* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Quantum Cryptography
Bell test experiments wikipedia , lookup
Double-slit experiment wikipedia , lookup
Wheeler's delayed choice experiment wikipedia , lookup
Path integral formulation wikipedia , lookup
Particle in a box wikipedia , lookup
Measurement in quantum mechanics wikipedia , lookup
Theoretical and experimental justification for the Schrödinger equation wikipedia , lookup
Probability amplitude wikipedia , lookup
Copenhagen interpretation wikipedia , lookup
Quantum field theory wikipedia , lookup
Hydrogen atom wikipedia , lookup
Density matrix wikipedia , lookup
Quantum dot wikipedia , lookup
Coherent states wikipedia , lookup
Bell's theorem wikipedia , lookup
Quantum entanglement wikipedia , lookup
Bohr–Einstein debates wikipedia , lookup
Many-worlds interpretation wikipedia , lookup
Quantum electrodynamics wikipedia , lookup
Symmetry in quantum mechanics wikipedia , lookup
Quantum fiction wikipedia , lookup
Orchestrated objective reduction wikipedia , lookup
Interpretations of quantum mechanics wikipedia , lookup
EPR paradox wikipedia , lookup
History of quantum field theory wikipedia , lookup
Delayed choice quantum eraser wikipedia , lookup
Canonical quantization wikipedia , lookup
Quantum teleportation wikipedia , lookup
Quantum group wikipedia , lookup
Quantum computing wikipedia , lookup
Quantum state wikipedia , lookup
Quantum machine learning wikipedia , lookup
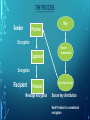
QUANTUM CRYPTOGRAPHY INTRODUCTION • Quantum cryptography is the single most successful application of Quantum Computing/Information Theory. • For the first time in history, we can use the forces of nature to implement perfectly secure cryptosystems. • It relies on 2 major elements of quantum mechanics: i.e heisenberg uncertainity principle and principle of photon polarization. NEED OF QUANTUM CRYPTOGRAPHY • Classical Cryptography relies heavily on the complexity of factoring integers. • Quantum Computers can use Shor’s Algorithm to efficiently break today’s cryptosystems. • We need a new kind of cryptography! BASIC IDEA IN CRYPTOGRAPHY • Cryptography: “the coding and decoding of secret messages.” • • The basic idea is to modify a message so as to make it unintelligible to anyone but the intended recipient. Cryptosystem (Cipher System) – method of disguising messages so that only certain people can read them • Cryptography – Art of creating and using Cryptosystems • For message (plaintext) M, e(M, K) encryption - ciphertext d[e(M, K), K] = M decryption • Cryptanalysis – Art of breaking Cryptosystems • Cryptography – study of Cryptography and Cryptosystems THE PROCESS Key Sender Plaintext Encryption Cryptotext Secure transmission Decryption Recipient Plaintext Message encryption Key ready for use Secure key distribution Hard Problem for conventional encryption THE CLASSIC CRYPTOGRAPHY • Encryption algorithm and related key are kept secret. • Breaking the system is hard due to large numbers of possible keys. • For example: for a key 128 bits long 128 38 • there are 2 10 keys to check using brute force. The fundamental difficulty is key distribution to parties who want to exchange messages. FACTORING A PRODUCT OF TWO LARGE PRIMES • The best known conventional algorithm requires the solution time proportional to: T (n) exp[ c(ln n) (ln ln n) 1/ 3 2/3 ] For p & q 65 digits long T(n) is approximately one month using cluster of workstations. For p&q 200 digits long T(n) is astronomical. QUANTUM COMPUTING ALGORITHM FOR FACTORING. • In 1994 Peter Shor from the AT&T Bell Laboratory showed that in principle a quantum computer could factor a very long product of primes in seconds. • Shor’s algorithm time computational complexity is T (n) O[(ln n) ] 3 Once a quantum computer is built the RSA method would not be safe. BINARY INFORMATION • A user can suggest a key by sending a stream of randomly polarized photons. • This sequence can be converted to a binary key. • If the key was intercepted it could be discarded and a new stream of randomly polarized photons sent. QUANTUM KEY DISTRIBUTION • Quantum Key Distribution exploits the effects discussed in order to thwart eavesdropping. • It enables two parties to produce a shared random bit string known only to them, which can be used as a key for encryption and decryption. • If an eavesdropper uses the wrong polarization basis to measure the channel, the result of the measurement will be random. SECURITY OF QUANTUM KEY DISTRIBUTION • Quantum cryptography obtains its fundamental security from the fact that each qubit is carried by a single photon, and each photon will be altered as soon as it is read. • This makes impossible to intercept message without being detected. NOISE • The presence of noise can impact detecting attacks. • Eavesdropper and noise on the quantum channel are indistinguishable. (1) Malicious eavesdropper can prevent communication. (2) Detecting eavesdropper in the presence of noise is hard. THE MAIN CONTRIBUTION OF QUANTUM CRYPTOGRAPHY. • It solved the key distribution problem. • Unconditionally secure key distribution method proposed by: Charles Bennett and Gilles Brassard in 1984. • The method is called BB84. • Once key is securely received it can be used to encrypt messages transmitted by conventional channels. STATE OF THE QUANTUM CRYPTOGRAPHY TECHNOLOGY. • Experimental implementations have existed since 1990. • Current (2004) QC is performed over distances of 30-40 kilometers using optical fiber. In general we need two capabilities. (1) Single photon gun. (2) Being able to measure single photons. CONCLUSION • Quantum cryptography promises to revolutionize secure communication by providing security based on the fundamental laws of physics, instead of the current state of mathematical algorithms or computing technology. • The devices for implementing such methods exist and the performance of demonstration systems is being continuously improved. • Within the next few years, if not months, such systems could start encrypting some of the most valuable secrets of government and industry. THANK YOU