* Your assessment is very important for improving the work of artificial intelligence, which forms the content of this project
Download Module3 - ITProGuru Blog
Mobile security wikipedia , lookup
Deep packet inspection wikipedia , lookup
Unix security wikipedia , lookup
Wireless security wikipedia , lookup
Security-focused operating system wikipedia , lookup
Computer and network surveillance wikipedia , lookup
Computer security wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
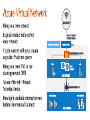
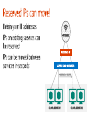
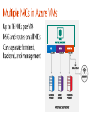
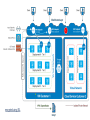
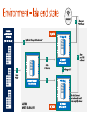
Dan Stolts, Chief Technology Strategist Twitter: @ITProGuru Blog: http://ITProGuru #InnovateIT WEBROLE.0.CONTOSO.CLOUDAPP.NET 130.26.10.80 WEBROLE.0.CONTOSO.CLOUDAPP.NET 130.26.10.80 Q. How do I securely connect my on-premises environment to the cloud? Azure Customer Site VPN Resources Azure Network Security Whitepaper Computers Behind Firewall Remote Workers addresses private IP Cloud Access Layer: • • • Define Security Groups OR Endpoint ACLs to control open inbound traffic 3rd Party Firewalls also available External public ports with sensitive data should be encrypted using SSL The administrator can segment intranet traffic at the network layer within a Virtual Network by using Network Security Groups. Network Security Groups can be applied to a subnet in a Virtual Network. <insert lab url here ↪.\Lab03Start.ps1 ↪.\RGCleanup.ps1 aka.ms/ITInnovation aka.ms/ITInnovationResources www.microsoftcloudroadshow.com