* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Single-Source Shortest Path on Weighted Graphs
Survey
Document related concepts
Transcript
EE2204
DATA STRUCTURES AND ALGORITHMS
3 0 0 3
Unit 1
Part a
1. What is meant by an abstract data type?
An ADT is a set of operation. Abstract data types are mathematical
abstractions.Eg.Objects such as list, set and graph along their operations can be
viewed as ADT’s.
2. What are the operations of ADT?
Union, Intersection, size, complement and find are the various operations of
ADT.
3. What is meant by list ADT?
List ADT is a sequential storage structure. General list of the form a1, a2,
a3.…., an and the size of the list is ‘n’. Any element in the list at the position I is
defined to be ai, ai+1 the successor of ai and ai-1 is the predecessor of ai.
4. What are the various operations done under list ADT?
a. Print list
b.Insert
c.Make empty
d.Remove
e.Next
f.Previous
g.Find kth
5. What are the different ways to implement list?
a. Simple array implementation of list
b.Linked list implementation of list
6. What are the advantages in the array implementation of list?
a. Print list operation can be carried out at the linear time
b. Find Kth operation takes a constant time
7. What is a linked list?
Linked list is a kind of series of data structures, which are not necessarily
adjacent in memory. Each structure contains the element and a pointer to a record
containing its successor.
8. What is a pointer?
Pointer is a variable, which stores the address of the next element in the list.
Pointer is basically a number.
9. What is a doubly linked list?
In a simple linked list, there will be one pointer named as ‘NEXT
POINTER’ to point the next element, where as in a doubly linked list, there will be
two pointers one to point the next element and the other to point the previous
element location.
10. Define double circularly linked list?
In a doubly linked list, if the last node or pointer of the list, point to the first
element of the list, then it is a circularly linked list.
11. What is the need for the header?
Header of the linked list is the first element in the list and it stores the
number of elements in the list. It points to the first data element of the list.
12. List three examples that uses linked list?
a. Polynomial ADT
b.Radix sort
c.Multi lists
13. Give some examples for linear data structures?
a. Stack
b.Queue
14. What is a stack?
Stack is a data structure in which both insertion and deletion occur at one
end only. Stack is maintained with a single pointer to the top of the list of
elements. The other name of stack is Last-in -First-out list.
15. Write postfix from of the expression –A+B-C+D?
A-B+C-D+
16. How do you test for an empty queue?
To test for an empty queue, we have to check whether READ=HEAD
where REAR is a pointer pointing to the last node in a queue and HEAD is a
pointer that pointer to the dummy header. In the case of array implementation of
queue, the condition to be checked for an empty queue is READ<FRONT.
17.What are the postfix and prefix forms of the expression?
A+B*(C-D)/(P-R)
Postfix form: ABCD-*PR-/+
Prefix form: +A/*B-CD-PR
18. Explain the usage of stack in recursive algorithm implementation?
In recursive algorithms, stack data structures is used to store the return
address when a recursive call is encountered and also to store the values of all the
parameters essential to the current state of the procedure.
19. Write down the operations that can be done with queue data structure?
Queue is a first – in -first out list. The operations that can be done with
queue are addition and deletion.
20. What is a circular queue?
The queue, which wraps around upon reaching the end of the array is called
as circular queue.
Unit 1 part B
1. Explain the linked list implementation of list ADT in Detail?
a. Definition for linked list
b. Figure for linked list
c. Next pointer
d. Header or dummy node
e. various operations
f. Explanation
g. Example figure
h. Coding
2. Explain the cursor implementation of linked list?
a. Definition for linked list
b. Figure for linked list
c. Next pointer
d. Header or dummy node
e. various operations
f.Explanation
g.Example figure
h.Coding
3. Explain the various applications of linked list?
a. Polynomial ADT
Operations
Coding
Figure
b. Radix Sort
Explanation
Example
c. Multilist
Explanation
Example figure
4. Explain the linked list implementation of stack ADT in detail?
a. Definition for stack
b. Stack model
c.Figure
d.Pointer-Top
e.Operations
f.Coding
g.Example figure
5. Explain the array implementation of queue ADT in detail?
a. Definition for stack
b. Stack model
c. Figure
d. Pointer-FRONT, REAR
e. Operations
f.Coding
g.Example figure
Unit 2& 3
Part A
1. Define non-linear data structure
Data structure which is capable of expressing more complex relationship
than that of physical adjacency is called non-linear data structure.
2. Define tree?
A tree is a data structure, which represents hierarchical relationship between
individual data items.
3. Define leaf?
In a directed tree any node which has out degree o is called a terminal node
or a leaf.
4. What is meant by directed tree?
Directed tree is an acyclic diagraph which has one node called its root with
in degree o while all other nodes have in degree I.
5. What is a ordered tree?
In a directed tree if the ordering of the nodes at each level is prescribed then
such a tree is called ordered tree.
6. What are the applications of binary tree?
Binary tree is used in data processing.
a. File index schemes
b. Hierarchical database management system
7. What is meant by traversing?
Traversing a tree means processing it in such a way, that each node is
visited only once.
8. What are the different types of traversing?
The different types of traversing are
a. Pre-order traversal-yields prefix from of expression.
b. In-order traversal-yields infix form of expression.
c. Post-order traversal-yields postfix from of expression.
9. What are the two methods of binary tree implementation?
Two methods to implement a binary tree are,
a. Linear representation.
b. Linked representation
10. Define pre-order traversal?
Pre-order traversal entails the following steps;
a. Process the root node
b. Process the left subtree
c. Process the right subtree
11.Define post-order traversal?
Post order traversal entails the following steps;
a. Process the left subtree
b. Process the right subtree
c. Process the root node
12. Define in -order traversal?
In-order traversal entails the following steps;
a. Process the left subtree
b. Process the root node
c. Process the right subtree
13. What is a balance factor in AVL trees?
Balance factor of a node is defined to be the difference between the height
of the node's left subtree and the height of the node's right subtree.
14. What is meant by pivot node?
The node to be inserted travel down the appropriate branch track along the
way of the deepest level node on the branch that has a balance factor of +1 or -1 is
called pivot node.
15. What is the length of the path in a tree?
The length of the path is the number of edges on the path. In a tree there is
exactly one path form the root to each node.
16. Define expression trees?
The leaves of an expression tree are operands such as constants or variable
names and the other nodes contain operators.
17. What is the need for hashing?
Hashing is used to perform insertions, deletions and find in constant
average time.
18. Define hash function?
Hash function takes an identifier and computes the address of that identifier
in the hash table using some function.
19. List out the different types of hashing functions?
The different types of hashing functions are,
a. The division method
b. The mind square method
c. The folding method
d. Multiplicative hashing
e. Digit analysis
20. What are the problems in hashing?
a. Collision
b. Overflow
21. What are the problems in hashing?
When two keys compute in to the same location or address in the hash table
through any of the hashing function then it is termed collision.
Unit 2 and 3 part B
1. Explain the different tree traversals with an application?
a. In order
Explanation with an example
Figure
b. Preorder
Explanation with an example
Figure
c. Post order
Explanation with an example
Figure
2. Define binary search tree? Explain the various operations with an example?
a. Definition
b. Figure for binary search tree
c. Operations
d.Codings
e.Explanation
f.Example
3. Define AVL trees? Explain the LL, RR, RL, LR case with an example?
a. Definition
b. LL, RR, RL, LR case
c.Figure
d.Example
e.Explanation
4. Define priority queue? Explain the basic heap operation with an example?
a. Definition
b. Basic operation
Insert
Delmin
Delmax
c. Coding
d. Explanation
e.Example
5. Explain any two techniques to overcome hash collision?
a. Separate chaining
Example
Explanation
coding
b. Open addressing
Linear probing
Quadratic probing
Unit 4
Part A
1. Define Graph?
A graph G consist of a nonempty set V which is a set of nodes of the graph,
a set E which is the set of edges of the graph, and a mapping from the set for edge
E to a set of pairs of elements of V. It can also be represented as G=(V, E).
2. Define adjacent nodes?
Any two nodes which are connected by an edge in a graph are called
adjacent nodes. For E is associated with a pair of nodesexample, if and edge x
(u,v) where u, v V, then we say that the edge x connects the nodes u and v.
3. What is a directed graph?
A graph in which every edge is directed is called a directed graph.
4. What is a undirected graph?
A graph in which every edge is undirected is called a directed graph.
5. What is a loop?
An edge of a graph which connects to itself is called a loop or sling.
6. What is a simple graph?
A simple graph is a graph, which has not more than one edge between a
pair of nodes than such a graph is called a simple graph.
7. What is a weighted graph?
A graph in which weights are assigned to every edge is called a weighted
graph.
8. Define out degree of a graph?
In a directed graph, for any node v, the number of edges which have v as
their initial node is called the out degree of the node v.
9. Define indegree of a graph?
In a directed graph, for any node v, the number of edges which have v as
their terminal node is called the indegree of the node v.
10. Define path in a graph?
The path in a graph is the route taken to reach terminal node from a starting
node.
11. What is a simple path?
A path in a diagram in which the edges are distinct is called a simple path.
It is also called as edge simple.
12. What is a cycle or a circuit?
A path which originates and ends in the same node is called a cycle or
circuit.
13. What is an acyclic graph?
A simple diagram which does not have any cycles is called an acyclic
graph.
14. What is meant by strongly connected in a graph?
An undirected graph is connected, if there is a path from every vertex to
every other vertex. A directed graph with this property is called strongly
connected.
15. When is a graph said to be weakly connected?
When a directed graph is not strongly connected but the underlying graph is
connected, then the graph is said to be weakly connected.
16. Name the different ways of representing a graph?
a. Adjacency matrix
b. Adjacency list
17. What is an undirected acyclic graph?
When every edge in an acyclic graph is undirected, it is called an undirected
acyclic graph. It is also called as undirected forest.
18. What are the two traversal strategies used in traversing a graph?
a. Breadth first search
b. Depth first search
19. What is a minimum spanning tree?
A minimum spanning tree of an undirected graph G is a tree formed from
graph edges that connects all the vertices of G at the lowest total cost.
20. What is NP?
NP is the class of decision problems for which a given proposed solution
for a given input can be checked quickly to see if it is really a solution.
Unit 4 part B
1. Explain the various representation of graph with example in detail?
a. Adjacency matrix
Figure
Explanation
Table
b. Adjacency list
Figure
Explanation
Table
2. Define topological sort? Explain with an example?
a. Definition
b. Explanation
c. Example
d. Table
e. Coding
3. Explain Dijkstra's algorithm with an example?
a. Explanation
b. Example
c. Graph
d. Table
e. coding
4.Explain Prim's algorithm with an example?
a. Explanation
b. Example
c. Graph
d. Table
e. Coding
5. Explain Krushal's algorithm with an example?
a. Explanation
b. Example
c. Graph
d. Table
e. Coding
Unit V
Part A
1. Write down the definition of data structures?
A data structure is a mathematical or logical way of organizing data in the
memory that consider not only the items stored but also the relationship to each
other and also it is characterized by accessing functions.
2. What is meant by problem solving?
Problem solving is a creative process, which needs systemization and
mechanization.
3. Give few examples for data structures?
Stacks, Queue, Linked list, Trees, graphs
4. What is problem definition phase?
The first step in solving a problem is to understand problem clearly. Hence,
the first phase is the problem definition phase. That is, to extract the task from the
problem statement. If the problem is not understood, then the solution will not be
correct and it may result in wastage of time and effort.
5. Define Algorithm?
Algorithm is a solution to a problem independent of programming
language. It consist of set of finite steps which, when carried out for a given set of
inputs, produce the corresponding output and terminate in a finite time.
6. Define Program?
Set of instructions to find the solution to a problem. It is expressed in a
programming language in an explicit and unambiguous manner.
7. Mention how similarities among the problems are used in problem solving?
This method is used to find out if a problem of this sort has been already
solved and to adopt a similar method in solving the problem. The contribution of
experience in the previous problem with help and enhance the method of problem
for the current problem.
8. What is working backward from the solution?
When we have a solution to the problem then we have to work backward to
find the starting condition. Even a guess can take us to the starting of the problem.
This is very important to systematize the investigation to avoid duplication of our
effort.
9. Mention some of the problem solving strategies?
The most widely strategies are listed below
Divide and conquer
Binary doubling strategy
Dynamic programming
10. What is divide and conquer method?
The basic idea is to divide the problem into several sub problems beyond
which cannot be further subdivided. Then solve the sub problems efficiently and
join then together to get the solution for the main problem.
11. What are the features of an efficient algorithm?
a. Free of ambiguity
b.Efficient in execution time
c.Concise and compact
d.Completeness
e.Definiteness
f.Finiteness
12. List down any four applications of data structures?
a. Compiler design
b.Operating System
c.Database Management system
d.Network analysis
13. What is binary doubling strategy?
The reverse of binary doubling strategy, i.e. combining small problems in to
one is known as binary doubling strategy. This strategy is used to avoid the
generation of intermediate results.
14. Where is dynamic programming used?
Dynamic programming is used when the problem is to be solved in a
sequence of intermediate steps. It is particularly relevant for many optimization
problems, i.e. frequently encountered in Operations research.
15. Define top-down design?
Top-down design is a strategy that can be applied to find a solution to a
problem from a vague outline to precisely define the algorithm and program
implementation by stepwise refinement.
16. Mention the types of bugs that may arise in a program?
The different types of bugs that can arise in a program are
Syntactic error
Semantic error
Logical error
17. What is program testing?
Program testing is process to ensure that a program solves the smallest
possible problem, when all the variables have the same value, the biggest possible
problem, unusual cases etc.
18. What is program verification?
Program verification refers to the application of mathematical proof
techniques, to verify that the results obtained by the execution of the program with
arbitrary inputs are in accord with formally defined output Specifications.
19. How will you verify branches with segments?
To handle the branches that appear in the program segments, it is necessary
to set-up and proves verification conditions individually.
20. What is proof of termination?
To prove that a program accomplishes its stated objective in a finite number
of steps is called program termini nation. The prooft of termination is obtained
directly from the properties of the interactive constructs.
Unit V part B
1. Explain top-down design in detail?
a. Definition
b.Breaking a problem in to sub problems
c.Choice of a suitable data structure
d.Constructions ofloops
e.Establishing initial conditions for loops
f.Finding the iterative construct
g.Terminations of loops
2. What are the steps taken to improve the efficiency of an algorithm?
a. Definition
b.Redundant computations
c.Referencing array elements
d.Inefficiency due to late termination
e.Early detection of desired output conditions
f.Trading storage for efficiency gains
3. Design an algorithm fro sine function computation. Explain it with an
example?
a. Algorithm development
b.Algorithm description
c.Pascalimplementation
d.Application
4. Design an algorithm for reversing the digit of an integer. Explain it with an
example?
a. Algorithm development
b.Algorithm description
c.Pascalimplementation
d.Application
5. Design an algorithm for base conversion. Explain it with an example?
Algorithm development
Algorithm description
Pascal implementation
Application
B.E / B.Tech DEGREE EXAMINATION,MAY/JUNE 2006
THIRD SEMESTER
Computer Science and Engineering
CS1151 – DATA STRUCTURES
PART A – (10 X 2 = 20 marks)
1.Define ADT
An ADT is a set of operation. Abstract data types are mathematical
abstractions.Eg.Objects such as list, set and graph along their operations can be
viewed as ADT's.
2.List out the operations of the list ADT?
Insert an item, Delete an item, find, Display
3. Define dequeue.
A deque (short for double-ended queue) is an abstract data structure for
which elements can be added to or removed from the front or back. This differs
from a normal queue, where elements can only be added to one end and removed
from the other
4. Explain the representations of priority queue.
Using Heap structure, Using Linked List
1. Compare the various hashing techniques.
1) Separate chaining – Linked list implementation
2) Open Addressing- Array implementation
2. List out the steps involved in deleting a node from a binary search tree.
1. t has no right hand child node t->r == z
2. t has a right hand child but its right hand child node has no left sub tree
t->r->l == z
3. t has a right hand child node and the right hand child node has a left hand
child node t->r->l != z
3. Explain the topological sort.
It is an Ordering of vertices in a directed acyclic graph such that if there is a
path from vi to vj, then vj appears after vi in the ordering.
4. Define NP hard
NP is the class of decision problems for which a given proposed solutionfor a
given input can be checked quickly to see if it is really a solution.
5. What is binary heap
It is a complete binary tree of height h has between 2h and 2h+1 -1 node. The value
of the root node is higher than their child nodes.
PART B – (5 X 16 = 80 marks)
6. (i) Write algorithms for ADT operations for insert a node to linked list
To insert a new item after B:
1) Modify pointer field of NEW to point to C
2) Modify pointer field of B to point to NEW
NEWNODE->NEXT=B->NEXT;
B->NEXT=NEWNODE;
(ii) Write algorithm for delete a node from linked list
To delete an item coming after B,
1) Modify pointer field of B, to point to the node pointed by pointer of OLD
2) Modify pointer field of OLD as ^ (not to cause problem later on)
B->NEXT=OLD->NEXT;
FREE(OLD);
12. (a) Write ADT routines for stack operation. Write routines for evaluating
a infix expression
A stack is a LIFO (Last-In/First-Out) data structure. Items are taken out of
the stack in the reverse order of their insertion. We can write an application that
evaluates an arithmetic expression using the LIFO storage policy of a stack. The
evaluation procedure consists of two parts: 1) converting an infix expression to the
postfix expression and 2) evaluating the postfix expression to get its value.
1. Infix notation vs. postfix notation
Infix notation
o A common mathematical notation is an infix notation.
o Binary operators, such as +, -, *, /, come in-between their operands.
o Unary operators, such as – (a unary negation), precede their operand.
o Example: A + B * C + D / E - A * C
Postfix notation
o Each operator appears after its operands
o Parenthesis-free notation
o Evaluation can be done by scanning an expression once from left to
right. Therefore, a postfix expression is easier for a calculator (or
computer) to process.
o Example: A B C * + D E / + A C * Infix to postfix (paper and pencil)
1. Fully parenthesize the expression so that each operator has a pair of
parentheses surrounding its operands.
2. Move all operators so that they replace their corresponding right
parenthesis
3. Delete all parentheses.
( ( ( A + ( B * C ) )+ ( D / E ) ) - ( A * C ) )
2. Criteria that determine the order of operator evaluation
Precedence of arithmetic operators:
Operators
Preceden
ce
(unary 3
minus)
*, /
2
+, -
1
Parentheses overrule the precedence of operators.
If the order is not indicated by parentheses, operators of higher precedence
are evaluated before those of lower precedence.
Operators of equal precedence are evaluated from left to right.
3. Infix to Postfix
Let’s first learn how to convert an infix expression to the postfix notation. An
infix2postfix program, the convert method of the textbook pp. 294, takes an infix
expression as a parameter and returns the corresponding postfix notation. The
method maintains one Character stack to store operators.
1) Key ideas of Infix2Postfix algorithm
a) The operands in the postfix expression have the same order as they were
in the infix expression.
o Example: 5*(3-7+9)/10 5 3 7 – 9 + * 10 /
o Operands are appended to postfix as they are read in.
o An operand stack is not needed.
b) All operations between a set of matching parenthesis will be together in a
group within the postfix expression.
o Example: 4 * (3 – 5) 4 3 5 – * ; 4 * (3 – 5 + 2) 4 3 5 – 2 + *
o push ( onto the stack and if ) is encountered, pop off only operators
that are within the pair of matching parentheses and never pop
operators that is below the (.
c) The postfix expression handles operators according to the precedence
rules: the higher precedence operator must be written first; operators of
equal precedence should be written from left to right.
o Example: 4 * 3 + 5 4 3 * 5 +; 4 + 3 * 5 4 3 5 * +; 2 + 3 – 5 2
3+5–
o The current operator will be pushed onto the stack anyway because
we don’t know if it has a higher precedence than the following
operator.
o Before pushing the current operator, pop off the stack until the stack
becomes empty or 2) the top operator has a lower precedence than the
current operator. Then, push the current operator to the stack.
2) Infix2Postfix algorithm
Algorithm
Initialize postfix to an empty StringBuilder.
1. Initialize a stack of characters to hold the operators and left parentheses.
2. while there are more tokens in the infix string
{
Get the next token.
if (the next token is a left parenthesis)
Push the token onto the stack. based on the idea b)
else if (the next token is an operand)
Append it to postfix. based on the idea a)
else if (the next token is an operator) similar to the processOperator method
of the textbook
Pop operators off the stack and append them to postfix until one of the three
things occurs:
1) stack becomes empty or
2) the top is an operator with lower precedence or
3) the top is '(' based on the idea b)
Push the token onto the stack
else
Discard the next token which should be a right parenthesis.
Pop operators off the stack and append them to postfix until the top is '('.
Pop and discard '('. (If no left parenthesis is encountered, then print an error
message indicating unbalanced parentheses, and halt)
} // while
4. Pop any remaining operators on the stack and append them to postfix. (There
should be no remaining left parentheses, otherwise the input expression did not
have balanced parenthesis.)
Note: An example of the while loop in the processOperator is
while (!operatorStack.isEmpty() &&
operatorStack.peek() != '(' &&
precedence(operatorStack.peek()) >=precedence(the current operator))
{ postfix = postfix + operatorStack.pop() + " "; }
operatorStack.push(the current operator);
3) Example
3 * X + (Y – 12 ) – Z 3 X * Y 12 – + Z –
3. Evaluating Postfix Expressions
Postfix expressions:
Parentheses-free.
A space between two consecutive numbers.
Evaluation requires only one stack, which is a stack of operands.
No operator stack is required because each operation is done as soon as it is
read.
2) Algorithm (the eval method of the textbook)
1. Create an empty stack of integers.
2. while there are more tokens
{ Get the next token.
if (the next token is an operand)
Push the token onto the stack.
else // the next token is an operator
{ Pop the correct number for the operator from stack.
Evaluate the operation.
Push the result onto the stack.
}
}
3. Pop the stack and return the result.
1) Example
5 3 2 * + 4 – 5 + 12
(OR)
(b) (i) Write routines for input restricted dequeue.
Three functions:
1)Insert Right 2)Delete Right 3) Delete Left
insert_right()
{
int added_item;
if((left == 0 && right == MAX-1) || (left == right+1))
{
printf("Queue Overflow\n");
return;
}
if (left == -1) /* if queue is initially empty */
{
left = 0;
right = 0;
}
else
if(right == MAX-1) /*right is at last position of queue */
right = 0;
else
right = right+1;
printf("Input the element for adding in queue : ");
scanf("%d", &added_item);
deque_arr[right] = added_item ;
}/*End of insert_right()*/
delete_left()
{
if (left == -1)
{
printf("Queue Underflow\n");
return ;
}
printf("Element deleted from queue is : %d\n",deque_arr[left]);
if(left == right) /*Queue has only one element */
{
left = -1;
right=-1;
}
else
if(left == MAX-1)
left = 0;
else
left = left+1;
}/*End of delete_left()*/
delete_right()
{
if (left == -1)
{
printf("Queue Underflow\n");
return ;
}
printf("Element deleted from queue is : %d\n",deque_arr[right]);
if(left == right) /*queue has only one element*/
{
left = -1;
right=-1;
}
else
if(right == 0)
right=MAX-1;
else
right=right-1;
}/*End of delete_right() */
(ii) Write ADT operation for circular queue
Operations: 1)Insertion
2) Deletion
void add(int item,int q[],int MAX,int front,int rear)
{
rear++;
rear= (rear%MAX);
if(front ==rear)
{
printf("CIRCULAR QUEUE FULL ");
return;
}
else
{
cq[rear]=item;
printf("
Rear = %d Front = %d ",rear,front);
}
}
int del(int q[],int MAX,int front,int rear)
{
int a;
if(front == rear)
{
printf("CIRCULAR STACK EMPTY");
return (0);
}
else
{
front++;
front = front%MAX;
a=cq[front];
return(a);
printf("
Rear = %d Front = %d ",rear,front);
}
}
13. (a) Write routines for ADT operation of AVL tree.
Operations 1)Insertion
struct
node *insert
*ht_inc)
{
struct
node *aptr;
struct
node *bptr;
2) Deletion
(int
info, struct node *pptr,
if(pptr==NULL)
{
pptr
=
(struct
node *)
pptr->info
=
info;
pptr->lchild
=
NULL;
pptr->rchild
=
NULL;
pptr->balance =
0;
*ht_inc =
TRUE;
return
(pptr);
}
malloc(sizeof(struct
if(info
<
pptr->info)
{
pptr->lchild
=
insert(info, pptr->lchild,
if(*ht_inc==TRUE)
{
ht_inc);
int
node));
switch(pptr->balance)
{
case
-1:
/*
Right heavy
*/
pptr->balance =
0;
*ht_inc =
FALSE;
break;
case
0:
/*
Balanced */
pptr->balance =
1;
break;
case
1:
/*
Left heavy
*/
aptr
=
pptr->lchild;
if(aptr->balance
== 1)
{
printf("Left
to
Left Rotation\n");
pptr->lchild= aptr->rchild;
aptr->rchild
=
pptr;
pptr->balance =
0;
aptr->balance=0;
pptr
=
aptr;
}
else
{
printf("Left
to
right rotation\n");
bptr
=
aptr->rchild;
aptr->rchild
=
bptr->lchild;
bptr->lchild
=
aptr;
pptr->lchild
=
bptr->rchild;
bptr->rchild
=
pptr;
if(bptr->balance
pptr->balance =
else
pptr->balance =
if(bptr->balance
aptr->balance =
else
aptr->balance =
bptr->balance=0;
pptr=bptr;
==
-1;
0;
==
1;
0;
1
-1)
)
}
*ht_inc
}/*End
}/*End
}/*End
=
of
of
of
FALSE;
switch
if
*/
if*/
*/
if(info
>
pptr->info)
{
pptr->rchild
=
insert(info, pptr->rchild,
if(*ht_inc==TRUE)
{
switch(pptr->balance)
{
case
1:
/*
Left heavy
*/
pptr->balance =
0;
*ht_inc =
FALSE;
break;
case
0:
/*
Balanced */
pptr->balance =
-1;
break;
case
-1: /*
Right heavy
*/
aptr
=
pptr->rchild;
if(aptr->balance
== -1)
{
printf("Right to
Right Rotation\n");
pptr->rchild= aptr->lchild;
aptr->lchild
=
pptr;
pptr->balance =
0;
aptr->balance=0;
pptr
=
aptr;
}
else
{
printf("Right to
Left Rotation\n");
bptr
=
aptr->lchild;
aptr->lchild
=
bptr->rchild;
bptr->rchild
=
aptr;
pptr->rchild
=
bptr->lchild;
bptr->lchild
=
pptr;
ht_inc);
if(bptr->balance
==
pptr->balance =
1;
else
pptr->balance =
0;
if(bptr->balance
==
aptr->balance =
-1;
else
aptr->balance =
0;
bptr->balance=0;
pptr=bptr;
}/*End of
else*/
*ht_inc =
FALSE;
}/*End of
switch
}/*End of
if*/
}/*End of
if*/
return(pptr);
}/*End of
-1)
1)
*/
insert()*/
(OR)
(b) Write algorithm for ADT operation of priority queue.
Insertion
int
pqinsert(struct pqueue *q, PQDATUM d)
{
PQDATUM *tmp;
int i, newsize;
if (!q) return 0;
/* allocate more memory if necessary */
if (q->size >= q->avail) {
newsize = q->size + q->step;
if (!(tmp = realloc(q->d, sizeof(PQDATUM) * newsize))) {
return 0;
};
q->d = tmp;
q->avail = newsize;
}
/* insert item */
i = q->size++;
while (i > 1 && PQPRIO(q->d[i / 2]) < PQPRIO(d)) {
q->d[i] = q->d[i / 2];
i /= 2;
}
q->d[i] = d;
return 1;
}
Removing Items
PQDATUM *
pqremove(struct pqueue *q, PQDATUM *d)
{
PQDATUM tmp;
int i = 1, j;
if (!q || q->size == 1) return NULL;
*d = q->d[1];
tmp = q->d[--q->size];
while (i <= q->size / 2) {
j = 2 * i;
if (j < q->size &&
PQPRIO(q->d[j]) < PQPRIO(q->d[j + 1])) {
j++;
}
if (PQPRIO(q->d[j]) <= PQPRIO(tmp)) {
break;
}
q->d[i] = q->d[j];
i = j;
}
q->d[i] = tmp;
return d;
}
14. (a)Write heap sort routines. Using above design, sort the following:
15,20,70,07,11,24,53,81,60
(OR)
(b) (i) Write routines for quick sort.
(ii) Explain the external sorting.
15. (a)Write algorithm for weighted and unweighted shortest paths.
Explain the above algorithms with suitable examples.
Single-Source Shortest Path on Unweighted Graphs
(* unweighted single-source shortest path *)
let val q: queue = new_queue()
val visited: vertexMap = create_vertexMap()
(* visited maps vertex->int *)
fun expand(v: vertex) =
let val neighbors: vertex list = Graph.outgoing(v)
val dist: int = valOf(get(visited, v))
fun handle_edge(v': vertex) =
case get(visited, v') of
SOME(d') => () (* d' <= dist+1 *)
| NONE => ( add(visited, v', dist+1);
push(q, v') )
in
app handle_edge neighbors
end
in
add(visited, v0, 0);
expand(v0);
while (not (empty_queue(q)) do expand(pop(q))
end
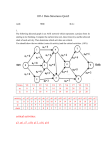
Single-Source Shortest Path on Weighted Graphs
let val q: queue = new_queue()
val visited: vertexMap = create_vertexMap()
fun expand(v: vertex) =
let val neighbors: vertex list = Graph.outgoing(v)
val dist: int = valOf(get(visited, v))
fun handle_edge(v': vertex, weight: int) =
case get(visited, v') of
SOME(d') =>
if dist+weight < d'
then add(visited, v', dist+weight)
else ()
| NONE => ( add(visited, v', dist+weight);
push(q, v') )
in
app handle_edge neighbors
end
in
add(visited, v0, 0);
expand(v0);
while (not (empty_queue(q)) do expand(pop(q))
end
This is nearly Dijkstra's algorithm, but it doesn't work. To see why, consider the
following graph, where the source vertex is v0 = A.
(* Dijkstra's Algorithm *)
let val q: queue = new_queue()
val visited: vertexMap = create_vertexMap()
fun expand(v: vertex) =
let val neighbors: vertex list = Graph.outgoing(v)
val dist: int = valOf(get(visited, v))
fun handle_edge(v': vertex, weight: int) =
case get(visited, v') of
SOME(d') =>
if dist+weight < d'
then ( add(visited, v', dist+weight);
incr_priority(q, v', dist+weight) )
else ()
| NONE => ( add(visited, v', dist+weight);
push(q, v', dist+weight) )
in
app handle_edge neighbors
end
in
add(visited, v0, 0);
expand(v0);
while (not (empty_queue(q)) do expand(pop(q))
end
(OR)
(b) Write and explain the prim’s algorithm and depth first search
algorithm.
Prim's algorithm is known to be a good algorithm to find a minimum spanning tree.
1. Set i=0, S0= {u0=s}, L(u0)=0, and L(v)=infinity for v <> u0. If |V| = 1 then
stop, otherwise go to step 2.
2. For each v in V\Si, replace L(v) by min{L(v), dvui}. If L(v) is replaced, put a
label (L(v), ui) on v.
3. Find a vertex v which minimizes {L(v): v in V\Si}, say ui+1.
4. Let Si+1 = Si cup {ui+1}.
5. Replace i by i+1. If i=|V|-1 then stop, otherwise go to step 2.
B.E / B.Tech DEGREE EXAMINATION,MAY/JUNE 2006
THIRD SEMESTER
Electronics and Communication Engineering
CS1151 – DATA STRUCTURES
PART A – (10 X 2 = 20 marks)
1. Mention any four problem solving strategies
2. What do you mean by program verification
3. What is an ADT?
4. List few applications of queues.
5. Construct an expression tree for the expression A+(B-C)*D*(E+F)
6. What do you mean by primary clustering?
7. Analyse the time complexity of insertion sort algorithm
8. What is external sorting?
9. Define topological sorting
10.What are NP-complete problems? Give an example
PART B – (5 X 16 = 80 marks)
11. (i) With an example, state and explain the algorithm/program to delete
an element from a lexically ordered tree
(10)
(ii) Explain the quadratic probing hashing technique with an example(6)
12.(a) Explain in detail the top down design of problem solving
(OR)
(b) (i) With examples, explain how verification of program segments
with loops is done
(ii) Write notes on o-notation
13. (a) (i) Give a singly linked list, whose first node is pointed to by the
pointer variable C, formulate an algorithm/program to delete the first
occurrence of X from the list(10)
(ii) With examples, explain how a stack can be used to convert an
infix expression to a postfix expression (6)
(OR)
(b) (i) Using linked lists, formulate separate routines to create an empty
stack and to push an element onto a stack
(10)
(ii) Discuss in brief about the array implementation of queues
(6)
14. (a) (i) State and explain the algorithm/program to perform Heap sort
(10)
(ii) Analyse the time complexity of quick sort algorithm (6)
(OR)
(b) (i) State the algorithm/program to perform shell sort. Also, analyse
its worst case running time.
(8)
(ii) Explain any one external sorting with an example
15. (a) (i) With an example, explain the topological sort
(8)
(8)
(ii) Write the pseudo code for Dijkstra’s algorithm. What is the
running time of this algorithm?
(8)
(OR)
(b) (i) For the graph given below, construct
2
2
4
2
1
1
2
10
1
3
8
5
7
4
5
4
1
6
7
6
A minimum spanning tree using Prim’s algorithm. Show the table created
during each pass of the algorithm
(12)
(ii) Write notes on Euler circuits
(4)
B.E / B.Tech DEGREE EXAMINATION,NOVEMBER/DECEMBER 2007
THIRD SEMESTER
Electronics and Communication Engineering
CS1151 – DATA STRUCTURES
TIME:3 Hrs
Marks
MAXIMUM: 100
ANSWER ALL QUESTIONS
PART-A(10*2=20 marks)
1) When will you say an algorithm efficient? Give the notations for time
complexity.
2) What is top-down design? Is C language a top down design?justify
your answer.
3) Why is linked list used for polynomial arithmetic?
4) Write the role of stack in function call
5) What is the minimum number of nodes in an AVL tree of height 5?
6) What is the use of sentinel value in binary heap?
7) Which is the best way of choosing the pivot element in quick sort
8) Merge sort is better than insertion sort .why?
9) Define a graph.how it differs from tree
10) What is minimum spanning tree? Name any two algorithms used
to find MST.
PART-B(5*16=80 marks)
11) (a)(i)Given two lists L1 and L2, write the routines to compute L1
∩ L2 using basic operations.(Hint :for efficient performance, sort the
lists). (10)
(ii)Write the routines for inserting and deleting elements from a
queue.Check for the conditions Q-empty and Q-full. (6)
(Or)
(b)(i) How would you implement a stack of queues? Write routines for
Creation and inserting of elements into it.
(8)
(ii)Write routines to insert heterogeneous data into the list (8)
12 (a)(i)Write the routines to insert and remove node from binary
search tree.(10)
(ii)A full node is a node with two children .Prove that the number
of full Nodes plus one is equal to the number of leave in a binary tree.
(6)
(Or)
(b)(i)Show the result of inserting 2, 1, 4, 5, 9, 3, 6,7into an empty
AVL tree. (6)
(ii) Write the procedures to implement single and double
rotations while inserting nodes in an AVL tree.
(10)
13(a) Explain, with suitable examples the basic heap operations and
write Algorithms for the same
(16)
(Or)
(b) How will you resolve the collisions, while inserting elements into
the hash able using separate chaining and linear probing? Write the
routines for inserting, searching and removing elements from the hash
table using the above mentioned technique.
14 (a) (i) Write the routines for sorting n elements in increasing order
using Heap Sort.
(12)
(ii) Sort 3, 1,4,1,5,9,2,6 in decreasing order using heap sort.
3
(Or)
(b)(i)Explain with example, about the insertion sort.
4
(4)
(6)
(ii)What is external sorting? Discuss the algorithms with proper
Examples (10)
15(a)(i)Discuss and write the program to perform topological sorting
(6)
(ii)What is single source shortest path problem?Discuss Dijikstra’s
single Source shortest path algorithm with an example. (10)
(Or)
(b)(i)write an algorithm to find the minimum cost spanning tree of an
undirected,weighted graph
(8)
(ii)Find MST for the following graph
(8)
2
A
D
4
3
C
3
F
4
B
E
3
B.E / B.Tech DEGREE EXAMINATION, NOVEMBER/DECEMBER 2009
THIRD SEMESTER
Electronics and Communication Engineering
EE2204 – DATA STRUCTURES AND ALGORITHMS
TIME:3 Hrs
Marks
MAXIMUM: 100
ANSWER ALL QUESTIONS
PART-A(10*2=20 marks)
1. Define Abstract Data Type.
An ADT is a set of operation. Abstract data types are mathematical
abstractions.Eg.Objects such as list, set and graph along their operations can
be viewed as ADT’s.
2. Convert the infix expression (A-B/C)*(D/E-F) into a postfix.
Postfix: ABC/-DE/F-*
3. What are the steps to convert a general tree into binary tree?
* use the root of the general tree as the root of the binary tree
* determine the first child of the root. This is the leftmost node in the
general tree at the next level
* insert this node. The child reference of the parent node refers to this
node
* continue finding the first child of each parent node and insert it below
the parent node with the child reference of the parent to this node.
* when no more first children exist in the path just used, move back to
the parent of the last node entered and repeat the above process. In other
words, determine the first sibling of the last node entered.
* complete the tree for all nodes. In order to locate where the node fits
you must search for the first child at that level and then follow the
sibling references to a nil where the next sibling can be inserted. The
children of any sibling node can be inserted by locating the parent and then
inserting the first child. Then the above process is repeated.
4. List the applications of trees.
a. Binary tree is used in data processing.
b. File index schemes
c.Hierarchical database management system
5. What do you mean by a heap?
A heap is a specialized tree-based data structure that satisfies the heap
property: if B is a child node of A, then key (A) ≥ key(B). This implies that an
element with the greatest key is always in the root node, and so such a heap is
sometimes called a max-heap. (Alternatively, if the comparison is reversed, the
smallest element is always in the root node, which results in a min-heap.)
6. Define hashing.
Hash function takes an identifier and computes the address of that identifier
in the hash table using some function
7. What is topological sort?
It is an Ordering of vertices in a directed acyclic graph such that if there is a
path from vi to vj, then vj appears after vi in the ordering.
8. Define biconnected graph.
A connected undirected graph is biconnected if there are no vertices whose
removal disconnects the rest of the graph.
9. State the greedy algorithm.
A greedy algorithm is any algorithm that follows the problem solving
metaheuristic of making the locally optimal choice at each stage with the hope
of finding the global optimum.
10.Mention any two decision problems which are NP-Complete.
NP is the class of decision problems for which a given proposed
solution for a given input can be checked quickly to see if it is really a
solution.
PART-B (5*16 = 80 Marks)
(For page numbers refer DATA STRUCTURES AND ALGORITHM ANALYSIS
IN C by Allen Weiss)
11. (a) Explain the following operations in a doubly linked list. (page no:116)
(i)
(ii)
(iii)
Insert an element
Delete an element
Reverse the list
Or
(6)
(5)
(5)
(b) (i) Discuss the algorithms for push and pop operations on a stack(8)
(ii) Write an algorithm to insert and delete a key in a circular queue
12. (a) (i) Construct all possible tree structure with 4 nodes. (8)
(ii) Perform preorder, inorder and postorder traversals of the given tree.(8)
Or
(b) Explain the following operations on a binary search tree with suitable
Algorithms.
(i)
find a node
(5)
(ii) Insert a node
(5)
(iii) Delete a node
(6)
13.(a) (i) Discuss how to insert an element in an AVL tree. Explain with
Algorithm
(10)
(ii) What is B-Tree? Explain its properties.
Or
(6)
(b) (i) Describe the different hashing functions with an example. (8)
(ii) Explain the common collision resolution strategies in open addressing
hashing.(8)
14. (a) (i) Explain the breadth first search algorithm
(8)
(ii) Write and explain the prims algorithm with an example (8)
Or
(b) (i) What is a strongly connected graph? Give an example. (4)
(ii) Write the algorithm to compute lengths of shortest path (4)
(iii) Explain the depth first search algorithm. (8)
15. (a) Find the optimal tour in the following traveling salesperson problem
Using dynamic programming.
(16)
Or
(b) (i) Explain the method of solving N queens problem by back tracking
(10)
(ii) Discuss briefly the various asymptotic notations used in algorithm
Analysis (6)
B.E./B.Tech. DEGREE EXAMINATION, NOVEMBER/DECEMBER 2010
Third Semester
Electrical and Electronics Engineering
EE 2204 — DATA STRUCTURES AND ALGORITHMS
(Common to Electronics and Instrumentation Engineering and Instrumentation and
Control Engineering)
(Regulation 2008)
Time : Three hours Maximum : 100 Marks
Answer ALL questions
PART A — (10 × 2 = 20 Marks)
1. Distinguish between linear and non-linear data structures.
2. Write down the steps to modify a node in linked lists.
3. Define a path in a tree.
4. What is a binary search tree?
5. Define hashing.
6. What is meant by open addressing?
7. What is minimum spanning tree?
8. Define depth-first traversal in a tree.
9. Differentiate ‘‘divide and conquer’’ technique from ‘‘branch and bound’’
technique.
10. Explain dynamic programming.
PART B — (5 × 16 = 80 Marks)
11. (a) Write down and explain the algorithms for basic operations on stack
ADT.
Or
(b) Explain polynomial manipulation using linked lists with an example.
12. (a) With suitable examples, explain binary tree traversal algorithms.
Or
(b) Explain the following operations in binary search trees :
(i) Insertion of a node (6)
(ii) Searching a node (5)
(iii) Modification of a node. (5)
13. (a) With suitable examples, explain the basic operations on AVL trees.
Or
(b) Explain the following in hashing :
(i) Folding method (6)
(ii) Division method (5)
(iii) Linear probing. (5)
14. (a) Explain in detail the Dijkstra’s algorithm to solve the shortest path
problem.
Or
(b) Discuss in detail the applications of graphs.
15. (a) (i) With an example, explain backtracking. (8)
(ii) Discuss the asymptotic notations. (8)
Or
(b) Write detailed notes on NP-complete problem
B.E./B.Tech. DEGREE EXAMINATION, NOVEMBER/DECEMBER 2011.
Third Semester
Electrical and Electronics Engineering
EE 2204 — DATA STRUCTURES AND ALGORITHMS
(Common to Electronics & Instrumentation Engineering and Instrumentation &
Control Engineering)
(Regulation 2008)
Time : Three hours Maximum : 100 marks
Answer ALL questions.
PART A — (10 × 2 = 20 marks)
1. What is Abstract data type?
2. List any two applications of queue.
3. Define non linear data structure.
4. Define complete binary tree.
5. Define AVL trees.
6. Define load factor of a hash table.
7. What is a forest?
8. Define Biconnectivity.
9. List any two applications that use greedy algorithm.
10. Define Skip Lists.
PART B — (5 × 16 = 80 marks)
11. (a) (i) Explain in detail the linked stack and linked queue.
(ii) Given two sorted lists, L1 and L2, write procedure to compute L1 U L2 and L1
using only the basic list operations.
Or
(b) What is a doubly linked list? Write an algorithm for inserting and deleting an
element from Doubly linked list.
12. (a) How do you represent binary tree in a list? Write an algorithm for finding
Kth element and deleting an element.
Or
(b) Construct an expression tree for the following expression (a + b*c)+(d*e +
f)*g.
13. (a) Write the functions to insert and delete elements from the AVL tree.
Or
(b) What is meant by open addressing? Explain the collusion resolution strategies
in detail.
14. (a) Compare Prim’s algorithm with Kruskal’s algorithm.
Or
(b) List any two applications of DFS. Explain in detail.
15. (a) State the running time equation theorem of divide and conquer algorithms
and prove it.
Or
(b) Prove that the travelling salesman problem is NP complete.
B.E./B.Tech. DEGREE EXAMINATION, NOVEMBER/DECEMBER 2009
Third Semester
Electrical and Electronics Engineering
EE 2204 — DATA STRUCTURES AND ALGORITHMS
(Regulation 2008)
(Common to Instrumentation and Control Engineering and Electronics and
Instrumentation Engineering)
Time : Three hours Maximum : 100 Marks
Answer ALL Questions
PART A — (10 × 2 = 20 Marks)
1. Define Abstract Data Type.
2. Convert the infix expression F) (D/E B/C) (A − ∗ − into a postfix.
3. What are the steps to convert a general tree into a binary tree?
4. List the applications of trees.
5. What do you mean by a heap?
6. Define hashing.
7. What is topological sort?
8. Define biconnected graph.
9. State the greedy algorithm.
10. Mention any two decision problems which are NP-Complete.
PART B — (5 × 16 = 80 Marks)
11. (a) Explain the following operations in a doubly linked list.
(i) Insert an element (6)
(ii) Delete an element (5)
(iii) Reverse the list. (5)
Or
(b) (i) Discuss the algorithms for push and pop operations on a stack. (8)
(ii) Write an algorithm to insert and delete a key in a circular queue. (8)
12. (a) (i) Construct all possible tree structure with 4 nodes. (8)
(ii) Perform preorder, inorder and postorder traversals of the given
tree. (8)
Or
(b) Explain the following operations on a binary search tree with suitable
algorithms.
(i) Find a node (5)
(ii) Insert a node (5)
(iii) Delete a node. (6)
13. (a) (i) Discuss how to insert an element in an AVL tree. Explain with
algorithm. (10)
(ii) What is B-Tree? Explain its properties. (6)
Or
(b) (i) Describe the different hashing functions with an example. (8)
(ii) Explain the common collision resolution strategies in open
addressing hashing. (8)
14. (a) (i) Explain the breadth first search algorithm. (8)
(ii) Write and explain the Prim’s algorithm with an example. (8)
Or
(b) (i) What is a strongly connected graph? Give an example. (4)
(ii) Write the algorithm to compute lengths of shortest path. (4)
(iii) Explain the depth first search algorithm. (8)
15. (a) Find the optimal tour in the following traveling salesperson problem
using dynamic programming. (16)
Or
(b) (i) Explain the method of solving N queens problem by back tracking.
(10)
(ii) Discuss briefly the various asymptotic notations used in algorithm
analysis. (6)