* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Maritime Cyber Vulnerabilities in the Energy Domain
Unix security wikipedia , lookup
Mobile security wikipedia , lookup
Cross-site scripting wikipedia , lookup
Security-focused operating system wikipedia , lookup
Computer and network surveillance wikipedia , lookup
International cybercrime wikipedia , lookup
Cyberterrorism wikipedia , lookup
Cyber-security regulation wikipedia , lookup
Cyberwarfare wikipedia , lookup
Cybercrime countermeasures wikipedia , lookup
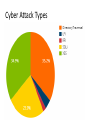
Maritime Cyber Vulnerabilities in the Energy Sector Center for Joint Operations of the Sea ODU Maritime Institute Students Crow, Fresco, Lee Situation In 2013, 40% of cyber attacks were directed at energy infrastructure. Challenges to energy industry cyber security can be broken down into 2 major categories. • Protecting the equipment that generates energy • Preventing the attackers to access to system database IT Systems • Shipboard computers are Linux based, and computers collect all the data into a storage center. – Inside database network server – Outside database network server via internet Data System • Supervisory Control and Data Acquisition (SCADA) systems which controls assets of industrial system. – When it was first introduced the problems to future security was not understood. Cyber Attack Types • SQL injection – improper coding to website to gain access to the database • Remote and Local File Inclusion – stealing data through manipulation of a company’s web server • XSS – Using victim’s browser to hijack information • Directory Traversal – Exploiting insufficient security validation on the server to access the content Liquefied Natural Gas • • • • 2nd highest energy source Clear odorless natural gas Volume changes to 1/600 when liquefied Higher-pressure tanks require periodic inspection LNG Process • Exploration and transportation of the natural gas is complex LNG Vulnerability • Collision • Release of gas to atmosphere (Computer Error) • Explosion • Fire Regulatory Guidance • Office of Energy Infrastructure Security increase the response time and efficiency to the potential threats • Draft a executive order to create a cybersecurity council (DHS) • Information Security Risk Management program is created by voluntary movement • The Critical Information Infrastructure Protection was introduced to protect energy sectors from cyber attacks.