property
RSA Security
Privacy Invasion and Personal Data Theft
Legal Implications
Global Payments
Reduced Trust and Confidence
Sony
Copyright Net`Q GmbH, 2000-2012
E-Trade
Bank of America
Epsilon
LinkedIn
Monster.com
WordPress
Hannaford Bros.
Page 9
New “Flame” Cyber Weapon
Kaspersky Labs have
uncovered a massive
cyber threat
Creators of the virus
used a network of some
80 servers across Asia,
Europe and North
America to remotely
control infected
machines
Copyright Net`Q GmbH, 2000-2012
Page 10
Codename
Worm.Win32.Flame
Copyright Net`Q GmbH, 2000-2012
Page 11
Did you ever hear about new codename
Worm.Z.Frame?
Copyright Net`Q GmbH, 2000-2012
Page 12
Documented Hacking Cases
We have documented cases of security violations
which have occurred in the mainframe environment
They have caused unauthorized viewing of data, free
access to databases, unauthorized access to
applications, and prolonged outages
Copyright Net`Q GmbH, 2000-2012
Page 13
Security Cases
Security Case 19 – Hijacking
Security Case 20 – Malicious Software
Security Case 21 – Rogue Intermediate Network
SNA Switches
Hacker-to-Go
Copyright Net`Q GmbH, 2000-2012
Page 14
Security Environment
Large Institutions
Multiple External Connections
IP Sec (to external connections)
IP Firewall
SSL Encryption
RACF
Single Sign-On
Secure ID Cards
Copyright Net`Q GmbH, 2000-2012
Page 15
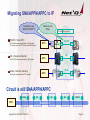
Migrating SNA/APPN/APPC to IP
Networks see
IPSec
Applications see
SNA/APPN/APPC
TN3270 - Telnet 3270
3270 data streams encapsulated in TCP packets.
TN- server converts TCP Packets with SNA Packets.
IP-HDR
TN
Server
APPL
Encypted Data
TN3270
IP@
IP@
EE
EE - Enterprise Extender
SNA (HPR) frame encapsulated in UDP packets
APPL
VIP@
APPL
IP@
VIP@
DLSw
DLSw - Data link switching
SNA frame encapsulated in TCP packets
IP@
Circuit is still SNA/APPN/APPC
DLSw
APPL
Copyright Net`Q GmbH, 2000-2012
EE
EE
EE
TN3270
SNA-Circuit
Page 16
IP Encrypting SNA data
DLSw
APPL
EE
EE
EE
TN3270
Circuit
Circuit is still SNA/APPN/APPC
Positive
SNA packets are encrypted when transported between IP addresses
Negative
SNA packets are encrypted when transported between IP addresses
SNA packets appear unencrypted at SNA/APPN/APPC nodes
Content of SNA Packets appear unencrypted to applications
IP based firewalls have no control over SNA activities
Copyright Net`Q GmbH, 2000-2012
Page 17
Migrating SNA Summary
SNA Hardware Devices disappeared
NCP, 3745, 3174, 3600 and many more …
Peripheral Terminal became Applications.
Most of the legacy Applications still exist and are running
( IMS, CICS, TSO, TSO, RACF, JES, NetView )
VTAM API interfaces have not changed.
Copyright Net`Q GmbH, 2000-2012
Page 18
Copyright Net`Q GmbH, 2000-2012
Page 19
Copyright Net`Q GmbH, 2000-2012
Page 20
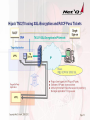
Hijack TN3270 SSL-Encrypted Connection
?
Switch at the right moment
Telnet Server
Target Application
Rogue
3rd Party
Application
Innocent
APPL
Switch
APPL
Telnet Server
Rogue
APPL
One of many good moments to switch is shortly before the target application
times out. Idle time is easy to monitor and calculate by third party application
1. Send timeout message to innocent user before target application
times out
2. Switch to rogue user
3. In case innocent user logs on again, switch back to innocent user
4. Activity of rogue user will avoid timeout at target application
Copyright Net`Q GmbH, 2000-2012
Page 21
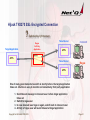
Malicious Software
Telnet Server
Rogue
3rd Party
Application
Target Application
Innocent
APPL
Switch
APPL
1, 2
3, 4
Copy of Rogue
3rd Party
Application
1. A customer who experienced Hijacking found suspicious files on several mainframes.
These suspicious files independently started sessions to other applications.
2. After in-depth analysis the customer discovered that the suspicious files were
‘replications’ of the same type.
3. In a test project they tested how successful ‘harmless replicated files’ could be
distributed. The result after one weekend was 500 replicates at 20 different networks.
Copyright Net`Q GmbH, 2000-2012
Page 22
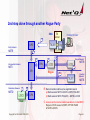
Rogue Intermediate Network - 1st step to get more …
SNA
1
TN
Server
Innocent User
CPE
Entry Network:
NETE
2
3
4
Intermediate Network:
CPI
NETI
CPIx
Rogue
Destination Network:
NETD
5
1.
2.
3.
4.
6
CPX
Real
Copyright Net`Q GmbH, 2000-2012
5.
6.
Initself TNLU001 - LUCICS
Send Search / Locate to CPI
CPI finds LUCICS inside NETI
Logon Exit driven in Rogue LUCICS
Logon exit of Rogue application sends
both partner names to another rogue
location. There are several ways to do:
FTP, Email info or IN$FILE.
Rogue LUCICS issues CLSDST,
OPTCD=PASS to NETD.LUCICS
Logon to real LUCICS completes
successfully
Page 23
2nd step done through another Rogue Party
SNA
1
TN
Server
Innocent User
CPE
Entry Network:
NETE
2
3
4
5
Rogue Network:
NETR
CPIx
Intermediate Network:
Ra
NETI
CPI
Rogue
Rb
Spoofed
Network:
NETE
Destination Network:
7
6
R. Remote location starts up two applications and
NETD
CPX
Real
a) Starts session NETR.LUCICS - NETE.TNLU001
b) Starts session NETE.TNLU001 – NETD.LUCICS
5. As soon as the remote location was able to contact NETI,
Rogue LUCICS issues CLSDST, OPTCD=PASS
to NETR.LUCICS
Copyright Net`Q GmbH, 2000-2012
Page 24
Rogue Intermediate Network,
what another Rogue Party can do ..
Spoofed
Rogue
NETE
NETR
Real
NETE
Telnet Server
Innocent
Telnet Server
Rogue
Switch
Real
TNLUXXX
Switch in Spoofed NETE.TNLU001 can Hijack like reported in Violation Case 19-3
RACF in real z/OS does not recognize it gets spoofed
IP based firewall does not recognize this attack
APPN-EE Firewall protects, as it is being able to check authentication of CP-CP connections
and it is discovering insufficient security definitions
Copyright Net`Q GmbH, 2000-2012
Page 25
Rogue Intermediate Network,
what another Rogue Party can do ..
Spoofed
Rogue
NETE
NETR
ATM, Terminal
Real
Entry
Network
Innocent
Printer
3270, TelNet3270,
TPX, NVAS …
Printer
APPC, MQ-Series,
CICS, IMS, DB2
Rogue Scripts
Real
Rogue
APPL
Rogue Scripts and Programs inside NETR.LUCICS
can be hacked selectively.
All sessions sending search/locates through Intermediate Network NETI Regardless from which
Entry Network to real LUCICS they are coming through. fe. NETE1, NETE99 …
Possible attacks:
a) Hijack authenticated sessions
b) Copy data,
c) modify data
d) spy for events
e) denial of service
Copyright Net`Q GmbH, 2000-2012
Page 26
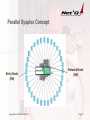
Parallel Sysplex Concept
Entry Node
(EN)
Copyright Net`Q GmbH, 2000-2012
Network Node
(NN)
Page 27
SNA Switching
Local Router
NN
EN
NN
....
NN
DLSw
NN
EN
EN
EN
EN
EN
EN
AS-400 z/OS
Extends Parallel Sysplex to the Desktop
Un-Authenticated CP-CP Sessions
Enables Encrypted Open Access to Core Mainframe
Copyright Net`Q GmbH, 2000-2012
Page 28
Hacker-to-Go …
Plug to any Laptop or PC
*** Legally Free Software ***
Develop & Test VTAM Applications.
TSO - H-Assembler - LinkEdit - VTAM plus Web and FT access
*** Downloadable z/OS Software from Internet available ***
z/OS 1.10 including APPN Crossnet and RACF and
REXX IP much more …
Both versions need just 8 GB USB stick
Copyright Net`Q GmbH, 2000-2012
Page 29
Logon User Data
Up to 255 bytes
Created by application code or entered by terminal users
Transmitted within the logon flows
Provided by Communication Servers to Applications in clear text
Can contain any text string including USERID, PWD, PIN CODES,
Social security IDs or other sensitive data
Often there was no security policy existing when legacy applications
were originally designed
Pertains to all types of SNA sessions
Copyright Net`Q GmbH, 2000-2012
Page 30
User Data carried on logon flows
EE
Comm
Server
CP-CP Circuit
Comm
Server
EE
EE
CP-CP Circuit
CP-CP Circuit
Comm
Server
APPL1
APPL2
CP-CP Circuit
CDRM-CDRM Circuit
APPL3
Logon User Data
Included inside the logon flows search/locates and provided to applications
Distributed intra and cross LPAR, cross DLSw ( SNASw ), cross MS HIS
Searches can distribute user data to external networks / applications
ADJCP and ADJSSCP tables of Comm Server define search order
Original Comm Server has no control over how adjacent servers search
Start Parameter SNVC of original Comm Server defines search depth
Copyright Net`Q GmbH, 2000-2012
Page 31
User Data transported inside BIND
APPL
LU-LU Circuit
APPL
Bind User Data
Up to 65 bytes
Created by application code
Carried within the SNA BIND command and delivered to partner applications
Provided by Communication Servers to Applications in clear text
User Data is carried crossnet if search locate found the partner there.
Copyright Net`Q GmbH, 2000-2012
Page 32
User Data transported inside BIND to TN3270E
APPL
LU-LU Circuit
Telnet
Server
Check:
IP@, Telnet, SSL
Bind User Data
TN3270 server provides User Data to TN3270 client ( RFC 1647 )
User Data is provided in clear text to TN3270 client
IP based firewall has no control over user data, because telnet server
encrypts IP data packets.
Copyright Net`Q GmbH, 2000-2012
Page 33
Observation 1, providing UID & PWD
A large financial organization.
We have found applications transmitting USERID and PASSWORD as User Data, of
which many of them were of privileged users / administrators.
In a conference call, network team assured that this was just inside their own
network.
Closer analysis of recordings revealed that USERIDs and PASSWORDs were
distributed to other networks.
In some cases USERIDs and PASSWORDs were received from a third party CP
which did not have direct a CP-CP connection.
Copyright Net`Q GmbH, 2000-2012
Page 34
Observation 2, Injection
Another large financial organization.
Hackers were sending in User Data inside Logon requests in the form of an
inquiry such as: INQ userid opt=PWD|PIN|SSID
An exit of the destination APPL reacted by sending the WWD|PIN|SSID included
in the BIND command back.
Closer analysis of recordings showed USERIDs and PASSWORDs were
distributed to other networks.
In some cases USERIDs and PASSWORDs were received from third party
Gateways which did not have direct a CP-CP connection.
Copyright Net`Q GmbH, 2000-2012
Page 35
User Data – Security Considerations
Be aware of the Transmission of sensitive Information
Ensure Security Policy Compliance
Coordinate between System, Security, Risk, and Business
Review Policies for USERDATA and applications using USERDATA
Collect, Record, and Analyze USERDATA
Monitor and Manage use of USERDATA
Re-evaluate Periodically Security Risks and Implications
Single Sign-on and Secure ID Cards may solve the USERID/PASSWORD
problem
Copyright Net`Q GmbH, 2000-2012
Page 36
What can hackers do?
Identification Theft
Data Theft and Modification
Fraudulent Transactions
Monitor Real-Time Data Flow
Malicious Software / Malware Intrusion
Activities recorded as authorized user/application
Copyright Net`Q GmbH, 2000-2012
Page 37
Neutralizes Security Investments
IP Firewalls
Encryption
Secure ID cards
Single Sign-on with changing passwords
RACF Pass Ticket
RACF/TSS/ACF2 will not recognize
Copyright Net`Q GmbH, 2000-2012
Page 38
APPN-EE Firewall
Components
Base Package
Host Part
Net-Examine
Optimization
VTAM Security Generator
RACF/ACF2/TSS Security Generator
VTAM Performance Generator
Compliancy
Corporate Compliancy
Sarbanes-Oxley Compliancy
NIST Compliancy
Client / Master
MASTER Set Handler
CLIENT Functions
Suites
Corporate Compliance Suite
Sarbanes-Oxley Compliance Suite
NIST Compliance Suite
Copyright Net`Q GmbH, 2000-2012
Page 39
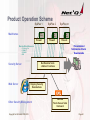
Product Operation Scheme
Mainframes
SysPlex 1
SysPlex 2
Sys
Cons
Sys
Cons
Firewall
Firewall
SysPlex nn
Sys
Cons
Firewall
Remote Virtual Resources
•
•
•
•
Precustomized
Net-Examine Clients
Downloadable
FW Config File
VTAMLST
PARMLIB
SMF
Net-Examine Suite
+ Add-on Functions
Security Server
Web Server
Ongoing Security
Examinations
Other Security Management
Copyright Net`Q GmbH, 2000-2012
NetView
Tivoli zSecure Suite
VanGuard
Page 40
US Financial Industry Findings
Copyright Net`Q GmbH, 2000-2012
Page 41
Administrate SNA Firewall
Both, Security and Network Team needs to agree on any changes
Get for more info at: http://www.net-q.com/ssl/NetQRuleChangeProcess2.html
Copyright Net`Q GmbH, 2000-2012
Page 42
LUCK checks Conditions for 3rd Parties
RACF
SNA
TN3270 SSL Encryption in IP Network
Check:
IP@, Telnet, SSL
Target Application
TN
Server
APPL
I
P
@
IP
Single
Sign-on
Innocent
I
P
@
2
1
LUCK
Same day, while innocent user‘s session is active
1. Check condition to start session to PLU
99% of chance to activate session from LUCK
2. Check condition to start session to SLU
No chance while TN Server LU is in session with Target Application
Copyright Net`Q GmbH, 2000-2012
Page 43
LUCK checks Conditions for 3rd Parties
RACF
SNA
TN3270 SSL Encryption in IP Network
Check:
IP@, Telnet, SSL
Target Application
APPL
X
TN
Server
I
P
@
IP
Single
Sign-on
Innocent
I
P
@
2
1
LUCK
When Innocent User logged off
2. Good % of chance to activate session from LUCK
Reports successful
Copyright Net`Q GmbH, 2000-2012
Page 44
LUCK informs other applications
RACF
SNA
TN3270 SSL Encryption in IP Network
Check:
IP@, Telnet, SSL
Target Application
APPL
X
TN
Server
I
P
@
IP
Single
Sign-on
Innocent
I
P
@
2
LUCK
When both PLU and SLU accept session
1. Update LUCK Status-Databases
2. Give Info to other 3rd parties (List congigurable)
o Same LPAR
o External LPAR in same SysPlex
o External LPAR in same Network
o External LPAR in other Network
Copyright Net`Q GmbH, 2000-2012
Page 45
LUCK Does . . .
Checks Status of Logical Units
Checks Connectivity to Logical Units using pregiven Logmodes/Bindimages within Network and
Cross Network
Establishes and immediately terminates Sessions
to PLU/SLU
Creates Security reports
Designed for large networks
Copyright Net`Q GmbH, 2000-2012
Page 46
LUCK Does Not . . .
Does not send or receive data on any session
Does not keep any sessions connected
Does not Acquire Resources except specially
requested
Does not only check TN3270 LU, it checks all LU
Copyright Net`Q GmbH, 2000-2012
Page 47
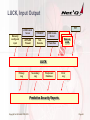
LUCK, Input Output
FTP
z/OS Comm
Server
VTAMLST
APPN-EE
Firewall
NetExamine
Manually
configured
input
z/OS CommServer
Trace files
External
LUCK
LUCK
Primary
Log
Secondary
Log
Postponed
Database
Error
Log
Predictive Security Reports
Copyright Net`Q GmbH, 2000-2012
Page 48
Predictive Security Report
5750
How many sessions would allow
3rd Man in middle attacks
Hijacked Sessions
Obsolete Secure ID cards like RMF
Obsolete RACF Pass Tokens
35822
Copyright Net`Q GmbH, 2000-2012
Page 49
Codename
Worm.Win32.Flame
Copyright Net`Q GmbH, 2000-2012
Page 50
Did you ever hear about new codename
Worm.Z.Frame?
Copyright Net`Q GmbH, 2000-2012
Page 51
New APIs make things easier
REXX
REXX
IP socket API
REXX
VTAM API
REXX
SAF API
REXX
SQL
REXX
UTIL ITIES
Others are available, list is not complete ...
- REXX language used for z/OS exits,
- Search Internet for others
- Check for homegrown REXX solutions
Copyright Net`Q GmbH, 2000-2012
Page 52
New API makes things easy
REXX VTAM socket API
This API function package eliminates the need of coding VTAM applications in Assembler
language. Basically this technology can be used with VTAM similar to coding mainframe exits
in REXX language. It enables the ability to code all interfaces to VTAM SNA, z/OS Console
and Trace capture in REXX language.
REXX IP socket API, provided by IBM with z/OS V1R7, ( since 2005 )
The sample programs and the jobs that you can use to run them are located in the
SEZAINST file. The following information applies to the batch jobs:
The batch job REXXAPI runs standalone socket EXECs and TCP/IP clients.
The batch job REXXAPIS runs TCP/IP servers.
The batch job REXXAPIT runs the subtask that is required to test the REXAPI04
program.
Copyright Net`Q GmbH, 2000-2012
Page 53
REXX VTAM socket API sample
Command ===>
Scroll ===> PAGE
000084 /* Open the ACB */
000085 Call NRXFVTAM 'OPEN_ACB',WKAR._ACB1._ADR_C /* result is RC from z/OS
000086 If result>0 Then Do; Say NRXF.0ERMSG; Exit; End
000087 Say 'ACB1 opened successfully.‘
000092 /* SETLOGON */
000093 TESTRPL1.0PARMLIST = 'OPTCD'
000094 TESTRPL1.0OPTCD
= 'SYN START’
000096 Call NRXFVTAM 'SETLOGON',WKAR._RPL1._ADR_C,'TESTRPL1.'
000097 If result='' Then Do; Say NRXF.0ERMSG; Exit; End
000098 If result<>0 Then Do; Say NRXF.0ERMSG; Exit; End
000099 Say 'SETLOGON is done. Feedback = 'NRXF.0FEEDBACK_X
000102 /* INQUIRE STATUS */
000104 Call NRXFMEM 'VALUE','WKAR._NIB1._NIBNET',left(netid,8)
000105 Call NRXFMEM 'VALUE','WKAR._NIB1._NIBSYM',left(luname,8)
000112 Call NRXFVTAM 'INQUIRE',WKAR._RPL1._ADR_C,'TESTRPL1.'
000113 If result='' Then Do; Say NRXF.0ERMSG; Exit; End
000114 If result<>0 Then Do; Say NRXF.0ERMSG; Exit; End
000115 Say 'INQUIRE STATUS is done. Feedback = 'NRXF.0FEEDBACK_X
Copyright Net`Q GmbH, 2000-2012
Page 54
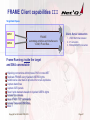
FRAME Client capabilities I
Target Addr Space
Client -Server connection
FRAME
automates activities and interfaces to
VTAM, IP and files . . .
Frame Running Outside the target
and only IP connectable
May be able to login using TN3270, WebSphere or SNA
if userid & password are known by one of the controlling servers
If ‘predefined’ userids & passwords
FRAME can access files and can do transactions based on the users
profile
Copyright Net`Q GmbH, 2000-2012
1. USER DATA transmission
2. IP connection
3. SNA/LEN/APPN connection
Tries to interconnect to
other servers/clients
whatever connection-type
is first successful
Remotely controlled by
external FRAME servers
External FRAME servers
receive captured
applications
Page 55
FRAME Client capabilities II
Target Addr Space
APPL1
APPL2
Client -Server connection
FRAME
automates activities and interfaces to
VTAM, IP and files . . .
1. USER DATA transmission
2. IP connection
3. SNA/LEN/APPN connection
Frame Running outside the target
and SNA connectable
Hijacking connections within/cross LPAR or cross NET
Replicate FRAME using hijacked USERID rights
Send/receive User data to provide info to new replicates
Capture data flows
Capture 3270 panels
Read /write datasets based on hijacked USERs rights
Acsess Sys console
Issue VTAM / TCP commands
Access Trace and CNM Data
More ..
Copyright Net`Q GmbH, 2000-2012
Page 56
FRAME Client capabilities III
Target Addr Space
APPL1
APPL2
Client -Server connection
FRAME
automates activities and interfaces to
VTAM, IP and files . . .
1. USER DATA transmission
2. IP connection
3. SNA/LEN/APPN connection
Frame Running inside the target
and SNA connectable
Hijacking connections within/cross LPAR or cross NET
Replicate FRAME using hijacked USERID rights
Send/receive User data to provide info to new replicates
Capture data flows
Capture 3270 panels
Read / write datasets based on hijacked USERs rights
Access Sys console
Issue VTAM / TCP commands
Access Trace and CNM Data
More ?
Copyright Net`Q GmbH, 2000-2012
Page 57
REXX Interpret Instruction
/* REX Base code */
Rc=rexint( file5, [Servers] )
Return 0
REXINT:
rexfile = arg(1)
Servers = arg(2)
If Servers = '‚ rc=(rexint_local)
Return 0
REXINT_LOCAL:
/* INTERPRET LOCAL FILE */
do while lines(rexfile)>0
line = linein(rexfile)
INTERPRET line
End
return
Copyright Net`Q GmbH, 2000-2012
Local File
/* REXX EZARXR02 */
src = socket("INITIALIZE","MYSET01",10);
if perror(src,"INITIALIZE") = 0 then do
src = socket("SOCKET","AF_INET6","STREAM");
if perror(src,"SOCKET") = 0 then do
parse var src l_retcode l_sockid
src = perror(socket("CLOSE",l_sockid),"CLOSE");
end; /* SOCKET */
end; /* INITIALIZE */
src =perror(socket("TERMINATE","MYSET01"),"TERMINATE");
exit 0;
/* Routine returns -1 if first word if arg 1 not zero */
perror: if word(arg(1),1) = 0 then return 0; else
Say arg(2) "Error : "arg(1);
return -1;
Page 58
Remote Code
Executing Locally
Remote Server Files
/*Open the ACB */
Call NRXFVTAM 'OPEN_ACB',WKAR._ACB1._ADR_C
If result>0 Then Do; Say NRXF.0ERMSG; Exit; End
Say 'ACB1 opened successfully.‘
/* SETLOGON */
TESTRPL1.0PARMLIST = 'OPTCD‘
TESTRPL1.0OPTCD
= 'SYN START’
Call NRXFVTAM 'SETLOGON',WKAR._RPL1._ADR_C,'TESTRPL
If result='' Then Do; Say NRXF.0ERMSG; Exit; End
If result<>0 Then Do; Say NRXF.0ERMSG; Exit; End
Say 'SETLOGON is done. Feedback = 'NRXF.0FEEDBACK_X
Multiple Remote servers searched for
files
Multiple Media types tried to connect
each server
Copyright Net`Q GmbH, 2000-2012
Page 59
Another way to run z/OS
Free Hercules z/OS Emulation
Search Google : Free Download Hercules Emulation
Free z/OS
Search Google: Free Download ibm adcd z/os 1.13
Warning: You may have already bought a license from IBM?
You can run z/OS either Windows, Linux or APPL platform
Free TN3270 emulation on Windows, Microsoft Mobile, IPad,
IPhone IBook, Blackberry or Android
REXX VTAM API downloadable from Internet
REXX IP Sockets API included in z/OS
Literature:
Search Google : REXX Language: A Practical Approach to Programming
Search Google : MVS TSO: Commands, CLIST & REXX
Copyright Net`Q GmbH, 2000-2012
Page 60
FLAME - FRAME Comparison
FLAME
FRAME
LUA
REXX
PCs connected to local LAN
Flash drives?
Bluetooth
Can record sounds and videos
Captures screenshot images
Log messaging conversations
Hijacking connections within/cross LPAR or cross NET
?
Replicate FRAME using hijacked USERID rights
?
Send/receive User data to provide info to new replicates
Capture data flows
Capture 3270 panels
?
Read / Write datasets based on hijacked USERs rights
Access Sys console
Issue VTAM / TCP commands at mainframe console
Programming Language
Copyright Net`Q GmbH, 2000-2012
Page 61
In-Depth and Holistic View
Look Across the Entire Organization
Keep Aware of Emerging Threats
Understand Security Risks and Business Impact
Conduct an In-Depth Assessment
Review Organizational Policies
Cross Organizational Communications
Be Proactive
Copyright Net`Q GmbH, 2000-2012
Page 62
Summary
Mainframes will continue to play a critical role
Mainframe are being integrated as part of
organizational Cloud Strategies
Security Continues to be a Concern
Threats are Similar whether IP or SNA based
Security Necessitates an In-Depth and Holistic
Perspective
Security is not an IT Decision – It’s a Business
Decision
Copyright Net`Q GmbH, 2000-2012
Page 63
Questions?
Copyright Net`Q GmbH, 2000-2012
Page 64
Contact
Peter Hager
CEO Net`Q GmbH
(202) 470-2563
[email protected]
Earl Rasmussen
President, Net‘Q America
(202) 470-2697
[email protected]
Copyright Net`Q GmbH, 2000-2012
Page 65
Thank You!
Copyright Net`Q GmbH, 2000-2012
Page 66